Security Blog, Rants, Raves, Write-ups, and Code

Security Blog, Rants, Raves, Write-ups, and Code
Find the Secret Flag
| Name: | Find the Secret Flag |
|---|---|
| Hint: | Find the secret flag and get the name of the creators of this challenge! |
| Base Points: | Medium - Retired [0] |
| Rated Difficulty: |  |
 |
stefano118 |
| Creator: | decoder |
Inside the ZIP file is a single, seemingly simple BIN file. Importing into Ghidra (I like Ghidra, just don't do the whole Shared Project thing) and analyzing the functions, we eventually come across a function that is never called FUN_00400AFE.
Incidentally, I'm skipping the entire function at FUN_004009aa. It is a rabbit hole that reads the /tmp/secret and spit out false flags. As someone who already struggles a bit with BIN and Assembly RE, all that did was piss me off.
Here is the function itself:
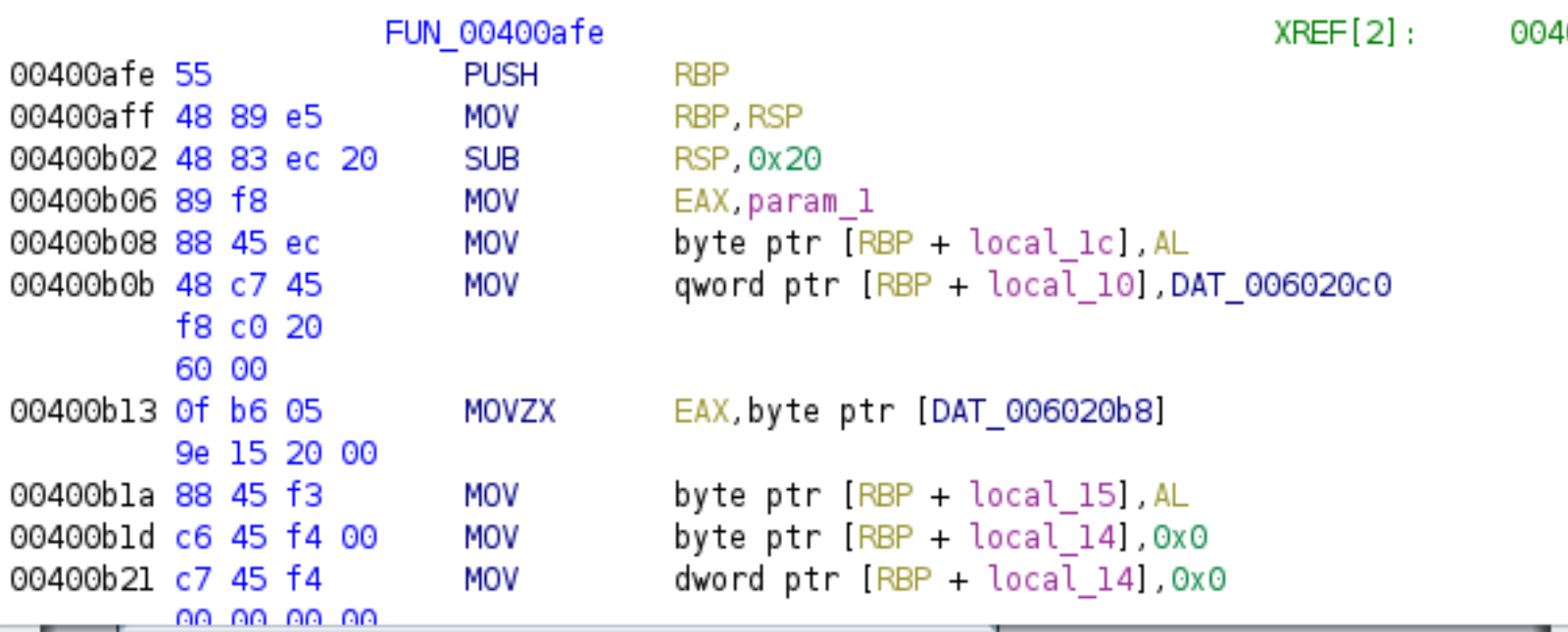
void FUN_00400afe(byte param_1)
{
int iVar1;
bool bVar2;
long lVar3;
int local_14;
byte *local_10;
local_10 = &DAT_006020c0;
local_14 = 0;
lVar3 = ptrace(PTRACE_TRACEME,0,0,0);
if (lVar3 != -1) {
while ((*local_10 != param_1 &&
(iVar1 = local_14 + 1, bVar2 = local_14
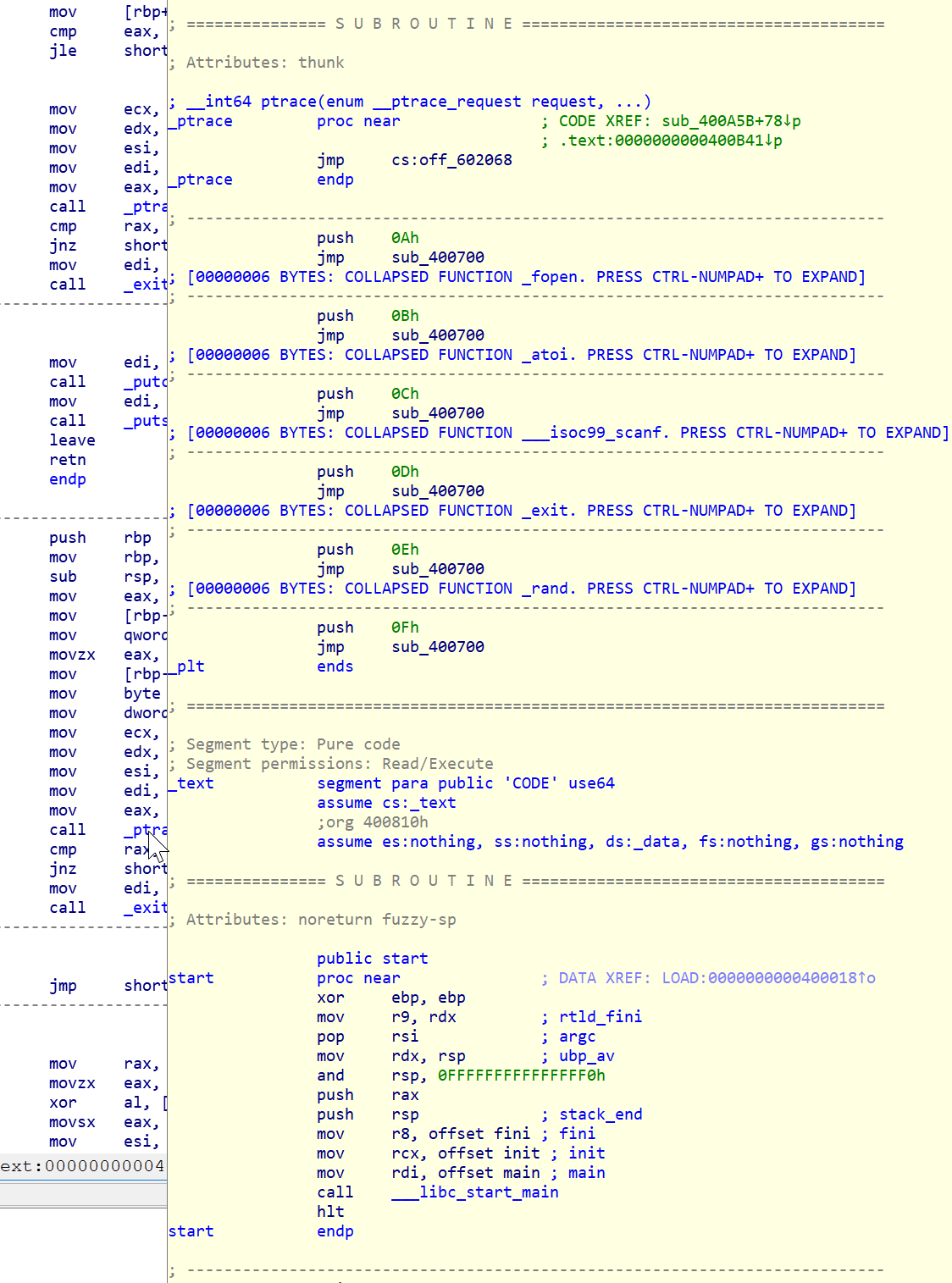
Here, we reach the limit of what I can do in Ghidra. There may be a way to proceed farther, but I don't know it (struggle with BIN remember). So, I pop it into IDA and look for that function again. Interestingly enough, 400AFE in IDA has us looking at some interesting strings/code.
.text:0000000000400AFE ; ---------------------------------------------------------------------------
.text:0000000000400AFE push rbp
.text:0000000000400AFF mov rbp, rsp
.text:0000000000400B02 sub rsp, 20h
.text:0000000000400B06 mov eax, edi
.text:0000000000400B08 mov [rbp-14h], al
.text:0000000000400B0B mov qword ptr [rbp-8], offset a7967iiYy ; "#967ii`\ayy\a%"
.text:0000000000400B13 movzx eax, cs:byte_6020B8
.text:0000000000400B1A mov [rbp-0Dh], al
.text:0000000000400B1D mov byte ptr [rbp-0Ch], 0
.text:0000000000400B21 mov dword ptr [rbp-0Ch], 0
.text:0000000000400B28 mov ecx, 0
.text:0000000000400B2D mov edx, 0
.text:0000000000400B32 mov esi, 0
.text:0000000000400B37 mov edi, 0
.text:0000000000400B3C mov eax, 0
.text:0000000000400B41 call _ptrace
.text:0000000000400B46 cmp rax, 0FFFFFFFFFFFFFFFFh
.text:0000000000400B4A jnz short loc_400B56
.text:0000000000400B4C mov edi, 1
.text:0000000000400B51 call _exit
.text:0000000000400B56 ; ---------------------------------------------------------------------------
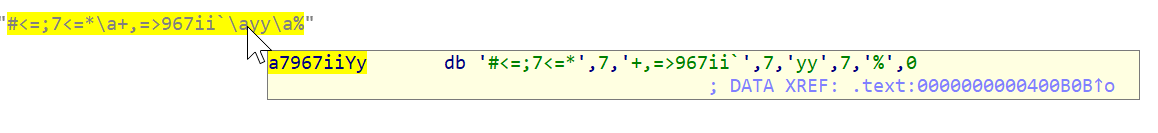
Going through each line of this, we find a nice subroutine in _ptrace that XOR's that
"#<=;7<=*\a+,=>967ii`\ayy\a%"
string with some random byte and we also notice that the \a's are actually Bells on the the actual string so it's really
#<=;7<=*+,=>967ii`yy%.
The HEX of that is 23 3C 3D 3B 37 3C 3D 2A 07 2B 2C 3D 3E 39 36 37 69 69 60 07 79 79 07 25
So, now we know what it's trying to do. Not bad for a guy that SUCKS at assembly, right? Let's dump that string into Cyber Chef and brute force the hex of it. We can Hex it https://onlinehextools.com/convert-hex-to-string
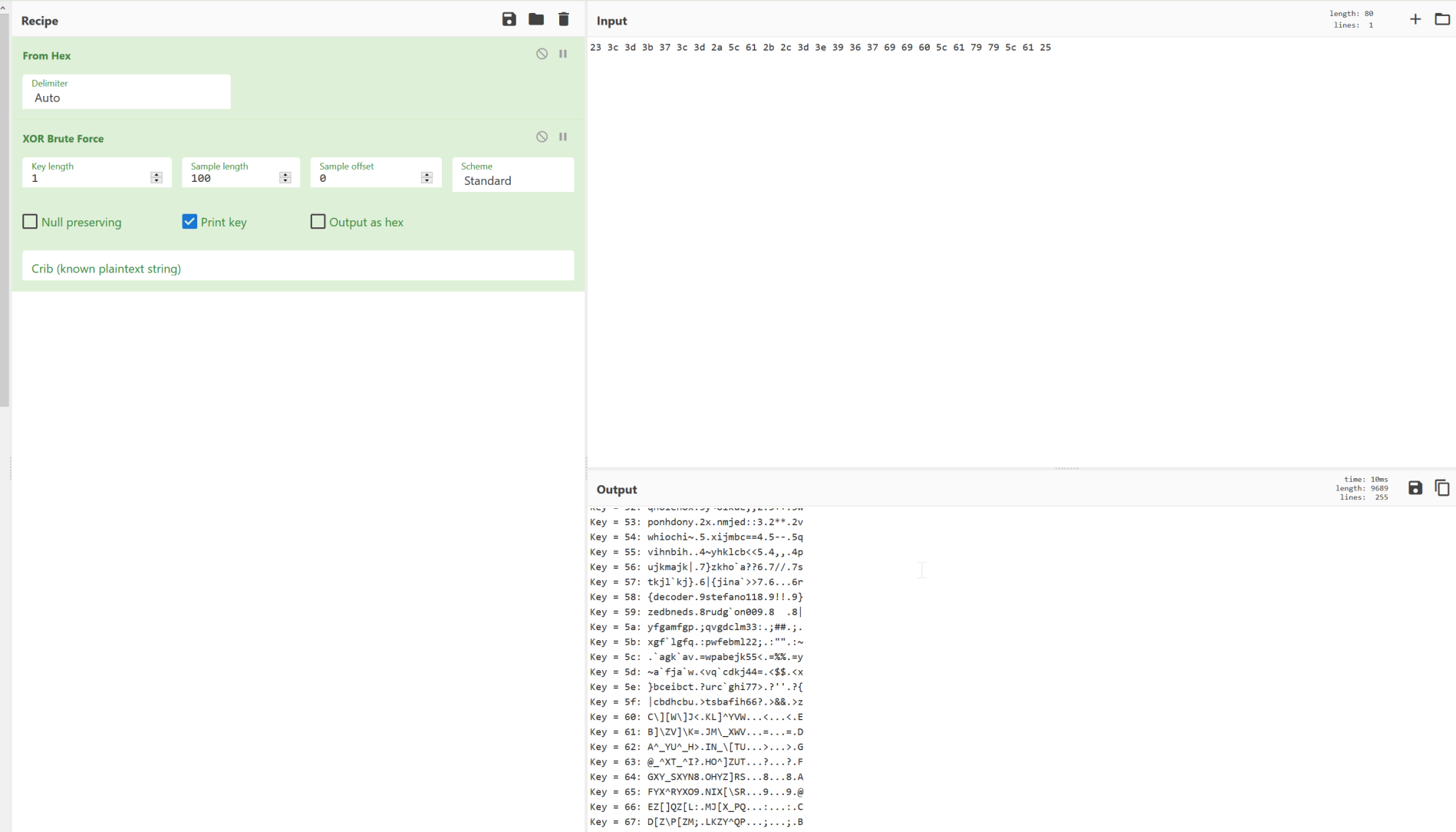
Hey, look! Chek baked a flag for us!
