
Security Blog, Rants, Raves, Write-ups, and Code
Beatles
We are greeted with two challenge files: BAND.zip and m3ss@g#_f0r_pAuL. If we try to unzip the ZIP file, it asks for a password. Let me fire it up in fcrack and look at the txt file.
$fcrackzip -u -D -w /usr/share/wordlists/rockyou.txt BAND.zip
[Changing Tabs]
cat m3ss@g#_f0r_pAuL
Url Cnhy,
Zl Sbyqre unf cnffcuenfr jvgu sbhe (4) punenpgref.
Pbhyq lbh spenpx vg sbe zr???
V fraq lbh n zrffntr sbe bhe Gbhe arkg zbagu...
Qba'g Funer vg jvgu bgure zrzoref bs bhe onaq...
-Wbua Yraaba
CF: Crnpr naq Ybir zl sevraq... Orngyrf Onaq sbe rire!
Looks like a simple subsitution cipher. Let me drop in Cryptii and see what I can find.
Hey Paul,
My Folder has passphrase with four (4) characters.
Could you fcrack it for me???
I send you a message for our Tour next month...
Don't Share it with other members of our band...
-John Lennon
PS: Peace and Love my friend... Beatles Band for ever!
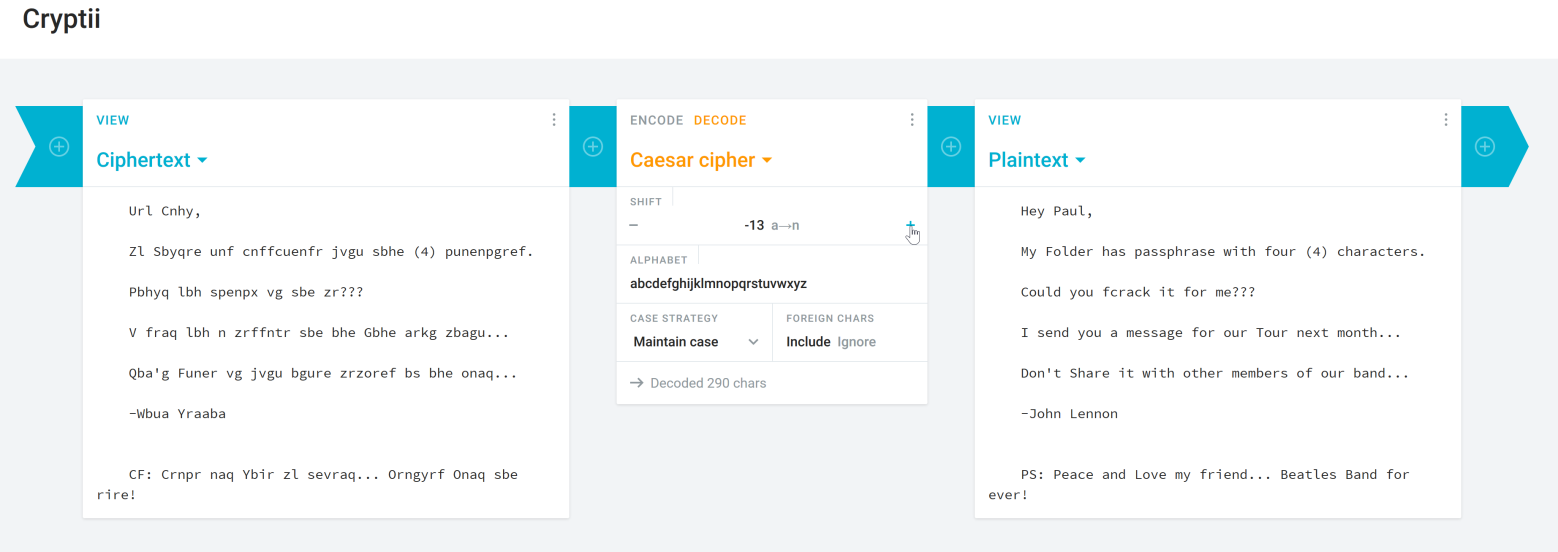
It looks like it's a Caesar Cipher with a -13 substitution. Funny thing is, if I switch back to my fcrack tab, it's already figured out that the password is 'pass'. Didn't really need to crack the message, but hey, it's good recognition practice XD So, we unzip BAND and are given a BAND.JPG (Dear God, why the CAPS?!?!) which is just a simple picture of one of the Beatles album covers (a silhouette of the Help! album cover if memory serves). Since we are in Stego, learn and love binwalk and stegsuite. You'll need them.
Binwalk gave us nothing useful, and steghide extract asks for a password, which we don't have yet. Unfortunately, this one takes a little bit of guesswork. The challenge is about the Beatles so let's start there with TheBeatles. That didn't work. I tried the beatles, The Beatles. thebeatles, The_Beatles, etc. Wait, the author apparently has a thing for CAPS so let's try THEBEATLES. BINGO!
$ steghide extract -sf BAND.JPG
Enter passphrase: THEBEATLES
wrote extracted data to "testabeatle.out".
$ file testabeatle.out
testabeatle.out: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2,
for GNU/Linux 2.6.32, BuildID[sha1]=ca68ea305ff7d393662ef8ce4e5eed0b478c8b4e, not stripped
An ELF file? Did this Stego turn into a Reversing? Let's run strings on it and see what happens.
$ strings testabeatle.out
<I shortened this for brevity and only showed th relevant strings>
Hey Paul! If you are here... Give my your favourite character!
Ok Paul... A little challenge for you mate, cause last month someone crazy man hacked...WTF! Let's Begin!
########################################Challenge############################################################
Tell me PAul! The result of 5+5?
Ok!ok! it was easy... Tell me now... The result of: 5+5-5*(5/5))?
Last one! The result of: (2.5*16.8+1.25*10.2+40*0.65+1.5*7.5+1.25*3.2):40
Hey Paul! nice!!! this is the message
VGhlIHRvdXIgd2FzIGNhbmNlbGVkIGZvciB0aGUgZm9sbG93aW5nIG1vbnRoLi4uIQ0KDQpJJ2xsIGdvIG91dCBmb3IgZGlubmVyIHdpdGggbXkgZ2lybGZyaWVuZC
BuYW1lZCBZb2NvISA7KQ0KDQpIVEJ7UzByUnlfTXlfRlIxM25EfQ0K
WTF! You are not Paul!! SOS SOS SOS HACKER HERE!! I will call the police someone want to steal my data!!!
########################################END OF CHALLENGE############################################################
Well that string looks interesting and looks like Base64. Let's decode it and see what John is saying.
https://www.base64decode.org/
OR
$ echo 'VGhlIHRvdXIgd2FzIGNhbmNlbGVkIGZvciB0aGUgZm9sbG93aW5nIG1vbnRoLi4uIQ0KDQpJJ2xsIGdvIG91dCBmb3IgZGlubmVyIHdpdGggbXk
gZ2lybGZyaWVuZCBuYW1lZCBZb2NvISA7KQ0KDQpIVEJ7UzByUnlfTXlfRlIxM25EfQ0K' | base64 -d
The tour was canceled for the following month...!
I'll go out for dinner with my girlfriend named Yoco! ;)
Easy Peasy!


