Security Blog, Rants, Raves, Write-ups, and Code

Security Blog, Rants, Raves, Write-ups, and Code
Peel Back The Layers
| Name: | Peel Back The Layers |
|---|---|
| Hint: | A well known hacker rival of ours, managed to gain access to our dockehub profile and insert a backdoor to one of our public docker images in order to distribute his malware and fullfil his soul purpose, which is to destroy our steampunk robot using his steam malware. When we started tracing him back he deleted his backdoor. Can you help us retrieve his backdoor? Docker Image: `steammaintainer/gearrepairimage` |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |

|
HTB-Bot |
| Creator: | thewildspirit |
There is no download on this one but check the hint to see the Docker image to grab:
Hint: A well known hacker rival of ours, managed to gain access to our dockehub profile and insert a backdoor to one of our public docker images in order to distribute his malware and fullfil his soul purpose, which is to destroy our steampunk robot using his steam malware. When we started tracing him back he deleted his backdoor. Can you help us retrieve his backdoor? Docker Image: `steammaintainer/gearrepairimage`
We first need to pull and save that image. We can do that by running (PBTR being short for Peel Back The Layers):
sudo docker pull steammaintainer/gearrepairimage
sudo docker save steammaintainer/gearrepairimage > PBTL.tar
We can see historical changes by using ContainerTools container-diff:
curl -LO https://storage.googleapis.com/container-diff/latest/container-diff-linux-amd64 && \ sudo install container-diff-linux-amd64 /usr/local/bin/container-diff
sudo container-diff analyze -t history PBTL.tar
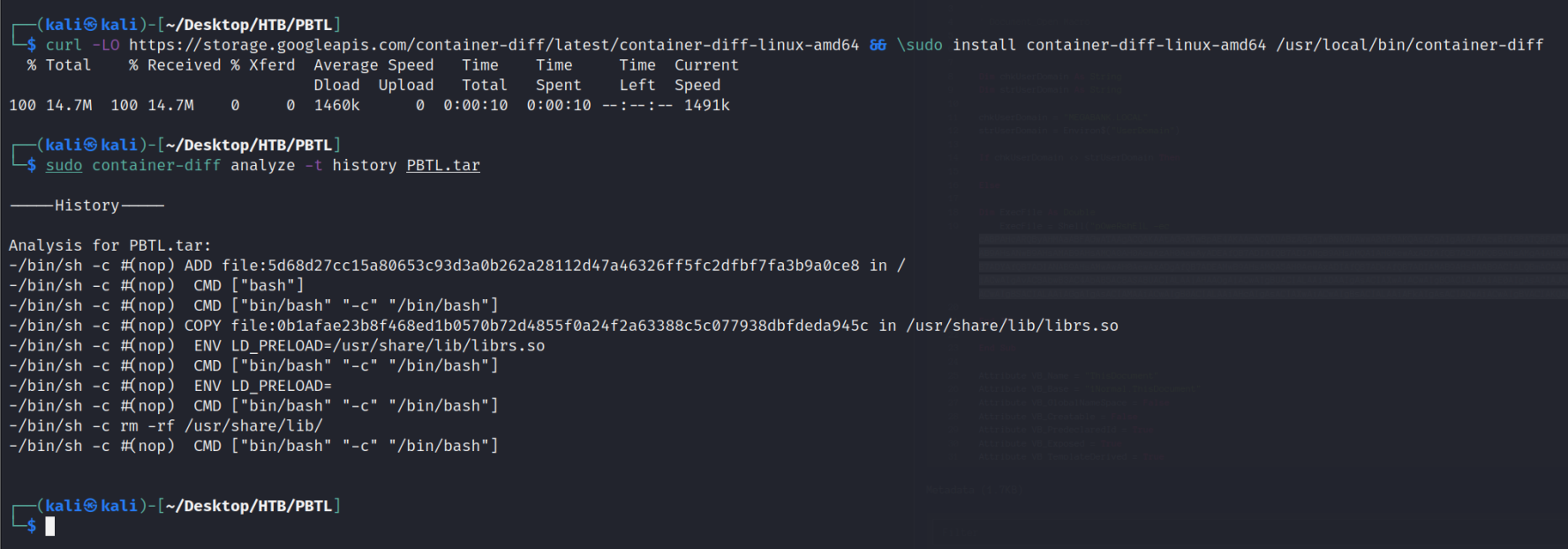
It appears the a file was /usr/share/lib. We need to check that file. So navigate to that folder by untar'ing the save and layer files.
tar xf PBTL.tar
cd 0aec9568b70f59cc149be9de4d303bc0caf0ed940cd5266671300b2d01e47922/
tar xf layer.tar
cd /usr/share/lib
strings librs.so
and run strings against librs.so and we get this output:
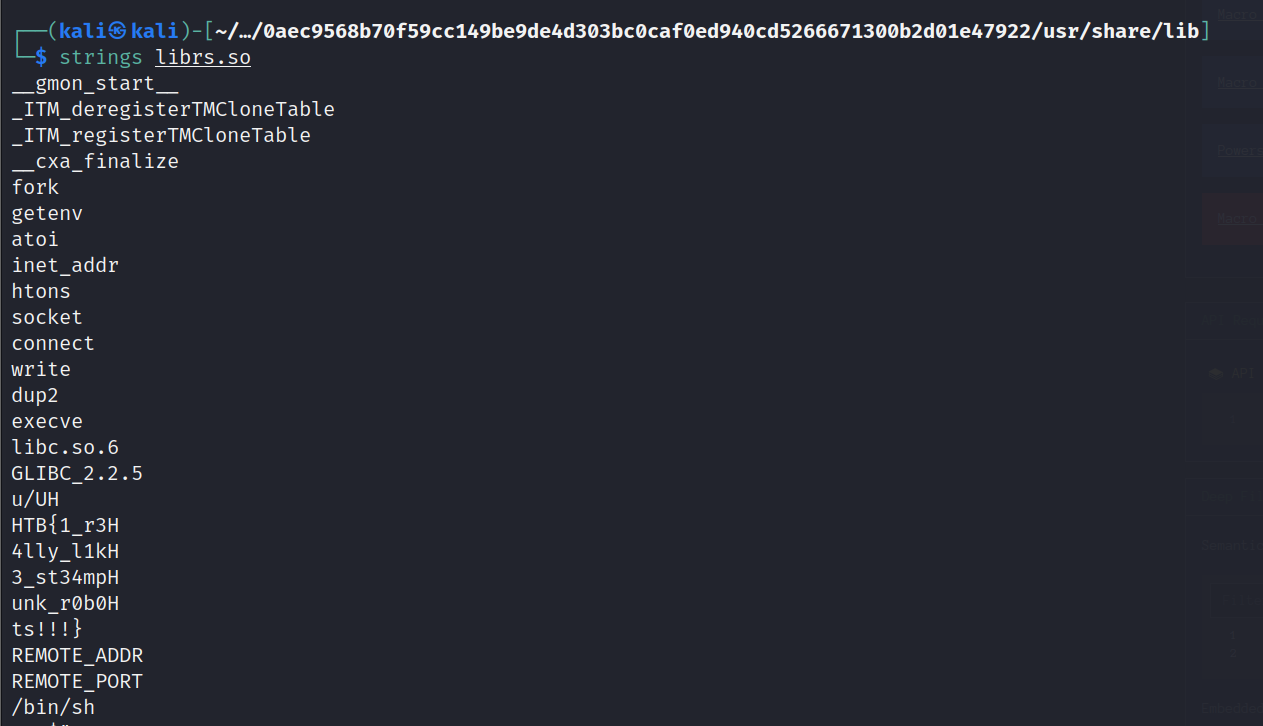
HTB{1_r3H4lly_l1kH3_st34mpHunk_r0b0Hts!!!} is right before the REMOTE_ADDR and REMOTE_PORT backdoor commands. Remove the H's. They're not supposed to be there and change the leet spelling on the flag.
HTB{1_r34lly_l1k3_st34mpunk_r0b0ts!!!}
Fun challenge. Always interesting to see what can be done with Docker.
