
Security Blog, Rants, Raves, Write-ups, and Code
Ransomware Payments: Should They be Made Illegal?
September 2, 2020
Chris Ruggieri
This one is going to sting a lot of people in a lot of circles, but this needs to be said and I’ve never exactly been known for my subtlety, but rather I am known for being the blunt, brutally honest person that says what’s on his mind. No one ever has to wonder where they stand with me, because I come right out and tell them when they’re being an idiot. I also wish to say that I do not advocate paying the ransom, unless there is absolutely NO OTHER OPTION. Which brings me to the topic of this article and the legality, and even fiscal responsibility, of ransomware payments.
Firstly, why in the world is this even a question up for debate?? I’m glad you asked! Here’s why. On, February 4, 2020 Mr. Flemming Shi, Chief Technology Officer for Barracuda Networks since 2004, published an article in Dark Reading entitled “Ransomware Attacks: Why It Should Be Illegal to Pay the Ransom.” Now on the surface, this seems like a mildly legitimate question……for someone that hasn’t been in the trenches of this Cyber War in over a decade. The article calls out mostly municipalities, counties, states, basically overall the public sector, but does pull in some private sector comparisons as well. The article states that between January and August of 2019, more than 70 State and Local governments had been hit, crippling IT operations and costing millions of tax dollars. The article specifically called out Lake City, FL ($500,000 or 42 BTC), Riviera Beach, FL ($600,000 or 65 BTC), La Porte County, Indiana ($130,000 or ~11 BTC), Baltimore, MD ($18,000,000 in data recovery, but notably DID NOT PAY THE RANSOM which at the time was $80,000) and a few others.
Having worked in the public sector at the city, county, state, and federal levels, I can attest to the fact that IT is an afterthought in EVERY SINGLE LEVEL. So, my first “Are you serious right now?” moment is that if your issue is that cities and states are getting hit more often, then let’s file that under “DUH!” and increase their IT budgets to actually get them the solutions they need to prevent said attacks. But the article doesn’t stop there. Oh, no. It’s just getting started. The article next goes after the fact that those entities are using Cyber Insurance and a “trade-off.” Well, yeah. They can’t get the budget to protect so they shift the risk to the insurance company. Bad strategy? Obviously in the long term that’s bad, but can you really blame them? You have this priceless painting hanging on your wall for all the world to see. You hire people to protect that priceless painting, but you don’t give them the money or tools to actually protect it (motion sensors, laser trips if someone gets to close to the painting, CAMERAS even). Nope. Those protectors are just supposed to wave their mystical, magical wands and keep it safe. Well, to quote the ABC TV Series “Once Upon a Time”, “All magic comes at a price, dearie!” (Unrelated side note: I actually dressed up as Rumplestiltskin from Once Upon a Time for a Halloween Contest in 2018. Had the green mottled skin, the dagger, the outfit, the voice, all of it.) The editor for Dark Reading even admitted that the author’s suggestions for protections against Ransomware are all items that Barracuda itself provides. The author, Mr. Shi, suggests these protections:
- Spam Filters/Phishing Detection Systems
- Advanced Firewalls
- Malware Detection
- User-Awareness Training
- Backups
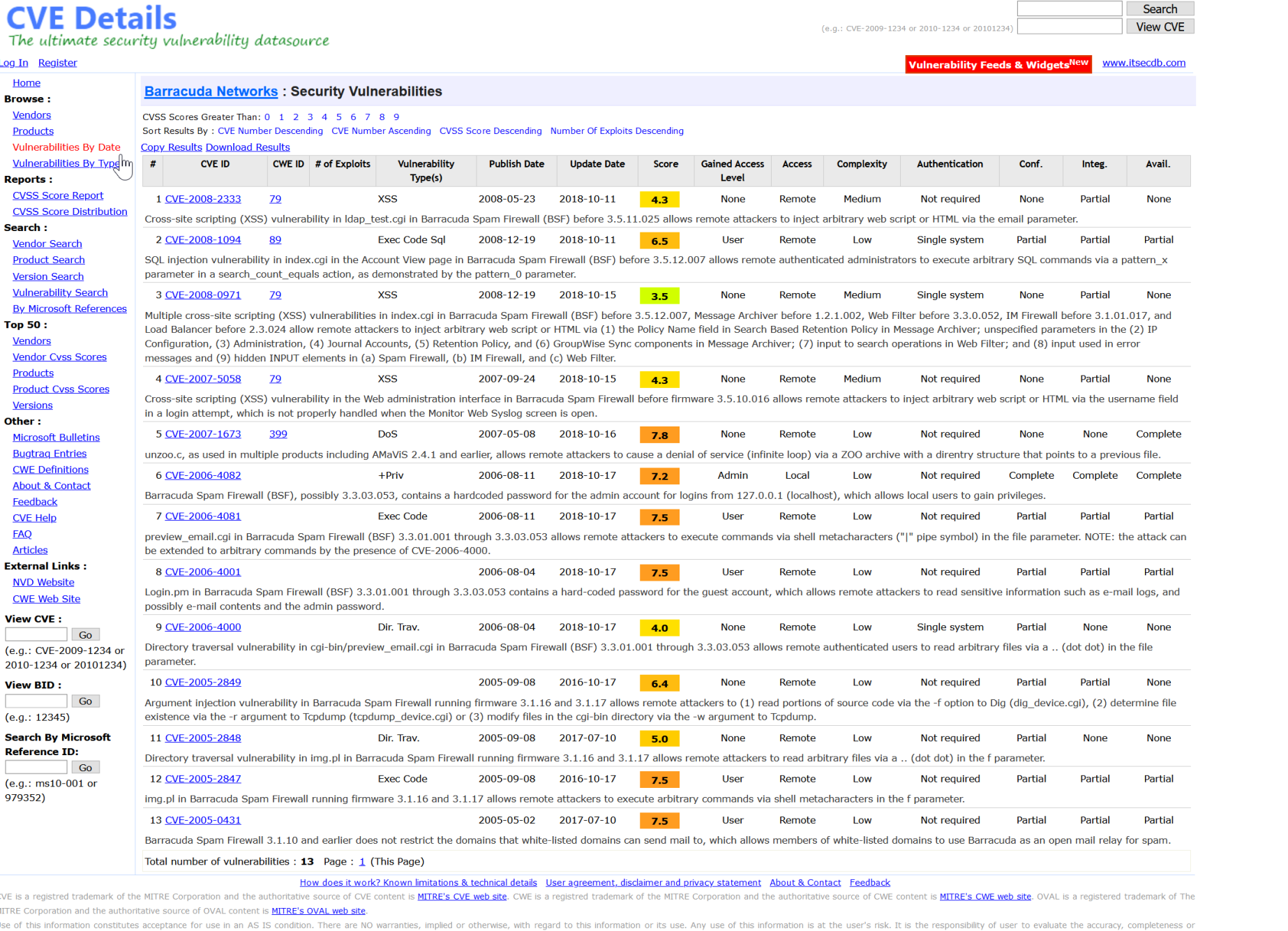
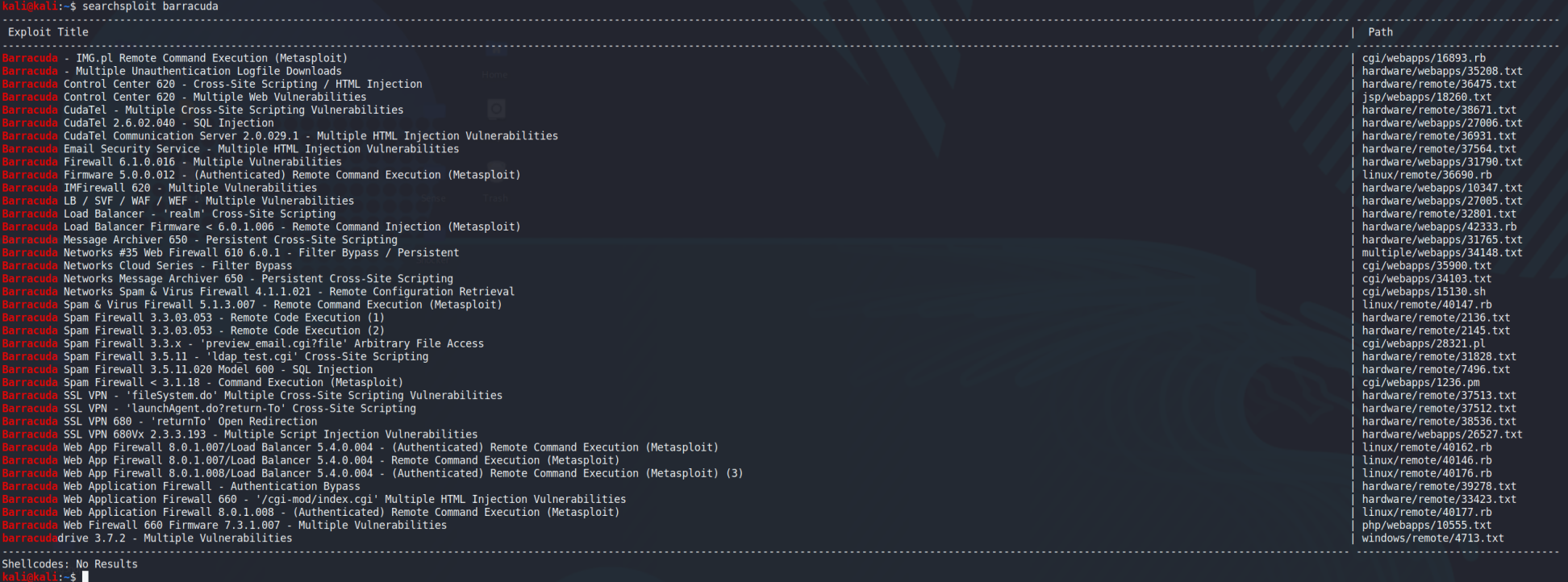
Let’s just take a quick look under the hood of just Barracuda’s devices.
Searchsploit
That’s a LONG list of vulnerabilities that would allow attackers past those protections. It’s not just Barracuda solutions either! It’s EVERYONE’S. Think about that for just a moment. Every one of those suggestions can be bypassed. Those of us that have been in the trenches our entire careers know that you can check every box, do everything right, and one click could bring it all crumbling down. Do I need to keep going? Have you figured it out yet? Second “Are you serious right now?” moment. EVERY ONE of the preventative solutions being sold can be bypassed and that public entity is still hit. Meaning THEIR OWN CUSTOMERS would no longer be able to recover.
I guess that’s where the “User Awareness Training” comes in. SANS Security Awareness has found that even the most highly mature phishing program can only get the click rate down to around 1-2%. Barracuda Networks has approximately 1,500 employees. Meaning 15-30 are clicking that link. It only takes one click buddy! ONE CLICK and it’s Humpty Dumpty time.
On Backups, this is where things get even more tricky. How long does a company traditionally keep backups? Yes, backups are the first and foremost best defense against ransomware, but here’s the snag. Is ransomware the first thing the attacker is detonating? Usually, and others of us in the Incident Response/Digital Forensics space can attest, ransomware usually only detonates AFTER the attacker has either A) gotten whatever data they wanted exfiltrated, or B) got caught. If your attacker had persistence for 6 months, your backups are useless. You will have backed up the ransomware too and as soon as you restore from backup, detonation again. You’ll be stuck in the same boat.
Long story to get to a point of, just preventative measures are NOT a guarantee. Now, let’s talk about the fiscal responsibility to the tax payers from JUST the public sector angle. Scenario: These preventative measures were in place. These preventative measures failed through either bypass from a skilled attacker, misconfiguration, whatever, pick a feature. Is it fiscally responsible for the tax payers of Baltimore, or Atlanta, or any other of the dozens of public entities to spend MILLIONS of dollars recovering, when they could have gotten the data back for, in Baltimore’s case, $80 grand? A $17,920,000 difference.
Let’s up the ante on this topic. Canon and Garmin. Canon was ranked 345 in the Fortune 500. They got hit (and paid) July 2020. Garmin was S&P 500. They got hit in July as well and paid $10 MILLION. The author would apparently prefer these major powerhouse companies to just go away, because anyone that’s been in these trenches knows that you can do every right and still get hit. Outlawing ransomware payments is NOT going to make the attackers change tactics or eliminate the market. In fact, it will cause an exponential increase in these attacks.
Now here’s the part that should scare EVERYONE and more importantly, kill this idea before it’s lunacy can gain anymore steam. Let’s go totally nuclear on the topic. Literally. Nuclear. Let’s say that the author gets what he wants, and all ransomware payments are now made illegal. Congratulations, Mr. Shi. You have single-handedly destroyed American Economics by handing a digital nuclear bomb to America’s enemies. If the world knows that no US company can pay the ransom, you will see EVERY other country immediately attack with ransomware. It doesn’t even have to be Nation State Actors!!! A competing company in say Spain, could attack their competition in the US, cripple them with ransomware and now they’ve got the upper hand. God help us if it IS a Nation State Actor! That possibility takes it into a whole new realm of National Security Interests and fortunately out of the hands of tech companies selling products that might or might not actually help. I understand the sentiment and idea behind the question. However, the last thing we need is another dumpster fire piece of legislation from politicians that thing IT is magic as it is (I’m looking at you CCPA). The other side of the question is also, is this a “if you can’t compete, legislate” situation? If that’s the case, it’s going to backfire in EPIC proportions.
Now, my issue is not with Barracuda. Hell, it’s not even an issue with Mr. Shi. He is obviously respected and accomplished enough to have made it to the CTO position of a MAJOR IT and Cyber firm as well as being published by Dark Reading. I’m just some shmuck that likes to play Devil’s Advocate, mix things up, and have a lot of fun while I’m at it. While all of that is true, it doesn’t mean that my viewpoint and concerns are wrong, does it? Would outlawing ransomware payments make public sector a bigger target than it is now? Right now, it’s just criminal syndicates trying to make a quick buck. Do this, and suddenly North Korea, Russia, China, Iran, and the list goes on and on ALL jump at the chance to cripple the US because they can. Would outlawing ransomware payments jeopardize small and medium business? Absolutely, count them out entirely. Hell, I built my first business on BEING the IT department for SMBs because they couldn’t afford full time staff.
The one thing I do agree with from this article are the final two paragraphs.
“Instead of paying ransoms, we need to build awareness and empower a workforce to help us digitally defend ourselves. This is an opportunity for America to lead the way in cyber protection and to build a strong industry of cybersecurity leaders by creating a variety of new jobs and opportunities to help us protect the data and build a stronger infrastructure.
Cybercriminals are going to keep launching attacks. More talent, skills, and training are needed to protect our governments, businesses, and individual citizens. It's time to think about cybersecurity in a new way.”
I would add to that final statement with, “Tech companies worldwide need to come together in their support of things like the ‘No More Ransom’ project. Projects like No More Ransom are what will eventually kill the ransomware market.
