Security Blog, Rants, Raves, Write-ups, and Code
HDC
When we navigate to the instance of the challenge, we are greeted with a simple login screen for Hades Distribution Company (now I know where HDC came from). Like the Cartographer challenge, the first thing I try is a SQL injection. No dice on that approach. So, I kick off Dirbuster and then take a look at the source code of the page while that runs. First thing that jumps out at me is the myscripts.js file with a doProcess() function. So, let me take a look at jquery and see if the doProcess function sends something there.
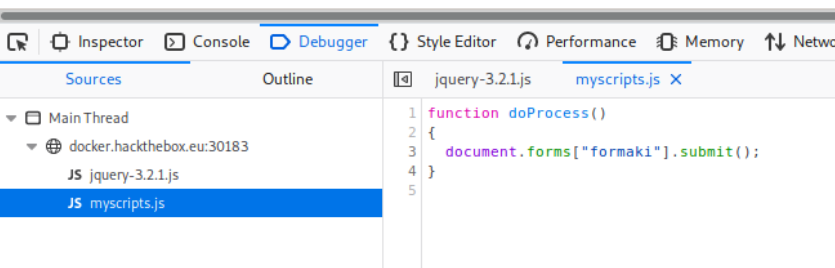
Sure enough, we find this (after dropping it into JS Beautify
function doProcess() {
var form = document.createElement("form");
form.setAttribute("method", "post");
form.setAttribute("action", "main/index.php");
form.setAttribute("target", "view");
var hiddenField = document.createElement("input");
hiddenField.setAttribute("type", "hidden");
hiddenField.setAttribute("name", "name1");
hiddenField.setAttribute("value", "TXlMaXR0bGU");
var hiddenField2 = document.createElement("input");
hiddenField2.setAttribute("type", "hidden");
hiddenField2.setAttribute("name", "name2");
hiddenField2.setAttribute("value", "cDB3bmll");
form.appendChild(hiddenField2);
form.appendChild(hiddenField);
form.appendChild(hiddenField2);
document.body.appendChild(form);
window.open('', 'view');
form.submit();
}
Hi there! 2 hidden fields that could easily be the credentials. Developers, please, for the love of ALL that is good and Holy in this world, please stop hard-coding credentials into things! So, let's try:
Username: TXlMaXR0bGU<br>
Password: cDB3bmll<br><br>
We're in. One problem solved. If somebody is doing shadiness (like the challenge hint would suggest), Mailbox of Special Customers looks like a good place to start
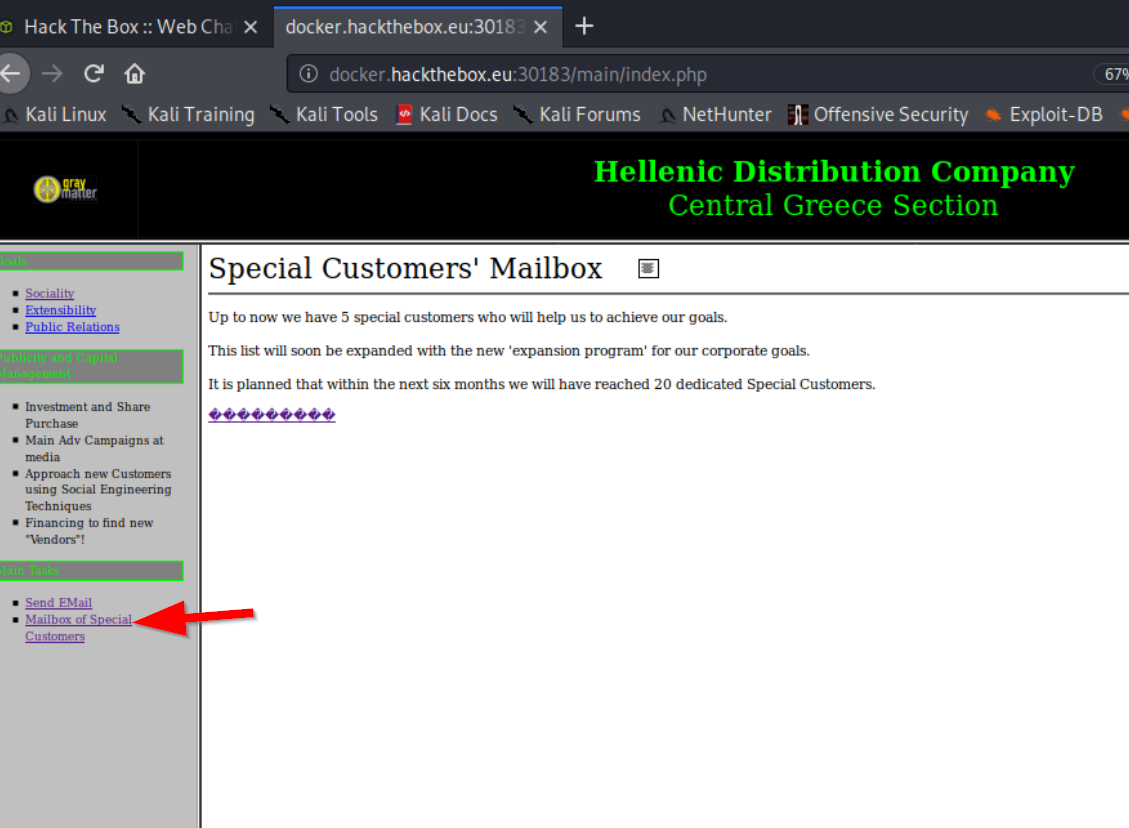
So, I take a look at the UTF Unicode string, but that's a dead end. We do have this strange tiny icon/image thing next to the heading. Let's Inspect Element on that.
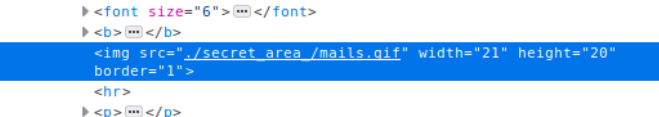
Well, that's interesting. We have a secret_area_ folder. My Dirbuster blew up with errors so I wasn't able to brute find it. Navigating to that folder shows us the mails.gif and a mails.txt file.
All good boys are here... hehehehehehe!
----------------------------------------
Peter Punk [email protected]
Nabuchodonosor [email protected]
Ilias Magkakos [email protected]
Nick Pipshow [email protected]
Don Quixote [email protected]
Crazy Priest [email protected]
Fishroe Salad [email protected]
TaPanta Ola [email protected]
Laertis George [email protected]
Thiseas Sparrow [email protected]
Black Dreamer [email protected]
Callme Daddy [email protected]
Aggeliki Lykolouli [email protected]
Kompinadoros Yannnnis [email protected]
Serafino Titamola [email protected]
Joe Hard [email protected]
Bond James [email protected]
Endof Text [email protected]
We're told the flag is not an email address, but the hint wants us to use the site's mail function to find out the who. So, let's just intercept each of the requests and responses in Burp Suite Community and see if any of them pop out a magic response. Finally, we get a response with the flag! HTB{FuckTheB3stAndPlayWithTheRest!!}