
Security Blog, Rants, Raves, Write-ups, and Code
Cartographer
| Name: | Cartographer |
|---|---|
| Hint: | Some underground hackers are developing a new command and control server. Can you break in and see what they are up to? |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
 |
destiny |
| Creator: | Arrexel |
Web Challenges provide a web address with a unique port. ALL of the Web challenges have an address of "docker.hackthebox.eu." It is the port that changes. So, we fire up the instance and nav to the address.
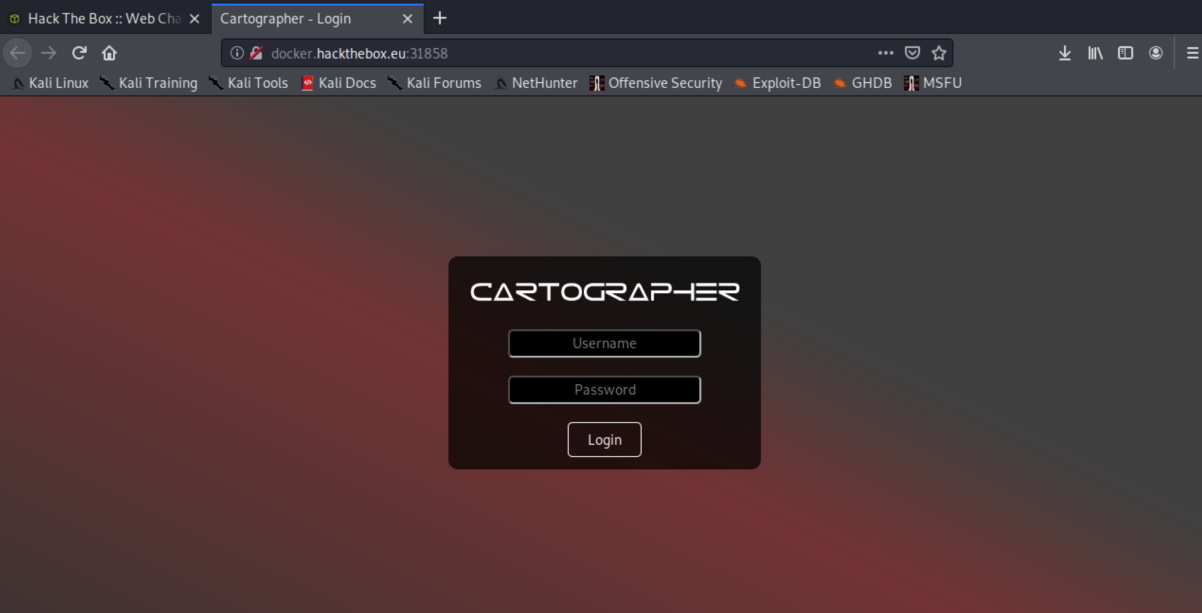
A simple login page. Let's try the usual suspects (admin:admin; admin:password; SQL injection). Using 'or'1'='1 for both user and password, we get in!!
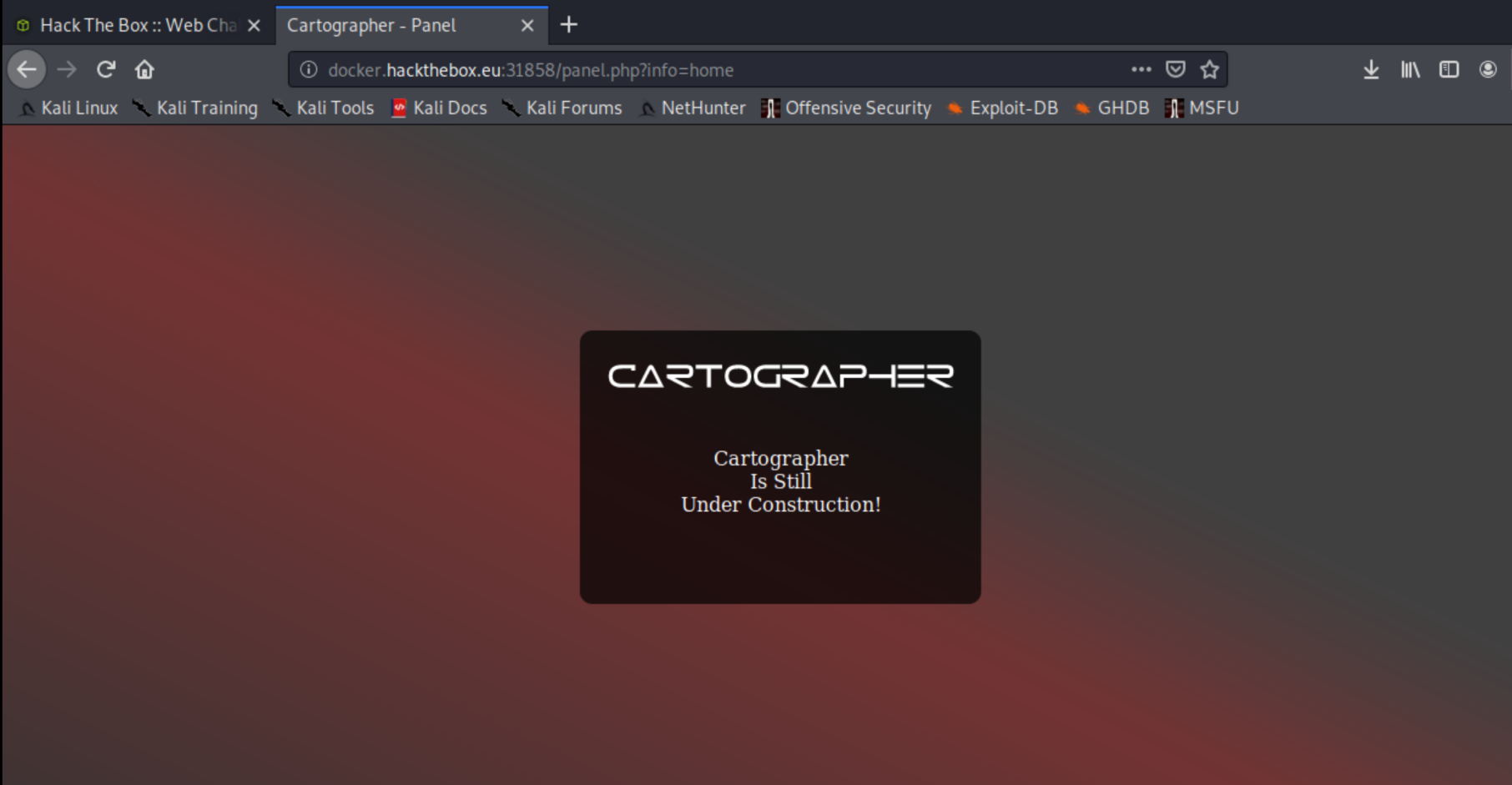
The URL now adds a ?info=home component. It looks like the site is using the info=whatever to query specific pagea. Just for kicks, let me change home to flag (So, ?info=flag).
OK....a) I got lucky; b) sometimes, it really is that easy.

