Security Blog, Rants, Raves, Write-ups, and Code

Security Blog, Rants, Raves, Write-ups, and Code
Export
| Name: | Persistence |
|---|---|
| Hint: | We're noticing some strange connections from a critical PC that can't be replaced. We've run an AV scan to delete the malicious files and rebooted the box, but the connections get re-established. We've taken a backup of some critical system files, can you help us figure out what's going on? |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |

|
HTB-Bot |
| Creator: | felamos |
Download and unzip the file and check the hint:
Hint: We're noticing some strange connections from a critical PC that can't be replaced. We've run an AV scan to delete the malicious files and rebooted the box, but the connections get re-established. We've taken a backup of some critical system files, can you help us figure out what's going on?
Files: query
This is a Windows Registry Hive. We can tell this by running "file query". So, we can use reglookup in Kali to see all the registry keys. Since the name of this challenge is Persistence, we need to examine the locations that would allow persistence for an attacker (usually HKCU/Windows/CurrentVersion/Run etc.).
Running:
┌──(kali㉿kali)-[~/Desktop/HTB/Persistence]
└─$ reglookup query | grep /Windows/CurrentVersion/Run
/Software/Microsoft/Windows/CurrentVersion/Run,KEY,,2020-10-27 04:38:55
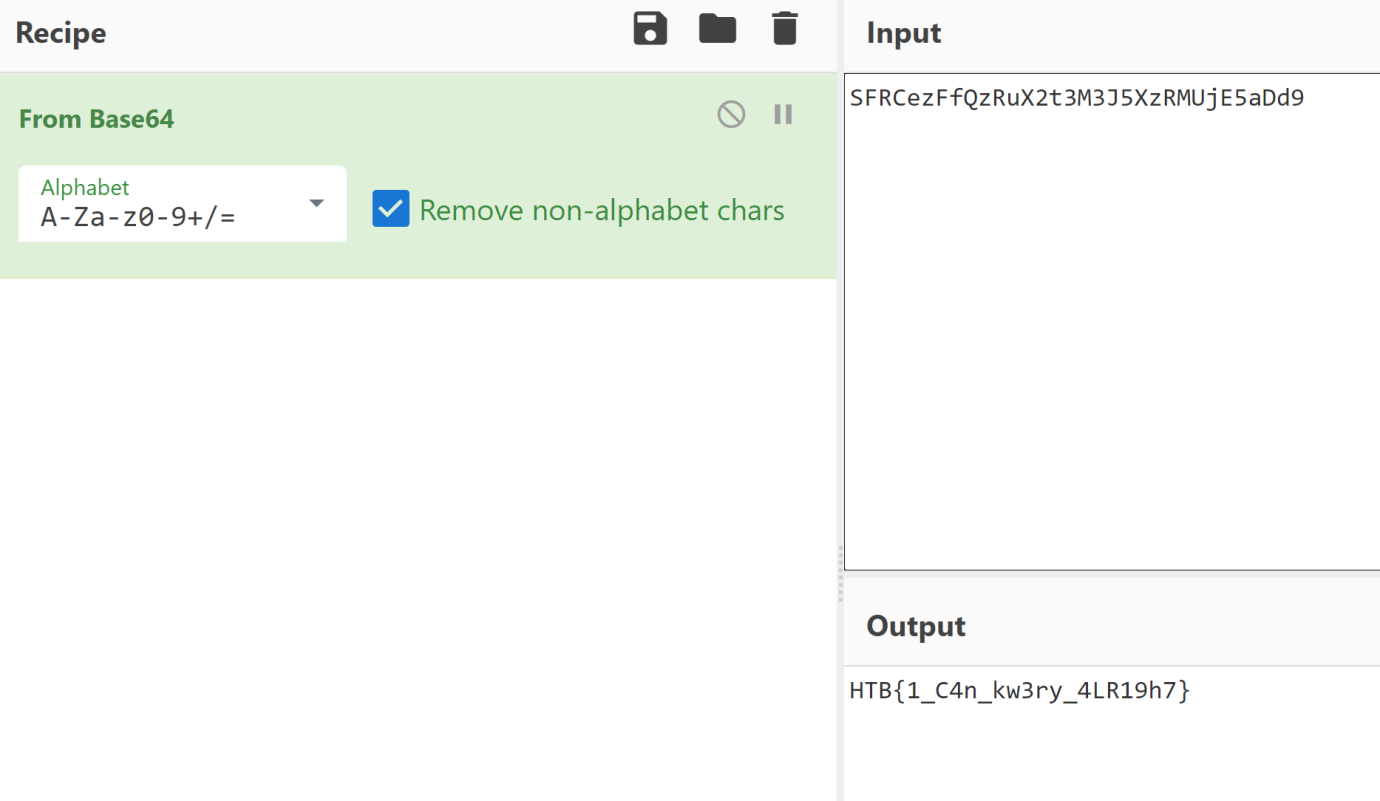
/Software/Microsoft/Windows/CurrentVersion/Run/Windows Update,SZ,C:\Windows\System32\SFRCezFfQzRuX2t3M3J5XzRMUjE5aDd9.exe,
Well, that exe filename looks interesting. Run it through CyberChef and Base64 decode it and we have our flag!
HTB{1_C4n_kw3ry_4LR19h7}